
Russia Infrastructure Spying Could Cause 'Total Chaos': UK Defence Minister
28.1.2018 securityweek BigBrothers
Britain's Defence Secretary Gavin Williamson has accused Russia of spying on its critical infrastructure as part of possible plans to create "total chaos" in the country that could "cause thousands and thousands of deaths".
In unusually alarmist words from a senior minister Williamson told the Daily Telegraph that, in its research on UK power supply connections with Europe, Moscow appeared intent on sowing "panic" and hurting Britain.
"What they are looking at doing is they are going to be thinking 'how can we just cause so much pain to Britain?'" he said in comments published Thursday night.
"Damage its economy, rip its infrastructure apart, actually cause thousands and thousands and thousands of deaths, but actually have an element of creating total chaos within the country."
Williamson, who only became defence chief in November after predecessor Michael Fallon resigned over allegations of misconduct, gave the interview at the outset of a new five-month defence review.
He is reportedly pressuring finance minister Philip Hammond to allocate more money to defence and scrap further cuts to Britain's strained armed forces.
In the interview the minister said Russia acts in a way "that any other nation would see as completely unacceptable".
Related: Learn More at SecurityWeek's ICS Cyber Security Conference
"Why would they keep photographing and looking at power stations, why are they looking at the interconnectors that bring so much electricity and so much energy into our country," he questioned in the paper.
"They are looking at these things because they are saying these are the ways that we can hurt Britain."
Earlier this week Fallon joined calls from the head of the army for more British military spending, amid warnings the country may struggle to match Russian battlefield capabilities.
Meanwhile the head of the National Cyber Security Centre said the country will likely face a major cyber-attack within two years.
Ciaran Martin told the Guardian it was inevitable a hostile actor would launch an online attack aimed at crippling Britain's critical infrastructure, such as energy supplies, and it was lucky not to have fallen victim to such a strike already.
Williamson, who is tipped as a possible future ruling Conservative party leader, described his scenario planning as "the real threat that I believe the country is facing at the moment."
A spokesman for the Ministry of Defence said it had nothing further to add to his remarks.
The Russian Embassy in London could not be reached for comment Thursday.
Japan's Crypto Exchange to Refund to Customers After Theft
28.1.2018 securityweek Incindent
Japan-based virtual currency exchange Coincheck said Sunday it will refund about $400 million to customers after hackers stole hundreds of millions of dollars' worth of digital assets.
The company said it will use its own funds to reimburse about 46.3 billion yen to all 260,000 customers who lost their holdings of NEM, the 10th biggest cryptocurrency by market capitalization.
On Friday, the company detected an "unauthorised access" of the exchange, and later suspended trading for all cryptocurrencies apart from bitcoin.
The resulting 58 billion yen ($530 million) loss exceeded the value of bitcoins which disappeared from MtGox in 2014.
The major Tokyo-based bitcoin exchange collapsed after admitting that 850,000 coins -- worth around $480 million at the time -- had disappeared from its vaults.
The high-profile demise of MtGox failed to douse the enthusiasm for virtual currencies in Japan, which in April became the first country in the world to proclaim it as legal tender.
Nearly one third of global bitcoin transactions in December were denominated in yen, according to specialist website jpbitcoin.com.
As many as 10,000 businesses in Japan are thought to accept bitcoin and bitFlyer, the country's main bitcoin exchange, saw its user base pass the one-million mark in November.
Many Japanese, especially younger investors, have been seduced by the idea of strong profits as the economy has seen years of ultra-low interest rates offering little in the way of traditional returns.
Major Japanese newspapers on Sunday labelled the management of virtual currencies at Coincheck as "sloppy" and said the company had "expanded business by putting safety second".
Local media added the Financial Services Agency was expected to take disciplinary measures against Coincheck, which proclaims itself "the leading bitcoin and cryptocurrency exchange in Asia", following the theft.
Iran-linked APT OilRig target IIS Web Servers with new RGDoor Backdoor
28.1.2018 securityweek APT
The Iran-linked cyber-espionage group tracked as OilRig started using a backdoor subbed RGDoor to target Internet Information Services (IIS) Web servers.
The OilRig hacker group is an Iran-linked APT that has been around since at least 2015, when targeted mainly organizations in the financial and government sectors, in the United States and Middle Eastern countries.
The hackers used the RGDoor backdoor to target Middle Eastern government organizations and financial and educational institutions.
According to the researchers, RGDoor is a secondary backdoor that allows the hackers to regain access to a compromised Web server when primary TwoFace webshell is discovered and removed.
OilRig hackers are using the TwoFace webshell since at least June 2016, the backdoor
“Unlike TwoFace, the actors did not develop RGDoor in C# to be interacted with at specific URLs hosted by the targeted IIS web server. Instead, the developer created RGDoor using C++, which results in a compiled dynamic link library (DLL).” states the analysis from PaloAlto Networks.
