Highly Targeted Attacks Hit North Korean Defectors
11.1.2018 securityweek BigBrothers
A recent set of attacks aimed at North Korean defectors and journalists were associated with a highly targeted campaign conducted by an actor that does not appear to be related to any known cybercrime groups, McAfee says.
The attacks used a range of vectors to infect victims with malware, including email, the KakaoTalk chat application (which is popular in South Korea), and social network services such as Facebook. Some of the attacks also employed Google-shortened URLs to spread malware.
McAfee’s research into the incident revealed the use of two versions of the dropper malware, namely applications called “Pray for North Korea” and “BloodAssistant.” Most of the clicks leading to infection originated from South Korea in both cases, McAfee's security researchers discovered.
The most frequently observed browser and operating system combination for the clicks was Chrome and Windows, with Android coming in second, McAfee notes in a technical report. Furthermore, the investigation revealed that Facebook was used in 12% of infections to send a malicious link to the targets.
The Trojan used in this campaign, which McAfee detects as Android/HiddenApp.BP, is dropped onto the victim’s device via malicious APK files. Although various malicious apps are used for malware delivery, the dropper mechanism is identical, the researchers say.
The dropper first checks whether the device hasn’t been already infected, then tricks the victim into enabling accessibility permissions. The application then displays an overlay to hide the fact that it turns on required settings and downloads and installs the Trojan. The overlay is removed once the installation has been completed.
The Trojan uses cloud services such as Dropox and Yandex as the command and control (C&C) server. Once installed, it uploads device information to the cloud, then downloads a file containing commands and other data to control the infected device. Malicious behavior such as saving SMS messages and contact information is implemented in a separate DEX file.
Variants of the malicious APKs were found on Google Drive, some using different cloud services as C&Cs, while others also dropping a separate call-recording application.
The researchers discovered that the initial malicious APKs were uploaded to Google Drive from a single account, which was also associated with a social network account. The same account is believed to have been used to send shortened URLs to victims.
The group behind the account appears to know the South Korean culture well, yet the account also revealed the use of the North Korean word for “blood type,” instead of the South Korean word. A North Korean IP address was also found in test log files on some Android devices connected to accounts used to spread the malware.
The researchers also discovered a deleted folder named Sun Team, supposedly revealing the name of the actor behind the campaign, which has been supposedly active since 2016.
“This malware campaign is highly targeted, using social network services and KakaoTalk to directly approach targets and implant spyware. We cannot confirm who is behind this campaign, and the possible actor Sun Team is not related to any previously known cybercrime groups. The actors are familiar with South Korea and appear to want to spy on North Korean defectors, and on groups and individuals who help defectors,” McAfee concludes.
Meltdown Patch Broke Some Ubuntu Systems
11.1.2018 securityweek Vulnerebility
Canonical was forced to release a second round of Ubuntu updates that address the recently disclosed CPU vulnerabilities after some users complained that their systems no longer booted after installing the initial patches.
On January 9, Canonical released Ubuntu updates designed to mitigate Spectre and Meltdown, two recently disclosed attack methods that work against processors from Intel, AMD, ARM, Qualcomm and IBM. The Linux kernel updates mitigate the vulnerabilities that allow the Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715) attacks.
Shortly after the kernel was updated to version 4.4.0-108, some Ubuntu users started complaining that their systems had failed to boot. Restoring the system to an earlier version apparently resolved the problem.
The updates released by Microsoft in response to the CPU flaws also caused problems, but only for users with some older AMD processors. The company has decided to no longer deliver the updates to AMD devices until compatibility issues are resolved. In the case of Ubuntu, however, the update has affected users with Intel processors.
Canonical has confirmed that the fix for the Meltdown vulnerability introduced a regression that prevented systems from booting successfully. The issue has been addressed with the release of new updates that deliver version 4.4.0.109 of the kernel.
Many affected users have confirmed that their systems boot properly after updating to 4.4.0-109. While it’s unclear how many devices have been hit, Canonical’s advisories mention “a few systems.”
Affected tech firms started announcing the availability of patches and workarounds for the Spectre and Meltdown vulnerabilities shortly after the flaws were disclosed by researchers. The latest major companies to release mitigations are IBM, whose POWER processors and Power Systems servers are impacted, and NVIDIA, which released updates for GPU display drivers and other products to help mitigate the CPU issues.
