
Two PoC exploits for Memcached DDoS attacks have been released online
7.3.2018 securityaffairs Attack Exploit
Memcached DDoS attacks – A few days after the disclosure of the World’s largest DDoS attack record that peaked a 1.7Tbps, two PoC exploits code for Memcached amplification attacks have been released online.
The technique behind Memcached DDoS attacks, is one of the coolest topics in cybersecurity at this moment.
World’s largest DDoS attack record lasted just a few days, Arbor Networks reported that earlier this month a US service provider suffered a 1.7 Tbps memcached DDoS attack.

Now two distinct proofs-of-concept (PoC) exploits code for Memcached amplification attacks have been released online, this means that anyone can use them to launch memcached DDoS attacks
One of PoC code exploits is written in Python scripting language and relies on the Shodan search engine API to obtain update a list of vulnerable Memcached servers and then involve them in memcached DDoS attacks.
The second exploit code is written in C programming and uses a pre-compiled list of vulnerable Memcached servers. The author also published the file memecache-amp-03-05-2018-rd.list that is a list of vulnerable memcached servers as of 03-05-2018.
Bonus—its description already includes a list of nearly 17,000 potential vulnerable Memcached servers left exposed on the Internet.
22h
DΛNIΞL 🤖
@hypoweb
List of memcached servers as of 03-06-2018https://pastebin.com/raw/eSCHTTVu
DΛNIΞL 🤖
@hypoweb
Another memcached-poc https://pastebin.com/raw/ZiUeinae
11:06 AM - Mar 7, 2018
39
27 people are talking about this
Twitter Ads info and privacy
We first read about memcached DDoS attacks when on February 28, 2018, the code hosting website GitHub was hit by the largest-ever DDoS attack that peaked at 1.3Tbps.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
The abuse of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.
Experts at Cloudflare dubbed this type of attack Memcrashed, according to the researcher the amplification technique could allow attackers to obtain an amplification factor of 51,200.
We have no doubts, the situation will get worse due to the availability online of the PoC exploit codes.
Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
“Internet Service Providers – In order to defeat such attacks in future, we need to fix vulnerable protocols and also IP spoofing. As long as IP spoofing is permissible on the internet, we’ll be in trouble.” concluded Cloudflare.
“Developers – Please please please: Stop using UDP. If you must, please don’t enable it by default. If you do not know what an amplification attack is I hereby forbid you from ever typing SOCK_DGRAM into your editor.”
The fear for this new kind of attack represents a good opportunity for cyber criminals, crooks already started to blackmail companies asking for a ransom demand in Monero cryptocurrency to avoid being attacked via Memcached servers.
Memcached DDoS Exploit Code and List of 17,000 Vulnerable Servers Released
7.3.2018 thehackernews Attack Vulnerebility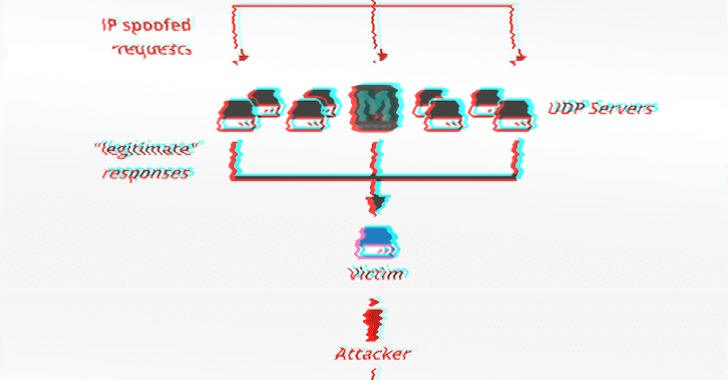
Someone has just released proof-of-concept (PoC) exploit code for amplification attack and a pre-compiled list of nearly 17,000 potential vulnerable Memcached servers on the Internet that could even allow script-kiddies to launch massive DDoS attacks using UDP reflections easily.
Last week we saw two record-breaking DDoS attacks—1.35 Tbps hit Github and 1.7 Tbps attack against an unnamed US-based company—which were carried out using a technique called amplification/reflection attack.
