
2017 has also seen a substantial rise in SQL Injection vulnerabilities. It’s surprising how many sites were put in danger by vulnerabilities found in WordPress plugins. The total number of active installs is 17,101,300+.
WordPress plugins and themes vulnerabilities statistics for 2017
24.1.2018 securityaffairs Vulnerebility
WordPress plugins and themes vulnerabilities statistics for 2017. The statistics were derived from our up-to-date WordPress Vulnerabilities Database. We are monitoring a large number of sources to add new vulnerabilities to the database on a daily basis.
The year in figures
We added 221 vulnerabilities to our database. The total number of vulnerabilities decreased by 69%. During 2017, just like in 2016, Cross-Site Scripting (XSS) has been at the top of the list. More and more WordPress plugins and themes are found to be vulnerable to Cross-Site Scripting (XSS) vulnerability. This is because many developers do not pay enough attention to escaping data output.

2017 has also seen a substantial rise in SQL Injection vulnerabilities. It’s surprising how many sites were put in danger by vulnerabilities found in WordPress plugins. The total number of active installs is 17,101,300+.
Total vulnerable plugins – 202
Total vulnerable themes – 5
Plugins affected by vulnerabilities in WordPress.org repository – 153
Non-WordPress.org repository plugins affected by vulnerabilities – 24
WordPress plugins vulnerabilities-2017
WordPress top 3 vulnerabilities
Cross-Site Scripting (XSS)
SQL Injection (SQLi)
Broken Access Control
Plugins by vulnerability type
XSS (Cross-Site Scripting) – 71
SQL Injection – 40
Unrestricted Access – 20
Cross Site Request Forgery (CSRF) – 12
Multi – 10
Information Disclosure – 10
Arbitrary File Upload – 7
BYPASS – 7
Arbitrary File Download – 7
PHP Object Injection – 5
Remote File Inclusion – 3
Local File Inclusion – 3
Arbitrary Code Execution – 2
Direct static code injection – 1
Directory Traversal – 1
Top 5 most popular plugins affected by vulnerabilities in 2017
Yoast SEO (most popular SEO plugin) – 5,000,000+ – XSS (Cross-site Scripting)
WooCommerce (most popular ecommerce plugin) – 3,000,000+ – XSS (Cross-site Scripting)
Smush Image Compression and Optimization – 1,000,000+ – Directory Traversal
Duplicator – 1,000,000+ – XSS (Cross-site Scripting)
Loginizer – 600,000+ – SQL Injection
Some interesting facts?
WordPress released 8 security updates in 2017 year.
The total number of vulnerabilities in the ThreatPress vulnerabilities database is 3321
First vulnerability discovered in 2005-02-20
Intel recommended to stop deploying the current versions of Spectre/Meltdown patches
24.1.2018 securityaffairs Vulnerebility
Intel recommended OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of Spectre/Meltdown patches.
While the Linux father Linus Torvalds defines the Spectre updates “utter garbage”, Intel warns to stop installing current versions of Spectre/Meltdown patches.
Intel explained its approach in its technical note about Spectre mitigation (“Speculative Execution Side Channel Mitigations“), the tech giant addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The Indirect Branch Restricted Speculation, along with Single Thread Indirect Branch Predictors (STIBP) and Indirect Branch Predictor Barrier (IBPB), prevent the abuse of the prediction feature and the exploitation of the flaw.
Torvalds speculate the Intel’s decision to address the issues in this way is mainly motivated by the intention to avoid legal liability. Recalling two decades of flawed chips would have a catastrophic impact on the tech giant.
Torvalds explained that the impact of using IBRS on existing hardware is so severe that no one will set the hardware capability bits.
Users and IT companies are reporting severe problems after installing the patches, such as a significant degradation of performance and unwanted reboots.
Intel recommended OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of Spectre/Meltdown patches. The company announced to have found the root cause of reboot issued for Broadwell and Haswell platforms and is asking to wait for a fix.
The tech giant began rolling out to industry partners a beta update to address the issue.
“As we start the week, I want to provide an update on the reboot issues we reported Jan. 11. We have now identified the root cause for Broadwell and Haswell platforms, and made good progress in developing a solution to address it.”Intel said in a press release published on Monday. “Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed.”
