
Maersk Reinstalled 50,000 Computers After NotPetya Attack
26.1.2018 securityweek Ransomware
Jim Hagemann Snabe, chairman of Danish shipping giant A.P. Moller–Maersk, revealed this week at the World Economic Forum in Switzerland that the company was forced to reinstall software on nearly 50,000 devices following the NotPetya attack.
In a panel on securing a common future in cyberspace, Hagemann Snabe, former co-CEO of SAP, said the NotPetya malware had hit a large number of systems housed by the company.
According to Hagemann Snabe, Maersk’s IT team had to reinstall software on its entire infrastructure, including 45,000 PCs and 4,000 servers, totaling 2,500 applications.
The mammoth task took only 10 days to complete, during which time the company manually coordinated operations. This was not easy considering that Maersk is the largest container shipping company in the world and it’s responsible for roughly 20 percent of world trade. Hagemann Snabe noted that a ship carrying 10,000-20,000 containers docks into a port every 15 minutes.
Maersk employees managed to manually process 80 percent of the work volume, but the NotPetya incident still cost the company $250-$300 million.
In the aftermath of the cyberattack, the shipping giant realized that its cybersecurity capabilities had been only “average,” but Hagemann Snabe says the company is now determined to improve cybersecurity to the point where it “becomes a competitive advantage.”
“We need a very significant increase in our level of understanding of this problem,” Hagemann Snabe told the panel. “It is time to stop being naive when it comes to cybersecurity. I think many companies will be caught if they are naive – even size does not help you. I think it is very important that we are not just reactive but proactive, and I think we can’t be average, we got to be the best we can.”
Hagemann Snabe believes his company was probably collateral damage in a state-sponsored attack.
The NotPetya malware outbreak, which U.S. and Ukrainian government agencies have attributed to Russia, affected tens of thousands of systems in more than 65 countries. Many of the victims were located in Ukraine, the home of a tax software firm whose product was used as the main attack vector.
Researchers initially believed NotPetya (also known as PetrWrap, exPetr, GoldenEye and Diskcoder.C) was a piece of ransomware. However, a closer analysis revealed that it was actually a wiper.
In addition to Maersk, the list of major organizations hit by the incident includes Rosneft, Merck, FedEx-owned TNT Express, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain. These companies reported that the attack had cost them tens and even hundreds of millions of dollars.
The Dutch intelligence service AIVD ‘hacked’ Russian Cozy Bear systems for years
26.1.2018 securityaffairs BigBrothers
Spying on spies – The hackers from the Dutch intelligence service AIVD ‘compromised’ for years the network of the Russian APT Cozy Bear.
It’s not a mystery, technology firms that intend to work with Russia need to allow the Government experts to scan their code for backdoors and vulnerabilities.
The problem is that this software is often used by the US Government, this means that Russian experts could found bugs or backdoors to exploit in cyber attacks against US Agencies.
Many tech giants already allowed their software review, including McAfee, SAP, Symantec, and HPE, the risk is that foreign Governments could exploit a bug or a backdoor to control them.
Anyway, other firms like Trend Micro has refused to allow the Russians to conduct a source code review of their products.
Of course, the companies defend their position clarifying that the code review s were done under controlled conditions and that not code was allowed to be copied.
News of the day is that the Dutch intelligence service AIVD ‘hacked’ Russian state-sponsored hackers.
The news was reported by the newspaper de Volkskrant, AIVD in 2014 monitored the activity of the Russian APT Cozy Bear (aka APT29) and its efforts to hack into systems at the US Democratic Party‘s and US government servers.
Dutch intelligence service AIVD provided the FBI with crucial information about Russian interference with the American elections.
The AIVD cyber spies compromised security cameras surrounding the building used by the Cozy Bear crew, the Dutch agents were looking for known Russian spies accessing the structure.
“Hackers from the Dutch intelligence service AIVD have provided the FBI with crucial information about Russian interference with the American elections,” reports the Dutch daily newspaper Volkskrant.nl.
