
COINHOARDER criminal gang made an estimated $50 million with a Bitcoin phishing campaign
19.2.2018 securityaffairs Phishing
Researchers with Cisco Talos have monitored a bitcoin phishing campaign conducted by a criminal gang tracked as Coinhoarder that made an estimated $50 million by exploiting Google AdWords.
Researchers with Cisco Talos have monitored a bitcoin phishing campaign for several months with the help of the Ukraine Cyberpolice.
The gang, tracked as Coinhoarder, has made an estimated $50 million by exploiting Google AdWords to trick netizens into visiting Bitcoin phishing sites. This is the element that characterized this phishing campaign, Coinhoarder attackers used geo-targeting filters for their ads, the researchers noticed that hackers were targeting mostly Bitcoin owners in Africa.
The Ukrainian authorities located and shut down the servers hosting some of the phishing websites used by crooks. The phishing sites were hosted on the servers of a bulletproof hosting provider located in Ukraine, Highload Systems. The operation was temporarily disrupted but the police haven’t arrested any individual.
“Cisco has been tracking a bitcoin theft campaign for over 6 months. The campaign was discovered internally and researched with the aid of an intelligence sharing partnership with Ukraine Cyberpolice. The campaign was very simple and after initial setup the attackers needed only to continue purchasing Google AdWords to ensure a steady stream of victims.” reads the analysis published by Talos. “This campaign targeted specific geographic regions and allowed the attackers to amass millions in revenue through the theft of cryptocurrency from victims.”
The Coinhoarder group used Google Adwords for black SEO purposes, on February 24, 2017, researchers at Cisco observed a massive phishing campaign hosted in Ukraine targeting the popular Bitcoin wallet site blockchain.info with over 200,000 client queries. Crooks used Google Adwords to poison user search results in order to steal users’ wallets.
Unfortunately, this attack scheme is becoming quite common in the criminal ecosystem, hackers implement it to target many different crypto wallets and exchanges via malicious ads.
The COINHOARDER gang leveraged the typosquatting technique, the hackers used domains imitating the Blockchain.info Bitcoin wallet service in conjunction SSL signed phishing sites in order to appear as legitimate. Based on the number of queries, the researchers confirmed that this is one of the biggest campaigns targeting Blockchain.info to date.
“The COINHOARDER group has made heavy use of typosquatting and brand spoofing in conjunction SSL signed phishing sites in order to appear convincing. We have also observed the threat actors using internationalized domain names.” continues the analysis. “These domains are used in what are called homograph attacks, where an international letter or symbol looks very similar to one in English. Here are some examples from this campaign.
The Punycode (internationalized) version is on the left, the translated (homographic) version on the right:
xn–blockchan-d5a[.]com → blockchaìn[.]com
xn–blokchan-i2a[.]info → blokchaín[.]info”
Talos researchers revealed that one campaign that was conducted between September and December 2017, the group made around $10 million.
“While working with Ukraine law enforcement, we were able to identify the attackers’ Bitcoin wallet addresses and thus, we could track their activity for the period of time between September 2017 to December 2017. In this period alone, we quantified around $10M was stolen.In one specific run, they made $2M within 3.5 week period. ” states Cisco Talos.
Further technical details on the campaign, including Indicators of Compromise are included in the analysis published by Cisco Talos.
Germany’s defense minister: Cyber security is going to be the main focus of this decade.
19.2.2018 securityaffairs BigBrothers
On Saturday, Germany defense minister Ursula von der Leyen told CNBC that cyber attacks are the greatest challenge threatening global stability.
The cybersecurity is a pillar of modern states, the string of recent massive attacks including NotPetya and WannaCry is the demonstration that we are all potential targets.
Cyber attacks could hit governments, private companies and citizens in every time and from every where causing severe problems to the victims and huge financial losses. The cyber risk is directly linked to geopolitical, environmental, technological, and economic risks. A cyber attack could destabilize governments worldwide, it can get a business out of the business.
When journalists asked about the “single greatest threat to global stability,” to the German defense minister, she confirmed the disconcerting scenario.
“I think it’s the cyber threats because whatever adversaries you can think of and even if you talk about Daesh (the terrorist group) they use the cyber domain to fight against us.” Germany’s defense minister Ursula von der Leyen told CNBC.
Germany defense minister urges European states to invest in collective defense
“This decade will be the decade of improvement in cyber security and information ruling,” she added.

Governments and companies are already investing to improve the resilience to cyber attacks of their networks. The Germany defense minister also noticed that Governments are also working to improve their offensive cyber capabilities.
The US and UK are reportedly using cyber soldiers to fight the Islamic State.
The video interview is available at the following link:
https://www.cnbc.com/video/2018/02/17/cyber-threats-biggest-threat-to-stabililty-german-defense-minister-says.html
JenkinsMiner made $3.4 million in a few months by compromising Jenkins servers
19.2.2018 securityaffairs Hacking
Hacker Group Makes $3 Million by Installing Monero Miners on Jenkins Servers
A criminal organization has made $3.4 million by compromising Jenkins servers and installing a Monero cryptocurrency miner dubbed JenkinsMiner.
“The perpetrator, allegedly of Chinese origin, has been running the XMRig miner on many versions of Windows, and has already secured him over $3 million worth of Monero crypto-currency. As if that wasn’t enough though, he has now upped his game by targeting the powerful Jenkins CI server, giving him the capacity to generate even more coins.” states a blog post published by CheckPoint.
Jenkins is the most popular open source automation server, it is maintained by CloudBees and the Jenkins community.
The automation server supports developers build, test and deploy their applications, it has more than 133,000 active installations worldwide with more than 1 million users.

According to the researchers, threat actors behind the massive mining operation were leveraging the CVE-2017-1000353 RCE vulnerability in the Jenkins Java deserialization implementation.
The vulnerability is due to lack of validation of the serialized object, its exploitation allowed the attackers to make Jenkins servers download and install the JenkinsMiner.
“The operation uses a hybridization of a Remote Access Trojan (RAT) and XMRig miner over the past months to target victims around the globe. The miner is capable of running on many platforms and Windows versions, and it seems like most of the victims so far are personal computers. With every campaign, the malware has gone through several updates and the mining pool used to transfer the profits is also changed.” continues the post.
Most of the downloads for the JenkinsMiner are from IP address located in China and assigned to the Huaian government information center, of course, we are not able to determine if the server was compromised or explicitly used by state-sponsored hackers.

Further details and IoCs are included in the analysis published by CheckPoint.
In January, security expert Mikail Tunç analyzed Jenkins servers exposed online discovering that many instances leak sensitive information.
Tunç highlighted that Jenkins typically requires credentials to the code repository and access to an environment in which to deploy the code, usually GitHub, AWS, and Azure. Failure to configure the application correctly can expose data to serious risk.
The researcher discovered that many misconfigured systems provided guest or administrator permissions by default, while others allowed guest or admin access to anyone who registered an account.
Oracle to Acquire Cloud Security Firm Zenedge
17.2.2018 securityweek IT
Oracle said Thursday that it has agreed to acquire cloud security firm Zenedge for an undisclosed sum.
Zenedge offers a suite of services to protect systems deployed in the cloud, on-premise or in hybrid hosting environments, with solutions including a Web Application Firewall (WAF), Distributed Denial of Service (DDoS) protection, and products to secure applications, networks, databases and APIs from attacks. Additionally, the company provides outsourced security monitoring and mitigating attacks
Powered by artificial intelligence (AI), Zenedge's products and 24/7 virtual Security Operations Center (SOC) defend over 800,000 web properties and networks globally.
Oracle says the acquisition of Zenedge expands Oracle Cloud Infrastructure and Oracle's Domain Name System (DNS) capabilities, adding application and network protection that augments existing Oracle security services and partnerships.
“The combination with Zenedge equips Oracle Cloud Infrastructure with integrated, next-generation network and infrastructure security, to address modern security threats,” claims Don Johnson, Senior Vice President of Product Development, Oracle.
According to Crunchbase, Zenedge has raised approximately $13.7 million in funding.
In September 2016, Oracle announced its acquisition of Cloud Access Security Broker (CASB) firm Palerra for an undisclosed sum, followed by an acquisition of Web traffic management firm Dyn in late 2016.
Global Powers Must Address 'Episodes of Cyberwar': UN Chief
17.2.2018 securityweek BigBrothers
World leaders must lay the groundwork on how countries respond to cyberattacks that have proven to be a daunting threat, whether by state actors or criminal enterprises, UN secretary general Antonio Guterres said Friday.
"It is clear we are witnessing in a more or less disguised way cyberwars between states, episodes of cyberwar between states," Guterres said during one of the opening speeches at the Munich Security Conference.
"It's high time to have a serious discussion about the international legal framework in which cyberwars take place," he said.
"The fact is we haven't been able to discuss whether or not the Geneva convention applies to cyberwar and whether international humanitarian law applies to cyberwar."
The United States and Britain on Thursday blamed the Russian military for last year's devastating "NotPetya" ransomware attack, calling it a Kremlin effort to destabilise Ukraine, which spun out of control.
The attacks ended up crippling computer networks in the United States and Europe, including those of some big companies.
Washington has also blamed North Korea for the huge "WannaCry" ransomware attack last May in which more than 300,000 computers were struck in some 150 nations.
"How to respond in cases of permanent violations of cybersecurity? What are the different uses that criminal, terror organisations are making of the web?" Guterres said.
Finding a consensus on how to respond to such attacks is urgent, he said, "especially now that artificial intelligence, that is providing enormous potential for economic development, social development, for the well-being of all, is also in the opinion of many an existential threat for humankind."
"It is necessary to bring together governments, the private sector, those involved in civil society, academics, research centres, in order to be able to establish at least some basic protocols to allow the web to be an effective instrument for the good," he said.
Unknown hackers stole $6 million from a Russian bank via SWIFT system last year
17.2.2018 securityaffairs Hacking
A new attack against the SWIFT system made the headlines again, unknown hackers have stolen 339.5 million roubles (roughly $6 million) from a Russian bank last year.
The news of the attack against the international payments messaging system was reported on Friday by the Russian central bank, this is the last incident of a long string of cyber heists.
“The volume of unsanctioned operations as a result of this attack amounted to 339.5 million roubles,” states the Russian central bank.
“The central bank said it had been sent information about “one successful attack on the work place of a SWIFT system operator.” reported the Reuters agency.
According to a spokesman for the central bank, hackers took control of a computer at a Russian bank and transferred the money to an account they controlled through the payment messaging system.
The spokesman did not provide details about the attack, he quoted Artem Sychev, deputy head of the central bank’s security department, as saying the hackers implemented “a common scheme”.
“When a case of potential fraud is reported to us, we offer our assistance to the affected user to help secure its environment,” said Natasha de Teran, a spokeswoman for SWIFT.
SWIFT highlighted that its “own systems” have never been compromised by attackers in past attacks.
“Brussels-based SWIFT said late last year digital heists were becoming increasingly prominent as hackers use more sophisticated tools and techniques to launch new attacks.” continues the Reuters.
This isn’t the only cyber attacks against a Russian bank that attempted to steal money through the SWIFT system, in December, hackers tried to steal 55 million roubles from Russian state bank Globex.
The string of attacks began with the cyber attack against Bangladesh Bank in February 2016 that resulted in the theft of $81 million.
Even if the SWIFT hasn’t revealed the exact number of victims of the SWIFT hackers, details on some attacks were revealed, such as the attack on Taiwan’s Far Eastern International Bank.
119,000 Scanned IDs of FedEx-owned company Bongo International’s customers exposed online
17.2.2018 securityaffairs Incindent
Researchers discovered an Amazon S3 bucket contains personal information and scans of IDs of some 119,000 US and international citizens.
