
Microsoft vydal nový update Windows, řeší restarty kvůli chybám čipů Intelu
31.1.2018 SecurityWorld Zranitelnosti
Intel nedávno varoval uživatele, aby si nestahovali firmwarové aktualizace, vydané za účelem řešení zranitelností Spectre a Meltdown, protože způsobovaly náhodné restartování systému. Microsoft na to o víkendu reagoval vydáním aktualizace KB4078130.
Bezpečnostní aktualizace deaktivovala předchozí nestabilní záplatu. Nová aktualizace je reakcí Microsoftu na týden staré oznámení, které zákazníky firmy – podniky, výrobce i koncové uživatele – varovalo před nestabilní záplatou.
Podle Intelu může nový firmware „může způsobit neočekávaně vysoký počet restartů a dalších nepředvídatelných systémových reakcí na procesorech Broadwell a Haswell.“ Tyto stále ještě rozšířené čipy pochází z let 2015 a 2013.
Microsoft na nepříjemné zprávy reagoval odstraněním mitigací pro jednu ze tří zranitelných oblastí, které Meltdown a Spectre zasahují.
„Naše vlastní zkušenost je, že nestabilita systému může v určitých případech způsobit ztrátu dat,“ potvrzuje v podpůrném dokumentu k nové aktualizaci Microsoft. „Zatímco Intel testuje, aktualizuje a nasazuje nový mikrokód, my zpřístupňujeme aktualizace KB4078130, který specificky ruší mitigaci CVE-2017-5715 ‚Branch target injection vulnerability‘. V našem testování se ukázalo, že tato aktualizace popsané chování blokuje.“
Aktualizace je dostupná pro všechny dosud podporované verze Windows, tedy 7, 8.1, 10 a související Windows Server edice. Spolu s tím Microsoft zveřejnil klíče, které IT administrátorům umožňují v registrech libovolně aktivovat či deaktivovat vybrané mitigace Spectre a Meltdown zranitelností.
Společnost Microsoft dále doporučuje uživatelům, aby poté, co Intel oznámí vyřešení problémů, uživatelé zablokované mitigace znovu povolili.
Tenable, Cylance Disclose Revenue Metrics
30.1.2018 securityweek IT
Cybersecurity solutions providers Tenable and Cylance this week shared financial metrics for 2017, with both privately-held companies showing strong revenue growth.
Cylance reported revenue of more than $100 million last year, which the company says represents a year-over-year growth of 177 percent.
The company’s AI-powered endpoint protection and threat detection solutions are used by over 3,800 enterprises, including 87 percent of Fortune 500 firms. Cylance’s customers include The Gap, Dell, Panasonic, Noble Energy, the National Hockey League Players Association, United Service Organizations (USO), and Partners In Health.
Cylance has raised more than $170 million in funding, including $20 million in February 2014, $42 million in June 2015, and $100 million in June 2016.
When announcing its financial results, Cylance highlighted that its growth rate and the time it took the company to reach $100 million in annual revenue surpassed other cybersecurity firms, including Palo Alto Networks, FireEye, Symantec and CyberArk.
Tenable announced record billings of more than $250 million in 2017, which it says represents a 45 percent growth. The company has attributed this success to strong performance in North America, Europe and Asia. The fourth quarter of 2017 was the seventh consecutive quarter of greater than 40 percent year-over-year billings growth.
As for revenue, Tenable reported $189 million for the 12-month period that ended on December 31, 2017, which represents over 50 percent growth.
Tenable, makers of vulnerability scanners and software solutions that help find network security gaps, has more than 24,000 customers across 160 countries. The list includes more than 50 percent of Fortune 500 companies, over 20 percent of Global 2000 firms, and the ten largest tech companies in the U.S.
Tenable recently announced a partnership with Siemens that aims to provide asset discovery and vulnerability management solutions for industrial networks.
Tenable has raised more than $300 million, including $250 million in November 2015 and $50 million in September 2012.
RELX Group to Acquire Fraud Fighting Firm ThreatMetrix for $815 Million
30.1.2018 securityweek IT
RELX Group, a provider of b2b Information and analytics services, announced on Monday that it has agreed to acquire fraud detection firm ThreatMetrix for £580 million (approximately $815 million) in cash.
Founded in 2005, San Jose, Calif.-based ThreatMetrix’s technology analyzes connections among devices, locations, identity information and threat intelligence, and combines the data with behavioral analytics to identify high-risk transactions in real time.
“ThreatMetrix has built the largest digital identity network that can determine when an individual’s credentials are being used by cybercriminals in real time, which enables businesses to better understand the global footprint of stolen identities,” Alisdair Faulkner, chief products officer at ThreatMetrix, said in 2015 when the company launched its ThreatMetrix Digital Identity Network.
The company says the network currently analyzes more than 100 million transactions per day across 35,000 websites from 5,000 customers.
According to a report published by ThreatMetrix in mid-2017, the United States was the world's primary target for cyber fraud attacks, and Europe has emerged as the major source of attacks, now accounting for 50% more attacks than the US. The report also found that growth in attacks was outpacing the growth of transactions; and that in a 90-day period, 130 million fraud attacks were detected.
Accoding to the company, ThreatMetrix will become part of Risk & Business Analytics, which under the LexisNexis Risk Solutions brand addresses fraud and authentication challenges by "applying advanced analytics to physical identity attributes, including identity credentials, addresses and asset ownership."
LexisNexis Risk Solutions has an existing partnership with ThreatMetrix, as ThreatMetrix’s device intelligence solutions are already integrated into its Risk Defense Platform.
“Further integration of ThreatMetrix’s capabilities in device, email and social intelligence will build a more complete picture of risk in today’s global, mobile digital economy, providing both physical and digital identity solutions,” the company said.
ThreatMetrix has raised more than $90 million in funding, including $20 million in Series E funding in March 2014, $30 million in growth funding from Silicon Valley Bank in October 2016, and $12.1 million in 2010.
The transaction is expected to close during the first half of 2018.
Cisco Patches Critical Code Execution Flaw in Security Appliances
30.1.2018 securityweek Vulnerebility
Cisco informed customers on Monday that updates released for its Adaptive Security Appliance (ASA) software patch a critical vulnerability that can be exploited to gain full control of devices or cause them to reload.