Meltdown and Spectre allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information. Patches for the underlying vulnerabilities may introduce significant performance penalties.
Mac Malware Creator Indicted in U.S.
11.1.2018 securityweek Apple
“FruitFly” Mac Malware Creator Allegedly Spied On Victims for 13 Years
An Ohio man was charged this week in a 16-count indictment for allegedly developing malware known as “FruitFly” and for infecting thousands of computers with it.
The man, Phillip R. Durachinsky, 28, of North Royalton, Ohio, has been charged with using the malware for more than 13 years to watch, listen to, and obtain personal data from unknowing victims, as well as to produce child pornography.
FruitFly, also known as Quimitchin, was first discovered a year ago, despite being said to have been developed over a decade ago. The malware was supposedly designed to exfiltrate data from anything it can access and its presence on machines at biomedical facilities led researchers to believe it was a cyber-espionage tool. What isn’t yet clear is how the malware was distributed to the compromised systems.
At Virus Bulletin last year, security researcher Patrick Wardle presented a paper on a second variant of FruitFly, explaining that the threat is installed persistently on the victims’ machines, that it employs obfuscation, and that it includes support for a large number of commands. By setting up a custom command and control (C&C) server for the threat, he was also able to observe and analyze the malware’s behavior.
The malware, Wardle revealed, included support for around 25 commands, and supports advanced commands rarely seen in macOS malware, such as the ability to simulate mouse and keyboard events, likely in an attempt to interact with system dialogs or alerts from security products.
Although designed to target Macs, FruitFly was found to contain Linux shell commands and to run just fine on Linux, which suggested that a variant targeting this operating system might have been built as well. Windows-based executable files that communicated with the malware’s C&C were also discovered, and one of them was found to use a libjpeg library that hasn't been updated since 1998, but which FruitFly also uses.
According to the indictment the Department of Justice made public this week, Durachinsky from 2003 through Jan. 20, 2017, allegedly orchestrated a scheme to access “thousands of protected computers owned by individuals, companies, schools, a police department, and the government, including one owned by a subsidiary of the U.S. Department of Energy.”
Using the FruitFly malware, he allegedly controlled infected computers “by accessing stored data, uploading files, taking and downloading screenshots, logging a user’s keystrokes, and turning on the camera and microphone to surreptitiously record images and audio,” DoJ said.
The indictment also alleges that Durachinsky used the malware to steal victims’ personal information, including logon credentials, tax records, medical records, photographs, banking records, Internet searches, and communications. He is also charged with using the stolen credentials to access and download information from third-party websites.
Moreover, Durachinsky is said to have used the compromised systems to watch and listen to victims without their knowledge or permission and to intercept oral communications taking place in the room where the infected computer was located. Durachinsky was apparently alerted if a user typed words associated with pornography and is said to have saved millions of images and to have kept detailed notes of what he saw.
“For more than 13 years, Phillip Durachinsky allegedly infected with malware the computers of thousands of Americans and stole their most personal data and communications,” Acting Assistant Attorney General John P. Cronan of the Justice Department’s Criminal Division said.
CSE Malware ZLab – Double Process Hollowing -The stealth process injection of the new Ursnif malware
11.1.2018 securityaffairs Virus
pdf
A new variant of the infamous Ursnif malware spread in the wild and adopts a new advanced evasion technique dubbed Double Process Hollowing.
Whereas the malware LockPos, famous for its new incredibly advanced and sophisticated evasion technique, spread and affected many Points of Sale, another variant spread in the wild and adopts a similar but not identical advanced evasion trick. It is likely a new variant of “ursnif v3”, another evolution of an old banking trojan that was spreading since November 2017. Moreover, the command and control of this new malware, oretola[.]at has been sinkholed by authorities, so it is difficult to reconstruct the entire behavior and the real purpose of this malware.
However, it is very interesting to analyze its stealth evasion technique that allows it to be invisible to many modern antivirus software. In fact, its final stage is to hide itself as a thread of “explorer.exe” process and this make the analysis very difficult. To reach its goal, the malware uses a sort of “double process hollowing” technique based on Windows Native API, leveraging the “svchost.exe” system process as a way to make privilege escalation and to get to inject malicious code in “explorer.exe”.