Let’s hope Intel will release new Spectre/Meltdown patches soon
According to TrendMicro Business Email Compromise (BEC) attacks could reach $ 9 billion in 2018
24.1.2018 securityaffairs Spam
According to a report published by the security firm TrendMicro, Business Email Compromise (BEC) attacks could reach $ 9 billion in 2018.
The report highlights the growth of damage caused by hackers who adopts new attack vectors techniques like the ones used recently by Lebanese intelligence agency Dark Caracal
According to a report published by TrendMicro, Business Email Compromise (BEC) attacks had surpassed the value of damage to enterprises in the past years and it is estimated that it could reach $ 9 billion dollars in 2018. This rising value of loss for business takes into account new attack vectors like the one from Lebanese Intelligence Agency Dark Caracal malware who utilizes malware in android application.
The report states that the FBI released a public announcement revealing that BEC attacks had become a $ 5.3 billion industry in the past years. In that regard, the report emphasizes that hackers are employing Social Engineering to lure and deceive employees in a myriad of scams to bypass security measures. By using a deep understanding of Human Psychology hackers are circumventing the defenses, as the report states ” it requires little in the way of special tools or technical knowledge to pull off, instead of requiring an understanding of human psychology and knowledge of how specific organizations work.”
The report lists how BEC attacks are usually conducted. The techniques are: Bogus invoice scheme, CEO fraud, Account compromise, Attorney impersonation and Data Theft. The report highlight that these attacks can be classified into two major groups: Credential grabbing and email only.

The credential grabbing technique as detailed by the report has shown an increase in phishing HTML pages that are sent as spam attachments. Also, by employing malware campaign hackers target organizations. One recent example of malware is Zyklon that exploits flaws in Microsoft Office. The charts in the report shown that the attacks have doubled in the period from January to September 2017.
As discovered by researchers in the report, the two main types of malware techniques employed are keyloggers and Remote Access Tools (RAT). Since these tools are low cost and effective they can harvest all credentials on any infected machines. Malware techniques are very hard to detect by anti-virus since they are widely shared in forums or placed in applications commonly used on a daily basis. The report lists the most common malware used in Business Email Compromise attacks: AgentTesla, CyborgLogger, DarkComet, DiamondFox, Dracula Logger, iSpy Keylooger, Knight Logger and Luminosity Link.
The report also suggests how to defend and avoid against BEC attacks: Employee awareness and education, verifying emails received, verification of the legitimacy of executive requests, verification of requests from vendors and suppliers, verification of any requests and the adoption of a security culture within the organization.
Sources:
https://www.ic3.gov/media/2017/170504.aspx
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/business-email-compromise-bec-schemes
https://www.trendmicro.com/vinfo/us/security/research-and-analysis/predictions/2018
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/delving-into-the-world-of-business-email-compromise-bec
https://irishinfosecnews.wordpress.com/2018/01/18/bec-attacks-to-exceed-9b-in-2018-trend-micro/
https://www.infosecurity-magazine.com/news/new-attack-group-fires-rats-and/
https://threatpost.com/new-dridex-variant-emerges-with-an-ftp-twist/129546/
http://mashable.com/2018/01/19/dark-caracal-hackers-phish-whatsapp-and-facebook-accounts/#1p4UuGZVVSqx
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/delving-into-the-world-of-business-email-compromise-bec
https://www.darkreading.com/vulnerabilities—threats/bec-attacks-to-exceed-$9b-in-2018-trend-micro/d/d-id/1330853
https://www.csoonline.com/article/3247670/email/email-security-in-2018.html
http://www.informationsecuritybuzz.com/expert-comments/business-email-compromise-attacks-exceed-9b-2018-ironscales/
https://in.reuters.com/article/us-lebanon-cyber/lebanese-security-agency-turns-smartphone-into-selfie-spycam-researchers-idINKBN1F726S
https://www.forbes.com/sites/thomasbrewster/2018/01/18/lebanon-surveillance-hits-google-android-lookout-eff/#19ad8aef7971
http://www.computerweekly.com/news/252433527/Powerful-Zyklon-malware-exploiting-MS-Office-flaws
Satori’s threat actors are behind the new Masuta botnet that is targeting routers in the wild
24.1.2018 securityaffairs BotNet
Masuta botnet targets routers using default credentials, one of the versions analyzed dubbed “PureMasuta” relies on the old network administration EDB 38722 D-Link exploit.