The security hole, tracked as CVE-2018-0101 and assigned a CVSS score of 10, allows a remote and unauthenticated attacker to execute arbitrary code or cause a denial-of-service (DoS) condition.
The flaw exists in the Secure Sockets Layer (SSL) VPN functionality of the ASA software. If this “webvpn” feature is enabled on a device, an attempt to double free a memory region occurs. A remote attacker can trigger the bug by sending specially crafted XML packets to a webvpn-configured interface.
Several security appliances using ASA software are affected, including 3000 Series Industrial Security Appliances (ISA), ASA 5500 security appliances and firewalls, ASA services modules for Catalyst 6500 series switches and 7600 series routers, ASA cloud firewalls, ASAv virtual appliances, and various Firepower devices.
Cisco has released fixes for each of the affected ASA releases, except for ones that are no longer supported.
Cisco is not aware of any malicious attacks exploiting this flaw, but its product security incident response team (PSIRT) “is aware of public knowledge of the vulnerability.”
Cedric Halbronn, the NCC Group researcher who reported the weakness to Cisco, will disclose its details on February 2 at the Recon Brussels 2018 conference.
Researchers at NCC Group have been investigating Cisco ASA devices and their firmware, and they have released a series of tools and blog posts dedicated to analyzing ASA firmware and finding vulnerabilities.
The experts started analyzing Cisco’s ASA software following the discovery of two critical vulnerabilities back in 2016, namely the IKEv1/IKEv2 buffer overflow tracked as CVE-2016-1287, and CVE-2016-6366, which Cisco identified following the release of an Equation Group exploit by the Shadow Brokers hacker group.
Security Explorations Launches New Research Program
30.1.2018 securityweek Safety
After 10 years of conducting complex research often without expecting any monetary rewards, Poland-based Security Explorations has now decided to launch a commercial offering that gives organizations the chance to gain exclusive or non-exclusive access to the company’s most interesting and unique projects.
Security Explorations is known for conducting in-depth research into digital satellite platforms, Nokia phones, and Java, including Java SE, Oracle Java Cloud Service and the Java VM in Oracle Database, Apple Quicktime for Java, and Google App Engine for Java. The firm’s findings - a total of more than 200 vulnerabilities - were reported to the respective vendors and in many cases made public.
Google did award the company $100,000 following the discovery of more than 30 vulnerabilities in the search giant’s App Engine product. However, Security Explorations said most of its research so far was done pro bono in an effort to raise awareness of flaws that put both users and vendors at risk.
In addition to its on-demand security analysis service, Security Explorations has now decided to launch a Security Research Program (SRP) that allows organizations to obtain access to the results of complex and unique research conducted by the company.Security Explorations launches Security Research Program
The first research offered through the SRP targets digital video broadcasting (DVB) devices from STMicroelectronics. The vendor’s products were analyzed several years ago as part of Security Explorations’ analysis of digital satellite TV platforms. Security Explorations believes STMicroelectronics, which exited the set-top box business two years ago, and other vendors have done little to address vulnerabilities, leaving devices at risk of attacks and failing to prevent premium TV piracy.
According to Security Explorations, its research into STMicroelectronics chipsets can be useful to other companies in this industry as it can help them identify the presence of vulnerabilities, develop patches, and conduct further security research.
Companies interested in Security Explorations research offered via the SRP can opt for an exclusive purchase (EP) and become the owner of the research material - the information will not be provided to anyone else from that point on - or they can choose the access only (AO) option and obtain a copy of the materials. Both options provide access to research reports, proof-of-concept (PoC) code, and tools, and Security Explorations is prepared to provide clarifications if needed, but the offer does not include ongoing support.
In the case of the STMicroelectronics research, pricing for the AO option is 50,000 EUR (roughly 62,000 USD). Information on pricing for exclusive purchases is only provided under a non-disclosure agreement (NDA).
“Each material released as part of our SRP program is separately priced,” Adam Gowdiak, CEO and founder of Security Explorations, told SecurityWeek. “The final price depends on the complexity of the research process and the amount of hours dedicated by Security Explorations to complete it. The impact of discovered vulnerabilities is also taken into account.”
“For our first material, the SRP AO price is less than the offers we have received for reverse engineering work of some PayTV solutions. The SRP EP price is set to be a fraction of the costs of replacing vulnerable ST chipsets / STB devices still deployed to the market,” Gowdiak added. “In general, SRP AO will be below the costs of conducting a given research (it should be always more attractive to purchase access to SRP material than to engage its own resources / achieve given research results on its own).”
Gowdiak says his company is currently working on two undisclosed projects, one of which will be released to the public for free, while the other one will be offered through the new program. He says the goal of the new offering is to help fund the firm’s non-commercial research.
Security Explorations will typically pick its research targets and once the analysis has been completed the company will announce it on its website and reach out to potentially interested parties. The vendor whose products have been analyzed can acquire exclusive rights to the materials to ensure that it cannot fall into the wrong hands, it can acquire access to the research, or ignore the report and instead work on improving the security of its products on its own.
“While the latter does not warrant that vulnerabilities or exploitation techniques targeted by SRP get found or remediated, the net effect should be always positive: a vendor putting additional resources into security, new weaknesses being discovered and fixed, flawed products being recalled/replaced from the market,” Security Explorations said.
Gowdiak has described the new offering as an alternative to bug bounty programs and security evaluations - with some significant differences.
“For Bug Bounties, a researcher decides about a target, a vendor decides about a reward (if any). For a consulting work, a customer decides about a target, a provider decides about a price for security evaluation services. For SRP, we decide both about a target and a price for our work,” Gowdiak explained.
The advantages of this approach for the company conducting the research include not being “the vendor’s hostage for consulting gigs and bug bounties,” which results in unbiased and independent research, and eliminating the issues that can arise during the disclosure process, Gowdiak said.
Security Explorations has reserved the right to deny access to any organization to its research, but the company has admitted that it has no way of enforcing its license terms and ensuring that its findings are not abused.
Tech Support Scammers Fined in US, Jailed in UK
30.1.2018 securityweek Spam
Ohio Attorney General Mike DeWine and the Federal Trade Commission (FTC) announced Monday that operators of a nationwide computer repair scam have been banned from the tech support business as part of settlements with the FTC and Ohio.