Only after the concealment in “explorer.exe” it starts to make its malicious operations that consist of contacting a series of compromised sites the host encrypted additional payloads. The final step of its malicious behavior is to periodically communicate with its C2C, “oretola[.]at”, where it sends information about the victim host.
This malware probably spreads up through spam mails, the message contains an URL that points to a compromised site on which the sample is hosted. We discovered the malware sample just on one of these compromised sites, in particular it is an Italian blog dedicated to dolls “marinellafashiondolls[.]com/_private/php3.exe”.
Process Hollowing evasion technique
The malware uses almost exclusively the Native API of Windows with also its undocumented functions. The use of them causes a more difficult monitoring by antiviruses.
Once the php3.exe file is executed, it deletes itself from the original path and recopy itself in “%APPDATA%\Roaming\Microsoft\Brdgplua\ddraxpps.exe” path.
Once completed this operation, the malware starts its malicious behavior.
The full report published by researchers at ZLAb details step by step the technique implemented by the malware.
macOS Malware Creator Charged With Spying on Thousands of PCs Over 13 Years
11.1.2017 thehackernews Apple

The U.S. Justice Department unsealed 16-count indictment charges on Wednesday against a computer programmer from Ohio who is accused of creating and installing spyware on thousands of computers for more than 13 years.
According to the indictment, 28-year-old Phillip R. Durachinsky is the alleged author of FruitFly malware that was found targeting Apple Mac users earlier last year worldwide, primarily in the United States.
Interestingly, Durachinsky was just 14 years old when he programmed the first version of the FruitFly malware, and this full-fledged backdoor trojan went largely undetected for several years, despite using unsophisticated and antiquated code.
The malware was initially discovered in January 2017 by Malwarebytes and then Patrick Wardle, an ex-NSA hacker, found around 400 Mac computers infected with the newer strain of FruitFly. However, Wardle believed the number of infected Macs would likely be much higher.
The malware is capable of advanced surveillance on macOS devices with the ability to remotely take control of webcams, microphones, screen, mouse, and keyboards, as well as install additional malicious software.
Since the source code of Fruitfly also includes Linux shell commands, the researchers believe the malware would work just fine on Linux operating system.
From 2003 to January 2017, Durachinsky used spyware, which was later named FruitFly, to gain access to thousands of computers belonging to individuals, companies, schools, a police department, and a subsidiary of the U.S. Department of Energy.
Durachinsky allegedly used the malware to steal the personal data of victims, including their tax records, banking records, medical records, login credentials, photographs, Internet searches, and potentially embarrassing communications.
"He is alleged to have developed computer malware later named “Fruitfly” that he installed on computers and that enabled him to control each computer by accessing stored data, uploading files, taking and downloading screenshots, logging a user’s keystrokes, and turning on the camera and microphone to surreptitiously record images and audio," the DoJ says.
Besides installing Fruitfly, Durachinsky is also accused of producing child pornography, as in some cases, the malware alerted him if a user typed any pornography term. It’s likely such action would prompt recording.
Durachinsky is facing charges of Computer Fraud and Abuse Act violations, Wiretap Act violations, production of child pornography, and aggravated identity theft.
However, the charges are merely allegations at this time, and the defendant is presumed innocent unless proven guilty beyond a reasonable doubt in a court of law.
WhatsApp Flaw Could Allow 'Potential Attackers' to Spy On Encrypted Group Chats
11.1.2017 thehackernews Social

A more dramatic revelation of 2018—an outsider can secretly eavesdrop on your private end-to-end encrypted group chats on WhatsApp and Signal messaging apps.
Considering protection against three types of attackers—malicious user, network attacker, and malicious server—an end-to-end encryption protocol plays a vital role in securing instant messaging services.
The primary purpose of having end-to-end encryption is to stop trusting the intermediate servers in such a way that no one, not even the company or the server that transmits the data, can decrypt your messages or abuse its centralized position to manipulate the service.
In order words—assuming the worst-case scenario—a corrupt company employee should not be able to eavesdrop on the end-to-end encrypted communication by any mean.
