
The US Global surveillance bill has been signed by President Trump
20.1.2018 securityaffairs BigBrothers
US Government missed a historic opportunity to reform a dangerous surveillance law that opens to a global surveillance, instead it has signed a version that makes it worse.
The U.S. legal framework related to the domestic surveillance has been signed by President Trump one day after the Senate approved it with 65 votes against 34. The bill will be effective for other six years, below the Edward Snowden’s comment:
Edward Snowden
✔
@Snowden
65 Senators just voted to expand an unconstitutional law permitting Trump to spy on communications with one leg in the US–without a warrant. For the next six years, any unencrypted internet request that even touches a US border will be "ingested" (intercepted) and parsed by NSA. https://twitter.com/EFF/status/954048766000087041 …
7:56 PM - Jan 18, 2018
359 359 Replies 7,305 7,305 Retweets 7,843 7,843 likes
Twitter Ads info and privacy
Privacy advocates and civil rights have a long criticized the Section 702 of the Foreign Intelligence Surveillance Act (FISA) that allows US intelligence agencies to conduct domestic surveillance under certain conditions without a warrant.
The Section 702 allows the NSA to conduct warrantless spying of foreigners located abroad, including any communications with US citizens.

Section 702 was revealed by NSA whistleblower Edward Snowden in 2012. Civil rights and privacy advocates consider it as unconstitutional under the Fourth Amendment.
The bill increases spying powers of intelligence agencies and block safeguards, curiously it was passed by Republicans who always criticized the corruption of the Government.
Politicians that voted for the Section 702 believe it is crucial it is crucial to protect Americans from foreign governments and terrorism, they highlighted that the revisions to the bill will guarantee citizens from any abuse.
“There is a glimmer of light,” “The last few weeks have demonstrated that bipartisan efforts to reform our surveillance laws continue on an arc of progress.” wrote ACLU legislative counsel Neema Singh Guliani in a blog post.
“With only two more votes, reformers could have halted this bill from advancing and forced a floor debate over badly needed improvements. And an effort to pass the most comprehensive Section 702 reform bill introduced in Congress garnered the support of over 180 members in the House. With actual debate, real reform provisions likely would have passed.”
Just hours before the section 702 program was signed by the President, the Senate’s intelligence committee approved the release of a confidential four-page memo alleging previous abuse of the FISA spying program to the rest of Congress.
“Scores of Republicans have since viewed the document in a Sensitive Compartmented Information Facility on Capitol Hill. They left expressing shock, saying the special counsel investigation into whether Trump’s campaign officials had improper contacts with Russia is based on politically motivated actions at the highest level of law enforcement.” reported The Hill.
House Freedom Caucus Chairman Mark Meadows (R-N.C.) called the memo “shocking.”
““I’m here to tell all of a America tonight that I’m shocked to read exactly what has taken place,” Meadows (R-N.C.) said in a speech on the House floor.
“I thought it could never happen in a country that loves freedom and democracy like this country. It is time that we become transparent with all of this, and I’m calling on our leadership to make this available so all Americans can judge for themselves.”
Politicians opposing the section 702 program are defining its contents “worse than Watergate.”
In conclusion, this is a black page in the history of Americans. The 6-year extension of the regulation that allows the US government to monitor foreigners’ communications abroad without a warrant has been approved. Moreover, the US intelligence will also be able to spy on American citizens, politicians, businessmen, and journalists who communicate with them, despite the Fourth Amendment.
Red Hat reverts Spectre (CVE-2017-5715) security updates due to boot issues reported by customers
20.1.2018 securityaffairs
Red Hat is going to release updates that are reverting previous patches for the Spectre vulnerability (Variant 2, aka CVE-2017-5715).
Just after the release of Spectre and Meltdown patches many experts argued a significative impact on performance and stability of systems running them.
While Meltdown and Spectre Variant 1 could be theoretically being addressed by patching the OS, Spectre Variant 2 require a firmware/microcode update to address the issue.
Now Red Hat joint to the list of companies that observed problems after the installation of the patches, it is releasing updates that are reverting previous patches for the Spectre vulnerability (Variant 2, aka CVE-2017-5715).
The company decided to revert the initial security updates because it received from some customers complaints about booting failure for their systems.