Security experts at NewSky’s believe the operators of the recently discovered Satori botnet are launching a new massive hacking campaign against routers to recruit infect them and recruit in the botnet dubbed Masuta.
“We analyzed two variants of an IoT botnet named “Masuta” where we observed the involvement of a well-known IoT threat actor and discovered a router exploit being weaponized for the first time in a botnet campaign.” reads the analysis published by NewSky.
“We were able to get hands on the source code of Masuta (Japanese for “master”) botnet in an invite only dark forum. After analyzing the configuration file., we saw that Masuta uses 0xdedeffba instead of Mirai’s 0xdeadbeef as the seed of the cipher key, hence the strings in the configuration files were effectively xored by ((DE^DE)^FF) ^BA or 0x45.”
The Satori botnet is a variant of the Mirai botnet first discovered by the group of experts MalwareMustDie, it made the headlines at the end of 2016 when it was involved in hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
Masuta also targets routers using default credentials, one of the versions analyzed by the experts dubbed “PureMasuta” relies on the old network administration EDB 38722 D-Link exploit.
Researchers noticed a rise in the Masuta attacks since September, their honeypots observed 2400 IPs involved in the botnet in last three months and experts believe that other routers will be recruited in the next months.

The flaw triggered by the EDB 38722 D-Link exploit was discovered in 2015 by the researchers Craig Heffner, it affects the D-Link’s Home Network Administration Protocol.
“The weaponized bug introduced in PureMasuta botnet is in the HNAP (Home Network Administration Protocol) which itself is based on the SOAP protocol.” continues the analysis published by NewSky.
“It is possible to craft a SOAP query which can bypass authentication by using hxxp://purenetworks.com/HNAP1/GetDeviceSettings. Also, it is feasible to run system commands (leading to arbitrary code execution) because of improper string handling. When both issues are combined, one can form a SOAP request which first bypasses authentication, and then causes arbitrary code execution.”
The experts explained that a string like the following one will cause a reboot.
SOAPAction: “hxxp://purenetworks.com/HNAP1/GetDeviceSettings/`reboot`”
An attacker can run any command inserted after ‘GetDeviceSettings’, this mechanism is used by the PureMasuta bot to run a
wget
to fetch and run a shell script and take over the target router.
The experts noticed that the command and control server (93.174.93.63) used by PureMasuta variant is the same as used in the original Masuta variants, this means that PureMasuta is an evolution of the botnet operated by the same threat actors.
NewSky attributes the Masuta botnet to an entity dubbed “Nexus Zeta”, the name comes from the C&C URL nexusiotsolutions(dot)net, this URL is the same used by the Satori botnet.
Bell Canada suffers a data breach for the second time in less than a year
24.1.2018 securityaffairs Incindent
Bell Canada is notifying customers about a data breach that exposed personal data of roughly 100,000 individuals, this is the second security breach in a few months.
Bell Canada is notifying customers about a data breach that exposed personal data of roughly 100,000 individuals, including names, phone numbers, email addresses, usernames and account numbers.
“The protection of consumer and corporate information is of primary importance to Bell,” John Watson, Executive Vice-President of Customer Experience at Bell Canada, told customers. “We work closely with the RCMP and other law enforcement agencies, government bodies and the broader technology industry to combat the growth of cyber crimes.”
The Royal Canadian Mounted Police has launched an investigation into the security breach at Bell Canada.
“We are following up with Bell to obtain information regarding what took place and what they are doing to mitigate the situation, and to determine follow up actions,” said the federal privacy watchdog’s spokeswoman Tobi Cohen.
Bell company added that there is no evidence that financial data (i.e. credit card data) has been compromised.
Bell Canada
This the second time that Bell Canada has been a victim of a data breach, in May 2017 an anonymous hacker obtained access to about 1.9 million active email addresses and about 1,700 customer names and active phone numbers.