It has happened again, researchers discovered another unsecured Amazon S3 bucket holding a huge trove of data that was exposed online. The Amazon S3 bucket contains personal information and scans of IDs of some 119,000 US and international citizens, the discovered was made once again by Kromtech security experts earlier this month.
The data belongs to the FedEx-owned company Bongo International that provides support the online sales of North American retailers and brands to consumers in abroad. Bongo was acquired in 2014 by FedEx and was operating with the name FedEx Cross-Border International until it went out of the business in April 2017.
The AWS bucket contained more than 112,000 files, unencrypted information and ID scans of customers from many countries, including the US, Mexico, Canada, various EU countries, Saudi Arabia, Kuwait, Japan, Malaysia, China, Australia.
“Among other stuff, it contained more than 119 thousands of scanned documents of US and international citizens, such as passports, driving licenses, security IDs etc. IDs were accompanied by scanned “Applications for Delivery of Mail Through Agent” forms (PS Form 1583) – which also contained names, home addresses, phone numbers and zip codes.” reads the blog post published by the company.
ZDNet analyzed the documents and found scans of drivers’ licenses, national ID cards, work ID cards, voting cards, utility bills, vehicle registration forms, medical insurance cards, firearms licences, US military identification cards, and credit cards that customers used to verify their identity with the FedEx division.
“Among the exposed files, ZDNet confirmed drivers’ licenses, national ID cards, and work ID cards, voting cards, and utility bills. We also found resumes, vehicle registration forms, medical insurance cards, firearms licences, a few US military identification cards, and even a handful of credit cards that customers used to verify their identity with the FedEx division.” wrote Zack Whittaker on ZDNet.
“One identity card, when we checked, revealed the details of a senior official at the Netherlands’ Ministry of Defense.”
It seems that the Amazon S3 bucket includes data related to anybody who used Bongo International services between 2009 and 2012 and the bad news is that it has been available for public access for many years. As said, FexEx bought the company in 2014, it is likely it was not aware of the data leak at the time of the acquisition.
Amazon S3 bucket
Kromtech tried to contact FedEx without success, the company removed the S3 bucket only after its existence was publicly disclosed.
“After a preliminary investigation, we can confirm that some archived Bongo International account information located on a server hosted by a third-party, public cloud provider is secure,” said FedEx spokesperson Jim McCluskey. “The data was part of a service that was discontinued after our acquisition of Bongo. We have found no indication that any information has been misappropriated and will continue our investigation.”
In October 2017, the Kromtech Security Center released a free scan tool that could allow admins to identify and secure Amazon S3 Buckets belonging to their organizations.
Let me suggest reading the guide published by the company to explain how to secure Amazon S3 buckets.
Oracle WebLogic Server Flaw Exploited to Deliver Crypto-Miners
16.2.2018 securityweek Vulnerebility Exploit CoinMine
Threat actors are exploiting a recently patched vulnerability in Oracle WebLogic Server to infect systems with crypto-currency mining malware, FireEye reports.
Identified as CVE-2017-10271, the vulnerability resides in the WebLogic Server Security Service (WLS Security) in Oracle WebLogic Server versions 12.2.1.2.0 and older, and was addressed by Oracle it its October 2017 Critical Patch Update (CPU).
After proof-of-concept code exploiting the bug was made public in December, activity associated with the exploitation of this vulnerability increased in volume, FireEye's researchers say. Successful exploitation of the flaw on unpatched systems allows attackers to remotely execute arbitrary code.
“We saw evidence of organizations located in various countries – including the United States, Australia, Hong Kong, United Kingdom, India, Malaysia, and Spain, as well as those from nearly every industry vertical – being impacted by this activity,” FireEye reported.
The crypto-currency market boomed recently, and cybercriminals have not been shy in their attempts to take advantage of the market. However, actors involved in crypto-currency mining operations don’t normally target specific organizations, but rather launch attacks that are opportunistic in nature.
Attackers abusing CVE-2017-10271 to infect targeted systems with crypto-miners used various tactics to achieve their purpose, the researchers discovered. Some of the incidents, for example, used PowerShell to drop the miner directly onto the victim’s system and leveraged ShellExecute() for execution.
In other attacks, PowerShell scripts were used to deliver the miner, instead of downloading the executable directly. In addition to downloading the miner, the script would also attempt to achieve persistence through scheduled tasks.
The script would delete the tasks created by other crypto-miners and would kill processes associated with those programs, in addition to being able to connect to mining pools with wallet key. It would also limit CPU usage to avoid suspicion.
Tactics employed in other attacks also involved the use of tools such as Mimikatz and EternalBlue for lateral movement across Windows environments.
The malware would first determine whether the system is 32-bit or 64-bit, to fetch a specific PowerShell script from the command and control (C&C) server. Next, it checks all network adapters and attempts to connect to every system in the network using extracted credentials, to run a PowerShell to drop and run the malware on the targeted system.
The malware uses WMI (Windows Management Instrumentation) for persistence and can perform a Pass-the-Hash attack using NTLM information derived from Mimikatz, to download and execute the malware on remote machines. It sends the stolen credentials to a remote server using an HTTP GET request.
If it fails moving laterally, the malware uses the PingCastle MS17-010 scanner to determine whether the target is vulnerable to EternalBlue.
In scenarios targeting Linux machines, the vulnerability would be exploited to deliver shell scripts that include functionality similar to that of PowerShell scripts. They would attempt to kill already running crypto-miners and then download and execute the malware, in addition to creating a cron job to maintain persistence.
“Use of cryptocurrency mining malware is a popular tactic leveraged by financially-motivated cyber criminals to make money from victims. We’ve observed one threat actor mining around 1 XMR/day, demonstrating the potential profitability and reason behind the recent rise in such attacks,” FireEye says.
Although they might be seen as less risky when compared to ransomware operations, crypto-currency mining malware does pose a variety of risks. Systems infected with crypto-miners might experience slowed performance, but such operations could also be hiding additional malware.
U.S. Energy Department Announces Office for Cyber, Energy Security
16.2.2018 securityweek BigBrothers
The U.S. Department of Energy announced this week that it’s creating a new Office of Cybersecurity, Energy Security, and Emergency Response (CESER).
The new office will be led by an assistant secretary who will report to the undersecretary of energy. The role of the assistant secretary will be to focus on energy infrastructure security and support the DoE’s expanded national security responsibilities.
The CESER office will help the DoE efficiently coordinate preparedness and response to both manmade and natural threats.U.S. Department of Energy launches Office of Cybersecurity, Energy Security, and Emergency Response
“DOE plays a vital role in protecting our nation’s energy infrastructure from cyber threats, physical attack and natural disaster, and as Secretary, I have no higher priority,” said U.S. Secretary of Energy Rick Perry. “This new office best positions the Department to address the emerging threats of tomorrow while protecting the reliable flow of energy to Americans today.”
U.S. President Donald Trump has proposed a budget of $30.6 billion for the DoE, including $96 million allocated for bolstering the department’s cybersecurity and energy security efforts. Overall, the current administration wants to invest $80 billion in IT and cybersecurity, which represents a 5.2 percent increase compared to the previous fiscal year.
Energy facilities in the United States and the Energy Department itself have often been targeted by malicious hackers in the past years.
In response to the increasing threat, the DoE announced a few months ago its intention to invest more than $20 million in cybersecurity, including tools and technologies for enhancing cybersecurity, communication systems for resilient grid architectures, energy delivery systems that can adapt to survive a cyber incident, partnerships for vulnerability mitigation, and identifying energy delivery systems that are inadvertently accessible from the Web.
U.S. Government Contractors Score Poorly on Cyber Risk Tests
16.2.2018 securityweek BigBrothers
Report Analyzes Cyber Risk of Federal Supply Chain
Attacks against the supply chain are not uncommon. It represents the soft underbelly of large organizations that are otherwise well defended. The federal government is not an exception -- in fact, federal agencies are especially reliant on their supply chain; and the security posture of that supply chain is of national importance.
This importance is not unrecognized. The May 2017 presidential Executive Order specified that the supply chain be included in security improvements: it called for a report, "on cybersecurity risks facing the defense industrial base, including its supply chain, and United States military platforms, systems, networks, and capabilities, and recommendations for mitigating these risks."
BitSight this week published an analysis of the security posture of the federal supply chain following the executive order. BitSight is a firm that examines and rates companies' security posture by analyzing visible evidence. It sees indicators of compromise, infected machines, improper configuration, poor security hygiene and potentially harmful user behaviors. From such evidence, it is able to see and compare different organizations. It concludes that the federal supply chain continues to provide a soft underbelly for attacks against federal agencies.
While federal agencies are improving their own security stance, their supply chain is lagging. For its analysis, BitSight researchers took a random sample of over 1,200 U.S. federal government contractors across a range of sectors, and compared the results with the performance of over 120 U.S. federal agencies.
It found a mean performance gap of at least 15 points between the agencies and their contractors. BitSight's ratings are calculated on a scale of 250-900, where a higher score reflects a stronger security posture. "There is a significant gap between the security performance of U.S. federal agencies and their contractors," concludes the analysis. "The mean rating for agencies as of January 2018 was 725. This is markedly higher than any of the other sector of contractors for the U.S. federal government observed in this study."
This mean rating disguises some concerning specifics. For example, nearly one in five users at Technology and Aerospace/Defense contractors have an outdated internet browser, making these employees and their organizations highly susceptible to new variants of malware. "High-profile vulnerabilities like Spectre can exploit outdated browsers as an attack to intercept or compromise data," warns BitSight. "Updating to the latest browser, operating system, or software package is critical to mitigating risks."
Individual risk vectors are graded on a scale from 'A' to 'F'. "Nearly 50% of contractors have a BitSight grade below C for the Protective Technology subcategory of the NIST Cybersecurity Framework," states the report. "This data suggests that many contractors are not implementing best practices for network security, encryption, and email security." Engineering was the worst performing sector in this area, with only 4% achieving an A rate. This compares to 38% of the federal agencies achieving an A grade (which is almost three times the average second-best rate of 13% for Business Services).
Botnet infections are another worrying area. It was highlighted in the Trump executive order, which demanded action "to improve the resilience of the internet and communications ecosystem and to encourage collaboration with the goal of dramatically reducing threats perpetrated by automated and distributed attacks (e.g., botnets)."
Here there is less difference between the agencies and their contractors -- in fact both the Business Services (80%) and Aerospace/Defense (74%) sectors achieved more A grades than the Federal Agencies (73%). However, only Aerospace/Defense equaled the agencies in the low number of F and D grades (both at 4%). In general, however, far more of the subcontractors scored B and below than did the agencies. For reference, BitSight claims, "an organization receiving a B or lower in this category is more than twice as likely to experience a data breach."
It goes on to suggest, "This data suggests that these organizations have ineffective security programs in place and may be experiencing ongoing data breaches."
Security of the supply chain is a problematic issue for all organizations. This BitSight reports suggests that it is a serious problem for federal agencies. “Tens of thousands of government contractors hold sensitive data or perform services on behalf of federal agencies," says Jacob Olcott, VP of Strategic Partnerships at BitSight. "The U.S. government must be focused on evaluating, monitoring and improving the cyber hygiene of these contractors. Recent contractor regulations, like the new DOD requirements, are a start, but are too focused on check-the-box compliance. Cyber is a dynamic risk. By leveraging objective data and continuously monitoring the supply chain, the federal government will better comprehend the danger within its own ecosystem and begin to meaningfully mitigate this risk.”
Cambridge, Mass.-based BitSight Technologies raised $40 million in a Series C funding round in September 2016, bringing the total raised to $95 million.
OpenSSL alpha adds TLS 1.3 support in the alpha version of OpenSSL 1.1.1
16.2.2018 securityaffairs Krypto
OpenSSL adds TLS 1.3 (Transport Layer Security) supports in the alpha version of OpenSSL 1.1.1 that was announced this week.