Red Hat is recommending its customers to contact their OEM hardware provider to receive the latest release of firmware to mitigate the CVE-2017-5715.
“Red Hat Security is currently recommending that subscribers contact their CPU OEM vendor to download the latest microcode/firmware for their processor.” reads the advisory published by Red Hat.
“The latest microcode_ctl and linux-firmware packages from Red Hat do not include resolutions to the CVE-2017-5715 (variant 2) exploit. Red Hat is no longer providing microcode to address Spectre, variant 2, due to instabilities introduced that are causing customer systems to not boot. The latest microcode_ctl and linux-firmware packages are reverting these unstable microprocessor firmware changes to versions that were known to be stable and well tested, released prior to the Spectre/Meltdown embargo lift date on Jan 3rd. Customers are advised to contact their silicon vendor to get the latest microcode for their particular processor.”

Other distributions based on Red Hat Enterprise Linux like CentOS could suffer similar problems and it could be necessary to revert Spectre Variant 2 security updates.
The company suggests customers to access the Red Hat Customer Portal Lab App to verify systems have the necessary microprocessor firmware to address CVE-2017-5715 (variant 2):
Red Hat Customer Portal Labs – Spectre And Meltdown Detector
Italian companies and Ministry of the Interior under attack, experts spotted a huge botnet
20.1.2018 securityaffairs BotNet
Threat actors with a deep knowledge of the Fiscal Italian ecosystem are using a huge botnet to target Italian companies and Ministry of the Interior.
On Januaty 18 a colleague of mine (Luca) called me telling a malicious email was targeting Italian companies. This is the beginning of our new analysis adventure that Luca and I run together.
The email pretended to be sent by “Ministero dell’ Economia e delle Finanze” the Italian Department of Treasury and it had smart subjects such as:
Codici Tributo Acconti
F24 Acconti-Codice Tributo 4034
The attacker knows very well the Italian Fiscal Year since those modules are very popular from company administration employees at that time. The attacker would probably exploit this attack path reaching out as many companies as possible. The email address was not coming from the “Ministero dell’ economia e delle Finanze” at all, it was coming from the following addresses:
info@amber-kate.com
info@fallriverproductions.com
The email looks like :

Malicious eMail
A simple link pointing to a high reputation domain was popping out the default browser and downloading the following Javascript file. The high level of obfuscation and the way the content was provided was so suspicious to be worth to follow the analysis.

Infection: Stage 1 Obfuscated
After a deobfuscation phase the javascript looked much more easy te be read from a human side.

Infection: Stage 1 Clear Text
A romantic “drop and execute” section was happening. A GET connection to 239outdoors.com/themes5.php was dropping a file named 1t.exe and later on the same script was able to execute the dropped file. The file 1t.exe was running on the victim machine contacting the Command and Control waiting for further commands.
The new sample looks like GootKit, a weaponized version of Banker Malware. The malware installs itself and contacts Command and Control asking “what to do” and sending the “stolen credentials” directly to the Command and Control server. Details on IPs, Persistencies and so on, is provided in the IoC section, but today’s we won’t describe GootKit, we got access to the Dropping site!
We want to figure out if we might help victims to deactivate the malicious botnet by providing as much as possible details without focusing on the reverse the Malware per se since appears to be known.
By getting further analyzing the dropping website we immediately understood that the same URL was dropping another threat. The parallel threat the dropping website was spreading to the world was called “Nuovo Documento 2008” and it was a .bat file as follows.

New Threat Stage 1
That executable .bat file on a first stage opens up a browser pointing to a legitimate image but later on, it uses a notorious technique called “certutil for delivery of file” to drop and execute another file. This technique is well described here by carnal0wnage. Basically, the attacker uses the certutil.exe program do download a Base64 encoded payload, to decode it and to run it. This technique is very silent since the User-Agent of certutils.exe is not suspicious because it needs to connect outside the company networks to check certificates, so not much IPS rules on it. The dropped file name unslss.exe appears to be very close to the previously analyzed one (1t.exe) it contacts the same C&C and it behaves in a similar way. But again we won’t focus on reverse such a malware but rather we wont be able to reach the highest number of IoC to protect as much as possible the victims. By analyzing the Dropping website we founded that a significative number of connections had additional referrers, so we decided to focus our attention on how many DNS were pointing to such a domain. We did it and the result was quite impressive (please see the Dropping URLs IoC Section).
