
Necurs botnet involved in massive ransomware campaigns at the end of 2017
3.1.2017 securityaffairs Ransomware
The Necurs botnet made the headlines at year-end sending out tens of millions of spam emails daily as part of massive ransomware campaigns.
Necurs was not active for a long period at the beginning of 2017 and resumed it activity in April.
The Necurs botnet was used in the past months to push many other malware, including Locky, Jaff, GlobeImposter, Dridex , Scarab and the Trickbot.
According to data collected by the experts at AppRiver, between December 19 and December 29, 2017, the Necurs botnet was involved in the distribution of ransomware. Crooks use typical holiday-themed scam emails to distribute both Locky and GlobeImposter, malicious messages used .vbs (Visual Basic Script) or .js (JavaScript) files inside a .7z archive.

Starting on Dec. 19, the Necurs botnet was observed sending tens of millions of spam emails daily to distribute ransomware, the peak was reached on December 20th with over 47 million email (peaking at 5.7 million per hour).
“On Dec. 19, AppRiver’s filters stopped 45,976,814 malicious emails sent by the Necurs botnet. Maximum traffic for it was a just more than 4.6 million emails per hour. These were all .7z that contained malicious .vbs files leading to an infection.” reads the analysis published by AppRiver.

Experts noticed that during the first day operators only used vbs files inside the .7z archive, while the second day they started using also .js files.
“On Dec. 21 and 22, the traffic switched back over to the .js files and began to taper off. We saw 36,290,981 and 29,602,971 messages blocked respectively, for those two days, before the botnet went quiet from Dec. 23-25. Today (Dec. 26), Necurs re-awoke from its slumber for a couple hours then went quiet again.” continues the analysis.
“Hard to say why, however, I would hypothesize the operators may have been testing or monitoring the rate of infections and realized many workers are on vacation. As of the time this blog was authored we’ve captured the below statistics for today”
The activity of the botnet increased again on Dec. 28-29, on the first day it peaked 6.5 million messages early morning, on the next day, the Necurs botnet sent out nearly 59 million ransomware messages.
Critical Flaw Reported In phpMyAdmin Lets Attackers Damage Databases
3.1.2017 thehackernews Vulnerebility
A critical security vulnerability has been reported in phpMyAdmin—one of the most popular applications for managing the MySQL database—which could allow remote attackers to perform dangerous database operations just by tricking administrators into clicking a link.
Discovered by an Indian security researcher, Ashutosh Barot, the vulnerability is a cross-site request forgery (CSRF) attack and affects phpMyAdmin versions 4.7.x (prior to 4.7.7).
Cross-site request forgery vulnerability, also known as XSRF, is an attack wherein an attacker tricks an authenticated user into executing an unwanted action.
According to an advisory released by phpMyAdmin, "by deceiving a user to click on a crafted URL, it is possible to perform harmful database operations such as deleting records, dropping/truncating tables, etc."
phpMyAdmin is a free and open source administration tool for MySQL and MariaDB and is widely used to manage the database for websites created with WordPress, Joomla, and many other content management platforms.
Moreover, a lot of hosting providers use phpMyAdmin to offer their customers a convenient way to organize their databases.
Barot has also released a video, as shown above, demonstrating how a remote attacker can make database admins unknowingly delete (DROP) an entire table from the database just by tricking them into clicking a specially crafted link.
"A feature of phpMyAdmin was using a GET request and after that POST request for Database operations such as DROP TABLE table_name; GET requests must be protected against CSRF attacks. In this case, POST requests were used which were sent through URL (for bookmarking purpose may be); it was possible for an attacker to trick a database admin into clicking a button and perform a drop table database query of the attacker’s choice." Barot explains in a blog post.
However, performing this attack is not simple as it may sound. To prepare a CSRF attack URL, the attacker should be aware of the name of targeted database and table.
"If a user executes a query on the database by clicking insert, DROP, etc. buttons, the URL will contain database name and table name," Barot says. "This vulnerability can result in the disclosure of sensitive information as the URL is stored at various places such as browser history, SIEM logs, Firewall Logs, ISP Logs, etc."
Barot reported the vulnerability to phpMyAdmin developers, who confirmed his finding and released phpMyAdmin 4.7.7 to address this issue. So administrators are highly recommended to update their installations as soon as possible.
15-Year-Old Apple macOS 0-Day Kernel Flaw Disclosed, Allows Root Access
3.1.2017 thehackernews Apple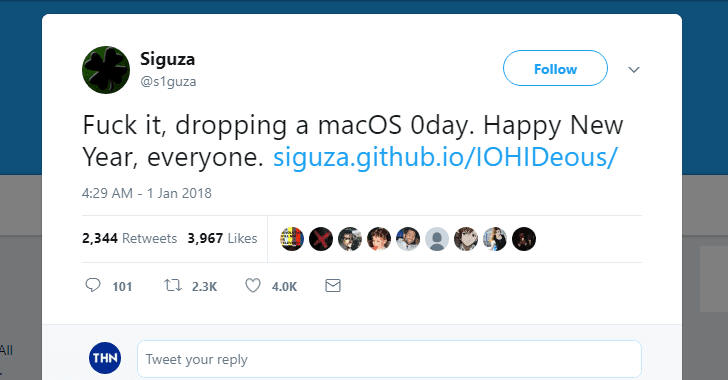
A security researcher on New Year's eve made public the details of an unpatched security vulnerability in Apple's macOS operating system that can be exploited to take complete control of a system.