OpenSSL adds TLS 1.3 supports in the alpha version of OpenSSL 1.1.1 that was announced this week. TLS protocol was designed to allow client/server applications to communicate over the Internet in a secure way preventing message forgery, eavesdropping, and tampering.
“OpenSSL 1.1.1 is currently in alpha. OpenSSL 1.1.1 pre release 1 has now been made available.” states the OpenSSL’s announcement.
“This OpenSSL pre-release has been provided for testing ONLY. It should NOT be used for security critical purposes. The alpha release is available for download via HTTP and FTP from the following master locations (you can find the various FTP mirrors under https://www.openssl.org/source/mirror.html)”
The first Internet-Draft dates back to April 2014, in January it was presented the 23 and will expire on July 9, 2018.
One of the most debated problems when dealing with TLS is the role of so-called middleboxes, many companies need to inspect the traffic for security purposes and TLS 1.3 makes it very hard.
“The reductive answer to why TLS 1.3 hasn’t been deployed yet is middleboxes: network appliances designed to monitor and sometimes intercept HTTPS traffic inside corporate environments and mobile networks. Some of these middleboxes implemented TLS 1.2 incorrectly and now that’s blocking browsers from releasing TLS 1.3. However, simply blaming network appliance vendors would be disingenuous.” reads a blog post published by Cloudflare in December that explained the difficulties of mass deploying for the TLS 1.3.
According to the tests conducted by the IETF working group in December 2017, there was around a 3.25 percent failure rate of TLS 1.3 client connections.
TLS 1.3 will deprecate old cryptographic algorithms entirely, this is the best way to prevent the exploiting of vulnerabilities that affect the protocol and that can be mitigated only when users implement a correct configuration.
In the last few years, researchers discovered several critical issues in the protocol that have been exploited in attacks.
OpenSSL maintainers have completely redesigned the OpenSSL random number generator in the new version.
The new OpenSSL release also includes the implementation for SHA3 and multi-prime RSA, and the support for the SipHash set of pseudorandom functions.
BGP Flaws Patched in Quagga Routing Software
16.2.2018 securityweek Vulnerebility
Several vulnerabilities that could lead to denial-of-service (DoS), information disclosure, and remote code execution have been patched this week in the Quagga routing software suite.
Quagga implements the Open Shortest Path First (OSPF), Routing Information Protocol (RIP), Border Gateway Protocol (BGP) and Intermediate System to Intermediate System (IS-IS) protocols for Unix-like platforms, particularly Linux, Solaris, FreeBSD and NetBSD.
Quagga developers and the CERT Coordination Center (CERT/CC) at Carnegie Mellon University announced this week that Quagga 1.2.3 patches several vulnerabilities affecting the BGP daemon (bpgd).
One of the more serious flaws, rated critical by CERT/CC based on its CVSS score, is CVE-2018-5379, a double-free memory corruption issue related to the processing of certain UPDATE messages containing cluster-list or unknown attributes.
“This issue can be triggered by an optional/transitive UPDATE attribute, that all conforming eBGP speakers should pass along. This means this may triggerable in many affected Quagga bgpd processes across a wide area of a network, because of just one UPDATE message,” Quagga developers explained. “This issue could result in a crash of bgpd, or even allow a remote attacker to gain control of an affected bgpd process.”
Another vulnerability, CVE-2018-5381, can be exploited to cause bgpd to enter an infinite loop and stop responding until it’s restarted. “BGP sessions will drop and not be reestablished,” developers said.
Quagga 1.2.3 also patches CVE-2018-5378, a security hole that can lead to sensitive data from the bgpd process being sent over the network to a configured peer. This can also cause the bgpd process to crash.
The last vulnerability patched by the latest Quagga release is CVE-2018-5378, which developers say has “very low” impact.
Linux distributions, including Ubuntu, Debian and Red Hat, have started publishing advisories describing these vulnerabilities. Regarding CVE-2018-5379, Red Hat said “Glibc's heap protection mitigations render this issue more difficult to exploit, though bypasses may still be possible.”
A Single-Character Message Can Crash Any Apple iPhone, iPad Or Mac
16.2.2018 thehackernews Apple
Only a single character can crash your iPhone and block access to the Messaging app in iOS as well as popular apps like WhatsApp, Facebook Messenger, Outlook for iOS, and Gmail.
First spotted by Italian Blog Mobile World, a potentially new severe bug affects not only iPhones but also a wide range of Apple devices, including iPads, Macs and even Watch OS devices running the latest versions of their operating software.
Like previous 'text bomb' bug, the new flaw can easily be exploited by anyone, requiring users to send only a single character from Telugu—a native Indian language spoken by about 70 million people in the country.
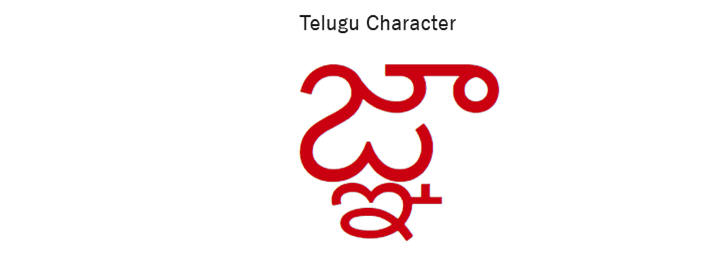
Once the recipient receives a simple message containing the symbol or typed that symbol into the text editor, the character immediately instigates crashes on iPhones, iPads, Macs, Apple Watches and Apple TVs running Apple's iOS Springboard.
Apps that receive the text bomb tries to load the character, but fails and refuses to function properly until the character is removed—which usually can be done by deleting the entire conversation.
iphone-crash-telugu-character
The easiest way to delete the offending message is by asking someone else to send a message to the app that is crashing due to the text bomb. This would allow you to jump directly into the notification and delete the entire thread containing the character.
The character can disable third-party apps like iMessage, Slack, Facebook Messenger, WhatsApp, Gmail, and Outlook for iOS, as well as Safari and Messages for the macOS versions.
Telegram and Skype users appear to be unaffected by the text bomb bug.
Apple was made aware of the text bomb bug at least three days ago, and the company plans to address the issue in an iOS update soon before the release of iOS 11.3 this spring.
The public beta version of iOS 11.3 is unaffected.
Since so many apps are affected by the new text bomb, bad people can use the bug to target Apple users via email or messaging or to create mass chaos by spamming the character across an open social platform.
U.S., Canada, Australia Attribute NotPetya Attack to Russia
16.2.2018 securityweek Ransomware
The United States, Canada, Australia and New Zealand have joined the United Kingdom in officially blaming Russia for the destructive NotPetya attack launched last summer. Moscow has denied the accusations.
In a statement released on Thursday, the White House attributed the June 2017 attack to the Russian military and described it as “the most destructive and costly cyber-attack in history.”
“The attack, dubbed ‘NotPetya,’ quickly spread worldwide, causing billions of dollars in damage across Europe, Asia, and the Americas,” the White House Press Secretary stated. “It was part of the Kremlin’s ongoing effort to destabilize Ukraine and demonstrates ever more clearly Russia’s involvement in the ongoing conflict. This was also a reckless and indiscriminate cyber-attack that will be met with international consequences.”
According to the Australian government, the conclusion that threat actors sponsored by Russia are responsible for the cyberattack was reached based on information from its domestic intelligence agencies and consultation with the U.S. and U.K.
“The Australian Government condemns Russia’s behaviour, which posed grave risks to the global economy, to government operations and services, to business activity and the safety and welfare of individuals,” stated Angus Taylor, Australia’s Minister for Law Enforcement and Cybersecurity. “The Australian Government is further strengthening its international partnerships through an International Cyber Engagement Strategy to deter and respond to the malevolent use of cyberspace.”
Canada’s Communications Security Establishment (CSE) also accused Russia of launching the NotPetya attack based on its own assessment.
“Canada condemns the use of the NotPetya malware to indiscriminately attack critical financial, energy, government, and infrastructure sectors around the world in June 2017,” said CSE Chief Greta Bossenmaier. “As previously stated, the Government of Canada continues to strongly oppose the use of cyberspace for reckless and destructive criminal activities. We remain committed to working with our allies and partners to maintain the open, reliable and secure use of cyber space.”
New Zealand’s Government Communications Security Bureau (GCSB) said that while the country was not directly targeted by NotPetya, the incident did cause disruption to some organizations that had rushed to update their systems after news of the attack broke.
New Zealand has joined the other Five Eyes countries in condemning the attack, but its statement suggests that its attribution of the incident to Russia is based solely on information provided by GCSB’s international partners.
British Foreign Office Minister for Cyber Security Lord Tariq Ahmad said Russia “showed a continued disregard for Ukrainian sovereignty” by launching the NotPetya attack.
Moscow has denied the accusations, describing them as unsubstantiated and groundless. “This is nothing more than the continuation of the Russophobic campaign lacking any evidence,” said Kremlin spokesman Dmitry Peskov.
The NotPetya malware (also known as PetrWrap, exPetr, GoldenEye and Diskcoder.C) affected tens of thousands of systems around the world. Researchers initially believed NotPetya was a piece of ransomware, but a closer analysis revealed that it was actually a destructive wiper.
Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain reported losing hundreds of millions of dollars due to the attack.
Last year, Five Eyes countries and Japan officially accused North Korea of launching the WannaCry attack.
'DoubleDoor' IoT Botnet Uses Two Backdoor Exploits
16.2.2018 securityweek BotNet
A newly discovered Internet of Things (IoT) botnet is using two exploits to ensure it can not only bypass authentication on targeted devices, but also render additional protections useless, NewSky Security has discovered.
Dubbed DoubleDoor, the botnet allows attackers to takeover devices even if the user has authentication enabled and has added a firewall for additional protection. Specifically, the malware abuses CVE-2015–7755, a Juniper Networks SmartScreen OS exploit, and CVE-2016–10401, a Zyxel modem backdoor exploit (also abused by the Hide ‘N Seek botnet).
What NewSky Security discovered was that the botnet first deploys the infamous Juniper Networks exploit, which essentially allows it to get past firewall authentication. The backdoor was initially discovered in the ScreenOS software running on NetScreen firewalls.
Through this backdoor, the telnet and SSH daemons of Netscreen firewalls become accessible with the hardcoded password <<< %s(un=’%s’) = %u and any username, regardless of whether a valid one or not. In the initial attack cycle of DoubleDoor, the attack was implemented using the username “netscreen,” NewSky's researchers say.
Next, the botnet attempts to deploy the backdoor for ZyXEL PK5001Z devices, which is pretty straight forward as well, using a hardcoded su password as zyad5001. This is a privilege escalation exploit, and the botnet’s operators were also observed performing a “password based attack to get a basic privilege account like admin:CenturyL1nk before going for the superuser,” the researchers say.
The DoubleDoor botnet was also observed performing reconnaissance to ensure the attack was successful and control of the IoT device was achieved.
“DoubleDoor botnet takes care of this, by using a randomized string in every attack. Lack of any standard string will make sure it is not very easy to classify the recon activity as malicious. The strings have one thing in common though, they are always 8 in length,” the security researchers note.
The botnet is currently in a nascent phase, with attacks observed only between Jan. 18 and Jan. 27, 2018. Most of the attacks were observed originating from South Korean IPs. The botnet’s attacks are expected to remain low, mainly because they are only effective if the victim runs a specific unpatched version of Juniper ScreenOS firewall and uses unpatched Zyxel modems.
“Double layer of IoT protection is more common in corporate environments, which don’t rely on built-in IoT authentication and like to protect it with another layer of firewall. Although such corporate devices can be lesser in number, getting control of corporate environment routers can be more valuable for an attacker as it can lead to targeted IoT attacks,” the researchers say.