“The DLL has an exported function named “RegisterModule”, which is important as it led us to believe that this DLL was used as a custom native-code HTTP module that the threat actor would load into IIS.”
The attackers exploited the IIS 7 functionality that allows developers to create modules in C++ to extend IIS’ capabilities, in this way they could carry out custom actions on requests
The “native-code modules can be installed either in the IIS Manager GUI or via the command-line using the ‘appcmd’ application,” Palo Alto has explains.

Malware researchers from Paloalto Networks discovered that the code calls the RegisterModule function with arguments that ignore inbound HTTP GET requests, but act on all HTTP POST requests.
When the IIS server receives an inbound HTTP POST request, the backdoor parses the requests searching for the string in HTTP “Cookie” field.
The find was used to issue cmd$ [command to execute], upload$ [path to file], or download$ [path to file] commands.
“RGDoor then constructs its own HTTP response by first setting the “Content-Type” field within the HTTP header to “text/plain”.” continues the analysis.
The choice of the Cookie fields makes it hard to analyze inbound requests related to RGDoor backdoor because IIS does not log the values within these specific fields of inbound HTTP requests by default.
“This backdoor has a rather limited set of commands, however, the three commands provide plenty of functionality for a competent backdoor, as they allow an actor to upload and download files to the sever, as well as run commands via command prompt. The use of RGDoor suggests that this group has contingency plans to regain access to a compromised network in the event their webshells are discovered and remediated.” concluded Palo Alto Networks.
Technical details, including IoCs are reported in the analysis published by PaloAlto Networks.
Download URLs for two packages of the phpBB forum software were compromised
28.1.2018 securityaffairs Vulnerebility
Hacker compromised the download URLs of the popular phpBB forum software, for around three hours they were delivering infected versions of legitimate files.
The popular phpBB free and open source forum software has been compromised by an unknown hacker. According to a security advisory released by the phpBB maintainers, the attacker has compromised download URLs for two phpBB packages.
phpBB
@phpbb
[Security] phpBB 3.2.2 Packages Compromised http://dlvr.it/QCxM6v
4:15 AM - Jan 27, 2018
1 1 Reply 8 8 Retweets 3 3 likes
Twitter Ads info and privacy
The downloads URLs compromised were related to the phpBB 3.2.2 full package and the phpBB 3.2.1 -> 3.2.2 automatic updater.
“Earlier today, we identified that the download URLs for two phpBB packages available on phpBB.com were redirecting to a server that did not belong to us. We immediately took down the links and launched an investigation.” reads the announcement published by the development team.
“The point of entry was a third-party site. Neither phpBB.com nor the phpBB software were exploited in this attack.
If you downloaded either the 3.2.2 full package or the 3.2.1 -> 3.2.2 automatic updater package between the hours of 12:02 PM UTC and 15:03 PM UTC on January 26th, you received an archive modified with a malicious payload. “
The compromised download links were online for around three hours, between 12:02 PM UTC and 15:03 PM UTC on January 26, those who used them received a malware.
Users who downloaded phpBB 3.2.2 packages on January 26 must verify the SHA256 file hash of the file they downloaded with the one reported on the phpBB official downloads page.

The phpBB development team is investigating the incident, it only revealed that the entry point is likely a third-party site and clarified that neither phpBB.com nor the phpBB software were exploited in this attack.
At the time of writing it is still unclear how hackers compromised the download URLs.
The phpBB maintainers quickly removed the links to the malicious payload.
Developers that have already used the package to install or update a phpBB forum, are advised to file an incident report on the forum tracker to receive assistance with removal of the malicious code.
Attackers behind Cloudflare_solutions Keylogger are back, 2000 WordPress sites already infected
28.1.2018 securityaffairs Virus
More than 2,000 WordPress sites have been infected with a malicious script that can deliver both a keylogger and the cryptocurrency miner CoinHive.
More than 2,000 sites running the WordPress CMS have been infected with a malicious script that can deliver both a keylogger and the in-browser cryptocurrency miner CoinHive.
This new hacking campaign was spotted by experts from the security firm Sucuri, the experts believe the attackers are the same that launched a campaign that infected 5,500 WordPress sites in December.
In both campaigns, the threat actors used a keylogger dubbed cloudflare[.]solutions, but be careful, there is no link to security firm Cloudflare.
After the discovery in December of campaign, the cloudflare[.]solutions domain was taken down, but this new discovery confirms that threat actors are still active and are using a new set of recently registers domains to host the malicious scripts that are injected into WordPress sites.
By querying the search engine PublicWWW, researchers discovered that the number of infected sites includes 129 from the domain cdns[.]ws and 103 websites for cdjs[.]online.
“A few days after our keylogger post was released on Dec 8th, 2017, the Cloudflare[.]solutions domain was taken down. This was not the end of the malware campaign, however; attackers immediately registered a number of new domains including cdjs[.]online on Dec 8th, cdns[.]ws on Dec 9th, and msdns[.]online on Dec 16th.” reads the analysis published by Sucuri.