On the first day of 2018, a researcher using the online moniker Siguza released the details of the unpatched zero-day macOS vulnerability, which he suggests is at least 15 years old, and proof-of-concept (PoC) exploit code on GitHub.
The bug is a serious local privilege escalation (LPE) vulnerability that could enable an unprivileged user (attacker) to gain root access on the targeted system and execute malicious code. Malware designed to exploit this flaw could fully install itself deep within the system.
From looking at the source, Siguza believes this vulnerability has been around since at least 2002, but some clues suggest the flaw could actually be ten years older than that. "One tiny, ugly bug. Fifteen years. Full system compromise," he wrote.
This local privilege escalation flaw resides in IOHIDFamily, an extension of the macOS kernel which has been designed for human interface devices (HID), like a touchscreen or buttons, allowing an attacker to install a root shell or execute arbitrary code on the system.
"IOHIDFamily has been notorious in the past for the many race conditions it contained, which ultimately lead to large parts of it being rewritten to make use of command gates, as well as large parts being locked down by means of entitlements," the researcher explains.
"I was originally looking through its source in the hope of finding a low-hanging fruit that would let me compromise an iOS kernel, but what I didn’t know it then is that some parts of IOHIDFamily exist only on macOS - specifically IOHIDSystem, which contains the vulnerability."
The exploit created by Siguza, which he dubbed IOHIDeous, affects all versions of macOS and enables arbitrary read/write bug in the kernel.
Besides this, IOHIDeous also disables the System Integrity Protection (SIP) and Apple Mobile File Integrity (AMFI) security features that offer protection against malware.
The PoC code made available by Siguza has for some reason stopped working on macOS High Sierra 10.13.2 and works on macOS High Sierra 10.13.1 and earlier, but he believes the exploit code can be tweaked to work on the latest version as well.
However, the researcher pointed out that for his exploit to work, it needs to force a log out of the logged-in user, but this can be done by making the exploit work when the targeted machine is manually shut down or rebooted.
Since the vulnerability only affects macOS and is not remotely exploitable, the researcher decided to dumped his findings online instead of reporting it to Apple. For those unaware, Apple's bug bounty program does not cover macOS bugs.
For in-depth technical details about the vulnerability, you can head on to researcher's write-up on GitHub.
Flaw In Major Browsers Allows 3rd-Party Scripts to Steal Your Saved Passwords
3.1.2017 thehackernews Vulnerebility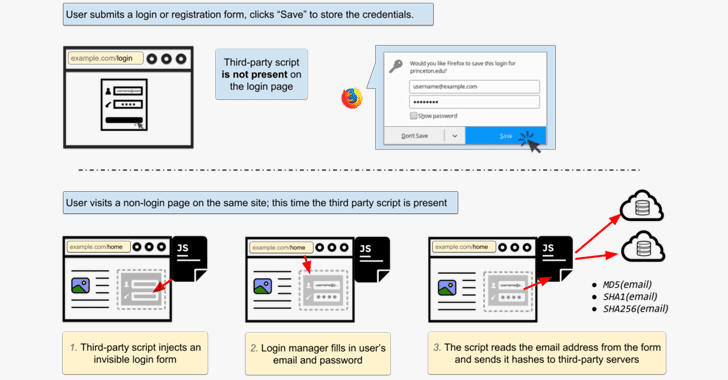
Security researchers have uncovered how marketing companies have started exploiting an 11-year-old bug in browsers' built-in password managers, which allow them to secretly steal your email address for targeted advertising across different browsers and devices.
The major concern is that the same loophole could allow malicious actors to steal your saved usernames and passwords from browsers without requiring your interaction.
Every modern browser—Google Chrome, Mozilla Firefox, Opera or Microsoft Edge—today comes with a built-in easy-to-use password manager tool that allows you to save your login information for automatic form-filling.
These browser-based password managers are designed for convenience, as they automatically detect login form on a webpage and fill-in the saved credentials accordingly.
However, a team of researchers from Princeton's Center for Information Technology Policy has discovered that at least two marketing companies, AdThink and OnAudience, are actively exploiting such built-in password managers to track visitors of around 1,110 of the Alexa top 1 million sites across the Internet.
Third-party tracking scripts found by researchers on these websites inject invisible login forms in the background of the webpage, tricking browser-based password managers into auto-filling the form using the saved user's information.
