Critical Oracle Micros POS Flaw Affects Over 300,000 Payment Systems
1.2.2018 thehackernews Vulnerebility
Oracle has released a security patch update to address a critical remotely exploitable vulnerability that affects its MICROS point-of-sale (POS) business solutions for the hospitality industry.
The fix has been released as part of Oracle's January 2018 update that patches a total of 238 security vulnerabilities in its various products.
According to public disclosure by ERPScan, the security firm which discovered and reported this issue to the company, Oracle's MICROS EGateway Application Service, deployed by over 300,000 small retailers and business worldwide, is vulnerable to directory traversal attack.
If exploited, the vulnerability (CVE-2018-2636) could allow attackers to read sensitive data and receive information about various services from vulnerable MICROS workstations without any authentication.
Using directory traversal flaw, an unauthorized insider with access to the vulnerable application could read sensitive files from the MICROS workstation, including service logs and configuration files.
As explained by the researchers, two such sensitive files stored within the application storage—SimphonyInstall.xml or Dbconfix.xml—contain usernames and encrypted passwords for connecting to the database.
"So, the attacker can snatch DB usernames and password hashes, brute them and gain full access to the DB with all business data. There are several ways of its exploitation, leading to the whole MICROS system compromise," the researchers warned.
"If you believe that gaining access to POS URL is a snap, bear in mind that hackers can find digital scales or other devices that use RJ45, connect it to Raspberry PI, and scan the internal network. That is where they easily discover a POS system. Remember this fact when you pop into a store."
ERPScan has also released a proof-of-concept Python-based exploit, which, if executed on a vulnerable MICROS server, would send a malicious request to get the content of sensitive files in response.
Besides this, Oracle's January 2018 patch update also provides fixes for Spectre and Meltdown Intel processor vulnerabilities affecting certain Oracle products.
Serious Flaws Affect Several ManageEngine Products
1.2.2018 securityweek Vulnerebility
Researchers at Digital Defense have uncovered several potentially serious vulnerabilities in IT management products from ManageEngine, including ones that allow an attacker to take complete control of the affected application. The vendor has released patches to address the flaws.
Zoho-owned ManageEngine provides network, data center, desktop and mobile device, and security solutions to more than 40,000 customers, including three out of every five Fortune 500 company.
One of the flaws found by Digital Defense affects ManageEnegine’s ServiceDesk Plus help desk software. An unauthenticated file upload vulnerability allows an attacker to upload a JavaScript web shell and use it to execute arbitrary commands with SYSTEM privileges.
Experts also discovered several blind SQL injection vulnerabilities that allow an unauthenticated attacker to take complete control of an application and possibly even the underlying host.
These types of flaws have been found in the OpManager network monitoring product, Network Configuration Manager, bandwidth monitoring and traffic analysis product NetFlow Analyzer, firewall configuration and log management product Firewall Analyzer, and IP address management app OpUtils.
These products are also impacted by an enumeration issue that can be exploited to access user information such as usernames, email addresses and phone numbers.
An attacker could gain access to the content of files on the host running ManageEngine applications by leveraging an unauthenticated XML External Entity (XXE) vulnerability.
Digital Defense said ManageEngine promptly responded to its vulnerability reports and released updates for each of the affected applications to address the security holes.
“Application layer vulnerabilities continue to be a key area of focus for software vendors,” said Mike Cotton, vice president of engineering at Digital Defense. “We are pleased to work collaboratively with affected vendors to facilitate prompt resolution, ensuring our clients and enterprises are protected from any potential exploitation of these vulnerabilities.”
Digital Defense recently reported discovering authentication bypass, arbitrary file upload, and path traversal vulnerabilities affecting data protection products from both Dell EMC and VMware.
Malware exploiting Spectre and Meltdown flaws are currently based on available PoC
1.2.2018 securityaffairs Virus
Malware Exploiting Spectre, Meltdown Flaws Emerges
Researchers at the antivirus testing firm AV-TEST have discovered more than 130 samples of malware that were specifically developed to exploit the Spectre and Meltdown CPU vulnerabilities.
The good news is that these samples appear to be the result of testing activities, but experts fear that we could soon start observing attacks in the wild.
Most of the codes obtained by AV-TEST are just recompiled versions of the Proof of Concept code available online. Experts at AV-TEST also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.