“That’s how the AIVD becomes witness to the Russian hackers harassing and penetrating the leaders of the Democratic Party, transferring thousands of emails and documents. It won’t be the last time they alert their American counterparts.”

The Dutch hackers conducted a Computer Network Attack against Russians, they are involved in offensive operations aim to compromise adversary networks.
The unit operates under the Joint Sigint Cyber Unit, a collaborative unit of the AIVD and the Dutch Military Intelligence and Security Service MIVD, of about 300 people.
The Dutch cyber unit is composed of about 80-100 people, part of them is focused on intercepting or managing sources, while another team is dedicated to Computer Network Defence.
It’s unknown what exact information the Dutch hackers collected, the unique certainty is that it linked Cozy Bear to the attacks against the US Government.
“Three American intelligence services state with ‘high confidence’ that the Kremlin was behind the attack on the Democratic Party. That certainty, sources say, is derived from the AIVD hackers having had access to the office-like space in the center of Moscow for years. This is so exceptional that the directors of the foremost American intelligence services are all too happy to receive the Dutchmen.” continues the newspaper.
The Cozy Bear hackers are located in a university building near the Red Square, the team is composed on average of ten people. The entrance is in a curved hallway controlled by a security camera that was hacked by Dutch cyber spies.
Thanks to the AIVD, the NSA was able to locate the command and control servers used by Cozy Bear while it was targeting the systems at the State Department.
“Access to Cozy Bear turns out to be a goldmine for the Dutch hackers. For years, it supplies them with valuable intelligence about targets, methods and the interests of the highest ranking officials of the Russian security service. From the pictures taken of visitors, the AIVD deduces that the hacker group is led by Russia’s external intelligence agency SVR.” continues the Volkskrant.
“There’s a reason the AIVD writes in its annual report about 2014 that many Russian government officials, including president Putin, use secret services to obtain information.”
The AIVD hackers left Cozy Bear’s computer network after an investigation that lasted for 1 and 2,5 years, likely because the Russians cut off their access.
Stealth CrossRAT malware targets Windows, MacOS, and Linux systems
26.1.2018 securityaffairs Virus
The popular former NSA hacker Patrick Wardle published a detailed analysis of the CrossRAT malware used by Dark Caracal for surveillance.
Last week a joint report published by security firm Lookout and digital civil rights group the Electronic Frontier Foundation detailed the activity of a long-running hacking group linked to the Beirut Government and tracked as Dark Caracal. The hacking campaigns conducted by Dark Caracal leverage a custom Android malware included in fake versions of secure messaging apps like Signal and WhatsApp.
The report detailed a new strain of cross-platform malware tracked as CrossRAT (version 0.1), it is remote access Trojan that can infect systems based on Windows, Solaris, Linux, and macOS.
The malware implements classic RAT features, such as taking screenshots and running arbitrary commands on the infected systems.
At the time of its discovery, the malware was not detected by almost all the anti-virus software (only two out of 58).

The Dark Caracal attack chain implemented relies primarily on social engineering, the hackers used messages sent to the victims via Facebook group and WhatsApp messages. At a high-level, the hackers have designed three different kinds of phishing messages to trick victims into visiting a compromised website, a typical watering hole attack.
CrossRAT is written in Java programming language, for this reason, researchers can easily decompile it.
The popular former NSA hacker Patrick Wardle published a detailed analysis of the CrossRAT malware.
Once executed on the victim’s system, CrossRAT will determine the operating system it’s running on to trigger the proper installation procedure.
On Linux systems, the RAT also attempts to query systemd files to determine the distribution (i.e. Arch Linux, Centos, Debian, Kali Linux, Fedora, and Linux Mint).
Wardle explained that the author implemented specific persistence mechanisms for each operating system. Once installed the malware will attempt to contact the C&C server.
“Now the malware has persistently installed itself, it checks in with the C&C server for tasking. As noted the EFF/Lookout report the malware will connect to flexberry.com on port 2223. ” states the analysis published by Wardle.