"Login form auto filling in general doesn't require user interaction; all of the major browsers will autofill the username (often an email address) immediately, regardless of the visibility of the form," the researchers say.
"Chrome doesn't autofill the password field until the user clicks or touches anywhere on the page. Other browsers we tested don't require user interaction to autofill password fields."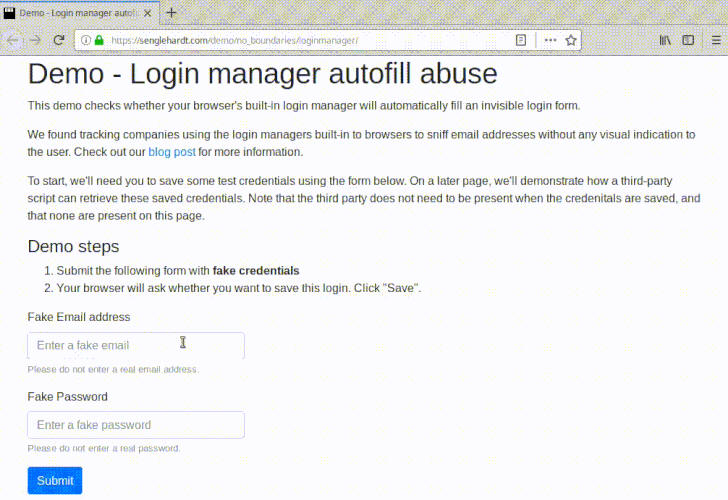
Since these scripts are primarily designed for user-tracking, they detect the username and send it to third-party servers after hashing with MD5, SHA1 and SHA256 algorithms, which could then be used as a persistent ID for a specific user to track him/her from page to page.
"Email addresses are unique and persistent, and thus the hash of an email address is an excellent tracking identifier," the researchers said. "A user's email address will almost never change—clearing cookies, using private browsing mode, or switching devices won't prevent tracking."
Although the researchers have spotted marketing firms scooping up your usernames using such tracking scripts, there is no technical measure to prevent these scripts from collecting your passwords the same way.
However, most third-party password managers, like LastPass and 1Password, are not prone to this attack, since they avoid auto-filling invisible forms and require user interaction as well.
Researchers have also created a demo page, where you can test if your browser's password manager also leaks your username and password to invisible forms.
The simplest way to prevent such attacks is to disable the autofill function on your browser.
Many GPS Tracking Services Expose User Location, Other Data
3.1.2017 securityweek Privacy
Researchers discovered that many online services designed for managing location tracking devices are affected by vulnerabilities that expose potentially sensitive information.
Fitness, child, pet and vehicle trackers, and other devices that include GPS and GSM tracking capabilities are typically managed via specialized online services.
Security experts Vangelis Stykas and Michael Gruhn found that over 100 such services have flaws that can be exploited by malicious actors to gain access to device and personal data. The security holes, dubbed Trackmageddon, can expose information such as current location, location history, device model and type, serial number, and phone number.
Some services used by devices that have photo and audio recording capabilities also expose images and audio files. In some cases, it’s also possible to send commands to devices in order to activate or deactivate certain features, such as geofence alerts.
Attackers can gain access to information by exploiting default credentials (e.g. 123456), and insecure direct object reference (IDOR) flaws, which allow an authenticated user to access other users’ accounts simply by changing the value of a parameter in the URL. The services also expose information through directory listings, log files, source code, WSDL files, and publicly exposed API endpoints that allow unauthenticated access.
Stykas and Gruhn have notified a vast majority of the affected vendors in November and December. Nine services have confirmed patching the flaws or promised to implement fixes soon, and over a dozen websites appear to have addressed the vulnerabilities without informing the researchers. However, the rest of the tracking services remain vulnerable.
There are roughly 100 impacted domains, but some of them appear to be operated by the same company. Researchers have identified 36 unique IPs hosting these domains and 41 databases that they share. They estimate that these services expose data associated with over 6.3 million devices and more than 360 device models.
The vulnerable software appears to come from China-based ThinkRace, but in many cases the company does not have control over the servers hosting the tracking services.
Gruhn and Stykas pointed out that vulnerabilities in ThinkRace products – possibly including some of the issues disclosed now – were first discovered in 2015 by a New Zealand-based expert while analyzing car tracking and immobilisation devices that relied on ThinkRace software.
Users of the online tracking services that remain vulnerable have been advised to change their password and remove any potentially sensitive information stored in their account. However, these are only partial solutions to the problem and researchers have advised people to simply stop using affected devices until patches are rolled out.
Critical Vulnerability Patched in phpMyAdmin
3.1.2017 securityweek Vulnerebility
An update released just before the holidays by the developers of phpMyAdmin patches a serious vulnerability that can be exploited to perform harmful database operations by getting targeted administrators to click on specially crafted links.
phpMyAdmin is a free and open source tool designed for managing MySQL databases over the Internet. With more than 200,000 downloads every month, phpMyAdmin is one of the top MySQL database administration tools.