As part of the incident response procedure, Bell confirmed to have implemented additional security measures, for accounts’ authentication.
Bell Canada advised users to monitor their financial and online accounts for unauthorized activity and recommends customers to use strong passwords and frequently change them.
The Canadian Government plans to review the Personal Information Protection and Electronic Documents Act that would require companies to notify data breaches.
Unfortunately, until now only the province Alberta has mandatory reporting requirements for private-sector companies that suffer a data breach.
Less than 10% of Gmail users enabled two-factor authentication
24.1.2018 securityaffairs Safety
According to Google software engineer Grzegorz Milka, less than 10 percent of its users have enabled two-factor authentication (2FA) for their accounts.
The availability of billions of credentials in the criminal underground due to the numerous massive data breaches occurred in the last years makes it easy for crooks to take over users’ accounts.
We always suggest enabling two-factor authentication to improve the security of our accounts, unfortunately, the suggestion is often ignored.
“Even if someone else gets your password, it won’t be enough to sign in to your account,” states Google’s page on 2FA.
According to Google software engineer Grzegorz Milka, less than 10 percent of its users have enabled two-factor authentication (2FA) for their accounts.
Considering that Google has more than 2 billion monthly active devices, the number of exposed accounts is very huge.
Milka made the disconcerting revelation at the Usenix’s Enigma 2018, two-factor authentication (2FA) implemented by Google allows its users to access the account by providing login credentials along with an authentication code sent to the user via SMS or voice call or generated through the Google mobile app.

Source: The Register
This data demonstrates the lack of awareness of cyber threats and the way to mitigate them.
Many users believe that configure and use 2FA for their accounts can make their experience worse.
The Register asked Milka why Google didn’t just make two-factor mandatory across all accounts and received the following answer:
“The answer is usability,” he replied. “It’s about how many people would we drive out if we force them to use additional security.”
Contrary to what you can think, it is very easy to enable 2FA for your account, Google published a step-by-step guide.
The risk of identity theft increases when users share the same credentials among many web services.
Milka also cited a 2016 Pew study saying that only 12 percent of Americans use a password manager.
On the other side, Google is working to improve both the users’experience and security for example to employing machine learning systems that are able to spot suspicious activities related to the accounts under accounts.
For example, usually, when an attacker gets access to an account, he shuts down notification to the legitimate owner and starts exploring the content of the email by searching for passwords, license, and activation codes, cryptocurrency wallet addresses and credentials, intimate photos, and other sensitive documents, including copies of ID cards.
When Google detects one of the above actions immediately triggers mitigation countermeasures.
SamSam Operators Make $325,000 in 4 Weeks
23.1.2018 securityweek Ransomware
Numerous SamSam attacks over the past month or so have paid off to the ransomware’s operators, as they made over $325,000 in a short period of time, security researchers with Cisco Talos say.
Starting last month, the malware began targeting organizations across multiple industries including government, healthcare and ICS in a series of attacks that appear to be rather opportunistic in nature. The impact, however, was wider, especially in the healthcare sector, where patients were affected too, not just the hit organizations.
On January 11, the ransomware hit Hancock Health, headquartered in Greenfield, Indiana, a hospital that ended up paying $55,000 to regain access to its files. Adams Memorial Hospital in Decatur, Indiana, and Allscripts, a major electronic health record (EHR) company headquartered in Chicago, IL (which confirmed to SecurityWeek that roughly 1,500 clients were impacted), were also hit by SamSam.
Other organizations were impacted as well, yet the security researchers still haven’t figured out what infection vector the attackers used. Previously, SamSam operators have been compromising a machine within the network and then moving laterally to inject code and execute the ransomware.
In a report released in March last year, Javelin Networks explained that SamSam’s operators have been using stolen domain credentials to gain access to a host, then leveraging Active Directory for reconnaissance purposes, and later moving laterally through the network.
In 2016, SamSam was observed targeting vulnerable JBoss hosts, and Cisco believes that compromised RDP/VNC servers might have been used in the recent wave of attacks, allowing SamSam operators to obtain an initial foothold.