Financial Regulator's Algorithm Compliance Concerns Are Relevant to All Businesses
16.2.2018 securityweek IT
The UK's financial regulator, the Financial Conduct Authority (FCA), issued a report Monday warning financial companies that it would be looking closely at so-called 'algo trading': "Algorithmic Trading Compliance in Wholesale Markets" (PDF).
Algo (or algorithmic) trading is the use of computer algorithms to buy or sell stock automatically and at speed if certain market conditions are met. The danger is that rapid trading by computers can change the market causing more buying or selling before human traders can intervene and correct the situation. Such algo trading has been blamed as partly responsible for this month's Wall Street sell-off that led to a 4% fall in Standard & Poor's 500-stock index last Monday -- the worst decline since August 2011.
David Murray, Corvil's chief marketing and business development officer, explains the problem. "It takes a person 300-400 milliseconds (thousandths of a second) to blink, and computers can execute a trade in 30-40 microseconds (millionths of a second) -- so it is clear that the new reality of time in an algorithmic world mandates new oversight and controls."
In its new report, compiled in the months preceding last week's Wall Street sell-off, the FCA warns, "In the absence of appropriate systems and controls, the increased speed and complexity of financial markets can turn otherwise manageable errors into extreme events with potentially wide-spread implications." Because of this, it adds, "We will continue to assess whether firms have taken sufficient steps to reduce risks arising from algorithmic trading."
Five key compliance areas are highlighted by the FCA: a full understanding and management of algorithms across the business; robust development and testing processes for algorithms; pre and post trade risk controls; an effective governance and oversight framework; and the ability to monitor for potential conduct issues and thereby reduce market abuse risks.
This isn't just about automated trading with the potential to wobble global financial markets -- it is also about localized and criminal abuse of algorithms. In November 2017, the FCA fined Paul Axel Walter -- subsequently known as 'algo-baiter' -- £60,090 for market abuse via algorithms. Walter was a senior bond trader, working at Bank of America Merrill Lynch (BAML). In 2014, he entered bids into the system that reflected the opposite of his intention. The algorithms reacted to his bids allowing him to subsequently enter his true bids into a market that he had manipulated.
But the issues go beyond just financial trading. "Similar conditions exist not only across global financial markets," explains Murray. "There are similar risks for other algorithmic businesses and use of artificial intelligence."
With the digitization and computer-based automation of all industry, the problems currently highlighted in the financial sector will become an issue for businesses generally. Actions will be triggered by and acted upon by unseen algorithms hidden within the system. It already happens within security products, where decisions can be made without anyone really understanding how or why they were reached. At the same time, outsiders will be able to manipulate the algorithms by feeding them false information, similar to Walter's manipulation of the trading algorithms.
The FCA's five principles for algo compliance are applicable far beyond just financial institutions. Compliance officers and security teams will need to understand their use of algorithms within machine learning and artificial intelligence systems to remain within compliance and defeat both internal and external malicious actors. Key, perhaps, is the second principle: robust development and testing processes. This is particularly relevant where a business develops its own algorithms -- as is common in the financial industry -- rather than relying, blindly, on externally developed algorithms.
Algorithm development is subject to the same pressures as any other software development -- the need to get it complete and operational as quickly as possible. The FCA warns against development procedures that focus on operational effectiveness without considering other issues. An example outside of finance could be automated customer or user profiling without considering the impact of the General Data Protection Regulation (GDPR). Article 22 states, "The data subject shall have the right not to be subject to a decision based solely on automated processing, including profiling, which produces legal effects concerning him or her or similarly significantly affects him or her."
The FCA's advice is good for all software development: "a culture of open communication between different business units, while having a clear separation of roles and independent reviews... by having a separate team that verifies and checks the output and quality of code."
As the algorithms get more complex, they get more difficult to control. "There's often a tradeoff between model or algorithm performance and complexity," explains Endgame's technical director of data science, Hyrum Anderson, "with higher performing models often requiring more model mass. Examples include: more trees in random forest or gradient boosting models, more layers in convolutional neural networks, etc. As a design principal, experienced machine learning researchers try to utilize the principle of Occam's razor -- when many models have similar performance, choose the simpler one."
But he also warns that while simplicity aids in human understanding and verification, and prevents models from making extreme predictions, it also potentially creates the best conditions for adversaries to fool them. While DevOps may be good for software development, DevSecOps would be better for algorithm development to ensure the most secure and reliable outcome.
A second of the FCA's five principles is also relevant to compliance and security teams beyond just the financial industry: the ability to monitor for potential conduct issues. Two aspects of this requirement are particularly relevant: network monitoring for signs of abuse or misuse; and algorithm testing standards and procedures.
The first will become increasingly challenging. Security teams already monitor their networks for anomalous events; but they use algorithms to do so. As algorithmic automation increases throughout industry, security teams will need to find monitoring methods to monitor even the algorithms they use for monitoring other aspects of the business. They will need to be able to detect malicious external actors attempting to subvert the algorithms, and insiders attempting to manipulate the algorithms. This is of course particularly concerning in the financial sector where entire markets, and potentially national economies, could be manipulated for criminal gain -- or individual company share prices manipulated in sophisticated versions of pump and dump schemes.
Corvil's Murray summarizes the problem. "To operate in today’s machine time environments and enable rapid, secure, compliant time to market, businesses require process controls as well as layered technology oversight to assure precision and accuracy of time stamping to establish sequencing, continuous capture and of all electronic business activity, real-time analysis of transactions, and anomaly detection for cyber and abuse surveillance."
Testing the veracity of algorithms will also be a problem. The third-party anti-malware testing industry is struggling to find methods of adequately and objectively testing algo-based endpoint protection systems. As companies begin to develop their own algorithms for their own automation purposes, testing will likely fall on the very people who developed the algorithms. Objectivity may be impossible, and testing may not be effective.
The FCA's algorithmic trading compliance report should be a clarion call for all businesses. The new and emerging world of artificial intelligence -- that is, algorithms -- promises huge benefits for industry in increased speeds and lower costs; just as it does in the financial markets. But whether industry generally has fully examined the security and compliance issues that algorithms bring with them is a separate but urgent question. Algorithmic Trading Compliance in Wholesale Markets is a good starting point.
Dispel Launches Election Security Platform
16.2.2018 securityweek Krypto
Dispel, a U.S.-based company that specializes in secure communication and collaboration systems, on Thursday announced the launch of a new product designed to help protect elections against malicious cyber actors.
According to Dispel, the new solution, which consists of its Election Cyber Defense System (ECDS) and a hardware device named ECDS Wicket, is capable of protecting the integrity of voter, ballot and campaign information. The company says its product can be easily installed even by a novice with only five minutes of training.
The election security platform is designed to automatically tunnel sensitive voting data and ensure that databases and networks cannot be located and attacked by malicious actors. The ECDS Wicket, which needs to be plugged into the reporting center computer, protects communications with two layers of AES-256 encryption with independent 4096-bit RSA keys for the initial exchange.
The device links the reporting center computer to a siloed dataroom where voting data is uploaded. Each dataroom is located in a network protected by Dispel’s Moving Target Defense technology. When the ECDS system is active, the reporting center computer can no longer transmit data to the Internet and can only communicate with election-related sites.
The platform has different systems that can help secure specific voting and campaign-related operations, including voter rolls, vote tabulation, and campaign communications.
For example, when voter rolls are changed, state officials connect with reporting officials through a secure video conferencing page to confirm the identity of the reporting official before granting them access to change the roll. Every change made to the roll is logged and stored in a secure location.
The tabulation system is designed to ensure that voting data is safely transmitted and stored. As for protecting campaign communications, Dispel provides what it calls the Campaign Comms Enclave, which includes secure video conferencing, telephony, messaging, file sharing, VPN, research stations, and logging capabilities for a flat fee of $2,500 per month, $7,500 per quarter, or $25,000 annually.
The voter roll and vote tabulation systems are priced based on the number of Wicket devices, voter rolls, access terminals, and reporting centers needed.
U.S. intelligence officials are convinced that Russia interfered in the 2016 presidential election and they have warned that it will likely attempt to meddle in this year’s midterm elections as well. Threat groups from Russia and other countries could try to interfere and experts warned recently that voting machines and other systems used in the election are vulnerable to hacker attacks.
Dispel told SecurityWeek that it has yet to make any deals with the U.S. government regarding the use of its product at the upcoming elections.
Democrats on Wednesday asked Congress for more than $1 billion in grants for boosting election security, and a product such as the one offered by Dispel could be taken into consideration for protecting votes.
Dispel is also offering its product to governments outside the U.S., but it has yet to actively promote it.
Russian Hackers Sent to U.S. Prison for Stealing 160 Million Bank Card Numbers
16.2.2018 securityweek BigBrothers
A United States Judge this week sent two Russian nationals to prison for their involvement in a hacking scheme that compromised roughly160 million credit card numbers and incurred losses of hundreds of millions.
The two, Vladimir Drinkman, 37, and Dmitriy Smilianets, 34, both of Moscow, were arrested in the Netherlands on June 28, 2012. Smilianets was extradited to the United States on Sept. 7, 2012, while Drinkman was extradited on Feb. 17, 2015.
Drinkman, who previously pleaded guilty before U.S. District Judge Jerome B. Simandle of the District of New Jersey, was sentenced to 144 months in prison. Smilianets, who pleaded guilty in September 2013, was sentenced to 51 months and 21 days in prison.
Drinkman and Smilianets, along with three co-defendants, were charged with hacking into the networks of organizations engaged in financial transactions, retailers operating with financial data, and other institutions with information of interest to the group.
The conspirators hacked the computer networks of NASDAQ, 7-Eleven, Carrefour, JCP, Hannaford, Heartland, Wet Seal, Commidea, Dexia, JetBlue, Dow Jones, Euronet, Visa Jordan, Global Payment, Diners Singapore and Ingenicard, court documents and statements show.
Each of the five defendants played a specific role in the scheme, with Drinkman penetrating network security, gaining access to the corporate victims’ systems, and harvesting valuable data from the compromised networks. Smilianets would sell the stolen data and distribute the proceeds of the scheme to the participants.
The other three co-defendants, namely Alexandr Kalinin, 31, of St. Petersburg, Russia, Roman Kotov, 36, of Moscow, Russia, and Mikhail Rytikov, 30, of Odessa, Ukraine, are fugitives.
The hackers targeted the computer networks of corporate victims to steal information such as user names and passwords, means of identification, credit and debit card numbers, and other personal identification information of cardholders.
The group used SQL injection attacks to penetrate the victims’ networks. The hackers targeted vulnerabilities in SQL (Structured Query Language) databases for initial access, then installed malware on the system to create a backdoor and help them maintain access to the network. They would sometime assault a victim network for months before being able to bypass security.
“The defendants used their access to the networks to install ‘sniffers’, which were programs designed to identify, collect and steal data from the victims’ computer networks. The defendants then used an array of computers located around the world to store the stolen data and ultimately sell it to others,” a Department of Justice announcement reads.
The stolen data was sold through online forums or directly to individuals and organizations for around $10 for a stolen American credit card number and associated data, $50 for a European credit card number and associated data, and $15 for a Canadian credit card number and associated data.
Their customers would encode such data onto the magnetic strip of a blank plastic card and use it to withdraw money from ATMs or make purchases.
To conceal the scheme, the five defendants used various methods, starting with the use of anonymous web-hosting services provided by Rytikov. They also used private and encrypted communication channels and also attempted to evade protections by security software, in addition to modifying settings on victim networks to disable the logging of their actions.
“As a result of the scheme, financial institutions, credit card companies and consumers suffered hundreds of millions in losses – including more than $300 million in losses reported by just three of the corporate victims – and immeasurable losses to the identity theft victims in costs associated with stolen identities and false charges,” DoJ says.
