
Google hacker found a critical flaw in Blizzard Games that expose millions of PCs to DNS Rebinding attacks
23.1.2018 securityaffairs Attack
The white hat hacker Tavis Ormandy discovered a severe flaw in Blizzard games that expose millions of PCs to DNS Rebinding attacks.
The notorious white hat hacker Tavis Ormandy at the Google’s Project Zero team made the headlines again, this time he discovered a severe flaw in Blizzard games that could be exploited by remote attackers to run malicious code on gamers’ computers.
The impact of the discovery is potentially amazing, millions of PC are at risk. Every month, roughly half a billion users play popular online games created by Blizzard Entertainment, including World of Warcraft, Overwatch, Diablo III, Hearthstone and Starcraft II.

Play the Blizzard games is very simple, players just need to install a client application, called ‘Blizzard Update Agent.‘ The application runs JSON-RPC server over HTTP protocol on port 1120, and “accepts commands to install, uninstall, change settings, update and other maintenance related options.”
“All blizzard games are installed alongside a shared tool called “Blizzard Update Agent”, investor.activision.com claims they have “500 million monthly active users”, who presumably all have this utility installed.” wrote Ormandy on a Chromium thread. “The agent utility creates an JSON RPC server listening on localhost port 1120, and accepts commands to install, uninstall, change settings, update and other maintenance related options. Blizzard use a custom authentication scheme to verify the rpc’s are from a legitimate source”
Ormandy demonstrated that the Blizzard Update Agent is vulnerable to ‘DNS Rebinding’ attack that allows any website to create a dns name that they are authorized to communicate with, and then make it resolve to localhost.
The local Blizzard updater service fails to validate what hostname the client was requesting and responds to such requests.
Practically, the website poses itself as a bridge between the external server and your localhost, “this means that *any* website can send privileged commands to the agent.”
The attackers can launch a DNS Rebinding attack to create a DNS entry to bind any attacker-controlled web page with 127.0.0.1 and trick users into visiting it, with this technique a hacker can remotely send privileged commands to the Blizzard Update Agent using JavaScript code.
Ormandy published a proof-of-concept exploit that executes DNS rebinding attack against Blizzard clients.
“I have a domain I use for testing called rbndr.us, you can use this page to generate hostnames: https://lock.cmpxchg8b.com/rebinder.html Here I want to alternate between 127.0.0.1 and 199.241.29.227, so I use 7f000001.c7f11de3.rbndr.us:
$ host 7f000001.c7f11de3.rbndr.us
7f000001.c7f11de3.rbndr.us has address 127.0.0.1
$ host 7f000001.c7f11de3.rbndr.us
7f000001.c7f11de3.rbndr.us has address 199.241.29.227
$ host 7f000001.c7f11de3.rbndr.us
7f000001.c7f11de3.rbndr.us has address 127.0.0.1" wrote Ormandy.
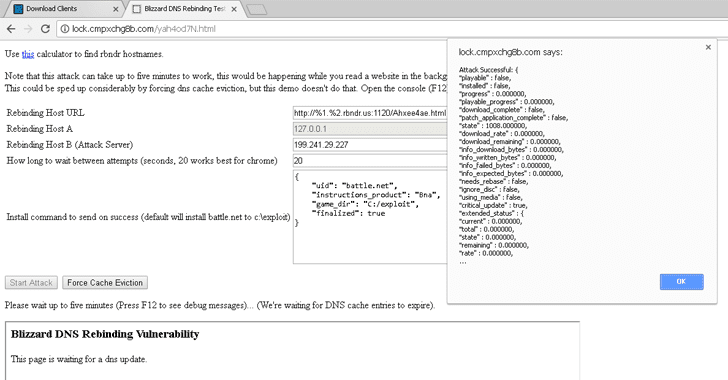
“Exploitation would involve using network drives, or setting destination to “Downloads” and making the browser install dlls, datafiles, etc. I made a very simple demo, I’m sure it’s quite brittle, but hopefully you get the idea! http://lock.cmpxchg8b.com/yah4od7N.html See screenshot attached of how it’s supposed to look.”