For those unaware, Memcached-based amplification/reflection attack amplifies bandwidth of the DDoS attacks by a factor of 51,000 by exploiting thousands of misconfigured Memcached servers left exposed on the Internet.
Memcached is a popular open source distributed memory caching system, which came into news earlier last week when researchers detailed how hackers could abuse it to launch amplification/reflection DDoS attack by sending a forged request to the targeted Memcached server on port 11211 using a spoofed IP address that matches the victim's IP.
A few bytes of the request sent to the vulnerable Memcached server can trigger tens of thousands of times bigger response against the targeted IP address, resulting in a powerful DDoS attack.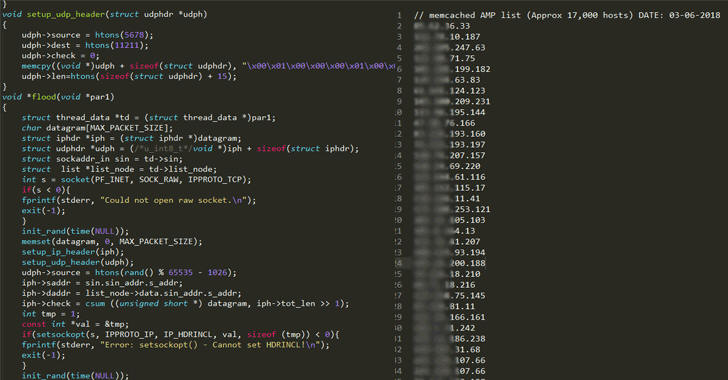
For a detailed explanation on how Memcached amplification attack works, you can head on to our previous article.
Since last week when Memcached has been revealed as a new amplification/reflection attack vector, some hacking groups started exploiting unsecured Memcached servers.
But now the situation will get worse with the release of PoC exploit code, allowing anyone to launch massive DDoS attacks, and will not come under control until the last vulnerable Memcached server is patched, or firewalled on port 11211, or completely taken offline.
Moreover, cybercriminals groups have already started weaponizing this new DDoS technique to threaten big websites for extorting money.
Following last week's DDoS attack on GitHub, Akamai reported its customers received extortion messages delivered alongside the typically "junk-filled" attack payloads, asking them for 50 XMR (Monero coins), valued at over $15,000.
Reflection/amplification attacks are not new. Attackers have previously used this DDoS attack technique to exploit flaws in DNS, NTP, SNMP, SSDP, Chargen and other protocols in order to maximize the scale of their cyber attacks.
To mitigate the attack and prevent Memcached servers from being abused as reflectors, the best option is to bind Memcached to a local interface only or entirely disable UDP support if not in use.
Qualcomm Requests National Security Review of Broadcom Bid
7.3.2018 securityweek IT
US chipmaker Qualcomm postponed its annual shareholders' meeting after secretly requesting a national security review of Broadcom's bid to take over the company, the Singapore-based Broadcom announced Monday.
Qualcomm shareholders were due to meet Tuesday, but Broadcom said it was informed Sunday night that Qualcomm filed a voluntary request on January 29 for US regulators to investigate the deal, and was ordered to postpone the meeting for 30 days.
"It should be clear to everyone that this is part of an unprecedented effort by Qualcomm to disenfranchise its own stockholders," Broadcom said in a statement.
Qualcomm fired back accusing Broadcom of trying to mislead shareholders and 'trivialize' US regulatory and national security issues.
Broadcom"Broadcom's dismissive rhetoric notwithstanding, this is a very serious matter for both Qualcomm and Broadcom," the US chipmaker said.
The Committee on Foreign Investment in the United States (CFIUS) can review any acquisition by a foreign corporation of a US firm that may have an impact on national security, and can recommend the president block the deal. CFIUS has blocked some transactions, but frequently foreign companies withdraw once it appears a transaction will be prohibited.
CFIUS issued an order to Qualcomm for the shareholder meeting to be delayed for 30 days to allow time to fully investigate the proposed acquisition by Broadcom, according to a US Treasury Department.