Commonly known as the 'tech support scam', repair fraud has become a global problem. A Microsoft survey with details published in October 2017 suggests that 2 out of 3 people have experienced a tech support scam in the last 12 months.
One in five U.S. respondents to this survey reported losing money to the scammers. "Since 2014," wrote Microsoft Assistant General Counsel Courtney Gregoire in an associated blog, "Microsoft has supported law enforcement agencies across the country who took legal action against known fraudsters responsible for approximately $165 million in consumer losses."
The scam attempts to engage victims in a telephone discussion about their computer, and to persuade them that it has problems that can be fixed for a price. In the current case, the scammers first caused pop-ups to appear on their victims' computers resembling security alerts from well-known technology companies. These are usually Apple and Microsoft.
ESET senior research fellow David Harley (who has been monitoring support scams for many years), calls them "opportunistic SEO-friendly ads claiming to be from real vendor helplines."
The false alerts claimed the computers had been breached by a virus or hacker, and urged the 'victims' to call a toll-free number for assistance. Telemarketers then took over and asked for remote access to the 'infected' computer. They then ran 'diagnostic tests' that falsely claimed to find major problems that could be solved through the purchase of a one-time fix or a long-term service plan that would cost hundreds of dollars.
The FTC filed a complaint in Ohio last year as part of an ongoing campaign called Operation Tech Trap. The defendants were Repair All PC LLC; Pro PC Repair LLC; I Fix PC LLC; WebTech World LLC; Online Assist LLC; Datadeck LLC; I Fix PC (also doing business as Techers 247, I Fix PC, and I Fix PC 247); Jessica Marie Serrano; Dishant Khanna; Mohit Malik; Romil Bhatia; Lalit Chadha; and Roopkala Chadha.
The settlements announced Monday resolve the case. The defendants have been barred from offering tech support products or services, whether genuine or fraudulent, and misrepresenting their affiliation with another company. Perhaps more to the point, the settlements also impose a $12.4 million judgement that will be suspended upon payment by the defendants of a total of $122,376.
"This scheme affected people in Ohio and across the country, and we were pleased to work with the Federal Trade Commission to shut it down," said Attorney General DeWine. "Scams regularly cross state and national borders, so this kind of collaboration is an important part of protecting consumers."
In the UK, the National Trading Standards (NTS) announced on Friday that Narendra Harilal Vadgama (age 56) has been sentenced to 12 months in prison (reduced to 9 months on a guilty plea) for a very similar offense. "Mr Vadgama's victims were targeted through cold-calling or with computer pop-ups," said the NTS. "In many of the cold-calls Mr Vadgama's company gained the trust of their victims by falsely claiming to be computer technicians from companies like Microsoft. They then claimed that the victim's computer had been compromised or their routers had been hacked or infected and needed urgent action to stop the victim's computer or data from being compromised."
Vadgama was discovered following a joint investigation by NTS, Microsoft, the UK's National Fraud Intelligence Bureau and Leicestershire police. "This case demonstrates precisely why public-private partnership is critical to tackling modern day fraud operating at global scale," commented the City of London Police's Commander Dave Clark (the national coordinator for economic crime). "Partnerships like this are increasingly being used and should send a warning to criminals that the UK is increasingly becoming a hostile environment to commit fraud in."
Whether individual successes against the support tech criminals in both the U.S. and the UK will have any great effect on the overall crime rate is a different matter. "How effective the FTC's ruling will be in practice is another question," Harley told SecurityWeek. "I suspect that it will do little to discourage the many other companies executing similar spams (though we can always hope). While there may be individual call-center operatives who don't realize that they're executing a scam -- they're not always the sharpest knives in the drawer -- I imagine that the companies who employ them are usually fully cognizant from day one. Even if the FTC sanctions are sufficiently scary to stop them operating in the same way, I suspect that there's little to stop them cashing out and/or regrouping."
Ultimately, the best defense against tech support scams is heightened user awareness. Reputable firms like Apple and Microsoft and (especially in the UK, BT) simply do not cold call their customers. Interestingly, the Microsoft survey figures suggest that aged consumers are not, as one might expect, either the prime targets or main victims. According to Microsoft, 50% of its respondents "who continued with a fraudulent interaction" were millennials aged between 18 and 34. Only 17% were over 55.
Security professionals should make sure that both their children and their parents are aware of this scam.
[Update] The FTC has just announced that it is sending 3,791 checks averaging around $176 (a total of $668,000) to victims of a tech support scam action that was settled in May 2017. Part of the settlement included turning over financial assets to the FTC. "These are legitimate checks," says the announcement. "The FTC never requires consumers to pay money or provide account information to cash a refund check."
Interestingly, the FTC also issued a warning today on a different scam: an email claiming to be Secretary Tillerson announcing a $1.8million government refund, provided the recipient sends him $320 plus personal information.
FTC law enforcement actions provided more than $6.4 billion dollars in refunds to consumers between July 2016 and June 2017.
ATM Jackpotting Attacks Strike in U.S.
30.1.2018 securityweek Hacking
Hackers have been targeting automated teller machines (ATMs) in the United States to make them spill out cash using an attack technique known as “jackpotting.”
As part of the attacks, individuals with physical access to the machines connect to them and “install malware, or specialized electronics, or a combination of both to control the operations of the ATM,” The United States Secret Service revealed in a warning issued on Friday.
The attackers targeted stand-alone ATMs located in pharmacies, big box retailers, and drive thru ATMs, the alert reads. Both individual suspects and large organized groups (both local and international organized crime syndicates) are engaged in such attacks.
“The Secret Service recently obtained credible information about planned jackpotting attacks in the U.S. through partners of our Electronic Crimes Task Force (ECTF). Subsequently, we alerted other law enforcement partners and financial institutions who could potentially be impacted by this crime,” the Secret Service warning (PDF) reads.
“The two most common ways to implement jackpotting are via Trojans and Blackbox attacks,” Sergey Golovanov, Principal Security Researcher at Kaspersky Lab, explained in an email to SecurityWeek.
When performing jackpotting via Trojans, the attackers connect a flash drive or a CD-ROM to upload the malware to the ATM, or attempt to compromise the machine via the network, Golovanov said.