Ormandy reported the flaw to Blizzard in December, but after initially communication, Blizzard stopped responding his messages. According to the expert, the companyrolled out just partial mitigation in the client version 5996.
Ormandy was disappointed about the company’s behavior.
“Blizzard were replying to emails, but stopped communicating on December 22nd. Blizzard are no longer replying to any enquiries, and it looks like in version 5996 the Agent now has been silently patched with a bizarre solution.” wrote the expert.
“Their solution appears to be to query the client command line, get the 32-bit FNV-1a string hash of the exename and then check if it’s in a blacklist. I proposed they whitelist Hostnames, but apparently that solution was too elegant and simple. I’m not pleased that Blizzard pushed this patch without notifying me, or consulted me on this.”
Once Ormandy publicly disclosed the issue, Blizzard informed him that it addressed the bug with a more robust Host header whitelist fix that is currently under validation in a QA environment.
A silver bullet for the attacker
23.1.2018 Kaspersky ICS
In the past years, the problem of vulnerabilities in industrial automation systems has been becoming increasingly important. The fact that industrial control systems have been developing in parallel with IT systems, relatively independently and often without regard for modern secure coding practices is probably the main source of ICS security problems. As a result of this, numerous custom solutions have appeared, including proprietary network protocols and algorithms for authentication and encryption. It is these solutions that were the main source of threats discovered by ICS IT security researchers. At the same time, we can see that industrial automation systems derive some of their problems from common technologies (examples include CodeSys Runtime, Microsoft Windows vulnerabilities, etc.).
Companies attach different priority levels to such problems and the risks associated with them. It is obvious for everybody that vulnerability information should never be disclosed until a patch is released. However, many companies believe that this information should not be published even when a patch is available. For software developers, this is always a blow to their reputation. And companies that use vulnerable systems are not always physically able to install a patch or this installation may involve significant costs (interrupted operation of the systems to be updated, the cost of work related to installing updates, etc.).
We assess risks based on our experience of a security system developer and supplier. We are convinced that it is absolutely essential to inform users of vulnerable software about the new threat and the need to update their software as soon as possible. This certainly does not guarantee that all users of vulnerable systems will promptly update them and the threat will go away. However, in our experience, if this is not done very few users update their systems in a timely manner, even if patches are available. We confront hundreds of thousands of new threats every day and we can see that threat actors are on a constant lookout for new attack opportunities. And we realize that by keeping silent about problems we give those threat actors a chance.
This is why we decided to share information on one of our discoveries: according to our research, connecting a software license management token to a computer may open a hidden remote access channel for an attacker.
Why we decided to analyze SafeNet Sentinel
While performing various penetration tests, Kaspersky Lab ICS CERT experts repeatedly encountered the same service on the computers of customers who used software and hardware solutions by different industrial vendors. The experts didn’t attach much importance to it until it was found to be vulnerable. The service was hasplms.exe, which is part of the SafeNet Sentinel hardware-based solution by Gemalto. The solution provides license control for software used by customers and is widely used in ICS and IT systems.
The solution’s software part consists of a driver, a web application and a set of other software components. The hardware part is a USB token. The token needs to be connected to a PC or server on which a software license is required. Some of the USB token models are listed in the table below.
License control solutions of this type are based on the following operating principles: a software product requires a license to operate properly; when a USB token is plugged into the computer, the software “sees” the license and becomes fully functional. The token must be plugged in every time the software is started and remain connected while it is in use. The software part of the Gemalto solution is installed once and remains functional regardless of the life cycle of the software requiring a token.
This Gemalto solution is used in products by other software vendors, including such companies as ABB, General Electric, HP, Cadac Group, Zemax and many other organizations, the number of which, according to some estimates, reaches 40 thousand.
According to the results of independent research conducted by Frost and Sullivan in 2011, SafeNet Sentinel, which is currently owned by Gemalto, has a 40% market share for license control solutions in North America and over 60% in Europe.