In addition to prison terms, Drinkman and Smilianets were also sentenced to three years of supervised release.
DELL EMC addressed two critical flaws in VMAX enterprise storage systems
16.2.2018 securityaffairs Vulnerebility
Dell EMC addressed two critical vulnerabilities that affect the management interfaces for its VMAX enterprise storage systems.
The Dell EMC’s VMAX Virtual Appliance (vApp) Manager is an essential component of a wide range of the enterprise storage systems.
The first flaw tracked as CVE-2018-1215 is an arbitrary file upload vulnerability that could be exploited by a remote authenticated attacker to potentially upload arbitrary maliciously crafted files in any location on the web server. The flaw received a Common Vulnerability Scoring System (CVSS) base score of 8.8.
“Arbitrary file upload vulnerability A remote authenticated malicious user may potentially upload arbitrary maliciously crafted files in any location on the web server. By chaining this vulnerability with CVE-2018-1216, the attacker may use the default account to exploit this vulnerability.” reads the security advisory.
VMAX enterprise storage systems
The second flaw tracked as CVE-2018-1216 is an undocumented default account in the vApp Manager with a hard-coded password. The flaw received a Common Vulnerability Scoring System (CVSS) base score of 9.8.
“Hard-coded password vulnerability The vApp Manager contains an undocumented default account (ÒsmcÓ) with a hard-coded password that may be used with certain web servlets. A remote attacker with the knowledge of the hard-coded password and the message format may use vulnerable servlets to gain unauthorized access to the system. Note: This account cannot be used to log in via the web user interface.” continues the advisory.
The CVE-2018-1215 could be chained with a second flaw tracked as CVE-2018-1216 to use a hard-coded password to a default account to exploit this vulnerability.
“The vApp Manager which is embedded in Dell EMC Unisphere for VMAX, Dell EMC Solutions Enabler, Dell EMC VASA Virtual Appliances, and Dell EMC VMAX Embedded Management (eManagement) contains multiple security vulnerabilities that may potentially be exploited by malicious users to compromise the affected system.” states the security advisory issued by Dell EMC.
Affected products:
Dell EMC Unisphere for VMAX Virtual Appliance versions prior to 8.4.0.18
Dell EMC Solutions Enabler Virtual Appliance versions prior to 8.4.0.21
Dell EMC VASA Virtual Appliance versions prior to 8.4.0.514
Dell EMC VMAX Embedded Management (eManagement) versions prior to and including 1.4 (Enginuity Release 5977.1125.1125 and earlier)
Dell EMC has removed the default ÒsmcÓ account from new installs, but the company noticed that the account will not be removed after the upgrade of the vApp Manager application.
UK Foreign Office Minister blames Russia for NotPetya massive ransomware attack
16.2.2018 securityaffairs Ransomware
The United Kingdon’s Foreign and Commonwealth Office formally accuses the Russian cyber army of launching the massive NotPetya ransomware attack.
The UK Government formally accuses the Russian cyber army of launching the massive NotPetya ransomware attack.
The United Kingdon’s Foreign and Commonwealth Office “attributed the NotPetya cyber-attack to the Russian Government.”
According to the UK, NotPetya was used to disrupt Ukrainian “financial, energy and government sector” targets, but it went out of control causing severe damages to companies worldwide.

The shipping giant Maersk chair Jim Hagemann Snabe revealed its company reinstalled 45,000 PCs and 4,000 Servers after NotPetya the attack.
In August 2017 the company announced that it would incur hundreds of millions in U.S. dollar losses due to the ransomware massive attack.
The UK considers the attack an intolerable act and will not accept future similar offensives.
“Foreign Office Minister Lord Ahmad has today attributed the NotPetya cyber-attack to the Russian Government. The decision to publicly attribute this incident underlines the fact that the UK and its allies will not tolerate malicious cyber activity.” reads the official statement issued by the UK Government.
“The attack masqueraded as a criminal enterprise but its purpose was principally to disrupt. Primary targets were Ukrainian financial, energy and government sectors. Its indiscriminate design caused it to spread further, affecting other European and Russian business.”
Below the declaration of the Foreign Office Minister for Cyber Security Lord (Tariq) Ahmad of Wimbledon:
“The UK Government judges that the Russian Government, specifically the Russian military, was responsible for the destructive NotPetya cyber-attack of June 2017.
The attack showed a continued disregard for Ukrainian sovereignty. Its reckless release disrupted organisations across Europe costing hundreds of millions of pounds.
The Kremlin has positioned Russia in direct opposition to the West yet it doesn’t have to be that way. We call upon Russia to be the responsible member of the international community it claims to be rather then secretly trying to undermine it.
The United Kingdom is identifying, pursuing and responding to malicious cyber activity regardless of where it originates, imposing costs on those who would seek to do us harm. We are committed to strengthening coordinated international efforts to uphold a free, open, peaceful and secure cyberspace.”
According to Ukraine’s Secret Service (SBY), Russia orchestrated the NotPetya ransomware attack, going public with their accusations just days after the incident.
NotPetya wasn’t the last massive ransomware attack in order of time, in October Bad Rabbit
NotPetya was followed by the Bad Rabbit ransomware that in late October infected systems in many countries wordlwide, most of in East Europe, such as Ukraine and Russia.
Over $100,000 Paid Out in 'Hack the Air Force 2.0'
15.2.2018 securityweek Security
HackerOne on Thursday announced the results of a bug bounty challenge run by the U.S. Air Force on its platform. More than $100,000 were paid out for over 100 vulnerabilities reported during Hack the Air Force 2.0.
The challenge ran between December 9 and January 1. The U.S. Department of Defense paid out a total of $103,883 for 106 valid vulnerability reports submitted by 27 hackers from the U.S., Canada, U.K., Sweden, Netherlands, Belgium and Latvia.
The largest single payout, which is also the highest reward in any federal bug bounty program to date, was $12,500.
Of the 106 flaws, 55 were discovered on the first day of Hack the Air Force 2.0 during a live hacking event at the WeWork Fulton Center inside the Fulton Center subway station in New York City.Hack the Air Force 2.0
Seven U.S. Airmen and 25 civilians earned a total of over $26,000 on the first day, including $10,650 by Mathias Karlsson and Brett Buerhaus, who demonstrated how malicious actors could have breached an unclassified DoD network by exploiting a vulnerability in the Air Force’s website.
“We continue to harden our attack surfaces based on findings of the previous challenge and will add lessons learned from this round,” said Air Force CISO Peter Kim. “This reinforces the work the Air Force is already doing to strengthen cyber defenses and has created meaningful relationships with skilled researchers that will last for years to come.”
The first edition of Hack the Air Force paid out more than $130,000 for 207 valid vulnerability reports. The bug bounty challenges run by the Pentagon on the HackerOne platform since 2016 led to the discovery and patching of more than 3,000 vulnerabilities, with a total of over $400,000 awarded to white hat hackers.
The Pentagon also has a vulnerability disclosure policy that aims to provide guidance to researchers on how to disclose security holes found in the organization’s public-facing websites. While no monetary rewards are being offered, the policy provides a legal avenue for reporting flaws.
U.K. Officially Blames Russia for NotPetya Attack
15.2.2018 securityweek Ransomware
The United Kingdom on Thursday officially accused the Russian government of launching the destructive NotPetya attack, which had a significant financial impact on several major companies.
British Foreign Office Minister for Cyber Security Lord Tariq Ahmad said the June 2017 NotPetya attack was launched by the Russian military and it “showed a continued disregard for Ukrainian sovereignty.”
“The Kremlin has positioned Russia in direct opposition to the West yet it doesn’t have to be that way. We call upon Russia to be the responsible member of the international community it claims to be rather then secretly trying to undermine it,” the official stated.
“The United Kingdom is identifying, pursuing and responding to malicious cyber activity regardless of where it originates, imposing costs on those who would seek to do us harm. We are committed to strengthening coordinated international efforts to uphold a free, open, peaceful and secure cyberspace,” he added.
The U.K. believes that while the NotPetya attack masqueraded as a criminal campaign, its true purpose was to cause disruption. The country’s National Cyber Security Center (NCSC) assessed that the Russian military was “almost certainly” responsible for the attack, which is the highest level of assessment.
The U.K. was also the first to officially accuse North Korea of launching the WannaCry attack. The United States, Canada, Japan, Australia and New Zealand followed suit several weeks later.
Last month, Britain's Defence Secretary Gavin Williamson accused Russia of spying on its critical infrastructure as part of a plan to create “total chaos” in the country.
While the U.S. has not made an official statement on the matter, confidential documents obtained by The Washington Post last month showed that the CIA had also concluded with “high confidence” that the Russian military was behind the NotPetya attack.
Cybersecurity firms and Ukraine, the country hit the hardest by NotPetya, linked the malware to other threats previously attributed to Russia.
The NotPetya malware outbreak affected tens of thousands of systems in more than 65 countries. Researchers initially believed NotPetya (also known as PetrWrap, exPetr, GoldenEye and Diskcoder.C) was a piece of ransomware, but a closer analysis revealed that it was actually a destructive wiper.
Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain reported losing hundreds of millions of dollars due to the attack.
Intel Offers $250,000 for Side-Channel Exploits
15.2.2018 securityweek Exploit
Intel Opens Bug Bounty Program to All Researchers, Offers up to $250,000 for Flaws Similar to Meltdown and Spectre
Intel on Wednesday announced major changes to its bug bounty program, including that it’s now open to all researchers, and significant rewards for exploits similar to Meltdown and Spectre.
Researchers who find critical hardware vulnerabilities that allow software-based side-channel attacks – just like Meltdown and Spectre – can earn up to $250,000. Flaws classified as high severity are worth up to $100,000, while medium- and low-risk issues are worth up to $20,000 and $5,000, respectively. The severity of a flaw is determined based on its CVSS base score, adjusted depending on the security objectives and threat model of the targeted product.
The part of Intel’s bug bounty program covering side-channel exploits will run until December 31, 2018.
Intel also announced that its bug bounty program is now open to all researchers – it was invitation-only until now. When the company launched this initiative back in March 2017, the maximum reward for hardware vulnerabilities was $30,000, but it has now been increased to $100,000 for critical flaws.
The maximum amount the company is prepared to pay for firmware vulnerabilities has increased from $10,000 to $30,000, and for software flaws from $7,500 to $10,000.
The list of hardware products covered by Intel’s bug bounty program includes processors, chipsets, field-programmable gate array (FPGA) integrated circuits, networking and communications equipment, motherboards, and solid-state drives.
“We believe these changes will enable us to more broadly engage the security research community, and provide better incentives for coordinated response and disclosure that help protect our customers and their data,” said Rick Echevarria, vice president and general manager of Platform Security at Intel.
Intel was made aware of the Spectre and Meltdown attack methods several months before researchers disclosed them, but many are unhappy with the way the company handled the situation.
While Spectre and Meltdown also affect processors from AMD, ARM and IBM, Intel was hit the hardest. The company started releasing microcode updates shortly after the existence of the vulnerabilities was brought to light, but the first round of patches introduced stability problems. Intel started releasing a second round of updates, which should address these issues, only last week.
The company says its future CPUs will include protections against attacks like Meltdown and Spectre.
Researchers Warn Against Knee-Jerk Attribution of 'Olympic Destroyer' Attack
15.2.2018 securityweek Attack
Cyber Attack Attribution
Attribution has become a buzzword in malware analysis. It is very difficult to achieve -- but is necessary in a world that is effectively engaged in the early stages of a geopolitical cyberwar. Malware researchers tend to stop short of saying, 'this country or that actor is behind this attack'. Nevertheless, they are not shy in dropping hints, leaving the reader to make subjective conclusions.
They have done just that with the recent cyber-attacks against the PyeongChang Winter Olympic Games.