“PublicWWW has already identified relatively few infected sites: 129 websites for cdns[.]ws and 103 websites for cdjs[.]online, but it’s likely that the majority of the websites have not been indexed yet. Since mid-December, msdns[.]online has infected over a thousand websites, though the majority are reinfections from sites that have already been compromised.”
Most of the infected domains are tied to msdns[.]online, with over a thousand reported infections. In many cases, threat actors re-infected WordPress sites compromised in the previous campaign.

The attackers target outdated and poorly configured WordPress sites, they inject the cdjs[.]online script either a WordPress database (wp_posts table) or into the theme’s functions.php file.
The Keylogger script is able to capture data entered on every website form, including the admin login form, information is sent back to the attackers via the WebSocket protocol.
Just like previous versions of the campaign leveraging a Fake GoogleAnalytics Script, researchers identified a fake googleanalytics.js that loads an obfuscated script used to load the malicious scripts “startGoogleAnalytics” from the attackers’ domains.
Experts discovered many similarities also in the cryptominer component of this campaign.
“We’ve identified that the library jquery-3.2.1.min.js is similar to the encrypted CoinHive cryptomining library from the previous version, loaded from hxxp:// 3117488091/lib/jquery-3.2.1.min.js?v=3.2.11 (or hxxp://185 .209 .23 .219/lib/jquery-3.2.1.min.js?v=3.2.11, a more familiar representation of the IP address). This is not surprising since cdjs[.]online also exists on the server 185 .209 .23 .219.” continues the analysis.
“It’s interesting to note that this script extends the CoinHive library and adds an alternative configuration using the 185 .209 .23 .219 server (and now specifically cdjs[.]online) for LIB_URL and WEBSOCKET_SHARDS.”
According to Sucuri experts, the threat actors behind this hacking campaign are active at least since April 2017. Sucuri has tracked at least other three different malicious scripts hosted on the same cloudflare.solutions domain across the months.
The first attack leveraging on these scripts was observed in April when hackers used a malicious JavaScript file to embed banner ads on hacked sites.
In November, experts from Sucuri reported the same attackers were loading malicious scripts disguised as fake jQuery and Google Analytics JavaScript files that were actually a copy of the Coinhive in-browser cryptocurrency miner. By November 22, the experts observed 1,833 sites compromised by the attackers.
Experts noticed that this campaign is still not massive as the one spotted in December, anyway it could not be underestimated.
“While these new attacks do not yet appear to be as massive as the original cloudflare[.]solutions campaign, the reinfection rate shows that there are still many sites that have failed to properly protect themselves after the original infection,” concluded Sucuri.
Intel Working on CPUs With Meltdown, Spectre Protections
27.1.2018 securityweek Safety
Intel is working on CPUs that will include built-in protections against the notorious Meltdown and Spectre attacks, CEO Brian Krzanich revealed on Thursday during a conference call discussing the company’s latest earnings report.
Intel has released some microcode updates to address the vulnerabilities, but the patches have caused serious problems for many users, which has led to Intel and other vendors halting updates.
“Our near term focus is on delivering high quality mitigations to protect our customers’ infrastructure from these exploits. We're working to incorporate silicon-based changes to future products that will directly address the Spectre and Meltdown threats in hardware. And those products will begin appearing later this year,” Krzanich said.Intel to release CPUs with Meltdown and Spectre protections
“However, these circumstances are highly dynamic and we updated our risk factors to reflect both the evolving nature of these specific threats and litigation, as well as the security challenge, more broadly,” he added.
The latest financial report shows that the company had a great 2017, with a record fourth-quarter revenue of $17.1 billion and a record full-year revenue of $62.8 billion. Despite its reputation taking a hit due to the Meltdown and Spectre vulnerabilities, the company expects 2018 to also be a record year.
It’s worth noting, however, that one of the factors that could cause results to differ from the company’s expectations are vulnerabilities in Intel processors and other products. In addition to the security flaws themselves, Intel is concerned about the adverse performance and system instability introduced by mitigations, associated lawsuits, the negative publicity they generate, and the impact they may have on customer relationships and reputation, the company said.
Several class action lawsuits have already been filed against Intel, accusing the company of violating state consumer laws by misleading customers about its product and breaching warranties.
Krzanich sold all the stock he was legally allowed to, worth roughly $24 million, just weeks before the existence of Spectre and Meltdown came to light, which has raised insider trading concerns.
Intel has denied the allegations, but French publication LeMagIT reported this week that Intel started informing its partners of the flaws on the same day the company’s CEO sold his shares, specifically November 29.
Iranian Hackers Target IIS Web Servers With New Backdoor
27.1.2018 securityweek CyberSpy
The Iran-linked cyber-espionage group known as OilRig is using a backdoor to target Internet Information Services (IIS) Web servers used by Middle Eastern government organizations and financial and educational institutions.