However, so far even the popular end-to-end encrypted messaging services, like WhatsApp, Threema and Signal, have not entirely achieved zero-knowledge system.
Researchers from Ruhr-Universität Bochum (RUB) in Germany found that anyone who controls WhatsApp/Signal servers can covertly add new members to any private group, allowing them to spy on group conversations, even without the permission of the administrator.
As described by the researchers, in the pairwise communication (when only two users communicate with each other) server plays a limited role, but in case of multi-user chats (group chat where encrypted messages are broadcasted to many users), the role of servers increases to manage the entire process.
That's where the issue resides, i.e. trusting the company's servers to manage group members (who eventually have full access to the group conversation) and their actions.
As explained in the newly published RUB paper, titled "More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema," since both Signal and WhatsApp fail to properly authenticate that who is adding a new member to the group, it is possible for an unauthorized person—not a group administrator or even a member of the group—to add someone to the group chat.
What's more? If you are wondering that adding a new member to the group will show a visual notification to other members, it is not the case.
According to the researchers, a compromised admin or rogue employee with access to the server could manipulate (or block) the group management messages that are supposed to alert group members of a new member.
"The described weaknesses enable attacker A, who controls the WhatsApp server or can break the transport layer security, to take full control over a group. Entering the group, however, leaves traces since this operation is listed in the graphical user interface. The WhatsApp server can therefore use the fact that it can stealthily reorder and drop messages in the group," the paper reads.
"Thereby it can cache sent messages to the group, read their content first and decide in which order they are delivered to the members. Additionally, the WhatsApp server can forward these messages to the members individually such that a subtly chosen combination of messages can help it to cover the traces."
WhatsApp has acknowledged the issue, but argued that if any new member is added to a group, let's say by anyone, other group members will get notified for sure.
"We've looked at this issue carefully. Existing members are notified when new people are added to a WhatsApp group. We built WhatsApp so group messages cannot be sent to a hidden user," a WhatsApp spokesperson told Wired.
"The privacy and security of our users is incredibly important to WhatsApp. It's why we collect very little information and all messages sent on WhatsApp are end-to-end encrypted."
But if you are not part of a group with very selected members, I'm sure many of you would relatively ignore such notifications easily.
Researchers also advised companies to fix the issue just by adding an authentication mechanism to make sure that the "signed" group management messages come from the group administrator only.
However, this attack is not easy (exception—services under legal pressure) to execute, so users should not be worried about it.
[Bug] macOS High Sierra App Store Preferences Can Be Unlocked Without a Password
11.1.2017 thehackernews Apple
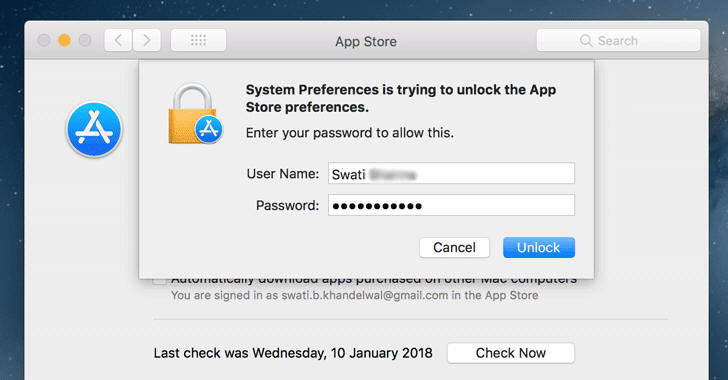
Yet another password vulnerability has been uncovered in macOS High Sierra, which unlocks App Store System Preferences with any password (or no password at all).
A new password bug has been discovered in the latest version of macOS High Sierra that allows anyone with access to your Mac to unlock App Store menu in System Preferences with any random password or no password at all.
The impact of this vulnerability is nowhere as serious as the previously disclosed root login bug in Apple's desktop OS that enabled access to the root superuser account simply by entering a blank password on macOS High Sierra 10.13.1.
As reported on Open Radar earlier this week, the vulnerability impacts macOS version 10.13.2 and requires the attacker to be logged in with an administrator-level account for this vulnerability to work.