Broadcom said it will fully cooperate with the review, but rejected any national security concerns since it is a US-controlled company, and is in the process of relocating its headquarters back to the United States.
- Board battle -
If finalized, the Broadcom-Qualcomm tie-up, estimated at $117 billion, would be the largest merger in a sector awash with consolidation amid the development of technologies for autonomous vehicles and 5G mobile services.
Qualcomm has repeatedly rejected multiple Broadcom offers that it says undervalue the company.
Shareholders at Qualcomm's annual meeting were to vote whether to replace six of the California company's 11 board members with candidates backed by Broadcom, essentially endorsing the merger deal.
Weeks of thrust and parry, along with tactical public statements, have left the companies' boards at odds over the unsolicited offer.
Qualcomm, which is the dominant maker of microprocessors for smartphones, says it has a bright future on its own, especially amid a transition to fifth-generation (5G) wireless communications networks.
The Qualcomm board has also expressed concern that any deal with Broadcom could be delayed or blocked by antitrust regulators around the world.
Broadcom has urged Qualcomm shareholders to elect all six of its nominees to the board, sending "a clear signal" supporting the takeover bid which would provide a handsome gain to shareholders of the US firm.
"This was a blatant, desperate act by Qualcomm to entrench its incumbent board of directors and prevent its own stockholders from voting for Broadcom's independent director nominees," Broadcom said of the delaying development.
- Coveted chip technology -
CFIUS last year opposed the takeover of US semiconductor manufacturer Lattice by a Chinese state group backed by a US investment fund, and President Donald Trump then blocked the deal.
In the semiconductor sector, the committee -- whose deliberations are secret -- in 2016 recommended that then-President Barack Obama oppose a deal between the German group Aixtron and Chinese fund Grand Chip because there was a US subsidiary of the German group.
Broadcom's initial offer already was tinged by politics, coming as it did the day after a White House meeting between Trump and Broadcom CEO Hock Tan, who promised to repatriate the company's headquarters.
Any tie-up of the two giants could reshape the fast-evolving sector of chips for smartphones and connected devices. But it would have to pass regulatory muster in several countries.
Analyst Patrick Moorhead of Moor Insights & Strategy questioned the wisdom of Broadcom buying Qualcomm.
The rival chip companies are very different in their approaches to the market, Moorhead said, comparing the tie-up to mixing "oil and water."
Qualcomm is known for mobile chip innovations that set industry standards, for example in new superfast 5G wireless connection technology, the analyst noted.
Meanwhile, Broadcom is adept at using intellectual property developed by others and making products at low cost, referring to them as "implementers."
Qualcomm, one of Apple's main suppliers, is currently engaged in the acquisition of the Dutch group NXP and has indicated the operation will proceed regardless of the outcome of discussions with Broadcom.
Broadcom shares lost 1.5 percent by the close of trading in New York, while Qualcomm fell 1.1 percent.
NSA Used Simple Tools to Detect Other State Actors on Hacked Devices
7.3.2018 securityweek BigBrothers
NSA uses simple tools to detect friendly parties and adversaries on hacked devices
An analysis of leaked tools believed to have been developed by the U.S. National Security Agency (NSA) provides a glimpse into the methods used by the organization to detect the presence of other state-sponsored actors on hacked devices, and it could help the cybersecurity community discover previously unknown threats.
Over the past few years, a mysterious hacker group calling itself Shadow Brokers has been leaking tools allegedly created and used by the Equation Group, a threat actor widely believed to be linked to the NSA. The Shadow Brokers have been trying to sell Equation Group tools and exploits, but without much success. They say their main goal has been to make money, but many doubt their claims.
One of the sets of files leaked by the hackers last year, named “Lost in Translation,” includes a series of modules dubbed “Territorial Dispute.” Researchers at the Laboratory of Cryptography and System Security (CrySyS Lab) of the Budapest University of Technology and Economics in Hungary, who have been involved in the analysis of Duqu and other advanced persistent threats (APTs), have conducted an investigation and they determined that the Territorial Dispute tools are designed to detect the presence of other state-sponsored groups.