As part of the new attacks, string obfuscation and improved anti-analysis techniques were employed. The attackers used a loader to decrypt and execute an encrypted ransomware payload, a mechanism they have been employing since at least October 2017.
The loader, a simple .NET assembly with no obfuscation, searches for files with the extension .stubbin in its execution directory, as these contain SamSam’s encrypted payload. The loader appears derived from an example posted on the Codeproject.com website.
The ransomware operators are believed to be deploying the malware manually. They also use symmetric encryption keys that are randomly generated for each file.
The actor behind the attacks was highly focused on preventing the forensic recovery of the malware sample itself and didn’t simply rely on obfuscating the running malware code. To reduce the chances of obtaining the payload for analysis, the password necessary for the loader to decrypt the payload is passed as a parameter.
Analysis of the code didn’t reveal automated mechanism for contacting a Tor address hardcoded in the malware, and Cisco believes that victim identification with the associated RSA private key is done manually or using another tool.
“The Tor onion service and the Bitcoin wallet address are hardcoded into the payload whilst the public key is stored in an external file with the extension .keyxml,” Cisco explains.
The wallet employed in this campaign was used for multiple victims, and the security researchers discovered that the first payment into the wallet was received on December 25, 2017. However, there is a chance that other Bitcoin wallets are also used.
The Bitcoin wallet address received approximately 30.4 Bitcoin at the time of analysis, meaning that the SamSam operators made over $325,217.07 since December 25. Within its first year of operation, between 2015 and 2016, SamSam is believed to have made its operators $450,000 richer.
One thing that SamSam victims should keep in mind, however, is that the ransomware does not delete Volume Shadow Copies. It also works by creating an encrypted version of the targeted file and then deleting the original using the regular Windows API.
“Although unlikely, due to block overwriting, recovery of the original files from the versions of affected folders saved by the operating system may be possible,” Cisco says.
HP, Dell Halt BIOS Updates Over Buggy CPU Patches
23.1.2018 securityweek Vulnerebility
Dell, HP and other system manufacturers have advised customers not to install the recent BIOS updates designed to address the Spectre and Meltdown CPU vulnerabilities due to unstable code delivered by Intel.
The Spectre and Meltdown vulnerabilities, which allow malicious applications to bypass memory isolation mechanisms and access sensitive data, were disclosed on January 3, one week before initially planned. As a result, vendors rushed to roll out patches and many of them turned out to be unstable.
Both software and firmware patches have caused problems. On Monday, Intel told users to stop deploying microcode updates that fix Spectre and Meltdown until it addresses issues that led to reboots and other unpredictable system behavior.
Intel initially said only systems running Broadwell and Haswell CPUs experienced more frequent reboots, but similar behavior was later observed on Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms as well.
The company now says it has identified the root cause of the reboot issue and is “making good progress in developing a solution to address it.” In the meantime, it has advised OEMs, system manufacturers, software vendors, and cloud service providers to stop deploying current versions.
Following Intel’s announcement, Dell told customers not to deploy the BIOS updates designed to address one of the Spectre vulnerabilities, specifically CVE-2017-5715, which is known as “Variant 2.”
“Dell is advising that all customers should not deploy the BIOS update for the Spectre (Variant 2) vulnerability at this time. We have removed the impacted BIOS updates from our support pages and are working with Intel on a new BIOS update that will include new microcode from Intel,” the company said.
Dell told users who have already deployed the BIOS updates to revert to a previous version until the issue has been resolved.
HP has also removed BIOS softpaqs from its website and expects to reissue updates with previous Intel microcode starting with January 25.
Lenovo informed customers that it has pulled UEFI firmware updates for systems with Intel Broadwell and Haswell processors.
VMware has also decided to delay new releases of microcode updates until Intel addresses these problems.
Some systems running Red Hat and Ubuntu operating systems failed to boot after Spectre and Meltdown patches were installed.
The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Variant 2 requires microcode updates for a complete fix. While some software updates have also been known to cause problems, vendors have still advised users to deploy them in order to protect their systems against potential attacks.
“The current unstable code for the Spectre and Meltdown CPU patches leaves end users vulnerable with no available options other than to wait for a stable fix. In times like these, customers should be extra vigilant to ensure they have not been compromised. Network traffic analytics should be used to monitor their environment for anomalous traffic patterns and unusual behaviors,” Bob Noel, Director of Strategic Relationships and Marketing for Plixer, told SecurityWeek.