India-based researcher Ashutosh Barot discovered that phpMyAdmin is affected by a cross-site request forgery (CSRF) flaw that can be exploited by an attacker to drop tables, delete records, and perform other database operations.
For the attack to work, an authenticated admin needs to click on a specially crafted URL. However, Barot noted that the attack works as long as the user is logged in to the cPanel web hosting administration interface, even if phpMyAdmin has been closed after use.
These types of attacks are possible due to the fact that vulnerable versions of phpMyAdmin use GET requests for database operations, but fail to provide CSRF protection.
The researcher also discovered that the URLs associated with database operations performed via phpMyAdmin are stored in the web browser history, which can pose security risks.
“The URL will contain database name and table name as a GET request was used to perform DB operations,” Barot said in a blog post published on Friday. “URLs are stored at various places such as browser history, SIEM logs, firewall logs, ISP logs, etc. This URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!). Wherever the URL is being saved, an adversary can gain some information about your database.”
phpMyAdmin developers fixed the CSRF vulnerability found by Barot with the release of version 4.7.7. All prior 4.7.x versions are impacted by the security hole, which phpMyAdmin has classified as “critical.” Users have been advised to update their installations or apply the available patch.
Necurs Botnet Fuels Massive Year-End Ransomware Attacks
3.1.2017 securityweek Ransomware
The Necurs botnet started 2017 with a four-month vacation, but ended the year sending tens of millions of spam emails daily as part of massive ransomware distribution campaigns.
Considered the largest spam botnet at the moment, Necurs was the main driver behind the ascension of the Locky ransomware (which in turn is associated with the Dridex banking Trojan) in 2016. As Necurs took a long vacation in the beginning of 2017, Locky was silent as well, but both resumed activity in April.
Over the course of 2017, however, the botnet was involved in the distribution of the Jaff, GlobeImposter, and Scarab ransomware families, as well as in 'pump-and-dump' schemes.
Over a 10-day period between December 19 and December 29, 2017, Necurs was once again involved in the distribution of ransomware, in addition to sending typical holiday-themed scam emails, data collected by AppRiver reveals.
The messages, AppRiver says, were distributing the Locky and GlobeImposter ransomware families and revealed the attackers’ preference to use malicious .vbs (Visual Basic Script) or .js (JavaScript) files located inside a .7z archive.
Consisting of between 5 and 6 million infected hosts and keeping around 1 or 2 million of them active at any given time, Necurs provides operators with remote access to the infected machines and can be used for various malicious activities, including malware downloads.
Starting on Dec. 19, the botnet was observed sending tens of millions of spam emails daily to distribute ransomware. It started at nearly 46 million emails on the first day (peaking at over 4.6 million messages per hour) and continued with over 47 million messages on Dec. 20 (peaking at 5.7 million per hour).
While the initial spam featured mainly .vbs files inside the .7z archive, .js files started appearing as well on the second day, and the traffic switched to .js files on Dec. 21-22, when it also started to taper off, at 36 million and 29 million messages per day, respectively. The botnet remained quiet from Dec. 23-25 and recommenced activity for only a couple of hours on Dec. 26.
“Hard to say why, however, I would hypothesize the operators may have been testing or monitoring the rate of infections and realized many workers are on vacation,” AppRiver’s David Pickett notes.
On Dec. 28-29, however, the botnet was highly active. It peaked at 6.5 million messages early morning on Dec. 28, but wasn’t active for long. On the next day, Necurs was observed sending nearly 59 million ransomware messages.
The malicious emails, the security researchers reveal, were masquerading as purchase orders and voicemails, but also claimed to contain images of interest to the intended victims.
Internet-connected Sonos Speakers Leak User Information
3.1.2017 securityweek Vulnerebility
A vulnerability found in Internet-connected Sonos Play:1 speakers can be abused to access information on users, Trend Micro has discovered.
By exploiting the issue, an attacker could learn a user’s musical preferences, get hold of their email address, and could even learn where the user lives and whether they are at home. Additionally, an attacker could play a recorded message on the device and trick the target into downloading malware.
While analyzing the device, Trend Micro’s researchers discovered the device had only three ports open and that Sonos applications on it were pointed to a specific website, while most of the communications were performed over port TCP/1400.
Looking at the specific URI path of /status on the device, the researchers also noticed that many of its subpages were shown via a simple website. Thus, no authentication was required to access information about the tracks being played or the music libraries the device knows about.
Furthermore, the website revealed personal information such as emails associated with audio streaming services and exposed various debug functions, including “the ability to traceroute, ping, and even make an mDNS announcement via a simple website,” the researchers say. The status page can reveal other information as well.
“Let’s say an attacker knows the target uses a Sonos device. The attacker can then take the information collected here to tailor better attacks against the target. This could include mobile devices, printers, and even types of computers on the networks,” Trend Micro notes in a technical analysis (PDF).