The expert discovered that the CrossRAT includes reference ‘jnativehook Java library that provides global keyboard and mouse listeners for Java, but didn’t see any code within that implant that referenced the jnativehook package, likely because the analyzed version was still under development.
Wardle detailed the persistence mechanism implemented for each OS, this information is useful to detect the presence of CrossRAT on a system.
Windows:
Check the HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ registry key. If infected it will contain a command that includes, java, -jar and mediamgrs.jar.
Mac:
Check for jar file, mediamgrs.jar, in ~/Library. Also look for launch agent in /Library/LaunchAgents or ~/Library/LaunchAgents named mediamgrs.plist.
Linux:
Check for jar file, mediamgrs.jar, in /usr/var. Also look for an ‘autostart’ file in the ~/.config/autostart likely named mediamgrs.desktop.
Beware! Undetectable CrossRAT malware targets Windows, MacOS, and Linux systems
26.1.2018 thehackernews Virus
Are you using Linux or Mac OS? If you think your system is not prone to viruses, then you should read this.
Wide-range of cybercriminals are now using a new piece of 'undetectable' spying malware that targets Windows, macOS, Solaris and Linux systems.
Just last week we published a detailed article on the report from EFF/Lookout that revealed a new advanced persistent threat (APT) group, called Dark Caracal, engaged in global mobile espionage campaigns.
Although the report revealed about the group's successful large-scale hacking operations against mobile phones rather than computers, it also shed light on a new piece of cross-platform malware called CrossRAT (version 0.1), which is believed to be developed by, or for, the Dark Caracal group.
CrossRAT is a cross-platform remote access Trojan that can target all four popular desktop operating systems, Windows, Solaris, Linux, and macOS, enabling remote attackers to manipulate the file system, take screenshots, run arbitrary executables, and gain persistence on the infected systems.
According to researchers, Dark Caracal hackers do not rely on any "zero-day exploits" to distribute its malware; instead, it uses basic social engineering via posts on Facebook groups and WhatsApp messages, encouraging users to visit hackers-controlled fake websites and download malicious applications.
CrossRAT is written in Java programming language, making it easy for reverse engineers and researchers to decompile it.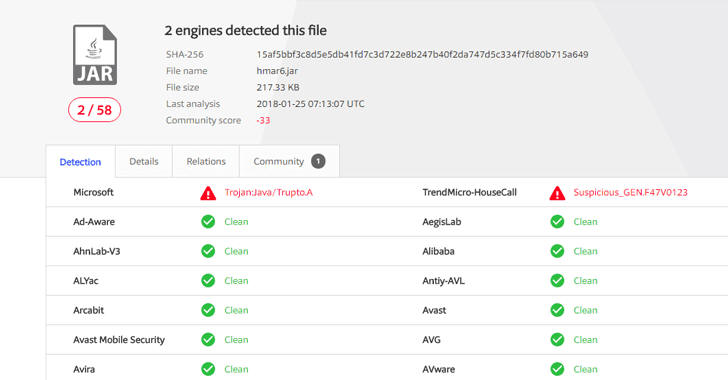
Since at the time of writing only two out of 58 popular antivirus solutions (according to VirusTotal) can detect CrossRAT, ex-NSA hacker Patrick Wardle decided to analyse the malware and provide a comprehensive technical overview including its persistence mechanism, command and control communication as well as its capabilities.
CrossRAT 0.1 — Cross-Platform Persistent Surveillance Malware
Once executed on the targeted system, the implant (hmar6.jar) first checks the operating system it's running on and then installs itself accordingly.
Besides this, the CrossRAT implant also attempts to gather information about the infected system, including the installed OS version, kernel build and architecture.
Moreover, for Linux systems, the malware also attempts to query systemd files to determine its distribution, like Arch Linux, Centos, Debian, Kali Linux, Fedora, and Linux Mint, among many more.