Dubbed RGDoor, the malware is believed to be a secondary backdoor that allows the actor to regain access to a compromised Web server in the event the primary malware is detected and removed. This primary malicious tool is the TwoFace webshell, which OilRig is believed to have been using since at least June 2016.
Around since 2015, the OilRig threat group has targeted mainly organizations in the financial and government sectors, in the United States and Middle Eastern countries. Believed to be operating out of Iran, the group is using multiple tools, is expanding its arsenal, and is quick to adopt new exploits.
The backdoor was created using C++, which results in a compiled dynamic link library (DLL) with an exported function named “RegisterModule.” Because of that, Palo Alto's researchers believe the DLL was used as a custom native-code HTTP module loaded into IIS, and suggest that there is no visual representation of the shell for the actors to interact with.
This approach takes advantage of IIS 7 functionality that allows developers to create modules in C++ to extend IIS’ capabilities, such as carry out custom actions on requests. These “native-code modules can be installed either in the IIS Manager GUI or via the command-line using the ‘appcmd’ application,” Palo Alto has explains.
The researchers also found that RGDoor would call the “RegisterModule” function with arguments that ignore inbound HTTP GET requests, but act on all HTTP POST requests, even those issued over HTTPS. The malware parses these requests to look for a specific string in the HTTP “Cookie” field, so as to find whether cmd$ [command to execute], upload$ [path to file], or download$ [path to file] commands were issued to it.
“The sample then transmits the data back to the actor by creating a loop that calls the IHttpResponse::WriteEntityChunk method until all of the data is sent to the actor within HTTP responses. If the WriteEntityChunk method fails at any point during this loop, the code will respond to the actor with a HTTP 500 “Server Error” response by using the IHttpResponse::SetStatus method,” the researchers explain.
Because IIS does not log the values within Cookie fields of inbound HTTP requests by default, it’s difficult to locate and analyze inbound requests related to RGDoor. Furthermore, because the module checks all inbound POST requests for commands, the actor can use any URL to interact with it.
The actors behind the backdoor used the TwoFace webshell to load it onto an IIS Web server and gain backdoor access to the compromised system. The main purpose of the tool, however, appears to be regaining access to the server in the event the TwoFace webshell was removed.
“This backdoor has a rather limited set of commands, however, the three commands provide plenty of functionality for a competent backdoor, as they allow an actor to upload and download files to the sever, as well as run commands via command prompt. The use of RGDoor suggests that this group has contingency plans to regain access to a compromised network in the event their webshells are discovered and remediated,” Palo Alto concludes.
Six Months in Jail for University Email Hacker
27.1.2018 securityweek Crime
A man who accessed over 1,000 email accounts maintained by a New York City-area university to download inappropriate photos and videos was sentenced to 6 months in prison this week.
The man, Jonathan Powell, 30, of Phoenix, Arizona, pled guilty to the charges on August 9, 2017, in Manhattan federal court before United States District Judge Alison J. Nathan, who also imposed the sentence.
According to the allegation he pled guilty to, Powell gained unauthorized access to the email accounts by accessing the password reset utility maintained by the email servers of a United States University that has its primary campus in New York, New York. The tool was meant for authorized users to reset their forgotten passwords.
Powell abused the utility between October 2015 and September 2016 to change the email account passwords of students and others affiliated with the University and to gain access to more than 1,000 accounts.
Once inside the email accounts, he obtained unauthorized access to other password-protected email, social media, and online accounts to which the users of the compromised accounts were registered. These include Apple iCloud, Facebook, Google, LinkedIn, and Yahoo! accounts.
Powell requested password resets for the linked accounts and changed those passwords as well, after a password reset email was sent to the compromised email accounts. Then, he logged into the linked accounts and started looking for private and confidential content.
The investigation into Powell’s nefarious activities revealed that he accessed all of the compromised accounts to download sexually explicit photographs and videos of college-aged women.
Between October 2015 and September 2016, Powell accessed the password reset utility approximately 18,640 different times and attempted around 18,600 password changes for an estimated number of 2,054 unique University email accounts. He succeeded in changing approximately 1,378 passwords for 1,035 email accounts, as he compromised some of the accounts multiple times.
Powell was also found to have compromised 15 email accounts hosted by a University in Pennsylvania. He also admitted to compromising email accounts at several other educational institutions in Arizona, Florida, Ohio, and Texas.
Power was also sentenced to two years of supervised release and ordered to pay $278,855 in restitution.
“Jonathan Powell used his computer skills to breach the security of a university to gain access to the students’ personal accounts. Once Powell had access, he searched the accounts for compromising photos and videos. No college student should have to fear that personal, private information could be mined by strangers for potentially compromising material,” Geoffrey S. Berman, the United States Attorney for the Southern District of New York, commented.