“We also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.”Andreas Marx, CEO of AV-TEST, told SecurityWeek.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
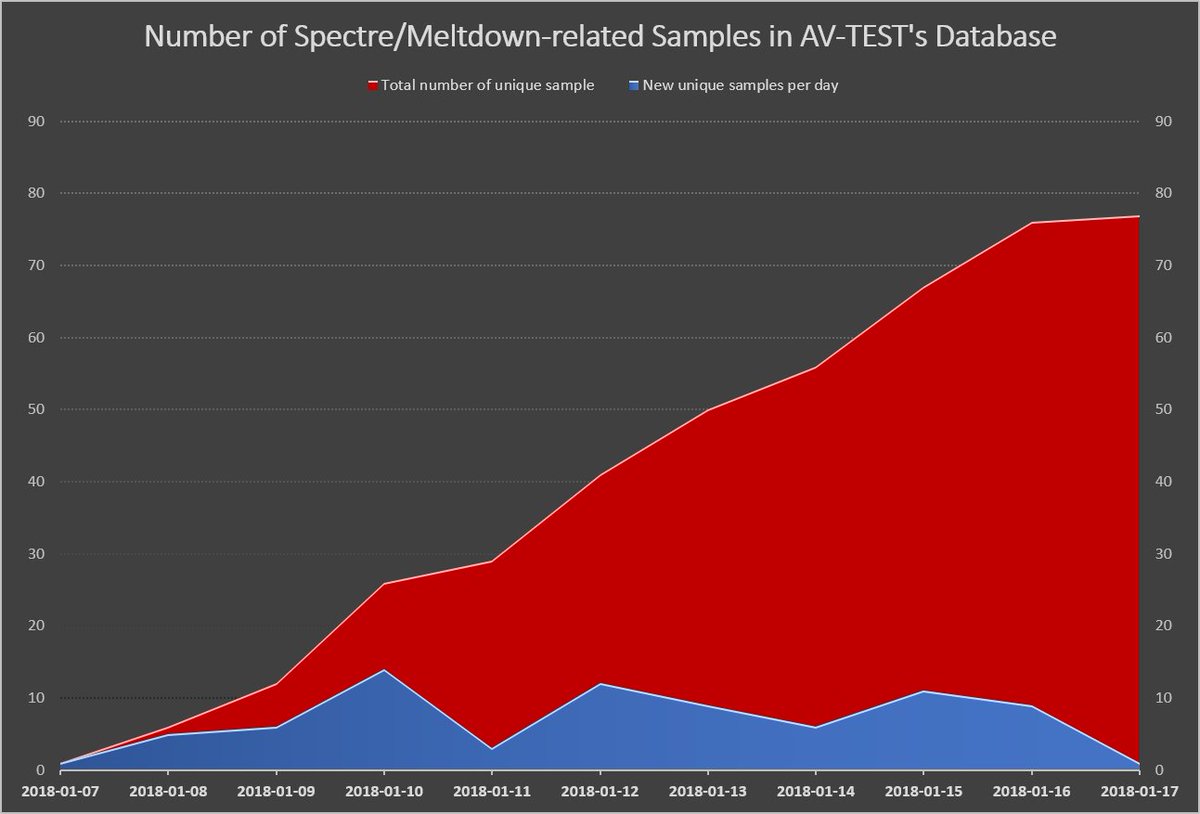
On January 17, experts at AV-TEST reported that they had detected 77 malware samples apparently related to the Intel vulnerabilities.
AV-TEST GmbH
✔
@avtestorg
#Spectre & #Meltdown: So far, the AV-TEST Institute discovered 77 samples which appear to be related to recently reported CPU vulnerabilities. #CVE-2017-5715 #CVE-2017-5753 #CVE-2017-5754
2:49 PM - Jan 17, 2018
7 7 Replies 24 24 Retweets 27 27 likes
Twitter Ads info and privacy
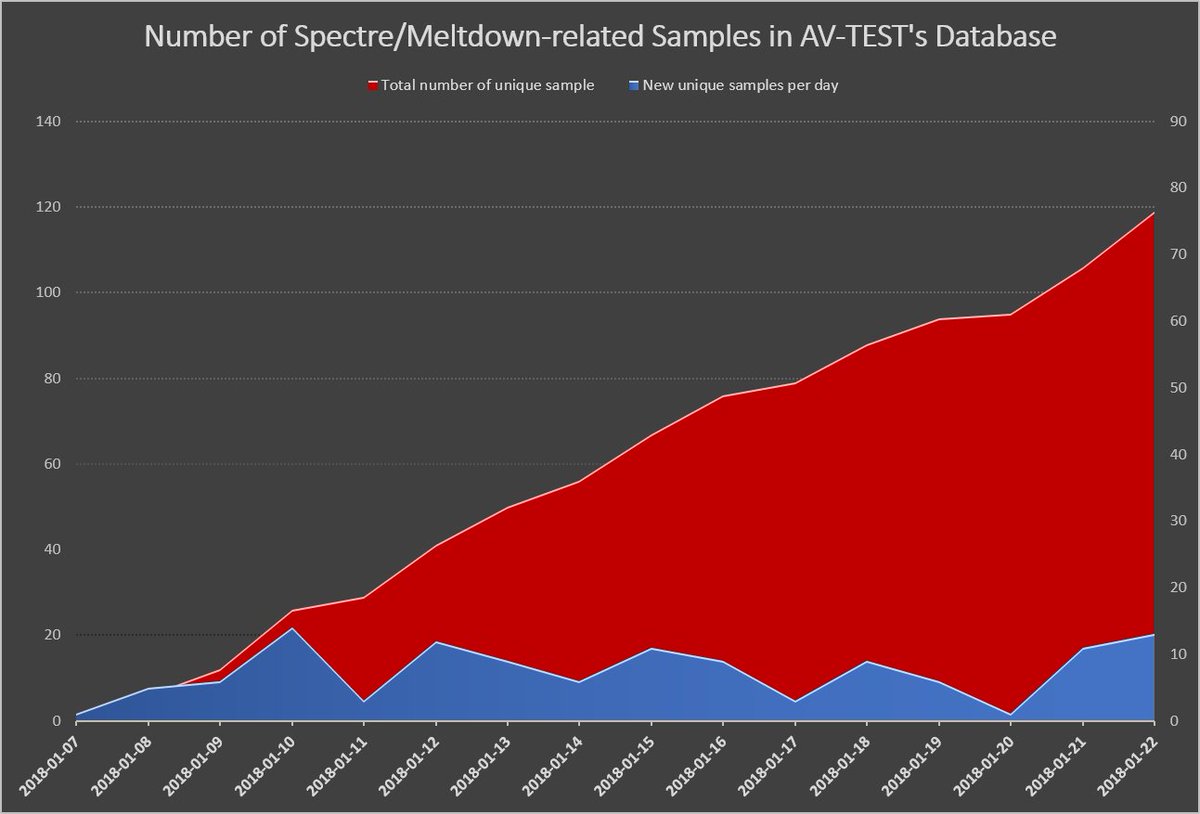
The number of malware samples related to Meltdown and Spectre reached pi119 by January 23.