According to CrySyS, the tools are relatively simple; they search the targeted device for specific files, Windows registry entries, and other indicators of compromise (IoCs) associated with known APTs.
Other Equation Group tools leaked by the Shadow Brokers are designed to allow operators to check for the presence of more common malware, but the Territorial Dispute modules are more interesting as they focus on state-sponsored attacks. Researchers believe the goal of these tools is likely to avoid any conflict with friendly parties and also minimize the chances of the NSA’s own malware getting detected.
There are several aspects that make the Territorial Dispute tools interesting. One of them is the fact that while typically there are tens or hundreds of IoCs associated with state-sponsored threat groups, these tools only look for 1-5 indicators.
Experts speculate that the reason behind this decision is to provide operators as little information as possible and prevent them from knowing too much about an attack. This theory is reinforced by the fact that each of the 45 signatures used by the detection engine has a very generic name, specifically SIG1 through SIG45.
Researchers say that while this seems like a strange decision, they believe the NSA may have conducted an analysis and determined that there is a significant risk of misappropriation. Limiting the number of IoCs included in the tools could represent a way to lower the risk.
Experts also noticed that if certain files are identified, the operator of the Territorial Dispute tools is informed that the malware is friendly or receives instructions to pull back. The list of instructions and observations includes “seek help immediately,” “dangerous malware - seek help ASAP,” “friendly tool - seek help ASAP” and “unknown - please pull back.”
CrySyS has attempted to link the IoCs to known threat groups using public information available via Google and by comparing them to data from its own malware repository, which contains roughly 150 Tb of malicious binaries. This led to the discovery of thousands of malware samples.
The IoCs appear to target known APTs whose activities have been analyzed by the cybersecurity industry over the past decade, including APT28 (aka Sofacy and Fancy Bear), Turla (aka Snake and Uroburos), Animal Farm, Duqu, Stuxnet, Flame, TeamSpy, Elderwood Group (Operation Aurora), Iron Tiger, and Dark Hotel, which have been linked to Russia, France, the United States, Israel, South Korea, and China.
While many of the IoCs are associated with known groups, there are also some indicators that researchers have not been able to link to any threat actor. This suggests that the NSA may be aware of attacks and attackers that are not known to the public.
Boldizsár Bencsát, one of the experts involved in this research, told SecurityWeek that the threat corresponding to the SIG32 signature could be a previously unknown APT. Searching Google for one of the SIG32 indicators of compromise points to a Trend Micro threat encyclopedia entry for a piece of malware first detected in 2010. However, there is no indication that this malware has been known to be used by state-sponsored hackers.
“We think that careful analysis of the leaked material and cross-checking with public information and malware databases can reveal interesting, previously unknown information about the APT scene,” Bencsát said. “Also, we can possibly get a better understanding about the knowledge of governmental organizations on these attacks.”
CrySyS does not exclude the possibility that – since these tools have been publicly available for nearly a year – others used these indicators of compromise to uncover previously unknown APTs. Furthermore, while the IoCs are limited, they can turn out to be useful for obtaining more information on a threat group and making connections between attackers, their operations and their tools.
Bencsát will detail this research on Friday at Kaspersky Lab’s Security Analyst Summit (SAS) in Cancun, Mexico.
McAfee Launches Security Platform for Azure Cloud
7.3.2018 securityweek Security
Migrating to the cloud is complex. One of the biggest concerns is a loss of visibility on data in the cloud; and this concern only grows with increasing regulatory requirements. GDPR, coming into force in less than 3 months time, is a case in point.
Cloud access security brokers (CASBs) can improve visibility and control, but aren't necessarily tailored to a specific cloud. Today, McAfee announced the first product resulting from its purchase of Skyhigh Networks, finalized in January 2018: the McAfee Skyhigh Security Cloud for Azure.
"Moving applications, data and workloads to the cloud exposes enterprises to new threats and risks," explains Rajiv Gupta, SVP of McAfee's cloud security business unit. "At the same time, the adoption of cloud allows organizations to transform their business. This is why we are on a mission to make cloud the most secure environment for business. The introduction of McAfee Cloud Security Platform for Microsoft Azure is an important step to fulfilling this mission for our customers."