The number of end users who use Gemalto solutions is not known. However, if each company has 100 clients, the number of users is in the millions. Unfortunately, few people realize that connecting a token to a computer to control licenses may not be a safe thing to do.
Vulnerabilities and attack vectors
From researchers’ viewpoint, hasplms.exe exhibited a rather curious behavior in the system: it could be remotely accessed and communicated with on open port 1947. The protocol type was defined by the network packet header – either HTTP or a proprietary binary protocol was used. The service also had an API of its own, which was based on the HTTP protocol.
Analyzing the service was made more difficult by the fact that the binary file used a VMProtect-type protector and generated its bytecode from the original Gemalto code. Due to this, it was decided to use fuzzing as the main tool for analyzing the vulnerable service’s behavior.
First of all, we looked at the localization function – the user could download language packs consisting of two files, one of which was localize.xml. The second file, in HTML format, had parameters, one of which turned out to be vulnerable to buffer overflow. It would have been a simple vulnerability, if it wasn’t for one curious detail: although, as mentioned above, a protector was used, for some reason the developers did not use any of the classical mechanisms providing protection from such binary vulnerabilities (such as Stack Canary, Stack Cookie, ASLR, etc.). As a result, a simple buffer overflow could allow an attacker to execute arbitrary code on the remote system.
Note that such software development flaws are very rare in modern solutions. As a rule, secure coding practices are implemented when developing serious commercial products (such as SDL – security development lifecycle), which means that security is designed into applications at the development stage, rather than being implemented as an additional option.
This attack vector can be used without LPE (local privilege escalation) – the vulnerable process runs with SYSTEM privileges, enabling malicious code to run with the highest privileges.
Sample script loading a language pack file
Result of Buffer Overflow exploitation, leading to RCE
The vulnerability was assigned the number CVE-2017-11496.
This was just one of the vulnerabilities we found. And the overall result of our research was disquieting.
In late 2016 – early 2017, 11 vulnerabilities were identified: two allowed remote code execution if exploited and nine were denial-of-service vulnerabilities.
By June 2017, Kaspersky Lab ICS CERT had identified three more vulnerabilities: an XML bomb and two denial-of-service flaws, one of which could potentially lead to remote execution of arbitrary code.
In total, 14 vulnerabilities have been identified, all quite dangerous (for example, exploitation of each of the Remote Execution of Arbitrary Code type vulnerabilities is automatically performed with SYSTEM privileges, i.e., the highest privilege level in Windows).
All attack vectors affecting the vulnerable service were multi-stage.
We promptly sent all information on the vulnerabilities identified to Gemalto. The vulnerabilities were assigned the following respective CVE numbers:
CVE-2017-11496 – Remote Code Execution
CVE-2017-11497 – Remote Code Execution
CVE-2017-11498 – Denial of Service
CVE-2017-12818 – Denial of Service
CVE-2017-12819 – NTLM hash capturing
CVE-2017-12820 – Denial of Service
CVE-2017-12821 – Remote Code Execution
CVE-2017- 12822 – Remote manipulations with configuration files
In addition to vulnerability descriptions, we sent a description of peculiar functionality to Gemalto.
Peculiar functionality
Kaspersky Lab ICS CERT experts have found that hasplms.exe has some rather unusual functionality:
When a Gemalto USB token is first connected to a computer (even if the active session is blocked), a driver and service that accepts network connections on port 1947 are installed if the Internet access is available.
If a driver is manually downloaded from the Gemalto website and installed, a driver and service that accept network connections on port 1947 are installed and port 1947 is added to Windows firewall exceptions.
If Gemalto software is installed as part of a third-party installation file, port 1947 is also added to Windows firewall exceptions.
There is an API function which enables or disables the administrative panel in the web interface, making it possible to modify the settings of the program part of the SafeNet Sentinel hardware-based solution. The panel is available by default on the localhost IP address – 127.0.0.1.
The API can be used to change the internal proxy settings for updating language packs.