“The second scenario, Blackbox, assumes that third party equipment (such as a laptop, or raspberry pie) is connected to the cash dispenser, which is responsible for collecting the money and cashing it out to the client,” Golovanov continued.
These and other compromise methods were detailed by Kaspersky Lab researchers in an interview with SecurityWeek at the DefCamp conference in Bucharest late last year.
Specific protection methods exist for both jackpotting attack methods, but ultimately it’s up to the bank to implement them or not, Golovanov said.
Although they have been long observed in Europe and Asia, jackpotting attacks haven’t targeted U.S. ATM operators until earlier this month. As part of the recently observed attacks, miscreants relied on the Blackbox technique to drain the cash from the ATMs.
In addition to the Secret Service, ATM vendors such as NCR and Diebold Nixdorf also sent out alerts last week, security blogger Brian Krebs reported.
“NCR confirms the matters reported by Brian Krebs, and had previously issued its own alert and guidance on this situation. NCR regularly and actively works with our financial solutions customers to address the security and fraud issues that impact this industry,” Owen Wild, security marketing director, NCR, told SecurityWeek via email.
“NCR has received reports from the U.S Secret Service and other sources of logical (jackpot) attacks on ATMs in the US. While at present these appear focused on non-NCR ATMs, logical attacks are an industry-wide issue. This represents the first confirmed cases of losses due to logical attacks in the US,” the company’s last week alert, which was shared with SecurityWeek, reads.
The company also provided guidance on how ATM deployers could protect their machines against these attacks and mitigate any consequences.
SecurityWeek has also contacted Diebold Nixdorf for comment, but haven’t heard back yet.
In the U.S., the attackers appear to be mainly targeting the Opteva 500 and 700 series ATMs from Diebold. With the help of an endoscope, they look inside the cash machine to locate ports to connect a laptop that contains a mirror image of the ATMs operating system, Krebs reports.
The Ploutus.D malware is also said to have been used in these attacks. Ploutus was first discovered in 2013 targeting ATMs in Mexico, and by 2014 it could also be used to withdraw cash using SMS messages.
Ploutus.D was first detailed in January last year, observed as part of attacks where money mules would open the top portion of the ATM, connect to the machine’s internals, and wait for activation codes from the actor in charge of the operation. Mainly targeting Diebold ATMs, the malware could easily be repurposed to hit machines from 40 different vendors in 80 countries.
Even unsophisticated attackers can defraud an ATM, David Vergara, Head of Global Product Marketing, VASCO Data Security, told SecurityWeek in an emailed comment. Anyone can become “a professional thief in this segment with a modest investment in cash,” Vergara says. He also urges banks to look “at and beyond reader devices and hidden cameras” when it comes to securing ATMs.
"With banks’ focus on digital channels, like ATM and mobile, to drive down costs and better serve customers, it’s no surprise that cybercrime is following. The relatively low-tech skimming attacks still represent the vast majority of ATM losses, but more coordinated attacks using physical access to the machine (i.e. master key and keyboard) along with more sophisticated malware are enabling much bigger paydays for hackers,” Vergara said.
Three Dutch banks and Tax Agency under DDoS Attacks … is it a Russian job?
30.1.2018 securityaffairs Attack
Three Dutch Banks (ABN AMRO, ING Bank, Rabobank) and Tax Agency were targeted by a coordinated DDoS Attacks a few days the revelation of the Russian APT Hack.
Early this week a massive DDoS attack targeted three Dutch banks, ABN AMRO, ING Bank, Rabobank, and the Dutch Taxation Authority (Belastingdienst).
The attack against the system of ABN AMRO started over the weekend, while both ING Bank and Rabobank suffered coordinated DDoS attacks on Monday.
while the other two banks were hit on Monday.
The DDoS attacks caused severe accessibility problems to the bank infrastructure, they prevented customers from accessing the web services.
The attack against the Dutch Tax Authority prevented taxpayers filing tax-related documents.

Who is behind the attack?
According to security experts from ESET, the origins of the attacks are servers in Russia.
“The DDoS attacks that hit ABN Amro, ING and Rabobank over the weekend and on Monday, came from servers in Russia, according to security company ESET. The company adds that this does not automatically mean that the perpetrators are also in Russia, the Telegraaf reports.” states NL Times.
“The perpetrators used a so-called botnet – an army of hijacked computers and smart devices – to commit the DDoS attacks. Using the program Zbot, they remotely ordered these devices to visit a certain site en masse, thereby overloading the site’s server and crashing the site. The command and control servers are mainly in Russia, ESET determined.”
It is difficult to attribute the attack to a specific threat actor. anyway, the cybersecurity expert Richey Gevers noted that the attacks came a few days after the story of the Cozy Bear hack operated by the Dutch Intelligence Agency AIVD. According to Gevers, the DDoS attack peaked 40 Gbps in volume of traffic.
Rickey Gevers
@UID_
Hey fellow DFIR people. Jan 25th the story broke the Dutch Intelligence Agency AIVD hacked Cozy Bear. At this moment critical Dutch infra is under (40Gbps) DDoS attack. Has anyone seen infected clients/network traffic performing a DDoS attack on Dutch infra? Please let me know.
7:51 PM - Jan 29, 2018
5 5 Replies 67 67 Retweets 57 57 likes
Twitter Ads info and privacy
The expert also added that the attackers powered the attacks using a botnet composed of home routers.
29 Jan
x0rz
@x0rz
Replying to @UID_
What are the source IPs? IoT devices?
Rickey Gevers
@UID_
The banks are not sharing much info. But they said some IPs look like routers. Thats all I know.
9:20 PM - Jan 29, 2018
Replies Retweets 2 2 likes
Twitter Ads info and privacy
The Ministry of Justice and Security called the attacks on the Dutch institutions very advanced, according to BNR. “But for example Dutch banks are known in Europe for having their cyber security in order. You often see that this provokes more advanced attacks. We are now fighting at a very high level”, the Ministry said. The Ministry can’t yet say who is behind these attacks.
Researchers from ESET claimed the attackers used the Zbot malware, a very old threat based on the infamous ZeuS banking trojan.