The new product offers five particular use cases for Azure users: configuration and compliance audit, activity monitoring, threat protection, DLP, and account management.
The configuration element detects misconfigurations in any Azure account. AWS S3 bucket misconfigurations have exposed millions of sensitive records in recent years, and in some cases left the accounts vulnerable to a MITM attack dubbed GhostWriter.
Detected misconfigurations can be corrected using McAfee best practices; CIS benchmark recommendations for Azure; and compliance recommendations for HIPAA-HITECH, ISO, FedRAMP, ITAR, other regulations, or internal compliance policies. "The solution can help with an organization's attempts to meet the GDPR regulations -- that are coming into force in less than 50 working days," said Nigel Hawthorn, EMEA marketing director at McAfee.
The activity monitoring element provides the visibility that can otherwise be lost in the cloud. It monitors both managed and unmanaged subscriptions, and captures a full audit trail of all activity. "We now have the visibility and control we need to be able to allow access to the cloud-based tools our employees need to be competitive and efficient, without compromising our security standards," comments Rick Hopfer, CIO at Molina Healthcare.
Threat protection is provided by AI-based user behavior analytics and signature-less, advanced malware analysis. Anomalous user behavior can highlight insider threats and unwarranted privilege escalation; while McAfee anti-malware will detect malware traveling into the cloud, and identify behavior indicative of malware data exfiltration or ransomware activity.
Data loss prevention (DLP) will help prevent unauthorized regulated data from being stored in Azure storage services -- which will be critical to maintaining GDPR compliance. McAfee's content analytics engine can be used to discover sensitive data stored in Azure services, using keywords and phrases, alpha-numeric patterns, file metadata, and more. It "allows us to extend DLP outside the perimeter and into the cloud and the user experience is seamless," says Mike Benson, CIO at DirecTV.
Account management is provided by McAfee's central policy engine, which aids the development of policies that can be enforced on new and pre-existing content, user activity, and malware threats. Options include the use of pre-built templates, the ability to import policies from other McAfee customers or partners, and a policy creation wizard to create custom policies to conform with corporate or regulatory requirements.
Security in the cloud is a shared responsibility between the cloud provider and the customer. It is a common failure to recognize this that leads to the misconfigurations so commonly found in AWS S3 buckets. In reality, both AWS and Azure have multiple flexible options for file and folder access -- and data protection problems are often based on this flexibility. The new McAfee/Skyhigh Azure solution is designed to remove confusion and apply customer visibility and control into the Azure cloud.
Chrome 65 Patches 45 Vulnerabilities
7.3.2018 securityweek Vulnerebility
Released in the stable channel this week, Chrome 65 brings 45 security fixes, including 27 patches for vulnerabilities discovered by external researchers.
The browser also includes an updated JavaScript engine, namely V8 version 6.5. Announced in early February and initially made available in Chrome 65 Beta, the new V8 engine includes an untrusted code mode meant to mitigate the latest speculative side-channel attack called Spectre.
The 27 vulnerabilities reported by researchers include 9 security flaws assessed with a High severity rating, 15 bugs considered Medium risk, and 3 issues with a Low severity rating.
Google rewarded the researchers over $34,000 in bug bounties, but hasn’t provided details on all payouts in the published advisory.
The most important of the addressed bugs are two High risk use after free in Flash (CVE-2018-6058 and CVE-2018-6059). Both were reported by JieZeng of Tencent Zhanlu Lab in August 2017 and were awarded a $5,000 bounty each.
Google also addressed a Use after free in Blink (CVE-2018-6060) and a Race condition in V8 (CVE-2018-6061) – two High severity flaws awarded $3,000 each –, as well as a Heap buffer overflow in Skia (CVE-2018-6062) – awarded $1,000.
Other High risk issues resolved in Chrome 65 include two incorrect permissions on shared memory bugs, one Type confusion in V8, and one Integer overflow in V8.
The most important of the Medium risk issues was CVE-2018-6066, a Same Origin Bypass via canvas that was awarded a $4,000 bounty.