CrossRAT then implements OS specific persistence mechanisms to automatically (re)executes whenever the infected system is rebooted and register itself to the C&C server, allowing remote attackers to send command and exfiltrate data.
As reported by Lookout researchers, CrossRAT variant distributed by Dark Caracal hacking group connects to 'flexberry(dot)com' on port 2223, whose information is hardcoded in the 'crossrat/k.class' file.
CrossRAT Includes Inactive Keylogger Module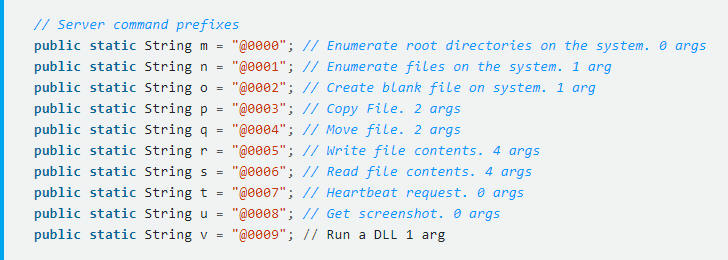
The malware has been designed with some basic surveillance capabilities, which get triggered only when received respective predefined commands from the C&C server.
Interestingly, Patrick noticed that the CrossRAT has also been programmed to use 'jnativehook,' an open-source Java library to listen to keyboard and mouse events, but the malware does not have any predefined command to activate this keylogger.
"However, I didn’t see any code within that implant that referenced the jnativehook package—so at this point it appears that this functionality is not leveraged? There may be a good explanation for this. As noted in the report, the malware identifies it’s version as 0.1, perhaps indicating it’s still a work in progress and thus not feature complete," Patrick said.
How to Check If You're Infected with CrossRAT?
Since CrossRAT persists in an OS-specific manner, detecting the malware will depend on what operating system you are running.
For Windows:
Check the 'HKCU\Software\Microsoft\Windows\CurrentVersion\Run\' registry key.
If infected it will contain a command that includes, java, -jar and mediamgrs.jar.
For macOS:
Check for jar file, mediamgrs.jar, in ~/Library.
Also look for launch agent in /Library/LaunchAgents or ~/Library/LaunchAgents named mediamgrs.plist.
For Linux:
Check for jar file, mediamgrs.jar, in /usr/var.
Also look for an 'autostart' file in the ~/.config/autostart likely named mediamgrs.desktop.
How to Protect Against CrossRAT Trojan?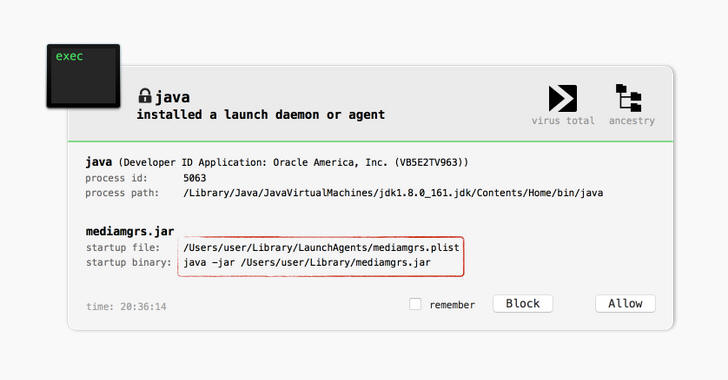
Only 2 out of 58 antivirus products detect CrossRAT at the time of writing, which means that your AV would hardly protect you from this threat.
"As CrossRAT is written in Java, it requires Java to be installed. Luckily recent versions of macOS do not ship with Java," Patrick said.
"Thus, most macOS users should be safe! Of course, if a Mac user already has Java installed, or the attacker is able to coerce a naive user to install Java first, CrossRAT will run just dandy, even on the latest version of macOS (High Sierra)."
Users are advised to install behaviour-based threat detection software. Mac users can use BlockBlock, a simple utility developed by Patrick that alerts users whenever anything is persistently installed.