AV-TEST GmbH
✔
@avtestorg
[UPDATE: 2018-01-23] #Spectre & #Meltdown: So far, the AV-TEST Institute discovered 119 samples which appear to be related to recently reported CPU vulnerabilities. #CVE-2017-5715 #CVE-2017-5753 #CVE-2017-5754
SHA256 Hashes: https://plus.google.com/b/100383867141221115206/photos/photo/100383867141221115206/6514266175374877506 …
4:23 PM - Jan 23, 2018
2 2 Replies 14 14 Retweets 24 24 likes
Twitter Ads info and privacy
On January 31, AV-TEST confirmed to be in possession of 139 samples from various sources.

AV-TEST GmbH
✔
@avtestorg
[UPDATE: 2018-01-23] #Spectre & #Meltdown: So far, the AV-TEST Institute discovered 119 samples which appear to be related to recently reported CPU vulnerabilities. #CVE-2017-5715 #CVE-2017-5753 #CVE-2017-5754
SHA256 Hashes: https://plus.google.com/b/100383867141221115206/photos/photo/100383867141221115206/6514266175374877506 …
4:23 PM - Jan 23, 2018
2 2 Replies 14 14 Retweets 24 24 likes
Twitter Ads info and privacy
According to the AV-TEST CEO, several groups of experts are working on a malware that could trigger Intel flaws, most of them are re-engineering the available PoC.
“We aren’t the only ones concerned. Others in the cybersecurity community have clearly taken notice, because between January 7 and January 22 the research team at AV-Test discovered 119 new samples associated with these vulnerabilities,” reads a blog post published by Fortinet. “FortiGuard Labs has analyzed all of the publicly available samples, representing about 83 percent of all the samples that have been collected, and determined that they were all based on proof of concept code. The other 17 percent may have not been shared publicly because they were either under NDA or were unavailable for reasons unknown to us.”
Mozilla fixes a critical remote code execution vulnerability in Firefox
1.2.2018 securityaffairs Vulnerebility
Mozilla has released security updates for Firefox 58 that addresses a critical remote code vulnerability that allows a remote attacker to run arbitrary code on vulnerable systems.
Mozilla has released an update for the Firefox 58 browser (aka Firefox Quantum) that addresses a critical flaw that could be exploited by a remote attacker to execute arbitrary code on computers running the vulnerable version of the browser.
The vulnerability, tracked as CVE-2018-5124, affects Firefox versions 56 through 58, meanwhile, it doesn’t impact Firefox for Android and Firefox 52 ESR.
The development teams behind major Linux distributions have also started rolling out updated packages that fix the flaw.
It was discovered by the Mozilla developer Johann Hofmann.
According to a security advisory published by Cisco, the Firefox 58.0.1 version fixed an ‘arbitrary code execution’ flaw that originates due to ‘insufficient sanitization’ of HTML fragments in chrome-privileged documents (browser UI).
“A vulnerability in Mozilla Firefox could allow an unauthenticated, remote attacker to execute arbitrary code on a targeted system.” states the security advisory.
“The vulnerability is due to insufficient sanitization of HTML fragments in chrome-privileged documents by the affected software. An attacker could exploit the vulnerability by persuading a user to access a link or file that submits malicious input to the affected software. A successful exploit could allow the attacker to execute arbitrary code with the privileges of the user. If the user has elevated privileges, the attacker could compromise the system completely.“
Firefox 58 was released on January 23, it addresses more than 30 vulnerabilities in the popular browser, some of them rated as high severity, including a use-after-free, buffer overflow, and integer overflow flaws.
According to Mozilla, its bug bounty program has already paid out nearly $1 million to white hat hackers who reported vulnerabilities.
Don’t waste time, apply the software updates as soon as possible.
FBI Pushes for Small Business Information Sharing
31.1.2018 securityweek BigBrothers
Howard S. Marshall, Deputy Assistant Director of the Cyber Division of the FBI, spoke Tuesday before the House Small Business Committee on the subject of 'Small Business Information Sharing: Combating Foreign Cyber Threats.' The purpose was to outline the FBI's role in helping small businesses defend against cyber threats.
His statement came in two parts: first, to outline the major cyber threats to U.S. business, and then to outline the FBI's response to these threats.
"Some of the more prevalent or rising cyber threats to small businesses," he said, include business e-mail compromise (BEC); ransomware; criminal data breach activity; and the internet of things (IoT). He did not provide any statistics on these cybercrimes, but instead concentrated on a high-level description of the threats with a brief explanation of FBI advice on countering them.
