ISPs Caught Injecting Cryptocurrency Miners and Spyware In Some Countries
10.3.2018 thehackernews Cryptocurrency

Governments in Turkey and Syria have been caught hijacking local internet users' connections to secretly inject surveillance malware, while the same mass interception technology has been found secretly injecting browser-based cryptocurrency mining scripts into users' web traffic in Egypt.
Governments, or agencies linked to it, and ISPs in the three countries are using Deep Packet Inspection technology from Sandvine (which merged with Procera Networks last year), to intercept and alter Internet users' web traffic.
Deep packet inspection technology allows ISPs to prioritize, degrade, block, inject, and log various types of Internet traffic, in other words, they can analyze each packet in order to see what you are doing online.
According to a new report by Citizen Lab, Turkey's Telecom network was using Sandvine PacketLogic devices to redirect hundreds of targeted users (journalists, lawyers, and human rights defenders) to malicious versions of legitimate programs bundled with FinFisher and StrongPity spyware, when they tried to download them from official sources.
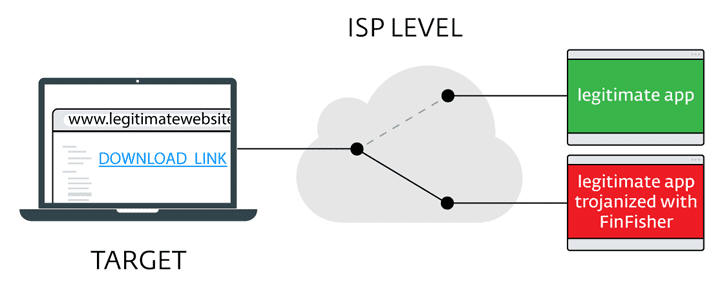
"This redirection was possible because official websites for these programs, even though they might have supported HTTPS, directed users to non-HTTPS downloads by default," the report reads.
A similar campaign has been spotted in Syria, where Internet users were silently redirected to malicious versions of the various popular application, including Avast Antivirus, CCleaner, Opera, and 7-Zip applications bundled with government spyware.
In Turkey, Sandvine PacketLogic devices were being used to block websites like Wikipedia, the sites of the Dutch Broadcast Foundation (NOS) and Kurdistan Workers' Party (PKK).
ISPs Injected Cryptocurrency Mining Scripts Into Users' Web Browsers

However, in Egypt, Sandvine PacketLogic devices were being used by a Telecom operator for making money by:
Secretly injecting a cryptocurrency mining script into every HTTP web page users visited in order to mine the Monero cryptocurrency,
Redirecting Egyptian users to web pages with affiliate ads.
In Egypt, these devices were also being used to block access to human rights, political, and news outlets like Al Jazeera, HuffPost Arabic, Reporters Without Borders, and Mada Masr, as well as NGOs like Human Rights Watch.
Citizen Lab researchers reported Sandvine of their findings, but the company called their report "false, misleading, and wrong," and also demanded them to return the second-hand PacketLogic device they used to confirm attribution of their fingerprint.
Citizen Lab started this investigation in September last year after ESET researchers published a report revealing that the downloads of several popular apps were reportedly compromised at the ISP level in two (unnamed) countries to distribute the FinFisher spyware.
Over 15,000 Memcached DDoS Attacks Hit 7,100 Sites in Last 10 Days
10.3.2018 thehackernews Attack
Memcached reflections that recently fueled two most largest amplification DDoS attacks in the history have also helped other cybercriminals launch nearly 15,000 cyber attacks against 7,131 unique targets in last ten days, a new report revealed.
Chinese Qihoo 360's Netlab, whose global DDoS monitoring service 'DDosMon' initially spotted the Memcached-based DDoS attacks, has published a blog post detailing some new statistics about the victims and sources of these attacks.