Following the research on the dropping website, we found an interesting log of all the connection coming from possible victims. We collected that log, and we built the following possible infection list (possible Victims). We won’t publish the Victims IP addresses but if you can prove you are legitimated by your company to ask that logs we can give you (for free, of course) the IP addresses we’ve found related to your company. A detailed list of possible infected networks follows.
Possible Victims:
ACI informatica s.p.a.
AGOS-AS
AGSM Verona Spa
ASGARR Consortium GARR
Acantho S.p.a
Alfanews S.r.l.
Ambrogio s.r.l.
Asco TLC S.p.A.
Autostrade-as
BT Italia
BT Italia S.p.A.
Banca Monte Dei Paschi Di Siena S.P.A.
Brennercom S.p.A.
COLT Technology Services Group Limited
Camera dei deputati
Cesena Net srl
Clouditalia Telecomunicazioni S.p.A.
Comune Di Brescia
Comune di Bologna
Consortium GARR
Consorzio per il Sistema Informativo
Costacrociere-as
Duebite-as
E4A s.r.l.
Energente S.r.l.
FASTNET SpA
FASTWEB SPA
FINECO Banca del Gruppo Unicredit
Fastweb
Forcepoint Cloud Ltd
GenyCommunications
Global Com Basilicata s.r.l.
H3G Italy
Hynet S.R.L.
IBSNAZ
ICT Valle Umbra s.r.l.
InAsset S.r.l.
InfoCamere SCpA
Infracom Italia S.p.A.
Inrete s.r.l
Insiel- Informatica per il sistema degli enti loca
Integrys.it di Stefania Peragna impresa individual
Intred S.p.A.
KPNQWest Italia S.p.a.
LEPIDA
Lepida S.p.A.
Liguria Digitale S.C.p.A.
Linea Com S R L
Linkem spa
Lombardia Informatica S.p.A.
Mandarin S.p.A.
Mc-link SpA
Metrolink S.R.L.
Ministero dell’Interno
Mnet srl
NGI SpA
Nemo S.r.l.
Nordcom S.p.a.
Officine Informatiche Srl
Progetto Evo S.r.l.
Provincia di Reggio nell’Emilia
Qcom spa
Raiffeisen OnLine GmbH
Regione Basilicata
Regione Toscana
Regione Veneto
STI ADSL
Sardegnait-as
Societa’ Gestione Servizi Bp S.p.A.
TELEX S.r.l.
TWT S.p.A.
Telecom Italia
Terra S.p.a.
Time-net S.r.l.
Tiscali SpA
Trenitalia SpA
Trentino Network S.r.l.
Universita’ degli Studi di Milano
Venis S.p.A.
Videotime SPA
Vodafone Group Services GmbH
Vodafone Italia DSL
Vodafone Omnitel B.V.
Vodafone Omnitel N.v.
WIIT S.p.A.
Welcome Italia S.p.A
Wind Telecomunicazioni
Wind Telecomunicazioni SpA
Following the found IoC provided by the long “analysis journey”. I managed this analysis over the night, so I am sure there would be some imprecisions, but I preferred to speed up the entire analysis process to give the opportunity to block such infamous threat as soon as possible.
Hope it helps the community.