According to BNR, even is the malware is not complex, the Ministry of Justice and Security has classified the attacks on the Dutch institutions as very complex
“But for example Dutch banks are known in Europe for having their cyber security in order. You often see that this provokes more advanced attacks. We are now fighting at a very high level”, the Ministry said. The Ministry can’t yet say who is behind these attacks.
Crooks target ATMs with Ploutus-D malware, these are the first confirmed cases of Jackpotting in US
30.1.2018 securityaffairs Hacking
Cybercriminals are targeting ATM machines in the US forcing them to spit out hundreds of dollars with ‘jackpotting‘ attacks.
According to a senior US Secret Service official, the organization has managed to steal more than $1m from ATM machines using this technique.
Once crooks gain physical access to the ATM, they will infect it with a malware or specialized electronics that is designed to instruct the machine to deliver money in response to specific commands.
The jackpotting technique was first proposed by white hat hacker Barnaby Jack in 2010.

The popular investigator Brian Krebs obtained an alert issued by ATM maker manufacturers Diebold Nixdorf this month, the company warns of an ongoing campaign conducted by a gang in the US.
“On Jan. 21, 2018, KrebsOnSecurity began hearing rumblings about jackpotting attacks, also known as “logical attacks,” hitting U.S. ATM operators. I quickly reached out to ATM giant NCR Corp. to see if they’d heard anything. NCR said at the time it had received unconfirmed reports, but nothing solid yet.” wrote Krebs.
“On Jan. 26, NCR sent an advisory to its customers saying it had received reports from the Secret Service and other sources about jackpotting attacks against ATMs in the United States.”
“While at present these appear focused on non-NCR ATMs, logical attacks are an industry-wide issue,” the NCR alert reads. “This represents the first confirmed cases of losses due to logical attacks in the US. This should be treated as a call to action to take appropriate steps to protect their ATMs against these forms of attack and mitigate any consequences.”
The crooks are infecting the ATM with the Ploutus-D malware, the vendor warns that Opteva 500 and 700 series machines are particularly vulnerable to these attacks.
These attacks are the first confirmed cases of jackpotting attacks against ATMs in the US. Jackpotting attacks were already reported in Europe, in May 27 people have been arrested by the Europol for jackpotting attacks on ATM across many countries in Europe.
Ploutus is one of the sophisticated ATM malware that was first discovered in Mexico back in 2013. The malicious code allows crooks to steal cash from ATMs using either an external keyboard attached to the machine or by sending it SMS messages.
In January, experts at FireEye Labs have discovered a new version of the Ploutus ATM malware, the so-called Ploutus-D, that works the KAL’s Kalignite multivendor ATM platform.
The experts observed the Ploutus-D in attacks against ATM of the vendor Diebold, but the most worrisome aspect of the story is that minor changes to the malware code could allow Ploutus-D to target a wide range of ATM vendors in 80 countries.

The alert issued by Secret Service explains that the cybercriminals use an endoscope to inspect the internal parts of the ATM searching for the place where they can attach a cord that allows them to sync their laptop with the ATM’s computer.

Diebold Nixdorf urges the improvement of physical security for ATMs, especially for those located in public places such as malls and pharmacies. Also, tightening the security configuration of the firmware is recommended.
The alert issued by Secret service recommends to limit physical access to the ATM machines and implement protection mechanisms for cash modules (i.e. Use firmware with latest security functionality. use the most secure configuration of encrypted communications incl. physical authentication).
Cisco ASA software is affected by a flaw with 10 out of 10 severity rating. Patch it asap
30.1.2018 securityaffairs Vulnerebility
Cisco released security updates to address a critical security vulnerability, tracked as CVE-2018-0101, in Cisco ASA software
Cisco addressed a critical security flaw, tracked as CVE-2018-0101, in Adaptive Security Appliance (ASA) software.
The vulnerability could be exploited by a remote and unauthenticated attacker to execute arbitrary code or trigger a denial-of-service (DoS) condition causing the reload of the system.
The vulnerability was discovered by the researcher Cedric Halbronn from NCC Group, he will disclose technical details on February 2 at the Recon Brussels 2018 conference.
The flaw resides in the Secure Sockets Layer (SSL) VPN feature implemented by CISCO ASA software.
According to CISCO, it is related to the attempt to double free a memory region when the “webvpn” feature is enabled on a device. An attacker can exploit the vulnerability by sending specially crafted XML packets to a webvpn-configured interface.
“A vulnerability in the Secure Sockets Layer (SSL) VPN functionality of the Cisco Adaptive Security Appliance (ASA) Software could allow an unauthenticated, remote attacker to cause a reload of the affected system or to remotely execute code.” reads the security advisory published by CISCO.
“The vulnerability is due to an attempt to double free a region of memory when the webvpn feature is enabled on the Cisco ASA device. An attacker could exploit this vulnerability by sending multiple, crafted XML packets to a webvpn-configured interface on the affected system. An exploit could allow the attacker to execute arbitrary code and obtain full control of the system, or cause a reload of the affected device.”
Below the list of affected CISCO ASA products:
3000 Series Industrial Security Appliance (ISA)
ASA 5500 Series Adaptive Security Appliances
ASA 5500-X Series Next-Generation Firewalls
ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
ASA 1000V Cloud Firewall
Adaptive Security Virtual Appliance (ASAv)
Firepower 2100 Series Security Appliance
Firepower 4110 Security Appliance
Firepower 9300 ASA Security Module
Firepower Threat Defense Software (FTD)
The vulnerability was introduced in Firepower Threat Defense 6.2.2 that implemented the remote access VPN feature since September 2017.
Cisco has addressed the vulnerability by issuing security updates for each of the affected CISCO ASA software that are still supported by the company.
The Cisco Product Security Incident Response Team (PSIRT) is aware of public knowledge of the vulnerability, but Cisco confirmed that it is not aware of any attacks in the wild that are exploiting this vulnerability.