Other Medium severity issues addressed in this release include Buffer overflow in Skia, Object lifecycle issues in Chrome Custom Tab, Stack buffer overflow in Skia, CSP bypass through extensions, Heap buffer overflow in Skia, Integer overflow in PDFium, Heap buffer overflow in WebGL, and Mark-of-the-Web bypass.
Google also addressed an overly permissive cross origin download, incorrect handling of URL fragment identifiers in Blink, a timing attack using SVG filters, URL Spoof in OmniBox, Information disclosure via texture data in WebGL, and Information disclosure in IPC call.
The three Low risk bugs resolved in the browser include XSS in interstitials, circumvention of port blocking, and incorrect processing of AppManifests.
The new application release is available for download as version Chrome 65.0.3325.146 for Windows, Mac and Linux computers. Chrome for Android has been updated as well, now available as version 65.0.3325.109.
Gozi Banking Trojan Uses "Dark Cloud" Botnet for Distribution
7.3.2018 securityweek BotNet Virus
The well-known Gozi ISFB banking Trojan recently started using the elusive "Dark Cloud" botnet for distribution, Talos warns.
Gozi has been around for several years and had its source code leaked online on two occasions over the past years, which led to the development of a new Trojan in 2016, GozNym. The malware has continued to remain active and even adopted new techniques in recent campaigns, such as the use of the Dark Cloud infrastructure.
The campaigns Talos has observed over the past few months are relatively low-volume, target specific organizations, and reveal significqant effort into the creation of convincing emails. Not only are the distribution and the command and control (C&C) infrastructure active for short periods of time only, but the actors behind them also move to new domains and IP addresses fast, even for individual emails sent as part of the same campaign.
The spam emails carry Microsoft Word documents as attachments. When opened, the files display a decoy image claiming that the document was created using Office 365 and that the user should "Enable Editing" and then "Enable Content" to view it. If the victim follows through, embedded macros are executed to download and run the malware.
The VBA macro is usually executed when the document is closed, in an attempt to bypass sandbox detection. The macro downloads an HTA file from a remote server, which is executed without alerting the user. The infection process continues with the execution of an obfuscated JavaScript script to run a PowerShell script to download and execute the final payload on the victim's machine.
The vast majority of the malicious documents used in campaigns in the fourth quarter of 2017 are individualized. Although they appear similar, differences exist in embedded macro, code, and even color of the decoy image.
Talos also discovered that the campaigns have been ongoing for a couple of years, and that the image in the documents has been changed from time to time, the same as the VBA code in the malicious macros. The researchers even observed localized documents in some cases, suggesting that “the separate attacks are highly customized and targeted.”
The final payload is usually a banking Trojan based on the Gozi ISFB code base, but other malware families (CryptoShuffler, Sennoma and SpyEye) were also observed.
The malware loader used in these attacks uses anti-virtualization and carries two versions of the same DLL, each targeting a different architecture. Depending on the victim machine, the loader injects either the 32-bit or the 64-bit DLL into the explorer.exe process.
The distribution infrastructure used in these campaigns overlaps with that of Dark Cloud, a botnet initially analyzed in 2016. The botnet, Talos notes, is used in the distribution and administration of various malware families, including Gozi ISFB and Nymaim.
In July 2016, a SentinelOne report on the Furtim-related SFG malware also revealed a connection between the Qbot (Qakbot or Quakbot) malware and Dark Cloud.
The botnet uses fast flux techniques to make the tracking of its backend infrastructure more difficult. “By frequently changing the DNS records associated with the malicious domains, attackers can make use of an extensive network of proxies, continuously changing the address of the IP being used to handle communications to the web servers the attacker controls,” Talos explains.
By looking at the domains and IP addresses associated with the infrastructure, the researchers discovered that it was serving a variety of cybercriminal activities, including carding forums, malware delivery and control, and spam.
Talos also discovered that the attackers aren’t using proxies and hosts in Western Europe, Central Europe, and North America, but mainly those located in Eastern Europe, Asia, and the Middle East.