Data Privacy Concerns Cause Sales Delays: Cisco
27.1.2018 securityweek Privacy
Nearly two-thirds of businesses worldwide have experienced significant delays in sales due to customer data privacy concerns, according to Cisco’s 2018 Privacy Maturity Benchmark Study.
The study, based on the responses of roughly 3,000 cybersecurity professionals from 25 countries, shows that 65% of businesses reported sales cycle delays due to concerns over data privacy, with an average delay of nearly 8 weeks.
However, organizations with a mature privacy process are less affected compared to privacy-immature companies. Privacy-mature firms experienced delays of only 3.4 weeks, while immature businesses reported delays averaging nearly 17 weeks.
Sales delays have also varied depending on several other factors, including country, with the longest delays reported in Mexico and Latin America, and industry, with the longest delays in the government and healthcare sectors.
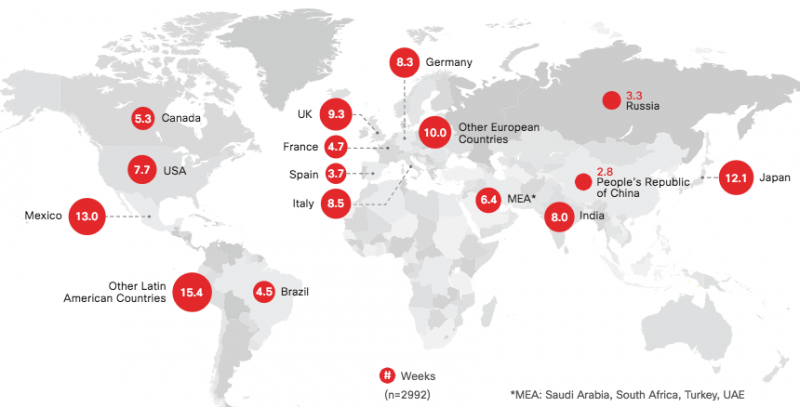
The report also shows that privacy-mature organizations suffer lower losses as a result of data breaches. According to Cisco, only 39% of privacy-mature organizations experienced losses exceeding $500,000, compared to 74% of companies that have an immature privacy process.
The type of model adopted by organizations for privacy resources also appears to be an important factor. According to the study, businesses with fully centralized and decentralized resources had sales delays of 10 and 7 weeks, respectively. On the other hand, organizations with a hybrid model, which represents a mix between centralized and decentralized, reported delays of less than 5 weeks.
“This study provides valuable empirical evidence of the linkage between firm privacy policies and performance-relevant impacts. These results are indicative of the direction that future empirical research on privacy, and cybersecurity more generally, should take to better validate and focus our understanding of best practices in these important areas,” said Dr. William Lehr, economist at MIT.
The complete 2018 Privacy Maturity Benchmark Study is available for download in PDF format.
Cryptocurrencies Fall After Hack Hits Japan's Coincheck
27.1.2018 securityweek Hacking
Cryptocurrencies fell Friday after Japan-based digital exchange Coincheck suspended client deposits and withdrawals for virtual currencies except bitcoin, saying it had been hacked.
Coincheck said it was investigating "unauthorised access" of the exchange that appeared to result in a loss worth half a billion US dollars of NEM, the 10th biggest cryptocurrency by market capitalisation.
"At 3 am (1800 GMT) today, 523 million NEMs were sent from the NEM address of Coincheck. It's worth 58 billion yen based on the calculation at the the rate when detected," said Coincheck's chief operating officer Yusuke Otsuka late Friday.
"We're still examining how many of our customers are affected," he said, adding that the exchange was trying to find out whether the breach was from Japan or another country.
After the exchange suspended deposits and withdrawals, NEM plunged more than 16 percent in a 24-hour period, according to CoinMarketCap.com.
Major virtual currencies had rebounded slightly by late Friday but were still down, with Bitcoin dropping 2.13 percent to $10,987.70, ripple sliding more than six percent and ethereum flat.
Coincheck said it had discovered the breach at 11.25 am and announced it had suspended trading for all cryptocurrencies apart from bitcoin in a series of tweets.
According to its website, which proclaims it is "the leading bitcoin and cryptocurrency exchange in Asia", Tokyo-based Coincheck was founded in 2012 and had 71 employees as of July last year.
In 2014 major Tokyo-based bitcoin exchange MtGox collapsed after admitting that 850,000 coins -- worth around $480 million at the time -- had disappeared from its vaults.
Bitcoin is recognized as legal tender in Japan and nearly one third of global bitcoin transactions in December were denominated in yen, according to specialist website jpbitcoin.com.
The virtual currency is well down from record highs approaching $20,000 in late December, having rocketed 25-fold last year, before being hit by concerns about a bubble and worries about crackdowns on trading it.
Billionaire investor George Soros, known for his legendarily successful currency trading, has dismissed bitcoin as a "typical bubble".