IoC:
eMail:
info@amber-kate.com
info@fallriverproductions.com
Dropping URLS:
185.61.152.71
239outdoors.com
bentlabel.com
cdvdautomator.com
cloudblueprintprogram.com
cnchalftone.com
comedyyall.com
conticellolaw.com
couplesdoingbusiness.com
dvoper.com
equinnex.com
ericandchrissy.com
evelynleekley.com
expungementstennessee.com
flaveme.com
grkisland.com
healingfoodconsulting.com
hertzsynergy.com
hollywoodisruption.com
home-sphere.com
integrativenutritiontherapy.com
jdkanyuk.com
kineloveclips.com
kylesinger.com
legionchristmas.com
menshoesonlinestore.com
microtiasurgery.com
movielotbar.com
muiienweg.com
niarhoslondon.com
opsantorinitours.com
progunjobs.com
rocketpak.com
scottishwindowsolutions.com
silkygames.com
snapshotsandwhatnots.com
snotterkind.com
solespin.com
strangerthanchristmas.com
synchronr.com
taramadden.com
terento.website
theargumint.com
thegildedwren.com
thejourneytogodsheart.com
thesaltybody.com
topsantorinitours.com
tuftandneedles.com
videospanishlessons.com
vovachka.com
wall-runners.com
war-arena.com
www.scottishwindowsolutions.com
z1logistics.com
zayantetinyhomes.com
zefeed.com
Command and Controls
185.44.105.97
ns15.dreamsinthesun.com
bdi2.nomadicdecorator.com
elis.k9redemptionrescue.com
api.hailstorm360.com
cerera.survivalbid.com
mark.k9redemptionrescue.org
nsc.dayswithsunrays.com
at.moonbeammagic.com
ssl.vci-cfo.com
sip3.propertiesandprojects.com
host1.jodiray.com
note.lawrencechoy.com
note.lawrencechoy.com:80
185.44.105.97:80/200
note.lawrencechoy.com:80
Hashes
63d6927881d4978da4e162c17d82e9c009d0a93e
7ea33f51b6c4aa54beee7fd878886339c22d2232
8cae0dc9255978a35cfd8db64cbe80001400de9b
839ff9f4c3980ac67d4cbef296520ee364a0911f
8cae0dc9255978a35cfd8db64cbe80001400de9b
Triton Malware exploited a Zero-Day flaw in Schneider Triconex SIS controllers
20.1.2018 securityaffairs Virus
The industrial giant Schneider discovered that the Triton malware exploited a zero-day vulnerability in Triconex Safety Instrumented System (SIS) controllers in an attack aimed at a critical infrastructure organization.
In December 2017, a new malicious code dubbed Triton malware (aka Trisis) was discovered by researchers at FireEye, it was specifically designed to target industrial control systems (ICS) system.
Security experts at CyberX who analyzed samples of the malware provided further details on the attack, revealing that Triton was likely developed by Iran and used to target an organization in Saudi Arabia.
![]()
The Triton malware is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers that are used in industrial environments to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially hazardous situation.
TRITON is designed to communicate using the proprietary TriStation protocol which is not publicly documented, this implies that the attackers reverse engineered the protocol to carry out the attack.
Initial analysis conducted by Schneider excluded that hackers may have leveraged any vulnerabilities in the target products, but now the vendor has discovered that Triton malware exploited a flaw in older versions of the Triconex Tricon system.
Schneider confirmed the presence of a flaw only in a small number of older versions and plans to release security updates that address it in the next weeks.
Schneider also announced that it is developing an application to detects the presence of the malware on a controller and removes it.
Anyway, Schneider pointed out that the root cause of the success of the Triton malware is that victims failed in implementing best practices and security procedures.
Just after the disclosure of the attack, Schneider published a security advisory to warn its customers and recommended to avoid leaving the front panel key position in “Program” mode when the controller is not being configured. The malicious code can only deliver its payload if the key switch is set to this mode.
“Schneider Electric is aware of a directed incident targeting a single customer’s Triconex Tricon safety shutdown system. We are working closely with our customer, independent cybersecurity organizations and ICSCERT to investigate and mitigate the risks of this type of attack.” reads the security advisory.
“The modules of this malware are designed to disrupt Triconex safety controllers, which are used widely in critical infrastructure. The malware requires the keyswitch to be in the “PROGRAM” mode in order to deliver its payload. Among others, the reported malware has the capability to scan and map the industrial control system environment to provide reconnaissance and issue commands directly to Tricon safety controllers.”
Schneider advised customers to implement the instructions in the “Security Considerations” section of the Triconex documentation.
OnePlus confirms up to 40,000 customers affected by Credit Card Breach
20.1.2018 thehackernews Incindent
OnePlus has finally confirmed that its online payment system was breached, following several complaints of fraudulent credit card transactions from its customers who made purchases on the company's official website.
In a statement released today, Chinese smartphone manufacturer admitted that credit card information belonging to up to 40,000 customers was stolen by an unknown hacker between mid-November 2017 and January 11, 2018.
According to the company, the attacker targeted one of its systems and injected a malicious script into the payment page code in an effort to sniff out credit card information while it was being entered by the users on the site for making payments.