“Gozi ISFB is a banking Trojan that has been used extensively by attackers who are targeting organizations around the world. It has been around for the past several years, and ongoing campaigns indicate that it will not be going away any time soon. Attackers are continuing to modify their techniques and finding effective new ways to obfuscate their malicious server infrastructure in an attempt to make analysis and tracking more difficult,” Talos concludes.
For the second time in two weeks CDOT shut down computers after a ransomware infection
7.3.2018 securityaffairs Ransomware
For the second time in two weeks, the computers at the Colorado Department of Transportation Agency shut down 2,000 computers after a ransomware infection.
For the second time in a few days, a variant of the dreaded SamSam ransomware paralyzed the CDOT.
The second incident occurred while the agency was still in the process of recovering its systems from the first attack.
Exactly two weeks ago, the SamSam ransomware made the headlines because it infected over 2,000 computers at the Colorado Department of Transportation (DOT).
The investigation on the first wave of infections revealed that the infected systems were running Windows OS and McAfee anti-virus software.
“Eight days into a ransomware attack, state information technology officials detected more malicious activity on the Colorado Department of Transportation computer systems Thursday.” reads the post published on the website 9news.com.
“A spokeswoman for the Governor’s Office of Information Technology says this is a variation of the same ransomware that hit computers last week, when criminals demanded a Bitcoin payment in exchange for freeing up the software.”
Approximately 20% of the machines infected by the first wave of attacks had been restored when a variation of the original Samsam ransomware hit the Colorado Department of Transportation for the second time. All the infected systems were taken down once again.
“The variant of SamSam ransomware just keeps changing. The tools we have in place didn’t work. It’s ahead of our tools.” Brandi Simmons, a spokeswoman for the state’s Office of Information Technology, told the Denver Post.

The attack forced CDOT employees to stop using computers and input data using pen and paper.
According to CDOT spokeswoman Amy Ford, the ransomware attack did not affect construction projects, signs, variable message boards and “critical traffic operations,”.
The Colorado National Guard and the FBI are working to restore normal operations.
“Employees have been ordered to shut off their computers until the source of the problem has been found. The network has been disconnected from the internet for now, and many employees are working on a pen and paper system.” continues the website.
At the time of writing, it is still impossible to evaluate the impact of the attack.
Mining is the new black
7.3.2018 Kaspersky Cryptocurrency
Last year we published a story revealing the rise of miners across the globe. At the time we had discovered botnets earning millions of USD. We knew this was just the beginning of the story, which turned out to develop rapidly.
Together with the rest of the world, we have been watching the hike in cryptocurrency, for example, the price of Bitcoin and Altcoins continuously beat records throughout 2017.
Bitcoin and Altcoins prices growth in 2017
While some spend time talking about what’s good or bad for the market and the global economy, we’ve seen that such a spike in prices was definitely a call for threat actors, meaning there are good opportunities for cybercriminals to earn money.
As a result, many cybercriminal groups have switched to malicious miner distribution, and the number of users that have encountered cryptocurrency miners has increased dramatically. We have found, that by the end of 2017, 2.7 million users had been attacked by malicious miners – this is almost 1.5 times higher than in 2016 (1.87 mln).
Number of Kaspersky Lab users attacked by malicious miners in 2017
They become so active and popular that even ransomware – which has frightened the world for the last couple of years, seems to step aside for this threat.
Here are some reasons why:
Firstly, miners and ransomware both have a clear monetization model. In the case of ransomware, attackers infect PCs, decrypt files and earn money by receiving a ransom for users’ data. The miners model is similar in its simplicity: attackers infect victims, make coins using CPU or GPU power, and earn real money through legal exchanges and transactions.
Miners’ monetization scheme
Secondly, unlike ransomware, it is very hard for users to understand if they’ve been infected by miners or not. In general, users use their computer for Internet surfing. This activity is not high loaded for CPU. The other 70-80% of CPU power is used by mining programs, and some of them have special functions to reduce mining capacities or cancel the process at all, if another resource-demanding program (for example, a videogame) is executed.
Most importantly, it is now very easy to make your own miner. Those interested can get everything that they need:
Ready to use partner programs
Open mining pools
A lot of miner builders
We have found that the most popular miner pool used by threat actors is Nanopool.