After changing the proxy server, the service’s internal logic can be used to obtain the NTLM hash of the user account under which the hasplms.exe process is running (i.e., SYSTEM).
This appears to be an undocumented feature and can be used for stealthy remote access. This means that remote attackers can use these capabilities to gain access to the administrative panel of the Gemalto software, carry out attacks with system user privileges and conceal their presence after completing these attacks.
As mentioned above, Gemalto representatives were informed of this attack vector.
Non-transparent security
Solutions, technologies or individual software modules used by many third-party vendors often do not undergo proper security testing. This potentially opens up new attack vectors. At the same time, closing vulnerabilities in such products, which are often used, among other applications, in banking and industrial control systems, is not always a smooth process: for some reason, vendors of such systems are in no hurry to notify their users of problems identified in their products.
In early 2017, we sent information about 11 vulnerabilities we had identified to Gemalto. It was only in late June that, in response to our repeated requests, the vendor informed us that a patch had been released and information about the vulnerabilities that had been closed, as well as a new version of the driver, could be found on the company’s internal user portal.
On June 26, we informed Gemalto of the suspicious functionality and of three more vulnerabilities. This time, things went quicker: on July 21 the vendor released a private notice on a new driver version – without any mention of the vulnerabilities closed.
According to Gemalto, the company has notified all of its customers of the need to update the driver via their account dashboards. However, this was apparently not sufficient: after we published information about the vulnerabilities identified, we were contacted by several developers of software which uses hasplms. It became clear from our communication with them that they were not aware of the problem and continued to use versions of the product with multiple vulnerabilities.
Update software to the current version (7.6) ASAP
We urge those users and companies that use Gemalto’s SafeNet Sentinel to install the latest (secure) version of the driver as soon as possible or contact Gemalto for instructions on updating the driver. We also recommend closing port 1947, at least on the external firewall (on the network perimeter) – but only as long as this does not interfere with business processes.
In the case of installing the driver via Microsoft Windows Update servers, we recommend checking hasplms.exe to make sure it is the latest version. If an obsolete version is used, it is crucial to install the latest (secure) version of the driver from the vendor’s website or contact Gemalto for instructions on updating the driver.
We also recommend closing port 1947, at least on the external firewall (on the network perimeter) – but only as long as this does not interfere with business processes. This will help to reduce the risk of the vulnerabilities being exploited.
Some software vendors who use third-party solutions as part of their products may be very thorough about the security of their own code, while leaving the security of third-party solutions to other companies (the vendors of these solutions). We very much hope that most companies act responsibly both with respect to their own solutions and with respect to third-party solutions used in their products.
V Androidu špehuje malware SkyGoFree
23.1.2018 SecurityWorld Android
Největší dosavadní bezpečnostní hrozbou roku 2018 spojenou s operačním systémem Android – tedy alespoň podle zájmu médií – je malware s mírně zarážejícím názvem SkyGoFree. Samotné jméno pravděpodobně pochází od výzkumníků společnosti Kaspersky a nestojí za ním žádné tajemno.
Toto slovní spojení totiž bylo nalezeno v jedné z domén požitých ve zkoumaném vzorku a malware tak nijak necílí na uživatele telekomunikační společnosti Sky nebo její televize Sky Go. A co vlastně SkyGoFree (nebo SkyFree dle identifikace produkty společnosti Sophos) přesně je? Jedním slovem: Spyware.
Následující část dekompilovaného kódu v Javě, přičemž znalost tohoto jazyka není nutná, protože se jedná jen o ilustraci, naznačuje rozsah dat, která může tento malware ukrást:
. . .
public static final String URL_UPLOAD_CAMERA = "upload_camera.php";
public static final String URL_UPLOAD_CELL_INFO = "upload_cella.php";
public static final String URL_UPLOAD_FILESYSTEM = "upload_filesystem.php";
public static final String URL_UPLOAD_FILE_SEND = "upload_documents.php";
public static final String URL_UPLOAD_HISTORY = "upload_history.php";
public static final String URL_UPLOAD_INFO_TEL = "upload_info_tel.php";
public static final String URL_UPLOAD_LISTAPP = "upload_listapp.php";
public static final String URL_UPLOAD_REG_CALL = "upload_reg_call.php";
public static final String URL_UPLOAD_RUBRICA = "upload_rubrica.php";
public static final String URL_UPLOAD_SMS = "upload_sms.php";
public static final String URL_UPLOAD_WHATSAPP_SMS = "upload_whatsapp_msg.php";
. . .