But speaking Thursday at the Davos summit, he said the cryptocurrency would likely avoid a full crash because authoritarians would still use it to make secret investments abroad.
PCI Council Introduces New Standard for Mobile Card Payments
27.1.2018 securityweek Mobil
Responding to the market's growing interest in, and use of, mobile payments, the PCI Security Standards Council (PCI SSC) has announced a new standard for software-based PIN entry on commercial off-the-shelf devices (COTS); such as smartphones and tablets.
"Mobile point-of-sale (MPOS) solutions have become very popular with smaller merchants for their flexibility and efficiency," explained said Aite Group senior analyst Ron van Wezel. "MPOS has enabled them to take orders and accept payments on a tablet or smartphone, anytime and anywhere."
The problem is the cost of hardware-based chip-and-pin can be prohibitive for small merchants in mobile situations.
"With the new PIN entry standard," van Wezel continued, "the PCI Council has responded to market need by specifying the security requirements for allowing PIN entry directly on the mobile touchscreen. This means that merchants can accept payments with just their mobile device and a small, cost efficient card reader connected to it along with a secure PIN entry application."
The new standard has been in the pipeline since last summer. In a July 2017 blog post, PCI SSC CTO Troy Leach announced, "We are starting work on a new standard that specifically focuses on software-based PIN-entry on commercial off-the-shelf (COTS) devices, such as consumer-grade mobile phones or tablets."
This is the standard (PDF) now announced. A separate document, Software-Based PIN Entry on COTS Test Requirements, will be published in the next month.
"With advancements in monitoring capabilities and the ability to isolate account data, we are introducing a security approach that leverages software-based security for accepting a PIN within the boundaries of a COTS device," said Leach in a new blog post on Wednesday -- adding that it was an alternative to, and not a replacement for, the existing PCI PIN Transaction Security Point of Interaction (PTS POI) standard.
There are five core principles to the new standard: isolation of PIN from other account data; ensuring the security of the PIN entry application on the COTS device; active security monitoring of the device; a secure card reader device to encrypt account data; and the restriction of transactions to EMV contact and contactless cards.
Initial reaction from the security industry has been mixed; that is, it is a good basic idea, but with reservations.
"While the new PCI PIN requirements are a good idea," Joseph Carson, chief security scientist at Thycotic told SecurityWeek, "this introduces increased risks as end to end security for PIN cannot be guaranteed. For example, credit card theft in Europe has been less impacted than credit card theft in the USA due to the PIN requirement -- meaning that credit card fraud in Europe has been limited due to the PIN. The new requirements mean the risk of the PIN getting exposed is increased and the risk on cyberattacks against the merchants will also increase. The PIN has been protected up until now; however, this new standard is actually lowering that protection."
Chris Morales, head of security analytics at Vectra Networks, has a different concern. "I have questions around how the PCI council intends for vendors to implement the required continuous monitoring for security threats," he said. "Continuous monitoring could be a costly and time-consuming exercise only large vendors or the payment system supplier would be able to afford to implement correctly. I believe these will need to be vetted out with further review by the security community."
Chris Roberts, chief security architect at Acalvio is also concerned about the monitoring aspect. "Monitoring and actually 'doing' anything about it are two different things. We've run afoul of that so many times in the past where companies are monitoring but are asleep at the wheel. It might be time for PCI to look at technologies that go beyond simply reacting.
"It's good they have realized that payments are going mobile," he added, "but it does feel as if they are in reactive mode as opposed to proactively looking at the marketplace and working with the vendors ahead of time to help shape the future as opposed to being part of the problem in 'gatekeeping'."
PCI SSC believes it has got the security right by isolating the PIN within the COTS device from the account identifying information. "This isolation happens as the Primary Account Number (PAN) is never entered on the COTS device with the PIN," said Leach. "Instead that information is captured by an EMV Chip reader that is approved as an SCRP that encrypts the contact or contactless transaction."
And it should be said that he has support. Sanjay Kalra, co-founder and chief product officer at Lacework, comments, "Businesses required to comply to PCI cover many industries -- retail, hospitality, entertainment, healthcare, electronics and more -- and are all rapidly being disrupted by mobile and cloud computing. They need to upgrade their payment processes to reflect the technology disruptions. This update to the PCI standard is welcome and will help organizations safely take advantage of new mobile technologies. Nobody should be surprised if similar changes come to regulations for the cloud."
Cybercriminals are offering for sale infant fullz on the dark web
27.1.2018 securityaffairs CyberCrime
Cybercriminals are offering for sale infant fullz on the dark web, this is the first time that unscrupulous sellers offer this kind of merchandise on a black marketplace.
Crooks are offering for sale Social Security numbers of babies on the dark web, the news was reported by the CNN.
The news is disconcerting, this is the first time that unscrupulous sellers offer this kind of merchandise on a black marketplace.
The offer appeared on the Dream Market marketplace, one of the biggest Tor marketplace that has been around since around Nov/Dec 2013.