The New York Times comments, "Security companies would not say definitively who was behind the attack, but some digital crumbs led to a familiar culprit: Fancy Bear, the Russian hacking group with ties to Russian intelligence services."
Microsoft tweeted, "Fresh analysis of the #cyberattack against systems used in the Pyeongchang #WinterOlympics reveals #EternalRomance SMB exploit."
EternalRomance -- one of the leaked NSA exploits -- along with SMB was employed in the Bad Rabbit ransomware which has been likened to NotPetya which the UK government today ascribed to the Russian intelligence services.
Intezer is a firm that specializes in recognizing code reuse. It has analyzed the Olympic attacks, and comments, "We have found numerous small code fragments scattered throughout different samples of malware in these attacks that are uniquely linked to APT3, APT10, and APT12 which are known to be affiliated with Chinese threat actors."
Recorded Future comments (PDF), "Our own research turned up trivial but consistent code similarities between Olympic Destroyer modules and several malware families used by the Lazarus Group. These include standard but different functions within BlueNoroff Banswift malware, the LimaCharlie family of Lazarus malware from the Novetta Blockbuster report, and a module from the Lazarus SpaSpe malware meant to target domain controllers." Lazarus is, of course, considered to be synonymous with North Korea.
But while saying that there are code similarity hints at connections with North Korea, Recorded Future warns against jumping to any specific conclusion. "The trouble with this technique is that while code similarity can be stated with certainty, down to a percentage of bytes shared, the results are not straightforward and require expert interpretation. The Olympic Destroyer malware is a perfect example of how we can be led astray by this clustering technique when our standard for similarity is too low."
Code analysis suggests that Russia, China or North Korea, or any combination thereof, or all, or none of these state actors were behind the Winter Olympics attack.
Juan Andres Guerrero-Saade, principal security researcher at the Insikt Group at Recorded Future says: “Complex malware operations make us take pause to reevaluate research methods and make sure the research community is not being misled by its own eagerness to attribute attacks."
Priscilla Moriuchi, director of strategic threat development at Recorded Future says: “Attribution continues to be important in cyber-attacks because it shapes the victim, public, and government responses. However, accurate attribution is both more crucial and more difficult to determine than ever because adversaries are constantly evolving new techniques and the expertise required to identify a sophisticated actor keeps increasing.”
This doesn't mean that Recorded Future drops no hints of its own. It notes that this was a sophisticated two-pronged attack probably involving an earlier malware attack designed to steal credentials to be used during the opening ceremony against both the organizers and the infrastructure providers. In other words, it could only be achieved by a highly resourced attacker.
The attack's purpose was disruption rather than absolute destruction. While systems were wiped, they were left able to reboot -- allowing the possibility of eventual data recovery and reinstatement. There is no immediately apparent attempt at extortion -- removing financial motivation and leaving the probability of political motivation.
The 'hints' contained in the code similarity point variously at Russia, China and North Korea. Recorded Future adds another possibility: "The co-occurrence of code overlap in the malware may be indicative of a false flag operation, attempting to dilute evidence and confuse researchers." In other words, without access to 5Eyes-quality wiretaps and intercepted voice conversations (which intelligence agencies would be unwilling to reveal) it is all but impossible to attribute this, or any other cyber-attack, with 100% confidence.
As Recorded Future concludes, "For the time being, attribution remains inconclusive."
SAP Security Notes – February 2018 addresses tens of flaws including High Risk issues
15.2.2018 securityaffairs Vulnerebility
SAP Security Notes – February 2018: SAP Security Notes February 2018 addressed several vulnerabilities including High-Risk flaws.
SAP has released February 2018 Patches that addressed some high-risk vulnerabilities in its software, a total of 26 Security Notes (5 high-, 19 medium- and 2 low-risk). Once again, the missing authorization check is the most common vulnerability type this month.
The Security Notes SAP addresses three cross-site scripting (XSS) vulnerabilities, two directory traversal flaws, two information disclosure bugs, two missing authorization checks, one unrestricted file upload, and other issues.
Affected products are the Internet Graphics Server (IGS), NetWeaver System Landscape Directory, HANA Extended Application Services, ABAP File Interface, SAP CRM, ERP Financials Information System, Netweaver Portal, Netweaver Java Web Application, CRM WebClient UI, BI Launchpad, and SAP HANA.
“On 13th of February 2018, SAP Security Patch Day saw the release of 11 Security Notes. Additionally, there were 3 updates to previously released security notes.” reads the advisory published by SAP.

SAP also addressed previous Security Notes that includes an incorrect authorization check in ERP Logistics, a cross-site request forgery (CSRF) vulnerability in SAP Sybase, and a flaw that ties the way the SAP Note Assistant handles digitally signed notes.
Three critical vulnerabilities were reported by Mathieu Geli, Vahagn Vardanyan, and Vladimir Egorov, researchers at ERPScan security firm.
The details of the issues fixed thanks to the support of the researchers are:
A Missing Authentication check vulnerability in SAP NetWeaver System Landscape Directory (CVSS Base Score: 8.3 CVE-2018-2368). Update is available in SAP Security Note 2565622. An attacker can use Missing authorization check vulnerability for access to a service without any authorization procedures and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation and other attacks.
A Directory Traversal vulnerability in SAP Internet Sales (CVSS Base Score: 6.6 CVE-2018-2380). Update is available in SAP Security Note 2547431. An attacker can use Directory traversal to access to arbitrary files and directories located in a SAP-server file system including application source code, configuration and system files. It allows to obtain critical technical and business-related information stored in a vulnerable SAP-system.
An Information Disclosure vulnerability in SAP HANA (CVSS Base Score: 5.3 CVE-2018-2369). Update is available in SAP Security Note 2572940. An attacker can use Information disclosure vulnerability for revealing additional information (system data, debugging information, etc) which will help to learn about a system and to plan other attacks.
The most severe vulnerability addressed by the security updates is a missing authentication check in SAP NetWeaver System Landscape Directory tracked as CVE-2018-2368, which received a CVSS base score of 8.3.
The flaw could be exploited by an attacker to access a service without any authorization, a circumstance that could lead to several attacks, including the privilege escalation and information disclosure,
“A Missing Authentication check vulnerability in SAP NetWeaver System Landscape Directory (CVSS Base Score: 8.3 CVE-2018-2368). Update is available in SAP Security Note 2565622. An attacker can use Missing authorization check vulnerability for access to a service without any authorization procedures and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation and other attacks.” continues ERPScan.
The updates also addressed:
A Directory Traversal vulnerability in SAP Internet Sales (CVSS Base Score: 6.6 CVE-2018-2380) that could be exploited by an attacker to use Directory traversal to access to arbitrary files and directories located in a SAP-server file system including application source code, configuration and system files.
An Information Disclosure vulnerability in SAP HANA (CVSS Base Score: 5.3 CVE-2018-2369). that could be exploited by an attacker for revealing additional information (system data, debugging information, etc).
Other vulnerabilities addressed this month included a directory traversal (CVE-2018-2367) in SAP ABAP File Interface (CVSS base score: 6.6) and a directory traversal (CVE-2018-2380) in SAP Internet Sales (CVSS base score: 6.6).
Further info related to the flaws addressed by SAP are available on the company blog.
Unknown Threat Actor Conducts OPSEC Targeting Middle East
15.2.2018 securityaffairs Hacking
Hackers conduct OPSEC Targeting Middle East – Classified Documents That May Pertain To The Jordanian Research House Dar El-Jaleel Are Being Used As Bait In A Campaign Targeting The Middle East.
The researchers Paul Rascagneres with help of Martin Lee, from CISCO TALOS, described a campaign of targeted attacks against the middle east with key elements present: Geopolitical interest at stake, once documents pertaining Research House Dar EL-Jaleel, that research on Israeli-Palestinian conflict and Sunni-Shia conflict with Iran, are being used.
Second, the extensive use of scripting languages (VBScript, PowerShell, VBA) as part of the attack vector, once they are used to be dynamically loaded and execute VBScript functions stored in a Command & Control server.
Third, the attacker had deployed a series of sophisticated countermeasures to hide his identification using Operation Security (OPSEC), utilization of reconnaissance scripts to validate the victim machine according to his criteria, utilization of CloudFlare system to hide the IP and infrastructure and finally using filters on connections based on User-Agent strings to use the infrastructure for short periods of time before vanishing going offline.
Regarding the analysis in the report, the script campaign is divided into a series of steps to further advance the widespread of the infection. The VBS campaign is composed of 4 steps with additional payloads and 3 distinct functions that are: Reconnaissance, Persistence, and Pivoting.

According to the report the first stage starts with a VBScript named من داخل حرب ايران السرية في سوريا.vbs (“From inside Iran’s secret war in Syria.vbs”) that is aimed to create in the second stage a PowerShell script that will generate a Microsoft Office document named Report.doc and to open it. On the third stage, the opened document contains a macro that creates a WSF (Windows Script File) file to be executed. On the fourth stage the script contains configuration information such as: The hostname of the command and control server, the port used 2095 and the User-Agent.
As the report notice, the User-Agent strings are being used to the identification of targets, while the command and control server filter these strings to only allow connections based in these criteria. The script tries to register the infected system with an HTTP request, which in turn executes an infinite loop to further download and use other payloads. The researchers discovered three types of additional payloads that are the following: s0, s1, and s2. These payloads for WSF scripts are VBScript functions that are loaded and executed in ExecuteGlobal() and GetRef() APIs. The difference between the payloads resides on the number of arguments supplied to execute the function.
The researchers found out a reconnaissance function in the earlier steps of the campaign that was intended to acquire information on the targeted system, verify if it contained significant information or if it was a sandbox machine. The hackers layered out a methodology composed of these steps: first acquiring the serial number of disk volume, and then using a payload to acquire information on any anti-virus software present on the system. Next, by querying ipify.org the hackers tried to obtain the IP address of the infected machines to further obtain the computer name, username, operating system and architecture.
A second function is used to list the drives on the system and its type.
Finally, the researchers cover the remaining two functions: Persistence and Pivoting. Persistence functions were used alongside the reconnaissance functions linked to the WSF script. While the first script was used to persist, the second was used to clean the infected system to cover its tracks. Regarding the Pivoting function, it receives an argument where the PowerShell script executes a second base64 encoded script intended to download shellcode from 176.107.185.246 to be mapped in the memory and then executed.
As the researchers noticed, the hackers behind the campaign had been very careful to protect their infrastructure and their code against the leak. The command and control server was protected by CloudFlare to avoid tracking and difficult the analysis. Furthermore, by using filters on the User-Agents the hackers selected requests that only meet their criteria.
The Threat Actor was only seen active during the morning, on the Central European Time zone, to unleash their attacks and payloads. Once infected the operating system receives the pivot function to disable the firewall and allow the unique IP to receive the shellcode. Next, the server becomes unreachable. The researchers point out: “This high level of OPSEC is exceptional even among presumed state-sponsored threat actors”.
The researchers also noticed some similarities with Jenxcus (Houdini/H-Worn), but it was not clear if it is a new version or an adaption. They for sure agree that it is far more advanced in the resources it presents. The researchers state:
“This document is a weekly report about the major events occurring during the 1st week of November 2017, talking about the most important events happening in Jordan, Iraq, Syria, Lebanon, Palestine, Israel, Russia, ISIS and the ongoing Gulf Countries conflict with Qatar. These campaigns show us that at least one threat actor is interested in and targeting the Middle East. Due to the nature of the decoy documents, we can conclude that the intended targets have an interest in the geopolitical context of the region”.