Critical Flaw Hits Popular Windows Apps Built With Electron JS Framework
26.1.2018 thehackernews Vulnerebility
A critical remote code execution vulnerability has been reported in Electron—a popular web application framework that powers thousands of widely-used desktop applications including Skype, Signal, Wordpress and Slack—that allows for remote code execution.
Electron is an open-source framework that is based on Node.js and Chromium Engine and allows app developers to build cross-platform native desktop applications for Windows, macOS and Linux, without knowledge of programming languages used for each platform.
The vulnerability, assigned as the number CVE-2018-1000006, affects only those apps that run on Microsoft Windows and register themselves as the default handler for a protocol like myapp://.
"Such apps can be affected regardless of how the protocol is registered, e.g. using native code, the Windows registry, or Electron's app.setAsDefaultProtocolClient API," Electron says in an advisory published Monday.
The Electron team has also confirmed that applications designed for Apple's macOS and Linux are not vulnerable to this issue, and neither those (including for Windows) that do not register themselves as the default handler for a protocol like myapp://.
The Electron developers have already released two new versions of their framework, i.e. 1.8.2-beta.4, 1.7.11, and 1.6.16 to address this critical vulnerability.
"If for some reason you are unable to upgrade your Electron version, you can append—as the last argument when calling app.setAsDefaultProtocolClient, which prevents Chromium from parsing further options," the company says.
End users can do nothing about this vulnerability; instead, developers using Electron JS framework have to upgrade their applications immediately to protect their user base.
Much details of the remote code execution vulnerability have not been disclosed yet, neither the advisory named any of the vulnerable apps (that make themselves the default protocol handler) for security reason.
We will update you as soon as any details about the flaw come out.
EU Antitrust Regulators Fine Qualcomm $1.2 Billion Over Apple Deal
26.1.2018 thehackernews IT

The European Commission has levied a fine of €997 Million, approximately $1.2 Billion, against U.S. chipmaker Qualcomm Inc. for violating antitrust laws in a series of deals with Apple by "abusing its market dominance in LTE baseband chipsets."
According to the European Union (EU), Qualcomm paid Apple billions of dollars to make the iPhone-maker exclusively use its 4G chips in all its iPhones and iPads, reducing competition from other competing manufacturers in the LTE baseband chip industry like Intel.
The European Commission launched an investigation in 2015, which revealed that Qualcomm abused its market dominance in LTE baseband chipsets and struck a deal with Apple in 2011, which meant the iPhone maker would have to repay Qualcomm if it decided to use a rival's chipsets until the end of 2016, hurting innovation in the chip sector.
"This meant that no rival could effectively challenge Qualcomm in this market, no matter how good their products were. This is illegal under EU antitrust rules and why we have taken today's decision," EU competition commissioner Margrethe Vestager said in a press statement.
Apple received payments from Qualcomm for approximately 5 years between 2011 and 2016. The company still uses Qualcomm components in its iPhones and iPads, but it began using Intel LTE modems in its iPhone 7 and 7 Plus devices after the agreement ended.
The fine imposed on the chip maker is hefty, but won't hurt Qualcomm's bottom line significantly as it represents 4.9 percent of the company's turnover in 2017, according to the EU's antitrust commission.
Qualcomm said it 'strongly disagrees' with the European Commission's decision and will 'immediately appeal' it at the General Court of the European Union. The company also believes its agreement with Apple does not violate European Union competition law.
"We are confident this agreement did not violate EU competition rules or adversely affect market competition or European consumers," Qualcomm General Counsel Don Rosenberg said in a statement. "We have a strong case for judicial review, and we will immediately commence that process."
Not just one, Qualcomm is facing a patent fight with Apple over chip royalties, and simultaneously fending off a $100 billion hostile takeover from rival chipmaker Broadcom, but it rejected the bid last November, saying it 'dramatically undervalued' the company.