The seller is offering Social Security numbers of babies along with their dates of birth and mother’s maiden names, the ‘Infant fullz’ goes for $300 worth of bitcoin.
The slang term “Fullz” refers full packages of individuals’ identifying information. A “Fullz” package contains an individual’s name, Social Security number, birth date, account numbers and other data.
“Infant fullz get em befor tax seson [sic],” reads the ad.
‘Infant Fullz’ are a precious commodity in the criminal underground they allow crooks to access a clean credit history, they also allow crooks to apply for government benefits or take out mortgages.
The use of children PII is considered secure by cyber criminals because this specific type of identity theft could remain undiscovered for years.
“The listing for infant data was discovered by researchers at Terbium Labs, a dark web intelligence firm. The cost and age of the alleged victims came as a surprise to Emily Wilson, the company’s director of analysis.” states the CNN.
“Although the firm has seen child data for sale before, this was the first time it has seen infants’ data for sale.”
“It’s unusual to have information specifically marked as belonging to children or to infants on these markets,” Wilson said.

Identity theft crimes involving children is not a novelty, according to a 2011 report published by Carnegie Mellon University’s CyLab, the rate of this specific type of crimes for children as being 51 times greater than that of adults.
Researchers highlighted that “parents typically don’t monitor their children’s identities”.
Cryptocurrencies Black Friday – Japan-based digital exchange Coincheck hacked
27.1.2018 securityaffairs Hacking
It is a black Friday for cryptocurrencies, after the news of the hack of the Japan-based digital exchange Coincheck the value of major cryptocurrencies dropped.
It is a black Friday for cryptocurrencies, the news of the hack of the Japan-based digital exchange Coincheck had a significant impact on their value.
Coincheck was founded in 2012, it is one of the most important cryptocurrency exchange in Asia.
The Coincheck suspended the operations of deposits and withdrawals for all the virtual currencies except bitcoin, the exchange announced it was investigating an “unauthorised access” to the exchange.
According to the company, the hackers stole worth half a billion US dollars of NEM, the 10th biggest cryptocurrency by market capitalization.
The news of the incident has a significant impact on the NEM value that dropped more than 16 percent in 24 hours.
“At 3 am (1800 GMT) today, 523 million NEMs were sent from the NEM address of Coincheck. It’s worth 58 billion yen based on the calculation at the rate when detected,” said Coincheck COO Yusuke Otsuka.
“We’re still examining how many of our customers are affected,”

NEM Charts – CoinMarketCap.com
The experts at the exchange are investigating the security breach to find out whether it was from Japan or another country.
Coincheck discovered the incident at 11.25 am and notified the suspension of trading for all cryptocurrencies apart from bitcoin via Twitter.
Coincheck
@coincheck_en
We are currently halting deposits, withdrawals, buying and selling of NEM. Please accept our sincere apologies for this inconvenience and rest assured that we are working to resolve this issue as quickly as possible.https://coincheck.com/en/blog/4673
5:04 AM - Jan 26, 2018
*Urgent update regarding deposits of NEM* | Coincheck Cryptocurrency Exchange
View the latest news today for bitcoin market in Japan, cryptocurrency, new features, and campaign at Coincheck Blog.
coincheck.com
Twitter Ads info and privacy
In February 2014, Mt. Gox suspended trading and filed for bankruptcy protection from creditors.
At the time, the company was handling over 70% of all bitcoin transactions worldwide, it announced that approximately 850,000 bitcoins ($450 million at the time) belonging to customers and the company were stolen.
Hurry up, update your Lenovo Fingerprint Manager Pro if you use Windows 7, 8 and 8.1
27.1.2018 securityaffairs Vulnerebility
Lenovo has fixed a hardcoded password vulnerability in Lenovo Fingerprint Manager Pro affecting a dozen laptop models running Windows 7, 8 and the 8.1 OS.
The PC vendor Lenovo has fixed a hardcoded password vulnerability, tracked as (CVE-2017-3762), affecting a dozen Lenovo laptop models that run versions of Microsoft Windows 7, 8 and the 8.1 operating system.
Lenovo laptops running Windows 10 are not impacted by the vulnerability because that OS version natively supports fingerprint reader technology.
The list of impacted family models includes ThinkPad, ThinkCentre, and ThinkStation laptops.
“A vulnerability has been identified in Lenovo Fingerprint Manager Pro. Sensitive data stored by Lenovo Fingerprint Manager Pro, including users’ Windows logon credentials and fingerprint data, is encrypted using a weak algorithm, contains a hard-coded password, and is accessible to all users with local non-administrative access to the system it is installed in.” states the security advisory published by Lenovo.

The Lenovo Fingerprint Manager Pro is a utility that allows users to log into their laptop and configured websites by using the fingerprint.
The flaw resides in the Lenovo Fingerprint Manager Pro that encrypts sensitive data such as fingerprint data and login credentials using a weak algorithm.