Sources:
http://www.securityweek.com/actor-targeting-middle-east-shows-excellent-opsec
http://www.securitynewspaper.com/2018/02/10/targeted-attacks-middle-east/
http://blog.talosintelligence.com/2018/02/targeted-attacks-in-middle-east.html
https://blogs.cisco.com/security/talos/targeted-attacks-in-the-middle-east
https://cyware.com/news/targeted-attacks-in-the-middle-east-8e454752
Android Security Bulletin – Google fixed several Critical Code Execution vulnerabilities
15.2.2018 securityaffairs Android
Android Security Bulletin for February 2018 – Google has fixed tens of vulnerabilities for Android OS, including several critical remote code execution (RCE) flaws.
The Android Security Bulletin for February 2018 addresses 26 vulnerabilities in the mobile operating system, most of which are elevation of privilege flaws.
The 2018-02-01 security patch level fixed 7 vulnerabilities, 6 in Media Framework and one issue affecting the System component.
The tech giant has fixed two critical RCE vulnerabilities in Media Framework. The first issue is the CVE-2017-13228 that affects Android 6.0 and newer, the second one, tracked as CVE-2017-13230, impacts Android 5.1.1 and later.

Google also fixed other vulnerabilities in Media Framework, including an information disclosure vulnerability, an elevation of privilege bug, and several denial-of-service flaws.
“The most severe of these issues is a critical security vulnerability in Media framework that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process.” states the advisory.
The most severe of these vulnerabilities is tracked as CVE-2017-13236, it is a System issue that could be exploited by an attacker to achieve remote code execution in the context of a privileged process. The attacker can trigger the flaw via email, web browsing, and MMS when processing media files.
The 2018-02-05 security patch level includes fixes for 19 vulnerabilities in HTC, Kernel, NVIDIA, Qualcomm, and Qualcomm closed-source components.
The most severe flaws included in the 2018-02-05 security patch level are two remote code execution vulnerabilities in Qualcomm components tracked as CVE-2017-15817 and CVE-2017-17760.
Google also released the Pixel / Nexus Security Bulletin that addresses 29 vulnerabilities in Google devices.
“The Pixel / Nexus Security Bulletin contains details of security vulnerabilities and functional improvements affecting supported Google Pixel and Nexus devices (Google devices). For Google devices, security patch levels of 2018-02-05 or later address all issues in this bulletin and all issues in the February 2018 Android Security Bulletin.” states Google.
“All supported Google devices will receive an update to the 2018-02-05 patch level. We encourage all customers to accept these updates to their devices.”
Spam and phishing in 2017
15.2.2018 Kaspersky Analysis Spam
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US (13.21%).
40% of spam emails were less than 2 KB in size.
The most common malware family found in mail traffic was Trojan-Downloader.JS.Sload
The Anti-Phishing system was triggered 246,231,645 times.
9% of unique users encountered phishing
Global events in spam
Spam emails that mention the hottest topics in the world news agenda are a permanent feature of junk traffic. This trend has been observed for several years and is unlikely to change any time soon. Natural disasters in 2017 (hurricanes Irma and Harvey, the earthquake in Mexico) were a gift to fraudsters. “Nigerian” scammers bombarded mailboxes with messages asking for assistance in obtaining the inheritance of deceased relatives and donations for disaster victims, etc. Natural disasters were also a common theme in advertising spam and emails offering jobs and loans.
In 2017 spammers made frequent mention of natural disasters
Sporting events are another favorite topic of spammers. The most popular — and most mentioned in fake giveaway messages — are major soccer competitions and the Olympics. Back in 2016 we picked up emails citing the FIFA 2018 World Cup, and the following year their number increased, with the format and content unchanged. Typically, such emails say that during such-and-such lottery, supposedly held by a well-known organization, the recipient was randomly selected among a million others as the winner of a huge cash prize. Besides money, scammers sometimes promise tickets to competitions. The details are usually outlined in file attachments using official competition and sponsor logos.
“Winning” the lottery can be timed to major sporting events
The “Nigerian” scammers often refer to famous figures. Presidents and other political VIPs are especially in demand. In 2017, one of the most popular figures for fraudsters was US President Donald Trump.
We predict that in 2018 scammers will continue to pay close attention to world events and famous figures so as not to let slip the chance to squeeze ever more money and personal info out of gullible victims.
Cryptocurrencies in spam
Throughout the year we wrote that cryptocurrencies had gained a foothold in advertising spam and fraudulent mailings: all the numerous “Earn from home” schemes, financial pyramids, fake lottery wins, and phishing scams, etc., seem to have been updated and given a cryptocurrency makeover. Let’s try to systematize the various types of cryptocurrency-related spam.
Seminars
As major conferences and seminars are held on blockchain technology, spammers are making increasing use of this topic for their own purposes. The seminars advertised in their mailings don’t overload users with technical details, but promise to teach them how to extract eye-watering profits from cryptocurrencies. Such mailings are relatives of “traditional” spam on the topic “How to make a killing on the stock exchange.”
Example emails advertising “lucrative” seminars
Financial fraud
A specific type of cryptocurrency fraud relates to fake “cloud mining” services. Such services hire out the mining power of their own specialized data centers. Fake sites offer similar services, but on paying up, the user receives neither mining power nor their money back. The crypto version of the classic pyramid scam warrants a special mention: the user “receives” mining income until they enlist other victims (for which there is also a reward). But sooner or later the cash flow stops, and the original investment is not repaid.
Fake “cloud mining” services offer enticing rewards
Sites masquerading as cryptocurrency trading platforms operate in a similar manner. The crucial difference between them and real exchanges is that money can only be invested, not withdrawn. Revenue usually “grows” very quickly, stimulating the user to invest more funds.
On fake cryptocurrency exchanges, experience really isn’t necessary
More subtle are binary options brokers (and their fake counterparts). We covered them in a previous report.
Another type of cryptocurrency fraud is fake services offering to exchange one currency for another, or convert it into “real” money. Scammers lure victims with favorable exchange rates, and then make off with the cash.
The “currency exchange desk” simply pockets the money for itself
Spam is very often used for this kind of fraud because it gives what all scammers crave — anonymity.
Other types of fraud
More traditional types of fraud, such as fake lottery wins, started using bitcoin bait:
Malware
CryptoLocker, whose creators demanded payment in bitcoin, was found in spam far less often than in 2016. That said, we encountered various modifications of Locky, Cerber, Rack, and other ransomware. At the same time, new capabilities such as stealing passwords from cryptocurrency wallets and mining were added to spam-distributed malware.
What’s more, a host of malware was distributed in spam under the guise of bitcoin mining tools or trading instructions.
The attached document was detected as HEUR:Exploit.RTF.Generic
Address databases
Targeted address databases advertised through spam were updated with the email addresses of cryptocurrency users, putting the address owners at risk of a targeted attack (for example, phishing as mentioned above).
Like other hot global issues, cryptocurrency is set be a recurring theme in spam for a very long time to come. And given the juicy rewards on offer, 2018 can expect to see growth in both fraudulent and phishing “cryptocurrency” spam.
Spamming by ethnicity
As we all know, spam peddles everything from potency-enhancing drugs to fake goods by well-known brands — it’s an international phenomenon that knows no geographic boundaries. However, 2017 caught the eye for some more localized spam content.
China and manufacturing
Back in 2016, we wrote about the Chinese habit of using spam to market goods internationally. Nothing changed in 2017: More and more Chinese companies are offering their products in this way.
India and IT
Whereas the Chinese are keen to sell goods on the international market, spam from India is more likely to offer IT services: SEO, web design, mobile apps, and much more:
Russia and seminars
Russian spam is written in, yes, Russian — and is therefore aimed at the domestic market. It too advertises goods and services, but more striking is the range of seminars and training on offer:
America and targeted business spam
In the US, the law governing the distribution of advertising messages operates on the opt-out principle. Accordingly, users can be sent messages until they explicitly unsubscribe from the mailing list in question, for which a link must be provided. The CAN-SPAM Act stipulates many other legal requirements for mailings. The legislation demands that the message body match the subject in terms of topic, there be no automatic collection of addresses, the advertiser’s physical address appear in the text, and much more.
Using the opt-out principle, many small, and sometimes not-so-small, companies send out promotional materials to people who have not subscribed to them. A legal gray area arises from the fact that even if spam-mailing companies are physically located in the US, the emails are distributed worldwide, and most countries operate an opt-in policy, requiring the prior consent of recipients. In other words, some countries at the legislative level consider mailshots to be spam.
A trait of business spam is its very narrow targeting of companies operating in specific areas. Oftentimes, mailings are not directed to the company as a whole, but to people with certain job titles.
Malware and the corporate sector
The number of malicious spam messages in 2017 fell 1.6-fold against 2016. Kaspersky Lab clients registered a total of 145,820,119 triggers of Mail Anti-Virus throughout 2017.
Number of Mail Anti-Virus triggers among Kaspersky Lab clients in 2017
This drop is due to the unstable operation of the Necurs botnet: it mediated the spread of far fewer mailings, and in Q1 2017 was completely idle. Malicious mailshots sent via Necurs were short, not personalized. They were used to try to install cryptolockers from the Locky family on recipients’ computers.
In general, 2017 was marked by a large cluster of malicious, but well-crafted emails, containing fragments of business correspondence matching the company profile, plus the full details of the organizations in whose name they had been sent.
Emails containing malicious objects detected as Backdoor.Java.Adwind.cu
The messages were not mass-distributed, but most likely targeted. Based on the target domain names, it can be assumed that the attackers were primarily interested in the corporate sector, while the tactic of citing previous messages of the addressee suggests in some cases a Business Email Compromise-type attack.
An email containing a malicious object detected as Trojan-PSW.Win32.Fareit.dnak
Malware downloaded onto the victim computer most often had functions for collecting detailed information about the system and its settings (as well as passwords, keystrokes, etc.), and then transferring this data to a remote server. For information about potential targets and perpetrators of such attacks, see our article.
Phishing
Phishing pages migrate to HTTPS
Sites have been moving to HTTPS in increasing numbers, and not just legitimate resources. If a year ago a top tip for users was “check that pages requesting personal data are secure,” today a certificate does not guarantee safety: anyone or anything could be behind it.
Where do scammers get certificates? For domains created specifically for fraudulent purposes, attackers most likely use free 90-day certificates from Let’s Encrypt and Comodo, two certificate authorities. Getting hold of one is simplicity itself.
A phishing site with a free 90-day certificate issued by Let’s Encrypt
What’s more, phishing pages are often located on hacked sites that already have the necessary certificates.
A phishing page located on a hacked site with HTTPS
Scammers also make use of free web hosting with an SSL certificate:
On the topic of free hosting sites, it should be noted that attackers often use services that do not closely monitor user-posted content. It is not uncommon for phishing content to be placed on free hosting sites of well-known companies: this reduces the risk of the page being blacklisted, since it is located on a reputable domain with a high-profile name and a good SSL certificate. And although such services are pro-active in the fight against illegitimate content, phishing pages on their domains are found fairly often.
A phishing page located on the Google Sites service redirecting users to a third-party resource where payment system data is requested
Phishing pages located on the Force.com Sites service
Punycode encoding
Another important rule is to always check the spelling of the domain name, a task made more difficult due to the active use by phishers of Punycode encoding, which helps mask phishing domain names under the domains of well-known brands. Web browsers use Punycode to display Unicode characters in the address bar, but if all the characters in the domain name belong to the character set for one language, the browser displays them not in Punycode format, but in the specified language. Scammers select characters similar or identical to ones in Latin script, and use them to create domain names that resemble those of well-known companies.
The technique is not new, but caused a real stir this year, especially after an article by Chinese researcher Xudong Zheng. As an example, he created a domain with a name that in the address bar was indistinguishable from Apple’s domain. Phishers aren’t always able to find identical symbols, but the results are still look pretty convincing.
Examples of domains displayed in Punycode in browser address bars
Besides the external similarity to the original domain, such domains are more difficult to detect by keywords.