Heat Map Released by Fitness Tracker Reveals Location of Secret Military Bases
30.1.2018 thehackernews BigBrothers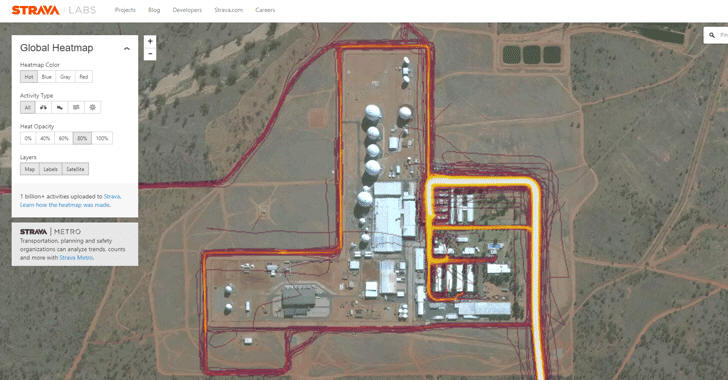
Every one of us now has at least one internet-connected smart device, which makes this question even more prominent —how much does your smart device know about you?
Over the weekend, the popular fitness tracking app Strava proudly published a "2017 heat map" showing activities from its users around the world, but unfortunately, the map revealed what it shouldn't—locations of the United States military bases worldwide.
Strava which markets itself as a "social-networking app for athletes" publicly made available the global heat map, showing the location of all the rides, runs, swims, and downhills taken by its users, as collected by their smartphones and wearable devices like Fitbit.
Since Strava has been designed to track users’ routes and locations, IUCA analyst Nathan Ruser revealed that the app might have unintentionally mapped out the location of some of the military forces around the world, especially some secret ones from the United States.
With a total of one billion activities logged on the Strava's activity map, it is a whole lot of useful data from all over the world.
Although Strava's publicly available activity map was live as of November 2017, Ruser recently noticed that the map includes the fitness routes of army soldiers and agents in secret base locations, including U.S. military bases in Afghanistan and Syria, a suspected CIA base in Somalia and even Area 51.
Besides American military bases, the map also revealed the UK's RAF Mount Pleasant airbase in the Falkland Islands, Lake Macphee and Gull Island Pond, among others. Russian bases have also been showed up by the Strava data.
What's more? Security experts on Twitter have also discovered potentially sensitive American military bases in Somalia, Afghanistan and Syria; secret Russian military bases in Ukraine; a secret missile base in Taiwan, as well as an NSA base in Hawaii.
Ruser said that the map allowed him to find out regular jogging routes for military personnel, which is bad news for security, as it establishes reliable "pattern of life" information that would otherwise be secret from the rest of the world.
"If soldiers use the app like normal people do, by turning it on tracking when they go to do exercise, it could be especially dangerous. This particular track looks like it logs a regular jogging route. I shouldn't be able to establish any Pattern of life info from this far away," Ruser tweeted.
Should Strava be blamed entirely for this revelation?
Strava said its heat map is based only on publically available data, and the company does offer a private mode that allows its users to turn off data sharing outside of the app.
However, it appears that many American and foreign military personnel using the app were sharing the confidential information publicly—perhaps without the knowledge or realising the implication, which is terrible.
What's even worse?
A security researcher told the Washington Post that this publically available data could even help enemy forces plan an "attack or ambush U.S. troops in or around the bases."
To make things even worse, some experts have also found ways to deanonymize the Strava heatmap, identifying individuals and their location where they have been exercising.
Strava has reminded its users that they could turn off location services for the app and that the map does not include private activities or areas deemed private.
"Our global heat map represents an aggregated and anonymised view of over a billion activities uploaded to our platform," Strava said in a statement. "It excludes activities that have been marked as private and user-defined privacy zones. We are committed to helping people better understand our settings to give them control over what they share."
The incident is a great reminder for people, especially for those working in or around sensitive locations, to turn off location sharing services for everything.
Moreover, militaries should also consider limiting smartphones and wearables use in sensitive areas as well as educate their soldiers on the importance of privacy.
Someone Stole Almost Half a BILLION Dollars from Japanese Cryptocurrency Exchange
30.1.2018 thehackernews CyberCrime
Coincheck, a Tokyo-based cryptocurrency exchange, has suffered what appears to be the biggest hack in the history of cryptocurrencies, losing $532 million in digital assets (nearly $420 million in NEM tokens and $112 in Ripples).
In 2014, Mt Gox, one of the largest bitcoin exchange at that time, filed for bankruptcy after admitting it had lost $450 million worth of Bitcoins.
Apparently, the cryptocurrency markets reacted negatively to the news, which resulted in 5% drop in Bitcoin price early this morning.
In a blog post published today, the Tokyo-based cryptocurrency exchange confirmed the cyber heist without explaining how the tokens were stolen, and abruptly froze most of its services, including deposits, withdrawals and trade of almost all cryptocurrencies, except Bitcoin.
Coincheck also said the exchange had even stopped deposits into NEM cryptocurrencies, which resulted in 16.5% drop in NEM coin value, as well as other deposit methods including credit cards.
During a late-night press conference at the Tokyo Stock Exchange, Coincheck Inc. co-founder Yusuke Otsuka also said that over 500 million NEM tokens (then worth around $420 million) were taken from Coincheck's digital wallets on Friday, but the company didn’t know how the tokens went missing, according to new source Asahi.
The digital-token exchange has already reported the incident to the law enforcement authorities and to Japan's Financial Services Agency to investigate the cause of the missing tokens.
"We will report on the damage situation and cause of the case, measures to prevent recurrence, but first we would like you to take every possible measure to protect our customers," said Executives of the Financial Services Agency (translated).
This incident marks yet another embarrassing hack in the world of digital currency technology, once again reminding us that the volatility in cryptocurrency prices is not going away anytime soon.
So far, the exchange has not provided any official statement regarding the cause of this hack. We will keep you updated about this incident. Stay Tuned!
Nearly 2000 WordPress Websites Infected with a Keylogger
30.1.2018 thehackernews Virus
More than 2,000 WordPress websites have once again been found infected with a piece of crypto-mining malware that not only steals the resources of visitors' computers to mine digital currencies but also logs visitors' every keystroke.
Security researchers at Sucuri discovered a malicious campaign that infects WordPress websites with a malicious script that delivers an in-browser cryptocurrency miner from CoinHive and a keylogger.
Coinhive is a popular browser-based service that offers website owners to embed a JavaScript to utilise CPUs power of their website visitors in an effort to mine the Monero cryptocurrency.
Sucuri researchers said the threat actors behind this new campaign is the same one who infected more than 5,400 Wordpress websites last month since both campaigns used keylogger/cryptocurrency malware called cloudflare[.]solutions.