Customers urge to update Fingerprint Manager Pro to version 8.01.87 or later.
The complete list of laptops that need to update their Lenovo Fingerprint Manager Pro version is:
ThinkPad L560
ThinkPad P40 Yoga, P50s
ThinkPad T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560
ThinkPad W540, W541, W550s
ThinkPad X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT)
ThinkPad X240, X240s, X250, X260
ThinkPad Yoga 14 (20FY), Yoga 460
ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, M93z
ThinkStation E32, P300, P500, P700, P900
The flaw was disclosed by Lenovo this week, the company credited Jackson Thuraisamy, a senior security consultant with Security Compass, for the discovery.
Trend Micro spotted a malvertising campaign abusing Google’s DoubleClick to deliver Coinhive Miner
27.1.2018 securityaffairs Virus
Trend Micro uncovered a spike in the number of Coinhie miners over the past few days, including Coinhive, apparently linked to Google’s DoubleClick ads that are proposed on YouTube and other sites.
The number of cyber-attacks against cryptocurrencies is increased due to a rapid increase in the value of currencies such as Bitcoin and Ethereum.
Hackers targeted almost any actor involved in the business of cryptocurrencies, single users, miners and of course exchanges.
Security firms have detected several malware applications specifically designed to steal cryptocurrencies, and many websites were compromised to install script used to mine virtual coins abusing computational resources of unaware visitors.
Researchers at Trend Micro uncovered a spike in the number of Coinhie miners over the past few days apparently linked to Google’s DoubleClick ads that are proposed on YouTube and other sites.
“On January 24, 2018, we observed that the number of Coinhive web miner detections tripled due to a malvertising campaign. We discovered that advertisements found on high-traffic sites not only used Coinhive (detected by Trend Micro as JS_COINHIVE.GN), but also a separate web miner that connects to a private pool.” states the analysis published by Trend Micro.
“We detected an almost 285% increase in the number of Coinhive miners on January 24. We started seeing an increase in traffic to five malicious domains on January 18. After closely examining the network traffic, we discovered that the traffic came from DoubleClick advertisements.“

The researchers observed two separate web cryptocurrency miner scripts, both hosted on AWS, that were called from a web page that presents the DoubleClick ad.
The advertisement uses a JavaScript code that generates a random number between 1 and 101. If the number generated is greater than 10, the advertisement will call the coinhive.min.js script to mine 80% of the CPU power. For the remaining 10%, the advertisement launch a private web miner, the mqoj_1.js script.
“The two web miners were configured with throttle 0.2, which means the miners will use 80% of the CPU’s resources for mining.” continues the analysis.

Google promptly took action against the ads that abuse users’ resources violating its policies.
Blocking JavaScript-based applications from running on browsers can prevent the execution of Coinhive miners, the experts suggest to regularly patch and update web browsers to reduce the risks.
Dutch Spies Watched as Russians Hacked US Democrats: Report
26.1.2018 securityweek BigBrothers
Dutch intelligence services hacked Russian cyber attackers and alerted US counterparts after watching them transfer "thousands" of Democratic Party emails ahead of the 2016 US election, Dutch media reported Friday.
The Dutch national intelligence service (AIVD) had been watching the notorious group known as Cozy Bear since 2014, according to the respected Volkskrant daily, and a Dutch TV news programme Nieuwsuur.
But as well as stumbling upon the group's computer network which was run out of a university building near Moscow's Red Square, the Dutch agents also gained access to the security cameras surveilling the room.
"Not only can the intelligence service now see what the Russians are doing, they can also see who's doing it," the Volkskrant said, citing anonymous US and Dutch sources.
The AIVD alerted its US counterparts when in 2015 it became a "witness to the Russian hackers harassing and penetrating the leaders of the Democratic Party, transferring thousands of emails and documents," it said.
"Yet, it will be months before the United States realise what this warning means: that with these hacks the Russians have interfered with the American elections. And the AIVD hackers have seen it happening before their very eyes."
Cozy Bear has been widely blamed for meddling in the 2016 US elections won by now President Donald Trump.
Although Trump has vehemently denied working with the Russians, his White House is under investigation by special prosecutor and former FBI director Robert Mueller.
Mueller's team is seeking to uncover whether the Trump campaign colluded with Russia's efforts to sway the election, including leaks of hacked Democratic Party files.
Mueller's team has spent the past eight months interviewing members of Trump's campaign and White House staff, and has issued four indictments, with two guilty pleas.
A spokeswoman for the AIVD refused to confirm the Dutch media reports, telling AFP "we never comment on operations."
But American intelligence agencies have said "with high confidence" they believe the Kremlin was behind the attack on the Democratic Party.
That confidence is based on "AIVD hackers having had access to the office-like space in the centre of Moscow for years," the Volkskrant said, citing sources who added that the Dutch had provided "technical evidence" of the attack on the Democratic Party.