Yikes! Three armed men tried to rob a Bitcoin Exchange in Canada
26.1.2018 thehackernews Crime
As many non-tech savvy people think that Bitcoin looks like a Gold coin as illustrated in many stock images, perhaps these robbers also planned to rob a cryptocurrency exchange thinking that way.
All jokes apart, we saw one such attempt on Tuesday morning, when three men armed with handguns entered the offices of a Canadian Bitcoin exchange in Ottawa, and restrained four of its employees.
The intruders then struck one of the employees in the head with a handgun, asking them to make an outbound transaction from the cryptocurrency exchange.
A fifth employee in another cabin, who remained unseen in an office, called the police before any assets could be taken, and the robbers left empty-handed.
One of the suspects arrested later Wednesday after arriving police officers saw him run into a ravine north of Colonnade Road and deployed "extensive resources," including K-9 unit officers, to find him, CBC News reports.
"Police are looking for two additional suspects, both described as black males," the police says. "Investigators are also interested in identifying and speaking to a person of interest that was inside the premise as the suspects arrived. That person did not remain at the scene."
The suspect in custody, identified as 19-year-old Jimmy St-Hilaire, has been charged with the following offences:
5 counts of robbery with a firearm
5 counts of point a firearm
5 counts of forcible confinement
Wear disguise
Conspiracy to Commit an indictable offence
Carry concealed weapon
Possess firearm while prohibited
Possess weapon for committing an offence
Possess loaded regulated firearm
St-Hilaire is set to appear in court on January 24, 2018. Ottawa police are now looking for the remaining two suspects.
The authorities have not revealed the name of the cryptocurrency exchange.
A similar incident happened last month when armed robbers kidnapped a top executive at UK-registered crypto-exchange EXMO Finance and allegedly stole more than $1.8 million of Ether for releasing him.
The New York District Attorney's Office charged New Jersey native Louis Meza for the kidnapping and robbery, claiming Meza held "demanded that the victim turns over his cell phone, wallet, and keys while holding the victim at gunpoint."
Maersk chair revealed its company reinstalled 45,000 PCs and 4,000 Servers after NotPetya Attack
26.1.2018 securityaffairs Ransomware
The shipping giant Maersk chair Jim Hagemann Snabe revealed its company reinstalled 45,000 PCs and 4,000 Servers after NotPetya the attack.
The shipping giant Maersk was one of the companies that suffered the NotPetya massive attack, in August 2017 the company announced that it would incur hundreds of millions in U.S. dollar losses due to the ransomware massive attack.
According to the second quarter earnings report, there were expecting losses between $200 million and $300 million due to “significant business interruption” because the company was forced to temporarily halt critical systems infected with the ransomware.

Now the Møller-Maersk chair Jim Hagemann Snabe has shared further details on the attack suffered by the company during a speech at the World Economic Forum this week.
Snabe explained that the attack forced the IT staff to reinstall “4,000 new servers, 45,000 new PCs, and 2,500 applications,” practically “a complete infrastructure.”
The IT staff worked hard for ten days to restore normal operations.
“And that was done in a heroic effort over ten days,” Snabe said.
“Normally – I come from the IT industry – you would say that would take six months. I can only thank the employees and partners we had doing that.”
Snabe defined the incident as a “very significant wake-up call,” a strong security posture for a company is essential for the development of its business.
Snabe pointed out that Maersk was the victim of the militarization of a cyberspace, the damages were caused by a cyber weapon used by a foreign government to hit Ukraine.
Maersk ship docks worldwide every 15 minutes, unloading between 10,000 to 20,000 containers. The effects of the attack were dramatic and only the heroic effort of the staff that manually restored the normal situation allowed to contain the damages.
Snabe claimed only “a 20 per cent drop in volumes,” and described the efforts of its IT staff as “human resilience”.
Snabe is aware of the risks for companies that operate on the Internet and urges an improvement of infrastructure.
“There is a need for a radical improvement of infrastructure.” he said.
Maersk chair also highlighted the importance of collaboration between companies, technology companies, and law enforcement.