The FBI's advice for BEC is that companies should require a second, independent verification on payment requests; that e-mail accounts should have regularly changed strong passwords and two-factor authentication; and that companies should use their own domain-based email rather than free web-based email. Wherever possible, the last recommendation should be supported a filter system that flags emails with look-alike domain names.
The primary advice against ransomware, which the FBI expects "to remain a significant threat to businesses in the U.S. and worldwide", is that businesses should schedule regular backups to drives not connected to their network. "These drives can be used to restore a system to the backup version without paying the ransom to the perpetrator."
There is no specific advice on whether businesses should or should not pay the ransom, although it is known that the FBI -- and LEAs generally -- would prefer that ransoms are not paid. Marshall did say, however, "It is important to note that even if a ransom is paid, there is no guarantee the business or individual will obtain their files from the cyber criminal."
In two recent ransomware incidents, two separate healthcare organizations were infected with different variants of the SamSam ransomware. One, Hancock Health, decided to pay the ransom. It was infected on January 11 and was back online by January 15. The second, Allscripts, chose not to pay the ransom. It was infected on January 18. On January 26, Allscripts emailed SecurityWeek, "We are pleased to announce that service to all affected clients has been restored." In the final analysis, whether to pay or not is a risk-based decision for each individual victim.
'Criminal data breach activity' is such a vast subject that the statement makes little attempt to discuss it in detail. This is probably a mistake since it could leave politicians with the idea that small businesses are at less risk of hacker attacks than large organizations -- which is not correct. All that Marshall says here is, "We encourage businesses to apply a variety of best practices to secure their network architecture."
The growing IoT threat is discussed as a problem with no current solution. "Increased connectivity through IoT devices will only increase the potential attack surface for networks, as cyber security is largely under-prioritized from device design through implementation." Marshall highlighted the IoT-based DDoS attacksof late 2016. He said, "Individuals and businesses can prevent their devices from being compromised by changing default user name and passwords, ensuring device firmware is up to date, implementing strong firewall rules, and by turning off or rebooting devices when not in use."
The long-term solution to the IoT threat will come from better designed and built devices, and he noted that NIST is currently developing standards to improve IoT devices.
The description of current threats provides the background for the second half of the statement: 'FBI Cyber private sector engagement', which is described as a key component of the FBI's strategy for combating cyber threats. This engagement has required a change to the FBI's traditional methods of intelligence gathering. Traditionally, intelligence has been gathered from its own operations, from intelligence services, and from other LEAs.
"However," said Marshall, "we are now also looking to integrate private industry information into our intelligence cycle to enhance our ability to identify and respond to both emerging and ongoing threats." The FBI is particularly looking to private industry to share both its understanding of sector-specific networks, and its threat intelligence in order to integrate that understanding into its own intelligence cycle. "This type of information sharing enables us to provide more specific, actionable, and timely information to our industry partners so they can protect their systems in a proactive manner."
The FBI accepts that such information sharing must be two-way. Marshall described some of the FBI's outreach projects: nearly 70 public service announcements (PSAs) over the past five years, and other notifications including FBI Liaison Alert System (FLASH) reports, and private industry notifications (PINs).
Other projects include its involvement with the National Cyber-Forensics and Training Alliance (NCFTA); its public awareness campaigns or 'open houses' to educate businesses on serious cyber threats; its workshops on specific threats (such as BEC); and its countrywide briefings, conferences, and workshops for key executives throughout industry. There have been nearly 2800 of the latter over the past five years.
This is achievable through the FBI's countrywide decentralized organization, with field offices in every state. "Cyber-trained special agents are in each field office, providing locally available expertise to deploy to victim sites immediately upon notice of an incident," he said.
One aspect of the FBI statement stands out. Marshall goes to some length to stress that the FBI will treat cyber victims as the victim. "No matter what course of action is deemed appropriate, the FBI views a company that has been attacked as a victim and will protect investigative information appropriately." This goes to the heart of the FBI's problem in engaging with small businesses. While companies will automatically consider the FBI as the first port of call in an emergency, other engagements are traditionally avoided or concerning.
Voluntarily offering operational details to the FBI is not yet in the psyche of small business -- and yet this must be achieved for the FBI to fulfil its purpose. That ultimate purpose, says the statement, is to "provide information that can be used to initiate indictments, affect arrests, generate demarches, or produce international sanctions against those who conduct cyber attacks or aggressive actions against entities in the United States."
Mozilla Patches Critical Code Execution Flaw in Firefox
31.1.2018 securityweek Vulnerebility
An update released this week by Mozilla for Firefox 58 patches a critical vulnerability that can be exploited by a remote attacker for arbitrary code execution.
Mozilla developer Johann Hofmann discovered that arbitrary code execution is possible due to unsanitized output in the browser UI.
The vulnerability, tracked as CVE-2018-5124, affects Firefox versions 56 through 58 and it has been fixed with the release of Firefox 58.0.1. According to Mozilla, Firefox for Android and Firefox 52 ESR are not impacted. Linux distributions have also started pushing out updated packages that include the fix.
“The vulnerability is due to insufficient sanitization of HTML fragments in chrome-privileged documents by the affected software,” Cisco said in an advisory describing this flaw. “An attacker could exploit the vulnerability by persuading a user to access a link or file that submits malicious input to the affected software. A successful exploit could allow the attacker to execute arbitrary code with the privileges of the user. If the user has elevated privileges, the attacker could compromise the system completely.”