Fake cryptocurrency wallets
Fraudsters are always up to speed on the latest trends, brands, and news hooks. The hype around cryptocurrencies in 2017 reached such a crescendo that even those far removed from the virtual world were snapping up bitcoin, whatever it was.
As a result, cryptocurrency wallets were a very attractive target for phishers. Proof of this is the large number of phishing pages spoofing cryptocurrency wallets. We encountered Coinbase, BitGo, and Xapo, to name just a few. One of the leaders by number of spoofs is blockchain.info.
Examples of phishing pages mimicking user sign-in to popular cryptocurrency wallets
Scammers also spoof popular cryptocurrency services in an attempt to get users to hand over money under the guise of lucrative investments.
A page spoofing the popular Coinbase
Social media fraud
In Q2, social networks were hit by a wave of air ticket giveaways. Scammers set up websites under famous airline brands that were supposedly raffling off tickets. After completing a short survey, the user was redirected to a resource created by the attackers. This could be an infected site, a phishing page prompting to install malware under the guise of a browser update, or a page spreading malicious content, etc.
Examples of Facebook posts with links to various scamming domains
The scheme is not new, but the distribution mechanism in this case is innovative: in winning a “prize,” users themselves shared unsafe content in social media.
For some domains in the scheme, visitor activity statistics were available, according to which just one of the sites was visited by more than 2,500 users worldwide in the space of an hour:
In Q3, scammers shifted their attention to WhatsApp and extended their assortment of fake prizes.
Fake giveaways that began their odyssey in social media migrated to WhatsApp, and the range of prizes expanded
Fake viruses
Cybercriminals often don’t even bother to write malware, using instead fake virus notifications supposedly from common operating systems. Such messages often appear as pop-up ads or as the result of the user being passed through a redirect chain. This might happen after completing a survey, as in the scheme described above.
The scammers’ primary aim is to intimidate and coerce users into calling a “technical support” number where they are offered solutions to disinfect their computer — not free of charge, of course.
Examples of pages showing fake system infection messages
It’s not only Windows users in the firing line. Scammers are targeting Apple products, too.
Example of a page showing a fake system infection message
Under the same guise, cybercrooks also distribute insecure software.
Example of a page showing a fake system infection message and prompting to download a file
Tax refunds
Another eternal topic is tax returns and tax refunds. Public trust in government sites plays an important role in the success of phishing operations in this segment. Exploiting features of the taxation system in different countries, scammers carry out successful attacks in the US, France, Canada, Ireland, and elsewhere.
Examples of phishing pages using the names of tax authorities in different countries
The new iPhone
The release of the new version of the popular smartphone also attracted scammers, with attempts to redirect users to phishing pages mimicking Apple sites growing 1.5-fold in September, when the latest iteration of the flagship series went on sale.
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites using the Apple brand, 2017
The launch of Apple’s new smartphone inspired a host of fraudulent schemes, including fake giveaways, sales of counterfeit devices, and classic phishing scams mentioning the brand.
Fake Apple sign-in page
Statistics: spam
Proportion of spam in email traffic
The share of spam in email traffic in 2017 fell by 1.68% to 56.63%.
Proportion of spam in global email traffic, 2017
The lowest share (52.67%) was recorded in December 2017. The highest (59.56%) belonged to September.
Sources of spam by country
In 2017, the US remained the biggest source of spam (13.21%). A 6.59% hike in spam distribution pushed China up to second place (11.25%). Vietnam took bronze (9.85%).
India slipped from third to fourth (7.02%), showing a 3.13% decline in its share of spam. Next came Germany (5.66%, +2.45%) and Russia (5.40%, +1.87%).
In the seventh place was Brazil (3.97%, -0.04%). And in ninth, France (3.71%, -0.32%). Italy rounds off the Top 10 with a score of 1.86%, up 0.62% against 2016.
Source of spam by country, 2017
Spam email size
In 2017, the share of very small emails (up to 2 KB) in spam again dropped sharply, averaging 43.40%, which is 18.76% less than in 2016. The proportion of emails ranging in size from 2 to 5 KB amounted to 5.08%, another significant change.
Spam emails by size, 2017
There was further growth in the share of emails between 5 and 10 KB (9.14%, +2.99%), 10 and 20 KB (16.26%, +1.79%), and 20 and 50 KB (21.23%, +11.15%). Overall, spam in 2017 did not buck the trend of fewer very small emails and rising numbers of average size emails (5-50 KB).
Malicious attachments in email
Malware families
Top 10 malware families in 2017
In 2017, the most common malware family in email traffic was Trojan-Downloader.JS.Sload — a set of JS scripts that download and run other malicious programs on the victim computer, usually encryptors.
Runner-up was last year’s leader Trojan-Downloader.JS.Agent — the typical member of this malware family is an obfuscated JS that uses ADODB.Stream technology to download and run DLL, EXE, and PDF files.
Third place went to the Backdoor.Java.Qrat family — a cross-platform multi-functional backdoor written in Java and sold in the Darknet under the umbrella of Malware-as-a-Service (MaaS). It is generally distributed by email in the form of JAR attachments.
The Worm.Win32.WBVB family took fourth place. It includes executable files written in Visual Basic 6 (both in P-Code mode and Native mode) that are untrusted in KSN.
Trojan-PSW.Win32.Fareit completes the Top 5. This malware family is designed to steal data, such as the credentials of FTP clients installed on infected computers, cloud-storage credentials, browser cookies, and email passwords. Fareit Trojans send the information collected to the attackers’ server. Some members of the family can download and run other malware.
In sixth position was the Trojan-Downloader.MSWord.Agent family. This malware takes the form of a DOC file with an embedded macro written in Visual Basic for Applications (VBA) that runs when the document is opened. The macro downloads another malicious file from the attackers’ site and runs it on the user’s computer.
In seventh is Trojan.PDF.Badur, which poses as a PDF document containing a link to a potentially dangerous site.
Eighth place was occupied by the Trojan-Downloader.VBS.Agent family — a set of VBS scripts that use ADODB.Stream technology to download ZIP archives and run malware extracted from them.
Trojan.WinLNK.Agent found itself in ninth position. Members of this malware family have the extension .lnk and contain links for downloading malicious files or a path for running another malicious executable file.
One more family of Trojan loaders, Trojan.Win32.VBKrypt, props up the Top 10.
Countries targeted by malicious mailshots
In 2017, Germany (16.25%, +2.12%) held on to top spot. China (12.10%) climbed from third to second, adding 4.78% for the year. Russia (6.87%, +1.27%) rounds off the Top 3.
Countries targeted by malicious mailshots, 2017
Further down come Japan (5.32%, -2.27%), Britain (5.04%, -0.13%), Italy (4.89%, -0.55%), and Brazil (4.22%, -0.77%).
Eighth place is taken by Vietnam (2.71%, +0.81%). And ninth by France (2.42%, -1.15%). The Top 10 is rounded off by the UAE (2.34%, +0.82%).
Statistics: phishing
In 2017, the Anti-Phishing system was triggered 246,231,645 times on computers of Kaspersky Lab users as a result of phishing redirection attempts. That is 91,273,748 more than in 2016. In all, 15.9% of our users were targeted by phishers.
Organizations under attack
The rating of organizations targeted by phishing attacks is based on the triggering of the heuristic component in the Anti-Phishing system on user computers. This component detects all instances when the user tries to follow a link in an email or on the Internet to a phishing page in the event that such links have yet to be added to Kaspersky Lab’s databases.
Organizations under attack by category
The lion’s share of heuristic component triggers in 2017 went to pages that mentioned banking organizations (27%, +1.24%). Second place in the rating is the Payment systems category (15.87%, +4.32%), followed by Online stores (10.95%, +0.78%).
Distribution of organizations subject to phishing attacks by category, 2017.
See our financial report (link) for more details about phishing in the financial sector.
Top 3 organizations under attack from phishers
As before, the trend in mass phishing is still to use the most popular brands. By doing so, scammers significantly increase the likelihood of a successful attack. The Top 3 is made of organizations whose names were most often used by phishers (according to the heuristic statistics for triggers on user computers):
Facebook 7.97%
Microsoft Corporation 5.57%
PayPal 4.50%
The geography of attacks
Countries by percentage of attacked users
As in the previous year, Brazil had the highest percentage of attacked unique users out of the total number of users in the country, seeing its score increase by 1.41% to 29.02%.
Percentage of users on whose computers the Anti-Phishing system was triggered out of all Kaspersky Lab users in the country, 2017
Top 10 countries by percentage of attacked users
Brazil 29.02%
Australia 22.51%
China 19.23%
Qatar 18.45%
Bolivia 18.38%
Albania 17.95%
New Zealand 17.85%
Portugal 16.76%
Angola 16.45%
Russia 16.43%
Top 10 countries by percentage of attacked users
The number of attacked users also increased in Australia — by 2.43% to 22.5%. Next come China (19.23%), where the share of attacked users fell by 3.61%, and Qatar (14.45%).
Results
The number of malicious spam messages in 2017 fell 1.6-fold against 2016. This drop is due to the unstable operation of the Necurs botnet, which mediated the spread of far fewer mailings.
In 2018, spammers and phishers will continue to closely monitor world events and famous figures so as not to miss any opportunity to extract money and personal info from their unsuspecting targets. We can expect mailings to refer to the Winter Olympic Games, the FIFA World Cup, the presidential elections in Russia, and other events. What’s more, the first few months of the year are likely to experience a wave of phishing pages and mailshots exploiting the topic of tax refunds, since in many countries April is tax payment month. The theme of cryptocurrency will be popping up in spam for a very long time to come. And given the juicy rewards on offer, 2018 can expect to see growth in both fraudulent and phishing “cryptocurrency” spam.
The number of phishing sites using SSL certificates will surely continue to grow. As will the use of different domain name obfuscation methods.
Kaspersky Files New Lawsuit Over U.S. Government Software Ban
15.2.2018 securityweek
Kaspersky Lab has filed a new lawsuit over the U.S. government’s decision to ban its products in federal agencies, this time challenging the National Defense Authorization Act (NDAA).
The NDAA for Fiscal Year 2018 was signed by President Donald Trump in mid-December and it reinforced the binding operational directive (BOD) issued by the Department of Homeland Security (DHS) in September, which ordered government agencies to stop using products from Kaspersky due to concerns regarding its ties to Russian intelligence.
Kaspersky filed a lawsuit to appeal the BOD on December 18, a few days after President Trump signed the NDAA. Last month, the security firm filed an injunction in an effort to expedite the appeal.
The government filed a response to the injunction earlier this month and Kaspersky responded this week with a new lawsuit that challenges the NDAA as a bill of attainder.
A bill of attainder is a legislative act that singles out an individual or group for punishment without a trial. Legislative bills of attainder are banned by the U.S. constitution.
“Kaspersky Lab has filed an action challenging the constitutionality of Section 1634 (a) and (b) of the National Defense Authorization Act for Fiscal Year 2018, which prohibits any federal entity from using the company’s hardware, software or services. Kaspersky Lab believes that these provisions violate the U.S. Constitution by specifically and unfairly singling out the company for legislative punishment, based on vague and unsubstantiated allegations without any basis in fact,” Kaspersky Lab stated.
“No evidence has been presented of any wrongdoing by the company, or of any misuse of its products. Kaspersky Lab is proven to be one of the world’s leading IT security companies, with a track record of uncovering malicious code and threat actors regardless of their origin or purpose,” the company added.
Kaspersky has attempted to clear its name by launching a new transparency initiative that involves giving partners access to source code and paying significantly larger bug bounties for vulnerabilities found in the firm’s products.
It has also attempted to provide a logical explanation over accusations that its software had been exploited by Russian hackers to steal data belonging to the U.S. National Security Agency (NSA) from a contractor’s device.