The security researchers also discovered a series of plausible attack scenarios that could be used not only against home users, but also to target enterprise networks.
By learning the user’s musical preferences, an attacker could craft phishing emails and deliver them to the target. In a workplace environment, such an attack could be used to discover other IoT devices connected to the same network and find vulnerabilities on them to further compromise the network.
Using a website that compounds multiple sources of Wi-Fi geolocation an attacker could also find where the user lives (the researchers determined the device location by looking at the wireless access points (WAPs) the device tried to access during installation) and whether they are at home by monitoring when the speaker is activated and deactivated.
“This hybrid attack involving cyber and physical elements presents new dangers that home and enterprise users should be aware of. Devices leaking presence data not only make users easier to predict — they can also put the user at physical risk,” the researchers say.
Leveraging information discovered on the aforementioned status page, including model numbers and serial numbers, an attacker could disrupt the device and even play a crafted status message containing misleading information.
The attacker could also send tailored emails to the user (to the addresses tied to accounts on music streaming applications) and trick them into downloading malware masquerading as a software update. Using other discoverable information on the target, the attacker could add personalized information to the message to make it even more convincing.
With the help of search service Shodan, the security researchers were able to find roughly 5,000 Sonos devices exposed to the Internet. The manufacturer was informed on the findings and has already released and updated to address the discovered bugs, but some of the issues continue to impact users, Trend Micro says.
“The problem of unsecured internet-connected devices is not limited to home users but also extends to workplace environments when seemingly safe IoT devices are introduced into the company network, as was shown in the attack scenarios. Whether these devices are installed to improve productivity or are simply brought to work by employees, the risk of having an exposed and unsecured device should not be taken lightly,” Trend Micro concludes.
Former NSA hacker reversed Kaspersky Lab antivirus to compose signatures capable of detecting classified documents
2.1.2017 securityaffairs BigBrothers
Former NSA hacker, demonstrated how to subvert the Kaspersky Lab antivirus and turn it into a powerful search tool for classified documents.
The Kaspersky case demonstrated that security software can be exploited by intelligence agencies as a powerful spy tool.
Patrick Wardle, chief research officer at Digita Security and former NSA hacker, demonstrated it by subverting the Kaspersky Lab antivirus and turning it into a powerful search tool for classified documents.
“In the battle against malicious code, antivirus products are a staple,” Patrick Wardle told the New York Times. “Ironically, though, these products share many characteristics with the advanced cyberespionage collection implants they seek to detect.”
“I wanted to know if this was a feasible attack mechanism,” Mr. Wardle added. “I didn’t want to get into the complex accusations. But from a technical point of view, if an antivirus maker wanted to, was coerced to, or was hacked or somehow subverted, could it create a signature to flag classified documents?”
In December, US President Donald Trump signed a bill that bans the use of Kaspersky Lab products and services in federal agencies.
According to a draft of a top-secret report leaked by Edward J. Snowden, the NSA at least since 2008 was targeting antivirus software (i.e. Checkpoint and Avast) to collect sensitive information stored in the target machines.
Mr. Wardle conducted a reverse-engineering of Kaspersky Lab antivirus software to explore the possibility to abuse it for intelligence purposes. The expert’s goal was to compose a signature that is able to detect classified documents.
Mr. Wardle discovered that the code incredibly complex, unlike traditional antivirus software, Kaspersky’s malware signatures are easily updated. This feature can be tweaked to automatically scan the victim’s machine and steal classified documents.
“Modern anti-virus products are incredibly complex pieces of software and Kaspersky is likely one of the most complex. Thus, merely gaining a reasonable understanding of its signatures and scanning logic is a challenging task.” wrote Wardle.
“Though the installer ships with built-in signatures, as is the case with any anti-virus program, Kaspersky’s anti-virus engine regularly checks for, and automatically installs any new signatures” “When new signatures are available, they are downloaded by the kav daemon from Kaspersky’s update servers”
Wardle found antivirus scanning could be the used for cyberespionage activities.
The expert pointed out that officials routinely classify top secret documents with the marking “TS/SCI,” (“Top Secret/Sensitive Compartmented Information),” then he added a rule to Kaspersky’s antivirus program to flag any documents that contained the “TS/SCI” marker.
To test the new rule, the researcher edited a document on his computer containing text from the Winnie the Pooh children’s book series and added “TS/SC” marker.

As soon as the Winnie the Pooh document was saved to his machine, the Kaspersky’s antivirus software flagged and quarantined the document.
The successive phase of Wardle’s test was on discovering how flagged documents are managed, but it normal that an antivirus software send data back to the company for further analysis.
Kaspersky Lab explained that Wardle’s research is not corrected because the company is not able to deliver a specific signature or update to only one user in a stealthy way.