Spotted in April last year, Cloudflare[.]solutions is cryptocurrency mining malware and is not at all related to network management and cybersecurity firm Cloudflare. Since the malware used the cloudflare[.]solutions domain to initially spread the malware, it has been given this name.
The malware was updated in November to include a keylogger. The keylogger behaves the same way as in previous campaigns and can steal both the site's administrator login page and the website's public facing frontend.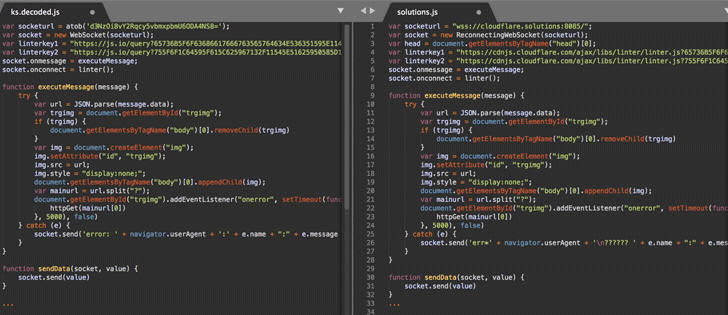
If the infected WordPress site is an e-commerce platform, hackers can steal much more valuable data, including payment card data. If hackers manage to steal the admin credentials, they can just log into the site without relying upon a flaw to break into the site.
The cloudflare[.]solutions domain was taken down last month, but criminals behind the campaign registered new domains to host their malicious scripts that are eventually loaded onto WordPress sites.
The new web domains registered by hackers include cdjs[.]online (registered on December 8th), cdns[.]ws (on December 9th), and msdns[.]online (on December 16th).
Just like in the previous cloudflare[.]solutions campaign, the cdjs[.]online script is injected into either a WordPress database or the theme's functions.php file. The cdns[.]ws and msdns[.]online scripts are also found injected into the theme's functions.php file.
The number of infected sites for cdns[.]ws domain include some 129 websites, and 103 websites for cdjs[.]online, according to source-code search engine PublicWWW, though over a thousand sites were reported to have been infected by the msdns[.]online domain.
Researchers said it's likely that the majority of the websites have not been indexed yet.
"While these new attacks do not yet appear to be as massive as the original Cloudflare[.]solutions campaign, the reinfection rate shows that there are still many sites that have failed to properly protect themselves after the original infection. It’s possible that some of these websites didn't even notice the original infection," Sucuri researchers concluded.
If your website has already been compromised with this infection, you will require to remove the malicious code from theme's functions.php and scan wp_posts table for any possible injection.
Users are advised to change all WordPress passwords and update all server software including third-party themes and plugins just to be on the safer side.
Hard-coded Password Lets Attackers Bypass Lenovo's Fingerprint Scanner
30.1.2018 thehackernews Safety
Lenovo has recently rolled out security patches for a severe vulnerability in its Fingerprint Manager Pro software that could allow leak sensitive data stored by the users.
Fingerprint Manager Pro is a utility for Microsoft Windows 7, 8 and 8.1 operating systems that allows users to log into their fingerprint-enabled Lenovo PCs using their fingers. The software could also be configured to store website credentials and authenticate site via fingerprint.
In addition to fingerprint data, the software also stores users sensitive information like their Windows login credentials—all of which are encrypted using a weak cryptography algorithm.
According to the company, Fingerprint Manager Pro version 8.01.86 and earlier contains a hard-coded password vulnerability, identified as CVE-2017-3762, that made the software accessible to all users with local non-administrative access.
"Sensitive data stored by Lenovo Fingerprint Manager Pro, including users’ Windows logon credentials and fingerprint data, is encrypted using a weak algorithm, contains a hard-coded password, and is accessible to all users with local non-administrative access to the system it is installed in," the company said in its advisory, giving brief about the vulnerability.
The vulnerability impacts Lenovo ThinkPad, ThinkCentre and ThinkStation laptops, and affects more than two dozen Lenovo ThinkPad models, five ThinkStation Models and eight ThinkCentre models that run Windows 7, 8 and the 8.1 operating systems.
Here's the full list of Lenovo devices compatible with Fingerprint Manager Pro and impacted by the vulnerability:
ThinkPad L560
ThinkPad P40 Yoga, P50s
ThinkPad T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560
ThinkPad W540, W541, W550s
ThinkPad X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT)
ThinkPad X240, X240s, X250, X260
ThinkPad Yoga 14 (20FY), Yoga 460
ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, M93z
ThinkStation E32, P300, P500, P700, P900
Lenovo has credited security researcher Jackson Thuraisamy with Security Compass for discovering and responsibly reporting the vulnerability.
The popular Chinese computer manufacturer strongly recommends its ThinkPad customers to update their devices to Fingerprint Manager Pro version 8.01.87 or later to address the issue. You can also head on to the company's official website to do so.
Since Microsoft added native fingerprint reader support with Windows 10 operating system, thus eliminating the need for the Fingerprint Manager Pro software, Lenovo laptops running Windows 10 are not impacted by the vulnerability.
Intel reportedly alerted Chinese companies before US Government about Meltdown and Spectre flaws
30.1.2018 securityaffairs BigBrothers
According to the Wall Stree Journal, Intel reportedly alerted Chinese companies before US Gov about Meltdown and Spectre vulnerabilities.
There is no peace for Intel, according to a report published by The Wall Street Journal the company warned Chinese tech giants about the Meltdown and Spectre vulnerabilities before notifying them to the US government.
Citing unnamed people familiar with the matter and some of the companies involved, The WSJ revealed that the list of Chinese companies includes Lenovo and Alibaba.
It is not clear when Intel notified the flaw to Lenovo, but a leaked memo from Intel to computer makers suggests the company reported the issues to an unnamed group of on November 29 via a non-disclosure agreement. The same day, the Intel CEO Brian Krzanich sold off his shares.
Last week, French tech publication LeMagIT’s Christophe Bardy disclosed the first page of the “Technical Advisory” issued by the Intel Product Security Incident Response Team.
Of course, security experts speculate the companies might have passed this information to the Chinese Government, but Alibaba spokesman refused any accusation.