Statistics for used legitimate pools
If actors use open pools, it’s possible to find out how much money threat actors could earn.
Example of wallet information
Also, according to our data, 80% of illegal miners contain the open source code of legal miners, or it is just a legal miner that has been packed.
Ways of spreading
Usually, threat actors collaborate with potentially unwanted application (PUA) partner programs to spread miners. However, some small criminal groups try to spread malware by using different social engineering tricks, such as fake lotteries, etc. Potential victims need to download a generator of random numbers from a file-sharing service and run this on a PC to participate. It’s a simple trick, but a very productive one.
Another popular method is web-mining through a special script being executed in browser. For example, in 2017 our security solutions stopped the launch of web miners on more than 70 million occasions. The most popular script used by cybercriminals is Coinhive, and usual cases of its use in the wild are websites with a lot of traffic. The longer the user session on those sites, the more money the site’s owner earned from mining. Major incidents involving Coinhive are hacked web pages, such as the Pirate Bay case, YouTube ads or UFC fight pass mining. However, other examples of its legal use are also known.
There are other groups, which do not need to spread miners to many people. Instead, their targets are powerful servers in big companies. Thus, for instance, Wannamine was spreading in internal networks using an EternalBlue exploit, and earned nine thousand Monero this way (approx. two million dollars). However, the first miner that used the EternalBlue exploit was Adylkuzz. In our previous research we described another miner family – Winder – that has used an extra service to restore a miner when it was being deleted by an AV product. That botnet earned a half million dollars.
Sophisticated techniques
This year we are observing the next trend – threat actors behind miners have begun to use malware techniques from targeted attacks. Our latest discovery is the “hollow” miner that uses a process-hollowing technique.
In this case the infection vector is a PUA module. A victim may have just wanted to download a legitimate application, but instead they downloaded a PUA with a miner installer inside. This miner installer drops the legitimate Windows utility msiexec with a random name, which downloads and executes a malicious module from the remote server. In the next step it installs a malicious scheduler task which drops the miner’s body. This body executes the legitimate system process and uses a process-hollowing technique (legitimate process code is changed to malicious). Also, a special flag, system critical flag, is set to this new process. If a victim tries to kill this process, the Windows system will reboot. So, it is a challenge for security solutions to deal with such malicious behavior and detect the threat properly.
Infection chain
Process hollowing example
Using such sophisticated technique, botnets earned over seven million dollars during the second half of 2017.
Also this year, we found one threat group that has been targeting big organizations with the main purpose to utilize their computer resources for mining. After getting into a corporate network they get access to the domain controller, and as a result they use domain policies to launch malicious code. In this particular case, actors executed malicious PowerShell script on each endpoint and server inside the corporate network.
Malicious powershell script
This script has the following logic:
After launching, it checks if this endpoint belongs to specific accounts, i.e. senior levels or information security officers. If it is true, then the script won’t execute the miner.
This script also checks current date and time information. It will execute the malicious miner in non-working time.
So what’s next?
Should we expect a further evolution in this class of malware? For sure. Moreover, we will see a spread in malware that uses new blockchain technologies. One of the recent and very promising technologies is the blockchain-based proof-of-space (PoSpace) concept.
Unlike proof-of-work (PoW) used in general mining botnets, a PoSpace algorithm needs a hard disk space. Therefore, a new type of miners based on this algorithm will be aiming first of all at big data servers.
On the one hand, monetization in this case is like that in usual malware miners with a PoW algorithm. On the other, this technology can provide cybercriminals with another profit. The blockchain on the PoS algorithm is a very big decentralized anonymous data center that can be used to spread malware or illegal content. As a result, it can bring more damage. Data will be encrypted and no one will know where it is physically stored.
Mining scheme based on proof-of-concept algorithm
To protect your network against such threats we advise you:
Conduct a security audit on a regular basis
Use security solutions on endpoints and servers
Kaspersky Lab products detect such threats with various verdicts.
PDM:Trojan.Win32.Generic
not-a-virus:RiskTool.Win32.BitCoinMiner
HEUR:Trojan.Win32.CoinMiner