“It is impossible for Kaspersky Lab to deliver a specific signature or update to only one user in a secret, targeted way because all signatures are always openly available to all our users; and updates are digitally signed, further making it impossible to fake an update,” Kaspersky said in a statement.
Anyway, Wardle’s research demonstrated that hacking vendor’s platforms it is possible to use the antivirus as a search tool.
“However, a malicious or willing insider within any anti-virus company, who could tactically deployed such a signature, would likely remain undetected. And of course, in a hypothetical scenario; any anti-virus company that is coerced to, or is willing to work with a larger entity (such as a governemnt) would equally be able to stealthily leverage their product to detect and exfilitrate any files of interest.” concluded the expert.
“Sometimes the line between what is good and evil, comes down to a signal signature… “
Iran ‘s Government is reportedly blocking the Internet to calm down protests
2.1.2017 securityaffairs BigBrothers
The Iran Government is also trying to isolate the protests by blocking internet on mobile networks, authorities are blocking Instagram and messaging services like Telegram.
At least 12 people dead in the biggest challenge to the Government of the Tehran regime since mass demonstrations in 2009. The Iranian President Hassan Rouhani tried to downplay the dangerous situation, while violent protests mount across the country.
The Government is also trying to isolate the protests by blocking internet on mobile networks, multiple reports confirm the authorities are blocking social media services like Instagram and messaging services like Telegram since December 30.
“It’s a busy weekend for oppressive governments trying to suppress digital communication. Iran has blocked mobile access to at least Telegram and Instagram as it tries to thwart protests that started over economic concerns (particularly inflation), but have extended into broader resistance to the government and clerical rule.” reported the website engadget.com.
“Officials claim the censorship is meant to “maintain peace,” but the argument doesn’t hold water. Telegram founder Pavel Durov noted that his company refused to shut down “peacefully protesting channels,” and Instagram is primarily being used to document protests — Iran clearly doesn’t want to reveal the extent of the demonstrations.”
Pavel Durov
✔
@durov
Iranian authorities are blocking access to Telegram for the majority of Iranians after our public refusal to shut down https://t.me/sedaiemardom and other peacefully protesting channels.
1:17 PM - Dec 31, 2017 · Dubai, United Arab Emirates
1,058 1,058 Replies 2,944 2,944 Retweets 5,358 5,358 likes
Twitter Ads info and privacy
The Government fears that technology could amplify the protests like happened during the Arab Spring.
“The authorities appeared to respond by cutting internet access to mobile phones, with the main networks interrupted at least in Tehran shortly before midnight” AFP reporters said.
“Several Iranian news agencies warned Telegram, the most popular social media service in the country, might soon be shut down after communications minister Mohammad-Javad Azari Jahromi accused one popular channel, Amadnews, of encouraging an “armed uprising”.”
1 Jan
Kavé Salamatian
@kavesalamatian
@bgpmon @InternetIntel Changes in Iran BGP connectivity happening right now. Seems that the full internet is getting disconnected

@InternetIntel
Large routing outage in Iran about 2hrs ago. pic.twitter.com/382BYEIscF
4:35 PM - Jan 1, 2018
View image on Twitter
5 5 Replies 75 75 Retweets 51 51 likes
Twitter Ads info and privacy
Iran Freedom
@4FreedominIran
#Sanandaj, January 1 - Large crowd took to streets confronting oppressive security forces. Some were arrested. (via #MEK activists in #Iran) #FreeIran #Iranprotests #IranProtests #Iran #RegimeChange
4:55 PM - Jan 1, 2018
1 1 Reply 111 111 Retweets 82 82 likes
Twitter Ads info and privacy
“How nervous the government is about losing control over the population is proportional to various control tactics they implement over the Internet,” Mahsa Alimardani, who researches internet freedoms in Iran for Article 19, told Motherboard. “In the past few hours there are also some reports of home connections (up until today mostly left undisturbed) also facing some blocks to accessing foreign web content.”
At the time I’m writing it is not clear the real effect on the Internet access by the population, in the following graph it is visible the increase in the number of directly connecting users to the Tor network.

During Iran’s elections earlier this year, Rouhani promised to cut down on censorship, but evidently, it was only political propaganda.
Force 47 – The Vietnamese brigade tasked with fighting “wrongful views” spreading online
2.1.2017 securityaffairs APT
Force 47 is a brigade composed of 10,000 cyber warriors to fight online dissent in Vietnam, a new threat to freedom of speech in the country.
Like many other Governments, also Vietnam is deploying a cyber army of 10000 cyber experts to fight online dissent in the country.
The news was revealed by a top Vietnamese general last week, the official that the brigade dubbed ‘Force 47’ has been tasked with fighting “wrongful views” spreading online.
More than half of the population (around 93 million people) has access to the Internet.
According to web watchdog Freedom House, the Internet in Vietnam is “not free”, the organization ranked it second only to China in Asia.
Human Rights Watch deputy Asia director Phil Robertson believes that the brigade Force 47 is a “shocking new dimension to Vietnam’s crackdown on dissent”.