I personally believe that the Chinese Government was informed by the companies about the Meltdown and Spectre vulnerabilities and it is disconcerting that the US intelligence agencies neither US CERTs were not aware of the flaws.
Meltdown Spectre patches
We also know that the Meltdown flaw is easy to exploit, this means that it is likely that threat actors might have triggered it to extract passwords and other sensitive data from a target machine. The situation is worrisome in cloud-computing environments were many customers share the same servers, in this scenario an attacker can launch a Meltdown attack to steal info belonging to other clients with applications hosted on the same server.
El Reg reached Intel for a comment, below the reply of the chip vendor:
“The Google Project Zero team and impacted vendors, including Intel, followed best practices of responsible and coordinated disclosure. Standard and well-established practice on initial disclosure is to work with industry participants to develop solutions and deploy fixes ahead of publication. In this case, news of the exploit was reported ahead of the industry coalition’s intended public disclosure date at which point Intel immediately engaged the US government and others.” states the El Reg.
Let me close with this eloquent Tweet published by security journalist Zach Whittaker:
Zack Whittaker
✔
@zackwhittaker
This is grade A crap. Several people told me Meltdown/Spectre's planned disclosure was set for Jan. 9 but was revealed on Jan. 3 after a PoC came out. Based on WSJ, Intel was going to tell the US gov. only a week before disclosure?! It knew since June! https://techmeme.com/#a180128p6
8:39 PM - Jan 28, 2018 · Manhattan, NY
#ThinkBeyond – Security solutions from market leaders may all fail in your particular environment
30.1.2018 securityaffairs Security
Buying solutions proposed by analyst firms without carefully analyzing your organization expose it to cyber threats. It’s time to #ThinkBeyond this broken paradigm.
The cybersecurity market is expected to double by 2022, analysts estimated the growth could reach three hundred thousand dollars, at a Compound Annual Growth Rate (CAGR) of 11.0%. In the same period, the number of cyber attacks are expected to increase, hackers will adopt new sophisticated techniques while the surface of attacks of companies and organizations is enlarging due to the adoption of paradigms such as the Internet of Things, Cloud computing, and mobile computing.
Another important element that will characterize the next months it the adoption of new regulations and directives, such as the GDPR and the NIS directive, that will influence the evolution of the market.
Businesses will face the “perfect storm,” the ideal condition for security firms that continue to develop new solutions designed to cover a specific portion of the market instead of responding to the real needs for cyber security of their customers.
The increasing number of successful cyber attacks and the daily security breaches reported by experts demonstrate that most of the companies are still far from an adequate security posture.
In origin it was mainly a problem of awareness on cyber threats, but now the critical issue is represented by the ability of businesses and decision makers in buying security solutions that match their needs.
The purchase of a new security solution or a service is often driven by the recommendations of analysts that produce any kind of report to influence the final decision of the management and the IT staff.
The emulation is part of the human nature, for C-Level personnel is easy to select their business partners by choosing them from the companies listed in authoritative studies and publications such as the Gartner Magic Quadrant.
Evidently, this approach is not sufficient to ensure the resilience to cyber attacks of a modern business.
In many cases the same security companies suggested by these reports were involved in embarrassing incidents, this is the case of the accountancy firm Deloitte that was awarded as the best Security Consulting Services providers by Gartner, but that was victims itself of a sophisticated hack that compromised its global email server in 2016.
These studies could influence a blind and an unaware choice of security solutions, they could give businesses a false sense of security.
It is absurd to compose a security infrastructure only by implementing the recommendations of the analyst firms while the events in the threat landscape demonstrate that such an approach is ruinous.
A model of cyber security driven by profits could not be effective against cyber threats. Threat actors rapidly and continuously change their Tactics, Techniques, and Procedures (TTPs ), and security industry is not able to follow them.
Security investments should be measured by the amount of cyber risk mitigated per dollar spent, only in this way it is possible to evaluate real enhancement of the resilience of an architecture while adding new components to the mosaic.
Before deciding to read a report from major analyst companies that suggest products from IT giants, it is essential for any organization to assess and prioritize all cyber risks and business processes.
The risk assessment must involve as many stakeholders, this is the best way to protect our infrastructure from several threat actors.
Once all the risks are identified and prioritized, the company will have to mitigate them by using systems inside their infrastructure and eventually integrating them with proper solutions. Instruments like Gartner’s Magic Quadrant could help companies to select vendors with a filtrated vision of the market, however, we cannot forget that security solutions from market leaders may all fail in a particular environment.
The adoption of security solutions that are recognized by the analysis as leading products of the cyber security industry will not protect our organizations for multiple reasons.
The reality is disconcerting, in most of the security breaches the attackers were able to bypass the stack of security solutions deployed by the victims to defend their infrastructure.
We cannot continue to build our defence implementing a model of cyber security that is imposed by a restricted number of firms. From the attacker’s perspective, #ThinkBeyondit is easy to predict the type of defence measures in place and adopt the necessary changes in their attack chain.
Don’t forget that threat actors continuously monitor our infrastructure and companies need to avoid in providing points of reference that could be the starting points for their offensive.
The choice of the components for the infrastructure of a company must be driven by an objective analysis of the context in which they operate and carefully considering the evolution of cyber threats.
Security solutions must be user-friendly, overly-complex systems make it hard to use. Another problem related to the choice of security products and services is related to the capability of the organization in processing their output of the defence systems. In a real scenario, cyber security analysts often miss the vast majority of alerts and warnings because of the huge volume of information generated by security solutions.
Most of the leading security firms urge a layered approach in cyber security, but what happens if these layers are not able to “correctly” exchange information each other, or in a worst scenario there are affected by vulnerabilities that can be triggered to compromise the security of the overall architecture.
Building a layered defense system doesn’t mean to simply put together the security products and service suggested by prominent studies, but the analysis must go beyond.
The integration is the most complicated part in setting up a security infrastructure, every time the IT staff intends to add another piece to their cyber barricade it needs to carefully understand the way various components interact and which are the behavior of the resulting system.
Buying solutions proposed by analyst firms will not protect the organizations, spending more doesn’t necessarily mean you will be secure, this must be clear to anyone that works to increase the resilience of its systems to cyber attacks. It’s time to #ThinkBeyond this broken paradigm.