Firefox 58, which Mozilla released on January 23, patches more than 30 vulnerabilities, including a potentially exploitable use-after-free bug and various memory safety issues that have been rated critical.
Firefox 58 also addresses over a dozen high severity flaws, including use-after-free, buffer overflow, and integer overflow bugs. A vulnerability that allows WebExtensions to bypass user prompts to download and open an arbitrarily file has also been classified as high severity.
Ten of these security holes were also addressed earlier this month in the Thunderbird email client with the release of version 52.6. Mozilla pointed out that the flaws typically cannot be exploited against Thunderbird using specially crafted emails.
Mozilla runs a bug bounty program for Firefox and the organization claims it has paid out nearly $1 million to experts who reported vulnerabilities. Hackers can earn between $3,000 and $7,500 for critical and high severity flaws in Mozilla software, but a novel exploit or form of exploitation can earn more than $10,000.
In addition to its software bug bounty program, Mozilla rewards flaws discovered in its websites and services with up to $5,000. The organization says it has paid out a total of roughly $3 million across its bug bounty programs.
Asus Router Flaws Disclosed by Several Researchers
31.1.2018 securityweek Vulnerebility
Several security researchers and companies have recently disclosed the details of potentially serious vulnerabilities they discovered in the past months in various Asus routers.
Fortinet reported on Tuesday that its researchers had found a vulnerability in some Asus routers that allows an authenticated attacker to execute arbitrary commands with root privileges.
“Technically, vulnerable models are prone to OS command injections via unsanitized parameters passed to the /apply.cgi,” Fortinet explained. “In Main_Analysis_Content.asp in particular, the SystemCmd variable is created on the client side in the JavaScript function updateOptions(), which in turn uses the values from the input fields pingCNT and destIP. A web proxy can then be used to bypass the local checks that are normally done, and then /cmdRet_check.htm is used to asynchronously return the response from the request. The command is then executed with no further checks performed on the server side.”
Eugene Dokukin, aka “MustLive,” a member of the Ukrainian Cyber Forces activist group, has also disclosed the details of some cross-site scripting (XSS) and cross-site request forgery (CSRF) vulnerabilities affecting several Asus RT-N10 models.Vulnerabilities in Asus routers

Dokukin claimed that the Ukrainian Cyber Forces, who are fighting a cyberwar against the Russian government and separatists in Eastern Ukraine, have exploited these vulnerabilities to take control of devices belonging to their targets.
Researcher Pedro Ribeiro informed Asus of two vulnerabilities via Beyond Security’s SecuriTeam Secure Disclosure program, including access bypass and configuration manipulation issues.
According to Ribeiro, the AsusWRT operating system running on mid-range and high-end Asus routers is affected by vulnerabilities that allow an unauthenticated attacker with access to the local network to remotely execute arbitrary code.
One of the flaws found by the expert allows an attacker to reset the device’s administrator password by sending a specially crafted request. Once the password has been reset, the attacker can log into the web interface with the new password, enable SSH, and then access the device via SSH. Ribeiro also noted that arbitrary command execution is also possible without resetting the admin password.
Finally, Víctor Calvo of Spain-based security firm S2 Grupo, discovered that an attacker can change the credentials of any user, including the device’s administrator, by sending a specially crafted request to the password reset form.
Calvo also found that the Asus AiCloud service, which allows users to remotely access their home network, is affected by XML External Entity (XXE) vulnerabilities that can be exploited to access system files, including ones that store user credentials.
The researchers who identified these vulnerabilities informed Asus of their findings – except for Dokukin, who typically doesn’t inform vendors of the flaws exploited by his group. The company in most cases developed patches within a few weeks after being notified. Information on the latest firmware patches is available on Asus’ Product Security Advisory page.
New AMD Processors to Include Protections for Spectre-like Exploits
31.1.2018 securityweek Exploit
AMD’s new Zen 2 and future processors will include protections against Spectre and other similar exploits, the tech giant revealed on Tuesday as it announced its earnings for 2017.
AMD CEO Lisa Su reiterated that the company’s CPUs are not vulnerable to Meltdown attacks and one variant of the Spectre attack is difficult to carry out against its products.AMD processors will include Spectre protections
“For Spectre Variant 1, we continue actively working with our ecosystem partners on mitigations, including operating system patches that have begun to roll out. We continue to believe that Variant 2 of Spectre is difficult to exploit on AMD processors, however we are deploying CPU microcode patches – in combination with OS updates – to provide additional mitigation steps,” Su explained.
The CEO highlighted that in the long-term the company plans on including protections for Specter-like exploits into all future processor cores. These protections have already been implemented into the design of recently unveiled Zen 2 CPUs, which are expected to become available next year.
AMD reported revenue of $5.33 billion for 2017, which it says represents a 25 percent increase compared to the previous year. However, the company warned that the Spectre and Meltdown exploits could have a negative impact on the company’s revenue, including as a result of lawsuits, which have already been filed against the organization.
“Actual or perceived security vulnerabilities of AMD products may subject AMD to adverse publicity, damage to its brand and reputation, and could materially harm AMD’s business or financial results,” the company stated.
Intel also informed customers that it’s working on CPUs that will include built-in protections against Meltdown and Spectre attacks.
In the meantime, existing software and microcode patches have caused problems for many users, which has led to vendors halting updates and disabling mitigations until issues are resolved.