“This is just the latest plank in a campaign to curb internet freedoms at all costs,” Shawn Crispin, Committee to Protect Journalists’ Southeast Asia representative, told AFP Friday.
“While they can’t unplug Facebook, Instagram and the likes outright, they can apply more and more pressure on those platforms and it looks like these cyber troops are their latest attempt to do that.”
The activist Nguyen Chi Tuyen (aka Anh Chi) said the new brigade is an important step in ahead of online repression.
“The main purpose for Force 47 is to try and control news and public opinion on the internet… they want to protect the party, not protect the country,” explained Tuyen.
The Vietnamese Government is applying a strict online monitoring, it continues to ask tech giants like Facebook and YouTube to remove any “toxic content” from their platforms.
The Vietnamese Government believes that hostile groups and foreign governments could use social media and the Internet to destabilize the country and threaten the “prestige of the party’s leaders and the state”.
According to Amnesty International, many dissidents have already been identified and arrested in the country, at least 15 people this year.
Madeline Earp, a senior research analyst with Freedom House, explained that the unit Force 47 is likely to include commentators tasked of spreading online pro-government content and counter critics.
“Vietnam very much follows China’s example when suppressing internet freedom, particularly when it comes to blocking websites and arresting dissidents,” she told AFP.
Vietnam had built up considerable cyber capabilities in across the years, according to the incident response firm Volexity, Vietnamese APT32 group is today one of the most advanced APTs in the threat landscape.
Expert publicly disclosed a macOS zero-day that allows local privilege escalation
2.1.2017 securityaffairs Apple
A security researcher has publicly disclosed the details of macOS zero-day flaw that can be exploited to take complete control of a system.
A security researcher that goes online with the Twitter account Siguza (@s1guza) has publicly disclosed the details of macOS zero-day vulnerability that can be exploited to take complete control of a system. The expert speculates the flaw has been around since at least 2002
Siguza
@s1guza
Fuck it, dropping a macOS 0day. Happy New Year, everyone. https://siguza.github.io/IOHIDeous/
11:59 PM - Dec 31, 2017
119 119 Replies 2,634 2,634 Retweets 4,407 4,407 likes
Twitter Ads info and privacy
The flaw is a local privilege escalation (LPE) vulnerability that affects IOHIDFamily, a kernel extension designed for human interface devices (HID) (e.g. the touchscreen, buttons, accelerometer, etc.).
The flaws discovered by the expert affect all versions of macOS and they can lead to an arbitrary read/write vulnerability in the kernel.
An attacker who has access to a system can trigger the zero-day flaw to execute arbitrary code and gain root permissions.
The expert was analyzing the iOS code searching for vulnerabilities in the iOS kernel when he discovered that the component IOHIDSystem exists only on macOS.
“I was originally looking through its source in the hope of finding a low-hanging fruit that would let me compromise an iOS kernel, but what I didn’t know it then is that some parts of IOHIDFamily exist only on macOS – specifically IOHIDSystem, which contains the vulnerability discussed herein.” Siguza wrote in the technical analysis published on gitHub.
The expert published a PoC code, dubbed IOHIDeous, that works for Sierra and High Sierra (up to 10.13.1, see README) and is able to disable both the System Integrity Protection (SIP) and Apple Mobile File Integrity (AMFI).
“Targets Sierra and High Sierra (up to 10.13.1, see README), achieves full kernel r/w and disables SIP to prove that the vulnerability can be exploited by any unprivileged user on all recent versions of macOS.” continues the expert.
The exploit code developed by the expert runs as fast as possible to avoid user interaction, for example on a shutdown “we’d be able to slip in between the user getting logged out and the kernel killing us.”

The PoC code published by Siguza seems not work on macOS High Sierra 10.13.2 released on December 6, but the expert believes that this version is still vulnerable.
“The prefetch timing attack I’m using for hid for some reason doesn’t work on High Sierra 10.13.2 anymore, and I don’t feel like investigating that.” said Siguza.
“Maybe patched, maybe just the consequence of a random change, I neither know nor care. The vuln is still there and my code does both info leak and kernel r/w, just not in the same binary – reason is explained in the write-up. If you want that feature, consider it an exercise for the reader.”
Siguza publicly disclosed this macOS zero-day because it is exploitable only by a local attacker and because Apple bug bounty doesn’t cover it.
1 Jan
Security Around The World
@security_china
Replying to @s1guza
Can I ask, why not sell it? I'm sure some government or blackhat would have paid a lot for it? Or are you just the type of person who can't be reasoned with, who doesn't care for money and just want to watch the world burn?
Siguza
@s1guza
My primary goal was to get the write-up out for people to read. I wouldn't sell to blackhats because I don't wanna help their cause. I would've submitted to Apple if their bug bounty included macOS, or if the vuln was remotely exploitable.