The malicious script was able to capture full credit card information, including their card numbers, expiry dates, and security codes, directly from a customer’s browser window.
"The malicious script operated intermittently, capturing and sending data directly from the user's browser. It has since been eliminated," OnePlus said on its official forum. "We have quarantined the infected server and reinforced all relevant system structures."
However, the company believes users who shopped on its website using their saved credit card, PayPal account or the "Credit Card via PayPal" method are not affected by the breach.
OnePlus is still investigating the incident and committed to conducting an in-depth security audit to identify how hackers successfully managed to inject the malicious script into its servers.
Meanwhile, credit card payments will remain disabled on the OnePlus.net store until the investigation is complete as a precaution, though users can make purchases through PayPal.
"We are eternally grateful to have such a vigilant and informed the community, and it pains us to let you down. We are in contact with potentially affected customers. We are working with our providers and local authorities to address the incident better," OnePlus says.
OnePlus is notifying all possibly affected OnePlus customers via an email and advises them to keep a close eye on their bank account statements for any fraudulent charges or look into cancelling their payment card.
The company is also looking into offering a one-year subscription of credit monitoring service for free to all affected customers.
Man Admits to DDoS-ing Employers, Competitors
19.1.2018 securityweek Crime
A New Mexico man admitted in court this week to launching distributed denial of service (DDoS) attacks against the websites of former employers, business competitors, and public services.
The culprit, John Kelsey Gammell, 55, pleaded guilty to one count of conspiracy to commit intentional damage to a protected computer, admitting to launching DDoS attacks on websites in the United States, from at least in or about July 2015 through in or about March 2017. He also pleaded guilty to two counts of being a felon-in-possession of a firearm.
The DDoS attacks were aimed at numerous websites, including domains operated by companies Gammell used to work for or of those that declined to hire him. He also targeted competitors of his business and websites for law enforcement agencies and courts, among others.
Gammell admitted to using programs on his own computers and to purchasing the services of “DDoS-for-hire” companies to launch the DDoS attacks. He purchased the services of companies such as VDoS, CStress, Inboot, Booter.xyz and IPStresser, the Department of Justice reveals.
Some of the victims he targeted include Washburn Computer Group, the Minnesota State Courts, Dakota County Technical College, Minneapolis Community and Technical College, the Hennepin County Sheriff’s Office, among others.
To avoid detection, he used IP address anonymization services, paid for the DDoS-for-hire services using cryptocurrency, used spoofed emails to conceal his conduct, and employed encryption and drive-cleaning tools to conceal digital evidence. To circumvent his victims’ DDoS attack mitigation efforts, Gammell amplified his attacks by using multiple DDoS-for-hire services at once.
Gammell is a convicted felon prohibited from possessing firearms or ammunition. He also admitted to possessing multiple firearms, ammunition, and parts for use in the building of firearms and ammunition. His sentence is scheduled for a later date.
Dridex Campaign Abuses FTP Servers
19.1.2018 securityweek Virus
A recently observed email campaign is abusing compromised FTP servers as download locations for malicious documents and infecting users with the Dridex banking Trojan, Forcepoint has discovered.
Dridex has been one of the most prolific banking Trojans over the past several years, with the actors behind it constantly adopting new techniques and improving their malware for increased efficiency. The malware is focused on stealing user’s online banking credentials to perform financial fraud.
Malicious emails distributed as part of the new campaign were observed on January 17, 2018, primarily sent to .com top level domains (TDLs). Analysis of the top affected TDLs revealed that major regional targets included France, the UK, and Australia.
The emails were sent from compromised accounts, where the sender names were rotated around a list of names, in an attempt to make the emails look more convincing to unsuspecting recipients, Forcepoint reveals.
The malicious actor(s) behind the attack used two types of malicious documents as delivery mechanisms, namely a Word document abusing Dynamic Data Exchange (DDE) for malware execution, and a XLS file with macro code to fetch the banking Trojan.
The compromised servers abused in this campaign don’t appear to be running the same FTP software, and the security researchers believe that the attackers obtained the login credentials as part of other attacks.