“The secondary problem this unstable patch code creates is a general hesitancy for end users to quickly apply future patches. Early adopters of these patches experienced hardware reboots and downtime, which is likely to leave them wary of becoming early adopters for future patches,” Noel added.
IoT Devices Fuel Complex DDoS Attacks: Report
23.1.2018 securityweek IoT
The continuous use of compromised Internet of Things (IoT) devices to launch distributed denial of service (DDoS) attacks has helped cybercriminals increase the complexity of their assaults, NETSCOUT’s Arbor Networks says.
According to the company’s 13th Annual Worldwide Infrastructure Security Report (WISR), attackers focused on increasing complexity in 2017, and the exploitation of IoT devices helped them achieve this goal. The frequency of attacks has increased as well, following a trend seen for the past several years.
The report is based on 390 responses received from a mix of Tier 1, Tier 2 and Tier 3 service providers, hosting, mobile, enterprise and other types of network operators globally. More than half of respondents are headquartered and operate in North America.
Last year, 57% of enterprise, government and education (EGE) respondents and 45% of data center operators had their network resources depleted due to DDoS attacks. Arbor observed 7.5 million DDoS attacks in 2017.
The largest attack reported by a service provider peaked at 600 Gigabits per second (Gbps), with only one quarter of respondents observing attacks that peaked at over 100Gbps. While the number of very large incidents decreased, however, attackers used more metered attack volumes to achieve their goals, the report reads.
Attack durations surged last year, with 29% of service providers saying they experienced attacks of over 12 hours. 45% of respondents said they experienced more than 21 attacks per month, while 17% were hit more than 500 times per month.
Service providers reported more volumetric attacks, while enterprises noticed a 30% increase in stealthy application-layer attacks. Multi-vector attacks hit 59% of service providers and 48% of enterprises, combining high volume floods, application-layer attacks, and TCP-state exhaustion assaults in a single sustained offensive.
The number of enterprises experiencing stealthy application-layer attacks increased 30% last year. 73% of the attacks targeted HTTP, 69% targeted DNS, and 68% targeted HTTPS. The number of assaults targeting encryption servers went up as well, with 53% of detected attacks aimed at the application layer and 42% of them targeting the SSL/TLS protocol.
Organizations appear to better understand the need for defenses and 77% of responding enterprises said DDoS was either a part of their business or their IT risk assessments in 2017.
DDoS attacks had various but more severe consequences, ranging from reputation/brand damage (57% of respondents) and concerns of customer churn (48% of respondents). The financial impact of DDoS attacks was double compared to 2016, as 56% of respondents admitted to losses of between $10,000 and $100,000.
The increase in threat landscape’s complexity challenged network and security teams. 88% of service providers said they use Intelligent DDoS Mitigation Solutions, while 36% revealed they employ technology that automates DDoS mitigation.
Demand for managed security services is increasing as well, driven by a surge in attack frequency, and 38% of enterprises revealed they rely on third-party and outsourced services (up from 28% the previous year). However, only 50% of respondents said they carried out defensive drills.
Nearly half of respondents have difficulty hiring and retaining skilled personnel. Thus, organizations have less time to conduct incident response training. Fewer organizations and service providers are carrying out defensive drills or plan on doing so, the report reveals.
“Attackers focused on complexity this year, leveraging weaponization of IoT devices while shifting away from reliance on massive attack volume to achieve their goals. Attackers have been effective, and the proportion of enterprises experiencing revenue loss due to DDoS nearly doubled this year, emphasizing the significance of the DDoS threat,” said Darren Anstee, NETSCOUT Arbor Chief Technology Officer.
Ransomware was the most commonly experienced attack last year, with DDoS in second place, but DDoS represented the top threat observed by service providers. Such assaults remain the top concern for 88% of these organizations in 2018 as well, fueled by the weaponized IoT botnets and the attackers’ ability to gain access to sophisticated assault techniques.