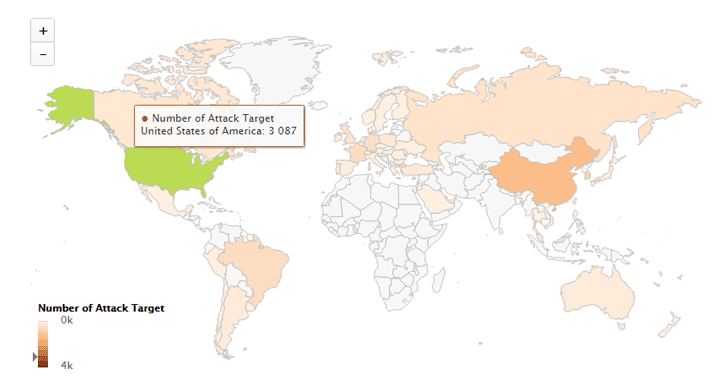
The list of famous online services and websites which were hit by massive DDoS attacks since 24th February includes Google, Amazon, QQ.com, 360.com, PlayStation, OVH Hosting, VirusTotal, Comodo, GitHub (1.35 Tbps attack), Royal Bank, Minecraft and RockStar games, Avast, Kaspersky, PornHub, Epoch Times newspaper, and Pinterest.
Overall, the victims are mainly based in the United States, China, Hong Kong, South Korea, Brazil, France, Germany, the United Kingdom, Canada, and the Netherlands.
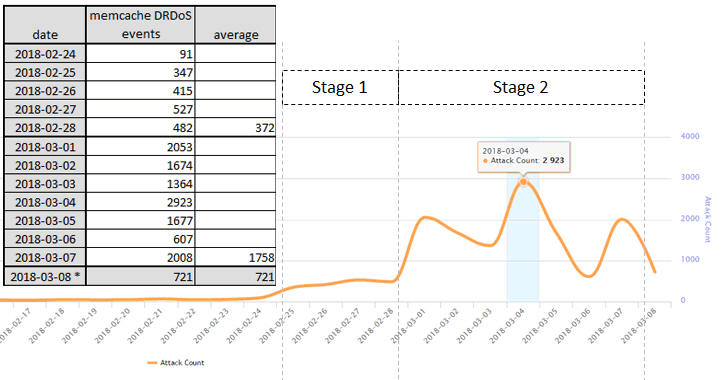
According to Netlab researchers, the frequency of attacks since 24th February has increased dramatically, as listed below:
Before 24th February, the day when Memcached-based DDoS attacks were first spotted, the daily average was less than 50 attacks.
Between 24th and 28th February, when Memcached as a new amplification attack vector was not publicly disclosed and known to a small group of people, the attacks raised to an average of 372 attacks per day.
Soon after the first public report came on 27th February, between 1st and 8th March, the total number of attacks jumped to 13,027, with an average of 1,628 DDoS attack events per day.
Netlab's 360 0kee team initially discovered the Memcached vulnerability in June 2017 and disclosed (presentation) it in November 2017 at a conference, but its researchers have hardly seen any Memcache DDoS attacks since then.
The maximum number of active vulnerable Memcached servers at a time that participated in the DRDoS attacks was 20,612.
I don't want to exaggerate this but expect hundreds of thousands of Memcached-based DDoS attacks in coming days, as hackers and researchers have now released multiple easy-to-execute exploits that could allow anyone to launch Memcached amplification attacks.
However, researchers have also discovered a 'kill-switch' technique that could help victims mitigate Memcached DDoS attacks efficiently.
Despite multiple warnings, over 12,000 vulnerable Memcached servers with UDP support enabled are still exposed on the Internet, which could fuel more cyber attacks.
Therefore, server administrators are strongly advised to install the latest Memcached 1.5.6 version which disables UDP protocol by default to prevent amplification/reflection DDoS attacks.
Windows 10 'S Mode' Coming Soon — For Security and Performance
10.3.2018 thehackernews Security

Microsoft has confirmed that the company is planning to convert Windows 10 S from a dedicated operating system to a special "S Mode" that will be available in all versions of Windows.