700,000 Bad Android Apps Removed From Google Play in 2017
31.1.2018 securityweek Android
Google took down over 700,000 Android applications from the official software marketplace last year, 70% more than were removed from the store in 2016.
Additonally, Google improved its ability to identify bad applications earlier, and 99% of apps featuring abusive contents were rejected before reaching users, the company claims.
According to Andrew Ahn, Product Manager, Google Play, this was possible because of new machine learning models and techniques that power Google’s abuse detection abilities (including impersonation, inappropriate content, or malware).
Furthermore, the company focused on identifying repeat offenders and abusive developer networks, which resulted in taking down 100,000 bad developers in 2017. It also “made it more difficult for bad actors to create new accounts and attempt to publish yet another set of bad apps,” Ahn says.
Last year, Google took action against copycat apps, or those programs attempting to deceive users by posing as popular programs. Because famous programs get massive search traffic for particular keywords, the bad actors attempt to take advantage of this by publishing impersonating apps to Google Play Store.
Some of the methods employed include the use of confusable Unicode characters or the hiding of impersonating app icons in a different locale. Google says it took down over a quarter of a million such applications last year.
Applications that contain or promote inappropriate content (pornography, extreme violence, hate, and illegal activities) aren’t accepted in the app store either, and Google removed tens of thousands of such programs from the Android marketplace last year.
Potentially Harmful Applications (PHAs) – malware that performs SMS fraud, acts as Trojans, or phishes user's information – can harm people or their devices despite going to lengths to appear as legitimate programs. According to Ahn, Google Play Protect helped the Internet giant reduce the annual PHA installs rates on Google Play by 50% last year.
“Despite the new and enhanced detection capabilities that led to a record-high takedowns of bad apps and malicious developers, we know a few still manage to evade and trick our layers of defense. We take these extremely seriously, and will continue to innovate our capabilities to better detect and protect against abusive apps and the malicious actors behind them,” Ahn says.
Malware Exploiting Spectre, Meltdown Flaws Emerges
31.1.2018 securityweek Virus
Researchers have discovered more than 130 malware samples designed to exploit the recently disclosed Spectre and Meltdown CPU vulnerabilities. While a majority of the samples appear to be in the testing phase, we could soon start seeing attacks.
The Meltdown and Spectre attack methods allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive data. Shortly after Spectre and Meltdown were disclosed on January 3, experts warned that we could soon see remote attacks, especially since a JavaScript-based proof-of-concept (PoC) exploit for Spectre had been made available.
On January 17, antivirus testing firm AV-TEST reported that it had seen 77 malware samples apparently related to the CPU vulnerabilities, and the number had increased to 119 by January 23.
On Wednesday, AV-TEST told SecurityWeek that it has obtained 139 samples from various sources, including researchers, testers and antivirus companies.

“Most appear to be recompiled/extended versions of the PoCs - interestingly, for various platforms like Windows, Linux and MacOS,” Andreas Marx, CEO of AV-TEST, told SecurityWeek. “We also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.”
Fortinet, which also analyzed many of the samples, confirmed that a majority of them were based on available PoC code.
Marx believes different groups are working on the PoC exploits to determine if they can be used for some purpose. “Most likely, malicious purposes at some point,” he said.
The expert believes the current malware samples are still in the “research phase” and attackers are most likely looking for ways to extract information from computers, particularly from web browsers. He would not be surprised if we started seeing targeted and even widespread attacks in the future.
Processor and operating system vendors have been working on microcode and software mitigations for the Meltdown and Spectre attacks, but the patches have often caused problems, leading to companies halting updates and disabling mitigations until instability issues are resolved.
In addition to installing operating system and BIOS updates, Marx has two other recommendations that should reduce the chances of a successful attack: switching off the PC when it’s not needed for more than an hour, and closing the web browser during work breaks. “This should decrease your attack surface a lot and also save quite some energy,” Marx said.
Remotely Exploitable Vulnerability Could Impact 300,000 Oracle PoS Systems
31.1.2018 securityweek Vulnerebility
A vulnerability Oracle addressed in the MICROS Point-of-Sale (PoS) terminals with the January 2018 Critical Patch Update could impact more than 300,000 payment systems worldwide.
Tracked as CVE-2018-2636 and featuring a CVSS v3 score of 8.1, the vulnerability was discovered in September 2017 as a directory traversal vulnerability. Hackers looking to abuse it could read any file by sending a packet to a particular web service of a PoS terminal.
The security bug can be exploited remotely without authentication to read files from the impacted PoS systems. Furthermore, attackers could abuse it to access configuration files that store sensitive information including passwords.
Attackers looking to exploit the flaw could gain full access to the operating system for espionage, sabotage or fraud operations, ERPScan, a company that specializes in securing Oracle and SAP products, reveals. By exploiting the flaw, cybercriminals could, for example, pilfer credit card numbers, the company says.
Because of the wide use of MICROS PoS terminals, the impact of such a security issue could be dire. At the moment, Oracle’s MICROS has more than 330,000 cash registers worldwide. The terminals can be found in over 200,000 food and beverage outlets and more than 30,000 hotels across 180 countries, ERPScan points out.
The vulnerability was discovered as a directory traversal in Oracle MICROS EGateway Application Service. With access to the URL, an attacker could exfiltrate files from the MICROS workstations, including services logs, and could also read files that contain usernames and encrypted passwords to gain full access to the database with all business data.