Facebook Offers $100,000 Grants for Improving Internet Security
23.1.2018 securityweek Social
Facebook announced on Monday that it’s prepared to award $100,000 grants for research proposals focusing on improving online security, privacy and safety.
The new project, called “Secure the Internet Grants,” is part of the initiative announced last summer by Facebook CSO Alex Stamos. Stamos revealed at the Black Hat conference that the social media giant had prepared $1 million in funding to encourage original defensive research.
For Secure the Internet Grants, university researchers and faculty, NGOs, and non-profit organizations have been invited to submit proposals for innovative and practical technology. A wide range of topics are accepted, including anti-phishing, user safety, post-password authentication, abuse detection and reporting, privacy-preserving technologies, and user security in emerging markets.Facebook launches Secure the Internet Grants
Applicants are required to submit a 2-page proposal detailing their ideas and how the grant funding will be used to put them into practice. Facebook is prepared to award up to $100,000 per proposal, depending on the specific requirements.
The deadline for submitting proposals is March 30. Selected award recipients will be notified in May and winners will be announced at Black Hat USA 2018.
“Good defense comes from understanding offense,” Stamos said last year at Black Hat. “The research presented at Black Hat and elsewhere is critical in understanding the kinds of flaws we face now and in the future, and it helps us build a base of knowledge that can be used to design more trustworthy systems. That being said, the balance of incentives is a bit off, and we need to figure out ways to encourage and celebrate risk-taking defensive research alongside spectacular vulnerability demonstrations.”
Facebook has made significant investments in securing its own platform and the Internet in general.
Last year, Facebook awarded $100,000 to a team of researchers as part of the 2017 Internet Defense Prize for designing a novel technique of detecting spear-phishing attacks in enterprise environments.
As for its own platform, the social media company paid out nearly $900,000 last year for vulnerabilities reported by external researchers, bringing the total paid since the launch of its bug bounty program in 2011 to more than $6.3 million.
Facebook’s founder and CEO, Mark Zuckerberg, recently stated that protecting the community is more important than maximizing profits.
Insurers, Nonprofits Most Likely to Fall for Phishing: Study
23.1.2018 securityweek Phishing
The employees of insurance companies and non-profit organizations are most likely to fall for phishing attacks, according to a study conducted by security awareness training firm KnowBe4.
KnowBe4’s study is based on data collected from six million users across 11,000 organizations. The company has tested users at three stages: before any awareness training, after 90 days of initial training and simulated phishing, and after one year of training.
The average phish-prone percentage, represented by the percentage of employees that clicked on a link or opened an attachment during testing, was 27% across all industries and organizations of all sizes.
In the case of small and mid-size organizations (under 1,000 employees), insurance companies have the highest percentage of phish-prone employees, specifically 35% and 33%. In the case of large organizations, nonprofits are at the top of the list with roughly 31% of employees taking the bait during the baseline phishing tests conducted by KnowBe4.
The lowest phish-prone percentage was recorded in large business services organizations, where only 19% of employees took the bait.
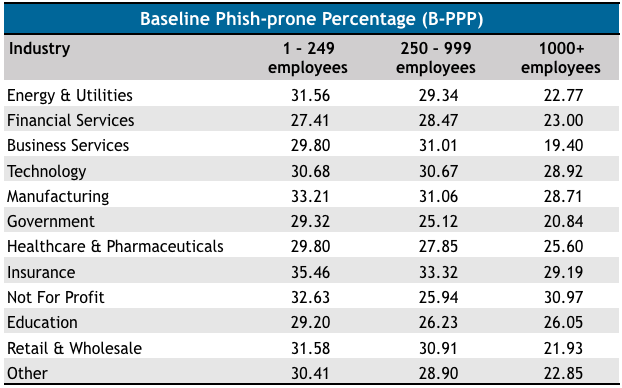
Unsurprisingly, 90 days after undergoing initial training and simulated phishing, the percentage of employees that fell for phishing attacks dropped significantly across all sectors and organizations of all sizes.
For example, in the case of the insurance industry, the phish-prone percentage dropped to 13% in small and large organizations, and 16% in mid-size companies. In the case of nonprofits, it dropped to 16-17%.