3:43 PM - Jan 1, 2018
4 4 Replies 11 11 Retweets 150 150 likes
CSRF Vulnerability in phpMyAdmin allows attackers to perform DROP TABLE with a single click!
2.1.2017 securityaffairs Vulnerebility
The development team of phpMyAdmin has fixed a CSRF vulnerability in phpMyAdmin that could be exploited by attackers for removing items from shopping cart.
Researcher Ashutosh Barot has discovered a critical CSRF vulnerability in phpMyAdmin that could be exploited by attackers to perform malicious operations like drop tables and delete records.
phpMyAdmin developers released the version 4.7.7 that addresses the CSRF vulnerability found by Barot.
“By deceiving a user to click on a crafted URL, it is possible to perform harmful database operations such as deleting records, dropping/truncating tables etc.” reads the security advisory published by phpMyAdmin developers.
An attacker could trick a database admin into performing database operations like DROP TABLE using CSRF with devastating consequences.
“In this case, a CSRF vulnerability allows an attacker to send a crafted URL to the victim and if she (authenticated user) clicks it, the victim may perform a DROP TABLE query on her database. phpMyAdmin team considers this issue as critical vulnerability.” reads the analysis published by Ashutosh Barot.
This means that an attacker can create a crafted URL and trick the victims having an active session into performing dangerous operations without their knowledge.
The expert discovered a feature in phpMyAdmin that uses GET requests for Database operations such as DROP TABLE table_name, this means that it is possible for an attacker to trick a database admin into clicking a button and perform a database query of the attacker’s choice.

Ashutosh Barot also discovered that the URL for performing database operations was being saved in the browser history, an attacker can access them to gain some information about the database.
“Any query you execute by clicking insert, DROP, etc., button as shown in above image . The URL will contain database name and table name as GET request was used to perform DB Operations. URLs are stored at various places such as browser history, SIEM logs, Firewall Logs, ISP Logs, etc. this URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!)” continues the analysis. 
The expert pointed out that the CSRF attack worked even when the user was authenticated in cPanel and phpMyAdmin was closed after use.
The vulnerability is ranked as Medium severity because its exploitation needs the user interaction.
Below a video PoC published by Barot:
All versions prior 4.7.7 are affected by the vulnerability, users must update their installations or apply the following patches:
The following commits have been made on the 4.7 branch to fix this issue:
edd929216ade9f7c150a262ba3db44db0fed0e1b
The following commits have been made on the 4.8 branch to fix this issue:
72f109a99c82b14c07dcb19946ba9b76efc32a1b
Necurs Botnet Fuels Massive Year-End Ransomware Attacks
2.1.2017 securityweek Ransomware
The Necurs botnet started 2017 with a four-month vacation, but ended the year sending tens of millions of spam emails daily as part of massive ransomware distribution campaigns.
Considered the largest spam botnet at the moment, Necurs was the main driver behind the ascension of the Locky ransomware (which in turn is associated with the Dridex banking Trojan) in 2016. As Necurs took a long vacation in the beginning of 2017, Locky was silent as well, but both resumed activity in April.
Over the course of 2017, however, the botnet was involved in the distribution of the Jaff, GlobeImposter, and Scarab ransomware families, as well as in 'pump-and-dump' schemes.
Over a 10-day period between December 19 and December 29, 2017, Necurs was once again involved in the distribution of ransomware, in addition to sending typical holiday-themed scam emails, data collected by AppRiver reveals.
The messages, AppRiver says, were distributing the Locky and GlobeImposter ransomware families and revealed the attackers’ preference to use malicious .vbs (Visual Basic Script) or .js (JavaScript) files located inside a .7z archive.
Consisting of between 5 and 6 million infected hosts and keeping around 1 or 2 million of them active at any given time, Necurs provides operators with remote access to the infected machines and can be used for various malicious activities, including malware downloads.
Starting on Dec. 19, the botnet was observed sending tens of millions of spam emails daily to distribute ransomware. It started at nearly 46 million emails on the first day (peaking at over 4.6 million messages per hour) and continued with over 47 million messages on Dec. 20 (peaking at 5.7 million per hour).
While the initial spam featured mainly .vbs files inside the .7z archive, .js files started appearing as well on the second day, and the traffic switched to .js files on Dec. 21-22, when it also started to taper off, at 36 million and 29 million messages per day, respectively. The botnet remained quiet from Dec. 23-25 and recommenced activity for only a couple of hours on Dec. 26.
“Hard to say why, however, I would hypothesize the operators may have been testing or monitoring the rate of infections and realized many workers are on vacation,” AppRiver’s David Pickett notes.
On Dec. 28-29, however, the botnet was highly active. It peaked at 6.5 million messages early morning on Dec. 28, but wasn’t active for long. On the next day, Necurs was observed sending nearly 59 million ransomware messages.
The malicious emails, the security researchers reveal, were masquerading as purchase orders and voicemails, but also claimed to contain images of interest to the intended victims.