Při pozornějším pohledu si lze všimnout slova RUBRICA – jde o italský pojem pro adresář. Mnohé ze škodlivého kódu tohoto malware pochází pravděpodobně od italsky mluvících autorů. Výše uvedená ukázka pochází ze souboru s názvem Costanti.java, což by v angličtině odpovídalo názvu Constants.java.
SkyGoFree obsahuje řadu škodlivých funkcí včetně StartReverse(), která nakažený telefon připojí k serveru kybernetických zločinců a umožní tzv. reverzní shell (pojem shell odkazuje na terminologii unixových a linuxových systémů). Za normálních okolností se uživatel musí přihlásit do příkazové řádky a provést připojení k zařízení, což znamená projít několika firewally i překladem síťové adresy, které stojí v cestě.
Řada mobilních datových sítí a téměř všechny Wi-Fi sítě, kde je uživatel konzumentem dat (klient), sice umožňují odchozí komunikaci s jinými lidmi, ale připojení k jeho zařízení již nedovolí - jeho zařízení tak nemůže sloužit jako poskytovatel dat, tedy server. A právě technika reverzního shellu umožňuje hackerům toto omezení obejít a celý proces přihlašování vlastně o 180 stupňů převrátit.
První krok sice i v tomto případě iniciuje uživatelské zařízení, nicméně pouze za účelem navázání spojení se serverem provozovaným počítačovými podvodníky. Následně se již nakažený telefon chová jako server, zatímco zločinci vystupují jako klienti – přihlásí se a získají nad zařízením nic netušící oběti přímou kontrolu.
Součástí SkyGoFree je vlastnost – dá-li se tak vůbec tato funkce nazvat – označovaná jako Social, jejímž cílem je sbírat data z mnoha dalších aplikací spuštěných na klientském zařízení.
Následující fragment kódu ukazuje, jak se SkyGoFree pokouší získat data ze sociálních sítí:
. . .
mMap.put("messenger", new Social("/data/data/com.facebook.orca/databases/", new String[] { "upload_facebook_chat.php" }));
mMap.put("facebook", new Social("/data/data/com.facebook.katana/databases/", new String[] { "upload_facebook_search.php", "upload_facebook_contacts.php" }));
mMap.put("whatsapp", new Social("/data/data/com.whatsapp/databases/", new String[] { "upload_whatsapp_msgstore.php", "upload_whatsapp_contacts.php" }));
mMap.put("gmail", new Social("/data/data/com.google.android.gm/databases/", new String[] { "upload_email_gmail.php" }));
mMap.put("mlite", new Social("/data/data/com.facebook.mlite/databases/", new String[] { "upload_messengerlite_chat.php" }));
. . .
Dobrou zprávou je, že drtivé většiny telefonů se systémem Android využívaných běžným způsobem se tento problém netýká a aplikace si data vzájemně (a nepozorovaně!) číst nemohou. Pokud nejde o rootnutý telefon nebo o příliš staré či neaktualizované zařízení, které obsahuje bezpečnostní chybu umožňující utajený automatický Root, nebude uvedená část tohoto malware fungovat.
SkyGoFree obsahuje i komponentu, která „může volat domů“ a stáhnout si k instalaci další moduly. Jde vlastně o obdobu systému pluginů, jen ve světě malware. Nicméně aktuálně jsou tyto dodatečné balíčky nedostupné. Malware bývá často naprogramován tak, aby se mohl sám aktualizovat i rozšiřovat. Důsledkem tohoto přístupu je, že reálné hrozby jsou ještě větší a nikdo, ani uživatelé ani bezpečnostní výzkumníci, vlastně neví, k čemu infikovaná zařízení kybernetičtí zločinci v budoucnu zneužijí.