“The perpetrators of the campaign do not appear to be worried about exposing the credentials of the FTP sites they abuse, potentially exposing the already-compromised sites to further abuse by other groups. This may suggest that the attackers have an abundant supply of compromised accounts and therefore view these assets as disposable,” Forcepoint notes.
The emails sent in this campaign appear to come from the Necurs botnet, currently considered the largest spam botnet out there. The domains used for distribution were associated with other Necurs campaigns and the document downloaders are similar to those used by the botnet before. Furthermore, Necurs is known to have distributed Dridex for a long time.
What Forcepoint noticed regarding this campaign, however, was that the spam volume was very low compared to typical Necurs campaigns. Only around 9,500 emails were observed in this attack, while normal Necurs campaigns involve millions of emails. The use of FTP servers for download is also new.
“Cybercriminals constantly update their attack methods to try and ensure maximum infection rates. In this case FTP sites were used, perhaps in an attempt to prevent being detected by email gateways and network policies that may consider FTPs as trusted locations. The presence of FTP credentials in the emails highlights the importance of regularly updating passwords,” Forcepoint notes.
Firms More Open to Receiving Vulnerability Reports: Ethical Hackers
19.1.2018 securityweek Vulnerebility
Companies have become more open in the past year to receiving vulnerability reports from security researchers, according to ethical hackers surveyed by bug bounty platform HackerOne.
According to HackerOne’s 2018 Hacker Report, which surveyed nearly 2,000 white hat hackers across 100 countries, companies are somewhat more open (38%) or far more open (34%) to receiving vulnerability reports. Only less than 10% of respondents said firms are less open.
On the other hand, nearly a quarter of respondents said they had not reported vulnerabilities due to the fact that the affected software’s developer had not provided a channel for responsible disclosure.
When it comes to motivation, money is not the most important – as it was in the previous year. There are more researchers hacking to learn new techniques (14.7%), for fun (14%), and for the challenge (14%) than ones who do it for the money (13.1%). Nearly one-quarter of respondents said they donated money earned from bug bounties to charities.
A majority of HackerOne users named websites as their favorite target (70%), followed by APIs (7.5%), Android apps (4.2%), operating systems (3.1%), and IoT systems (2.6%).
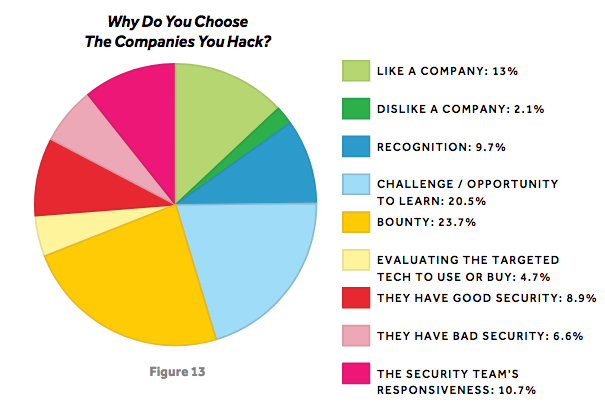
Burp Suite is the favorite tool of nearly one-third of hackers, but more than 15% claim they use their own tools to find vulnerabilities. Other popular tools include web proxies and scanners, network scanners, fuzzers, and debuggers.
A vast majority of the white hats who have signed up on the HackerOne platform, which hosts the bug bounty programs of more than 1,000 organizations, are under the age of 35, and many of them learned how to hack on their own. Most of them either work in IT (software or hardware), consulting, or they are students.
Roughly 66% spend less than 20 hours per week hacking, and only 13% spend 40 hours or more. More than 71% have less than 5 years experience, and only 10% have been hacking for more than 10 years.
Over $23 million have been paid out through HackerOne, with more than $4 million paid to researchers in the U.S., $3 million to India, and $1.3 million each to Australia and Russia. The largest chunk came from companies in the United States ($16 million) and Canada ($1.2 million).
In some places, bug bounty hunters earn far more than they would as a software engineer in their country. For example, in India and Argentina they earn roughly 16 times more than the median annual wage of a software engineer, while in Hong Kong and Egypt they earn 8 times more.
A quarter of respondents said bug bounties represent at least half of their annual income and 14% said they represent 90-100% of their income. Three percent reported making more than $100,000 per year from bug bounty programs, and 1% make more than $350,000.