After one year of training, the phish-prone percentage dropped to 1-2% in most cases. The highest percentage of employees that still fell for phishing attacks, roughly 5%, was in large organizations in the energy and utilities, financial services, insurance, and education sectors.
“The new research uncovered some surprising and troubling results. However, it also demonstrates the power of deploying new-school security awareness training by lowering a 27 percent Phish-prone result to just over two percent,” said Stu Sjouwerman, CEO of KnowBe4.
SaaS webservice for Seagate’s GoFlex Home Storage devices vulnerable to MiTM and XSS
23.1.2018 securityaffairs Vulnerebility
Security expert found more than 33000 Seagate’s GoFlex Home network-attached storage (NAS) devices vulnerable exposed online.
Seagate has patched several vulnerabilities in its Personal Cloud and GoFlex products, but unfortunately, some flaws remain unpatched.
In September, researcher Aditya K. Sood discovered vulnerabilities that can be exploited by attackers to launch cross-site scripting (XSS) and man-in-the-middle (MitM) attacks against Seagate GoFlex Home NAS product.
GoFlex Home NAS devices run a web service accessible at seagateshare.com, that allows users to remotely manage the device and its content. Customers can access their storage by providing the device name, and login credentials.

The GoFlex firmware runs an HTTP server that requires users to enable port forwarding on their router in order to connect to the web service.
Sood noticed that the HTTP server supports the obsolete protocols SSLv2 and SSLv3, while the web service seagateshare.com service supports SSLv3.
Both protocols expose the users to MiTM attacks, including DROWN and POODLE.
“It has been discovered that embedded server still supports SSLv2 / SSLv3 whereas the
seagateshare.com supports SSLv3. We have looked into 50,000+ devices that are running on unique IPs that have SSLv2/ SSLv3 enabled.” states the analysis published by the expert. “Additionally, during standard tests, we have collected 17000+ URLs of seagateshare.com with unique device_ids.”
The expert also discovered an XSS in the seagateshare.com website that could be exploited by an attacker to execute malicious code in the context of a user’s browsing session by tricking the victim into clicking on a specially crafted link.
The bad news for Seagate users is that the company has only fixed the XSS flaw, it doesn’t plan on fixing the remaining issue related to the use of SSLv2 and SSLv3.
Intel Warns Users Not to Install Its 'Faulty' Meltdown and Spectre Patches
23.1.2018 thehackernews Vulnerebility
Don't install Intel's patches for Spectre and Meltdown chip vulnerabilities.
Intel on Monday warned that you should stop deploying its current versions of Spectre/Meltdown patches, which Linux creator Linus Torvalds calls 'complete and utter garbage.'
Spectre and Meltdown are security vulnerabilities disclosed by researchers earlier this month in many processors from Intel, ARM and AMD used in modern PCs, servers and smartphones (among other devices), which could allow attackers to steal your passwords, encryption keys and other private information.
Since last week, users are reporting that they are facing issues like spontaneous reboots and other 'unpredictable' system behaviour on their affected computers after installing Spectre/Meltdown patch released by Intel.
Keeping these problems in mind, Intel has advised OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of its patches until the chip giant develops 'a solution to address it.'
"We have now identified the root cause for Broadwell and Haswell platforms, and made good progress in developing a solution to address it," Intel said in a press release published on Monday.
"Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed."
Linus Torvalds Calls Intel's Meltdown/Spectre Patches 'Garbage'
Meanwhile, in a public email conversation, Linus Torvalds complains that he is not happy with the Intel's approach of protecting the Linux kernel from Spectre and Meltdown flaws, saying:
"They do literally insane things. They do things that do not make sense... I really don't want to see these garbage patches just mindlessly sent out. … I think we need something better than this garbage." Torvalds said.
Intel patches require users to manually opt-in and enable the fix while their computers boot up when the security patches for such a critical flaw should be applied automatically.
It's because the 'Indirect Branch Restricted Speculation' or IBRS—one of three new hardware patches offered as CPU microcode updates by Intel—is so inefficient that it would result in widespread performance hits if rolled out worldwide.
So in other words, to prevent bad performance in benchmark tests, Intel is offering users to choose between performance and security.
New Intel patches will be available soon. Stay tuned.