Z pohledu uživatele
Zkoumaný vzorek Malware předstírá, že se jedná o „aktualizaci systému“ a používá k tomu zelenou ikonu Androidu:
Dojde-li ke spuštění této aplikace, poběží na pozadí a takřka okamžitě svoji ikonu odstraní a uživatel tak může snadno podlehnout dojmu, že se „aktualizace“ zdařila. Naštěstí se ale tento program stále zobrazuje v přehledu aplikací (Nastavení|Aplikace), kde ho lze zastavit a odinstalovat:
Všechny dostupné informace svědčí o tom, že tento malware nikdy nebyl součástí obchodu Google Play. Aby šlo tento škodlivý software nainstalovat, musí uživatelé zapnout volbu Povolit instalaci neoficiálních aplikací (Nastavení|Zabezpečení|Neznámé zdroje):
Obchod Google Play sice není rajská zahrada bez jakéhokoli viru obehnaná neprostupnou zdí, nicméně ve srovnání s neznámými zdroji – jako jsou alternativní obchody, nemoderovaná diskusní fóra nebo odkazy od přátel – jde pořád o mnohem bezpečnější místo pro získávání aplikací.
Co s tím?
Držet se obchodu Google Play. Pokud opravdu potřebujete využívat specifickou aplikaci, která není k dispozici v Google Play, po její nainstalování možnost využití neznámých zdrojů opět zakažte (Nastavení|Zabezpečení|Neznámé zdroje).
Používejte antivirový program pro operační systém Android.
Nevěřte systémovým aktualizacím třetích stran. Zvláště obezřetní buďte před „aktualizacemi“ uvádějícími, že nabízí další funkce a vlastnosti, které oficiálně nejsou k dispozici.
Critical Flaw in All Blizzard Games Could Let Hackers Hijack Millions of PCs
23.1.2018 thehackernews Vulnerebility
A Google security researcher has discovered a severe vulnerability in Blizzard games that could allow remote attackers to run malicious code on gamers’ computers.
Played every month by half a billion users—World of Warcraft, Overwatch, Diablo III, Hearthstone and Starcraft II are popular online games created by Blizzard Entertainment.
To play Blizzard games online using web browsers, users need to install a game client application, called 'Blizzard Update Agent,' onto their systems that run JSON-RPC server over HTTP protocol on port 1120, and "accepts commands to install, uninstall, change settings, update and other maintenance related options."
Google's Project Zero team researcher Tavis Ormandy discovered that the Blizzard Update Agent is vulnerable to a hacking technique called the "DNS Rebinding" attack that allows any website to act as a bridge between the external server and your localhost.
Just last week, Ormandy revealed a similar vulnerability in a popular Transmission BitTorrent app that could allow hackers to remotely execute malicious code on BitTorrent users' computers and take control of them.
By simply creating a DNS entry to bind any attacker-controlled web page with localhost (127.0.0.1) and tricking users into visiting it, hackers can easily send privileged commands to the Blizzard Update Agent using JavaScript code.
Although a random website running in a web browser usually cannot make requests to a hostname other than its own, the local Blizzard updater service does not validate what hostname the client was requesting and responds to such requests.
Blizzard DNS Rebinding Attack — Proof of Concept Exploit
Ormandy has also published a proof-of-concept exploit that executes DNS rebinding attack against Blizzard clients and could be modified to allow exploitation using network drives, or setting destination to "downloads" and making the browser install malicious DLLs, data files, etc.
Ormandy responsibly reported Blizzard of the issue in December to get it patched before hackers could take advantage of it to target hundreds of millions of gamers.
However, after initially communication, Blizzard inappropriately stopped responding to Ormandy's emails and silently applied partial mitigation in the client version 5996.
"Blizzard was replying to emails but stopped communicating on December 22nd. Blizzard is no longer replying to any enquiries, and it looks like in version 5996 the Agent now has been silently patched with a bizarre solution," Ormandy says.