“After sending a malicious request, for example, the request to read SeviceHost.xml file, the vulnerable MICROS server sends back a special response with the SeviceHost.xml contents,” the security firm explains.
The vulnerability was addressed in Oracle’s January 2018 CPU, but the patch was unlikely to have been already deployed to all of the vulnerable MICROS PoS systems out there.
“POS systems directly process and transmit our payment orders, so it’s self-evident that they are extremely important and valuable. We use them on the daily and hope to be secure from thefts. As a user, I want to rest safe and to avoid any problem while making payments with my card. We worry for the security of our money, and it makes sense,” Alexander Polyakov, CTO of ERPScan, says.
Is ICEMAN behind the malware-based attack on Crystal Finance Millennium?
31.1.2018 securityaffairs Virus
Exclusive – The Iceman gang taking responsibility for infecting Crystal Finance Millennium, the journalist Marc Miller interviewd one of the members of the crew.
Iceman gang member confirms that they are behind the introduction and spreading of malware that infected the systems at Crystal Finance Millennium.
In Septemeber security experts at TrendMicro reported that the Ukraine based Account Firm, Crystal Finance Millennium (CFM), has been hacked and is found to be distributing malware.
The incident caused the firm to take down its website to stop spreading the threat.

Crystal Finance Millennium attack (Source Trend Micro)
Marc Miller had a chance to speak to one of the gang members on XMMP and he confirmed that the Iceman group is behind this attack. They started with a simple web attack (SQLI which lead to web shell upload, no privilege escalation was needed) in order to gain access to the web servers of the company.
He confirmed that the math was simple, the Ukrainian company had many clients in the financial and medical sector which facilitated the propagation of their malware. From the archived web page, it becomes apparent they provide accounting software, personalization of medical records, blood service and “full automation of the doctor’s office” – contrary to what their company name suggests, it appears they are (mostly) focused on medical software.
The group sent phishing emails to various targets based in Ukraine and former Soviet countries. The emails contained a ZIP file that, in turn, contained a JavaScript file. When users unzipped the archive and ran the JS file, the script would download a file named load.exe from the CFM’s web server.
The loader (load.exe file) will, later on, download a Purge ransomware that was modified for that operation by the Iceman group. According to the gang, each target was treated individually to maximize profit. Sometimes they would run a ransomware program and sometimes they would run a banking Trojan. “When you sophisticate your attack, you can drain the sharks” – he said.
An inclusive interview is in the making to unveil the course of this attack. It will be released in the upcoming weeks.
Marc Miller is a web journalist, focused on cybercrime.
He started a blog called: THE PURPLE HAT – Cyber Gangs NAKED, dedicated to exposing the methods and works of cybercrime gangs such as “CARBANAK” or similar sophisticated syndicated Cybercrime organizations.
In the past. he worked as a web front-end programmer. Also, he is passionate about hardware, hacking, security and marketing.
Cybercriminals Stealing From Cybercriminals Ransomware Victims Left Stranded
31.1.2018 securityaffairs Ransomware
What do you get when you add Bitcoin, with a TOR network proxy and cybercriminals? Even more cybercrime!
Bitcoin is the preferred cryptocurrency for ransomware payments. Like most cryptocurrencies it is largely anonymous, allowing the ransoming cybercriminals to collect their money while staying safely in the shadows. Even though Bitcoin is the most popular cryptocurrency, the majority of victims do not have a ready cache of Bitcoin to pay ransom with so the cybercriminals came up with a process to facilitate these ransom payments.
Payment websites are hosted on the Tor network where victims login, purchase Bitcoin and deposit them into the wallet of the bad actors. Sounds convenient, unless there is another bad actor in the middle. To understand how that happens, we first need to explain the Tor network.
Tor is an acronym based on a software project called The Onion Router. It “[redirects] Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user’s location and usage…“, Tor (anonymity network), Wikipedia. In other words, you must use a Tor client to connect to the Tor network and in doing so, you participate as a relay in the network helping to provide anonymity for all other users.
There are many situations where this type of Internet anonymity would be useful: researching a company without alerting them to who is looking, researching a controversial topic without being identified, avoiding oppressive government restrictions or spying, and facilitating Bitcoin payments while hiding the location of the web server. The challenge for the ransomers is that victims are even less likely to be set up with a Tor client than they are to have Bitcoin! To solve this problem, there are individuals who run “Tor proxies.” These proxies are accessible with a regular browser on the Internet so no special software is required. For example, the hidden server on the Tor network might be addressed by hxxps://sketchwebsite.onion which requires a Tor browser to connect. However by entering hxxps://sketchwebsite.onion.to into a regular browser, a connection is made with a “regular server” on the Internet which redirects (proxies) the request to sketchwebsite.onion on your behalf. You can surf the Tor network, and make your Bitcoin payments with no special software required. By design, a proxy takes a connection from one party and passes it to another. This involves looking at the incoming request to understand where it needs to be forwarded. This also creates an opportunity for the proxy to make changes in between.
Proofpoint is the security vendor that identified cybercriminals taking advantage of Tor proxies to steal from victims and the ransoming cybercriminals. They discovered that when victims attempted to connect to the ransomers’ website through a Tor proxy, the criminals operating the proxy made changes to the stream. Instead of the Bitcoin being deposited to the intended ransomer’s digital wallets, the funds were redirected to the proxy operator’s wallet. While you won’t be sympathetic to the ransoming cybercriminals’ loss of revenue, the real problem is that without payment they won’t release the decryption key to the victim. The ransomware victim thought they were paying Bitcoin to the ransomer for the decryption key, but with the man-in-the-middle attack at the Tor proxy they paid for nothing.