Windows 10 S, a new operating system designed for simplicity, security, and speed, was released by Microsoft last year. It locks a computer down to run applications only downloaded from official Windows Store, but the slimmed-down and restricted flavor of Windows did not exactly turn out to be a success.
Therefore, the company has now decided Windows 10 S be offered as an optional mode rather than a dedicated operating system.
Windows 10 S was developed to simplify administration for school or business sysadmins that want the 'low-hassle' guaranteed performance version. It has been designed to deliver predictable performance and quality through Microsoft-verified apps via the Microsoft Store.
However, in a blog post published Wednesday, the corporate VP of Microsoft's operating systems group, Joe Belfiore admitted that the naming for Windows 10 S "was a bit confusing for both customers and partners."
Microsoft, therefore, decided that the original version of Windows 10 S would disappear and become an S Mode in Windows.
"Starting with the next update to Windows 10, coming soon, customers can choose to buy a new Windows 10 Home or Windows 10 Pro PC with S mode enabled, and commercial customers will be able to deploy Windows 10 Enterprise with S mode enabled," Belfiore said.
"We expect the majority of customers to enjoy the benefits of Windows 10 in S mode," he added.
Previous rumors also suggested that Windows 10 Pro customers with S Mode enabled on their devices would have to pay $49 to disable the mode to get access to a full version of Windows 10 Pro, but these rumors were inaccurate.
No user, be it a Windows 10 Home, Enterprise, and Pro customer, has to pay anything to disable the S Mode, as Belfiore wrote that "if a customer does want to switch out of S mode, they will be able to do so at no charge, regardless of edition."
"We hope this new approach will simplify and make it possible for more customers to start using Windows in S mode: a familiar, productive Windows experience that is streamlined for security and performance across all our editions," Belfiore said.
S Mode is expected to with the next major Windows 10 update, thought to be called the Spring Creators Update, likely to arrive next month, and it is now up to PC makers to choose whether to enable the new S Mode or not.
New Cryptocurrency Mining Malware Infected Over 500,000 PCs in Just Few Hours
10.3.2018 thehackernews Cryptocurrency

Two days ago, Microsoft encountered a rapidly spreading cryptocurrency-mining malware that infected almost 500,000 computers within just 12 hours and successfully blocked it to a large extent.
Dubbed Dofoil, aka Smoke Loader, the malware was found dropping a cryptocurrency miner program as payload on infected Windows computers that mines Electroneum coins, yet another cryptocurrency, for attackers using victims' CPUs.
On March 6, Windows Defender suddenly detected more than 80,000 instances of several variants of Dofoil that raised the alarm at Microsoft Windows Defender research department, and within the next 12 hours, over 400,000 instances were recorded.
The research team found that all these instances, rapidly spreading across Russia, Turkey, and Ukraine, were carrying a digital coin-mining payload, which masqueraded as a legitimate Windows binary to evade detection.
However, Microsoft has not mentioned how these instances were delivered to such a massive audience at the first place in this short period.
Dofoil uses a customized mining application that can mine different cryptocurrencies, but in this campaign, the malware was programmed to mine Electroneum coins only.
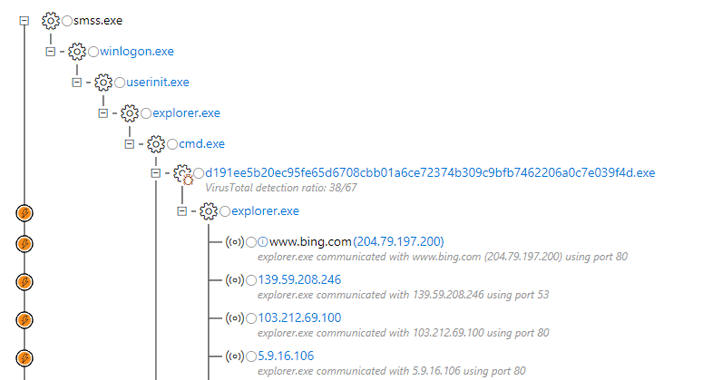
According to the researchers, Dofoil trojan uses an old code injection technique called 'process hollowing' that that involves spawning a new instance of a legitimate process with a malicious one so that the second code runs instead of the original, tricking process monitoring tools and antivirus into believing that the original process is running.