"Their solution appears to be to query the client command line, get the 32-bit FNV-1a string hash of the exename and then check if it's in a blacklist. I proposed they whitelist Hostnames, but apparently, that solution was too elegant and simple. I'm not pleased that Blizzard pushed this patch without notifying me, or consulted me on this."
After the Ormandy's report went public, Blizzard contacted and informed him that a more robust Host header whitelist fix to address the issue entirely is currently being developed for deployment.
Ormandy is also checking other big games vendors with a user base of over 100 Million to see if the problem can be replicated.
Nearly Half of the Norway Population Exposed in HealthCare Data Breach
23.1.2018 thehackernews BigBrothers
Cybercriminals have stolen a massive trove of Norway's healthcare data in a recent data breach, which likely impacts more than half of the nation's population.
An unknown hacker or group of hackers managed to breach the systems of Health South-East Regional Health Authority (RHF) and reportedly stolen personal info and health records of some 2.9 million Norwegians out of the country's total 5.2 million inhabitants.
Health South-East RHA is a healthcare organisation that manages hospitals in Norway’s southeast region, including Østfold, Akershus, Oslo, Hedmark, Oppland, Buskerud, Vestfold, Telemark, Aust-Agder and Vest-Agder.
The healthcare organisation announced the data breach on Monday after it had been alerted by HelseCERT, the Norwegian CERT department for its healthcare sector, about an "abnormal activity" against computer systems in the region.
HelseCERT also said the culprits behind the data breach are "advanced and professional" hackers, although it is still unknown as to whether they were managed to exfiltrate data successfully and if so, how many people may have been impacted.
So far there's also no evidence if the stolen data theft has had any consequences for or effects on patients' safety. However, the healthcare organisation assured that security "measures had been taken to limit the damage caused by the burglary."
"We are in a phase where we try to get an overview. It's far too early to say how big the attack is. We are working to acquire knowledge of all aspects, " NorCERT director Kjetil Nilsen told Norwegian publication VG.
"Everything indicates that it is an advanced player who has the tools and ability to perform such an attack. It can be advanced criminals. There is a wide range of possibilities."
Why Do Hackers Want Your Health Data?
Digital healthcare has been growing to satisfy the demands of connected healthcare technology that provides better treatment and improved patient care.
We know that any organisation with a computer is at risk from cyber-attacks both from criminals wanting to extort money and state-sponsored hackers wanting to cause chaos.
Since the healthcare sector is part of the critical national infrastructure, alongside water, electricity and transport, it becomes an attractive target for hackers.
Believe it or not, your medical records are worth more to hackers than your stolen credit card details on the dark web markets.
Financial data has a finite lifespan, but the information contained in health care records—which includes names, birth dates, policy numbers, diagnosis codes, social security number and billing information—has a much longer shelf life and is rich enough for identity theft.
Fraudsters can use this data to create fake identities to do all illegal kinds of stuff in your name, combine a patient number with a false provider number and file fake claims with insurers, and even file fake tax returns using your stolen addresses, phone numbers and employment history.
How to Protect Yourself After a Data Breach?
If you are a one of those affected by the healthcare breach, you will have to remain vigilant against fraud for the rest of your lives, because the risk of identity theft isn't short term, unlike in case of credit cards fraud.
You may follow the following steps to protect yourself:
1) Monitor Your Accounts: Watch out if someone using your information do not ever try to take over or transfer money out of your existing accounts. Don’t forget that thieves with stolen details on you can get through your security questions, including the last four digits of your social and street address. Also, watch for any unauthorised activity or transfers on your current financial accounts.
2) File Your Taxes Early: With the stolen information in the hands, cyber thieves could hook your tax refund by filing your taxes early and claiming it for themselves. So, to avoid any such problems, file your taxes as early as possible.
3) Stay Vigilant: The foremost thing to protect against any breach is to stay vigilant, as nobody knows when or where your stolen identities will be used. So, affected consumers will simply have to stay mindful forever.