Through some very detailed analysis documented here, Proofpoint estimates that approximately 2 BTC have been redirected (around $20,000 at the time they published their article.) It was a notice on the LockeR ransomware payment portal that alerted Proofpoint researchers that something was amiss in the cybercrime underworld:

“While this is not necessarily a bad thing, it does raise an interesting business problem for ransomware threat actors and practical issues for ransomware victims by further increasing the risk to victims who would resort to paying ransomware ransoms,” Proofpoint researchers said. “This kind of scheme also reflects the broader trend of threat actors of all stripes targeting cryptocurrency theft. Continued volatility in cryptocurrency markets and increasing interest in the Tor network will likely drive further potential abuses of Tor proxies, creating additional risks for new users.”
US Attorney General set up the Joint Criminal Opioid Darknet Enforcement team to fight online opioid trafficking
31.1.2018 securityaffairs CyberCrime
The US Attorney General announced the creation of the Joint Criminal Opioid Darknet Enforcement team to fight online opioid trafficking.
Tor network is still a privileged ecosystem for cyber criminals and pedos, law enforcement and intelligence agencies worldwide reserve a significative effort in fighting any illegal practice that leverages anonymizing networks.
The US Attorney General has set up a task force, dubbed Joint Criminal Opioid Darknet Enforcement (J-CODE), composed of federal agents and cyber experts to dismantle black marketplaces that offer for sale any kind of drug.
The Joint Criminal Opioid Darknet Enforcement team will be distributed in many cities across the US, the feds are tasked to infiltrate the black markets, identify the operators, and shut down them.
The darknet, and in particular black marketplaces, have a relevant aggregation role for the distribution of illegal opioids. Even if many sellers are overseas, the Joint Criminal Opioid Darknet Enforcement team will be focused on domestic operators.

During the official announcement of the task force, Attorney General Jeff explained the abuses of anonymizing networks, but he also highlighted that they can be used for good purposes, such as to avoid censorship. Sessions added that the hard work of law enforcement agencies allowed the infiltration of illegal rings.
“Criminals think that they are safe on the darknet, but they are in for a rude awakening,” Sessions said.
“We have already infiltrated their networks, and we are determined to bring them to justice. The J-CODE team will help us continue to shut down the online marketplaces that drug traffickers use and ultimately that will help us reduce addiction and overdoses across the nation.”
Drugs represent a serious threat to the state, it has been estimated that opioids kill more than 90 Americans every day through overdoses, and this is the tip of the iceberg of a phenomenon that has many other dramatic consequences.
The creation of the Joint Criminal Opioid Darknet Enforcement is an important investment in fighting online opioid trafficking in term or resources and cyber capabilities.
“J-CODE will more than double the FBI’s investment in fighting online opioid trafficking. The FBI is dedicating dozens more Special Agents, Intelligence Analysts, and professional staff to J-CODE so that they can focus on this one issue of online opioid trafficking.” concluded the press release published by the DoJ.
Once again, Oracle MICROS PoS have been breached
31.1.2018 securityweek Vulnerebility
Security experts from ERPScan discovered a new flaw in Oracle MICROS PoS terminals that could be exploited by an attacker to read sensitive data from devices.
Security experts from ERPScan discovered a new directory traversal vulnerability in Oracle MICROS Point-of-Sale terminals, tracked as CVE-2018-2636, which could be exploited by an attacker to read sensitive data from devices without authentication from a vulnerable workstation.
“CVE-2018-2636 states for a directory traversal vulnerability in Oracle MICROS EGateway Application Service. In case an insider has access to the vulnerable URL, he or she can pilfer numerous files from the MICROS workstation including services logs and read files like SimphonyInstall.xml or Dbconfix.xml that contain usernames and encrypted passwords to connect to DB, get information about ServiceHost, etc.” reads the analysis published by ERPScan.
“So, the attacker can snatch DB usernames and password hashes, brute them and gain full access to the DB with all business data. There are several ways of its exploitation, leading to the whole MICROS system compromise.”
Oracle’s MICROS has more than 330,000 cash registers worldwide, it is widely adopted in food and beverage outlets (200,000+) and hotels (30,000).
The researchers explained that it could be easy for a local attacker to access a MICRO POS URL, for example, he can find a digital scales or other devices that use RJ45 in the outlet and connect it to Raspberry PI, then scan the internal network. Another option is to locate such kind of devices exposed on the Internet, at the time of writing, there are 139 MICROS POS systems exposed online, most of them located in US and Canada.
Oracle MICROS POS
This is not the first time when MICROS security is touched. In 2016, there was an incident where hackers attacked MICROS through the Customer Support Portal.
The vulnerability received the 8.1 CVSS v3 score.
“If you want to secure your system from cyberattacks, you have to persistently implement all security patches provided by your vendor. In our case, refer to Oracle CPU January 2018.” concluded the post.
This isn’t the first time that we approach the security of Oracle MICROS PoS systems, on August 2016, the systems of the Oracle MICROS payment terminals division were infected with a malware.