"The hollowed explorer.exe process then spins up a second malicious instance, which drops and runs a coin mining malware masquerading as a legitimate Windows binary, wuauclt.exe."
To stay persistence on an infected system for a long time to mine Electroneum coins using stolen computer resources, Dofoil trojan modifies the Windows registry.
"The hollowed explorer.exe process creates a copy of the original malware in the Roaming AppData folder and renames it to ditereah.exe," the researchers say. "It then creates a registry key or modifies an existing one to point to the newly created malware copy. In the sample we analyzed, the malware modified the OneDrive Run key."
Dofoil also connects to a remote command and control (C&C) server hosted on decentralized Namecoin network infrastructure and listens for new commands, including the installation of additional malware.
Microsoft says behavior monitoring and Artificial intelligence based machine learning techniques used by Windows Defender Antivirus have played an important role to detect and block this massive malware campaign.
První DDoS útok z IPv6. Na obzoru jsou další
10.3.2018 SecurityWorld Počítačový útok
Poprvé na servery udeřil distribuovaný DoS útok pocházející z protokolu IPv6. Pocházel z více než 1 600 IPv6 adres rozprostřených na 650 různých sítí.
Slovníkový DNS útok proběhl na servery společnosti Neustar, která se věnuje například analytice a zároveň je také správcem některých internetových domén ve Spojených státech, popisuje server SC Magazine, který zprávu o útoku přinesl.
Distribuovaný útok ukázal, že hackeři využívají nové metody k vykonání IPv6 útoků a nejde o pouhou replikaci útoků IPv4 s použitím protokolů IPv6, věří Neustar.
„Už jsme něco podobného chvíli očekávali a nyní je to tu. Viděli jsme také v letošním roce nárůst IPv4 útoků – je téměř dvojnásobný oproti stejnému období v roce 2017 – ale IPv6 útoky přicházejí s novými problémy, které není snadné vyřešit. Jeden příklad za všechny je obrovské množství dostupných adres dostupných útočníkovi, které mohou přehltit paměť moderních bezpečnostních zařízení,“ popsal serveru SC Magazine šéf vývoje a výzkumu Neustaru Barrett Lyon.
Celkové množství adres IPv6 je nepředstavitelně vysoké – je jich 7.9x1028vícekrát než u IPv4. Stárnoucí protokol IPv4 poskytuje přibližně 4,3 miliardy 32bitových adres. Vlivem obrovského množství IPv6 adres je možný podstatně větší útok, a protože mnohé nové sítě mohou IPv6 podporovat, ale bezpečnostní nástroje zatím ne, představuje to pro útočníky lákavý cíl s vysokým potenciálem.
Wesley George, hlavní inženýr síťového zabezpečení Neustaru sdělil SC Magazinu: „Je to velká výzva, ale v posledních letech se věci posunuly dál. Dobré bezpečnostní rady už existují a je jasné, že protokol IPv6 je nutné vnímat jako velmi důležitý. V mnoha případech je problém ve viditelnosti – máme společnosti se skvělou telemetrií pro IPv4, a to samé se musí přesunout i k IPv6.“
UltraDNS služba Neustaru je odpovědná za 10 % veškerého internetového provozu, mezi zákazníky patří Tesco, Forbes nebo NetRefer. Z žebříčku Alexa Top 1000 webů je momentálně 26,9 % navštívitelných pomocí protokolu IPv6.