I checked the bug on my fully updated Mac laptop, and it worked by entering a blank password as well as any random password.
If you're running latest macOS High Sierra, check yourself:
Log in as a local administrator
Go to System Preferences and then App Store
Click on the padlock icon (double-click on the lock if it is already unlocked)
Enter any random password (or leave it blank) in login window
Click Unlock, Ta-da!
Once done, you'll gain full access to App Store settings, allowing you to modify settings like disabling automatic installation of macOS updates, app updates, system data files and even security updates that would patch vulnerabilities.
We also tried to reproduce the same bug on the latest developer beta 4 of macOS High Sierra 10.13.3, but it did not work, suggesting Apple probably already knows about this issue and you'll likely get a fix in this upcoming software update.
What's wrong with password prompts in macOS? It's high time Apple should stop shipping updates with such an embarrassing bug.
Apple also patched a similar vulnerability in October in macOS, which affected encrypted volumes using APFS wherein the password hint section was showing the actual password of the user in the plain text.
A security issue in WhatsApp potentially allows attackers to eavesdrop on encrypted Group chats
11.1.2017 securityaffairs Krypto
An attacker can secretly eavesdrop on your private end-to-end encrypted group chats on WhatsApp, Threema and Signal messaging apps.
Even if the messaging services implement end-to-end encryption, an attacker or someone in the company that provides the service can decrypt your messages.
A Group of researchers from Ruhr-Universität Bochum (RUB) in Germany discovered that anyone who controls WhatsApp/Signal servers can covertly add new members to any private group without permission of the administrator, with this trick it is possible to spy on group conversations.
In case of multi-user chats, the servers manage the entire communication process.
“Contrary to classical multi-user chats, for example, to IRC in which all members are online, groups in IM protocols must work in asynchronous settings; Groups must be createable and messages must be deliverable even if some group members are offline” reads the paper published by the researchers, titled “More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema,”
“We observed two shortcomings in the design of WhatsApp’s group protocol that allow to (1) burgle into a group and to (2) forge acknowledgments. The shortcomings have similar results as the attacks on Signal, although the underlying protocol and exploitation differ”
The experts discovered that both Signal and WhatsApp fail to properly authenticate an entity that is adding a new member to the group, this means that an unauthorized user that is not a group administrator or even a member of the group can add a member to the group conversations.
Experts also discovered that it is possible to add a new member without notifying the action to other members, this is possible because a rogue admin or employee with access to the server could manipulate (or block) the group management messages.
The abilities to burgle into a group and to forge acknowledgments could be chained to allow an attacker who controls the WhatsApp server or can break the transport layer security to fully control group activities.
“The described weaknesses enable attacker A, who controls the WhatsApp server or can break the transport layer security, to take full control over a group. Entering the group, however, leaves traces since this operation is listed in the graphical user interface. The WhatsApp server can therefore use the fact that it can stealthily reorder and drop messages in the group,” explained the researchers.
“Thereby it can cache sent messages to the group, read their content first and decide in which order they are delivered to the members. Additionally, the WhatsApp server can forward these messages to the members individually such that a subtly chosen combination of messages can help it to cover the traces.”
According to WhatsApp, the situation is quite different because if any new member is added to a group other group members will receive a notification.
“We’ve looked at this issue carefully. Existing members are notified when new people are added to a WhatsApp group. We built WhatsApp so group messages cannot be sent to a hidden user,” a WhatsApp spokesperson told Wired.
“The privacy and security of our users is incredibly important to WhatsApp. It’s why we collect very little information and all messages sent on WhatsApp are end-to-end encrypted.”
The RUB team also provide recommendations to the companies that are suggested to solve the issue by adding an authentication mechanism to group management messages, in this way only legitimate administrators can manage the activities of multi chats.
The Ruhr University researchers reported findings of their investigation to WhatsApp in July, in response to their report, WhatsApp fixed one problem with a feature of their encryption that made it harder to crack future messages even after an attacker obtained one decryption key.
“But they told the researchers the group invitation bug they’d found was merely “theoretical” and didn’t even qualify for the so-called bug bounty program run by Facebook, WhatsApp’s corporate owner, in which security researchers are paid for reporting hackable flaws in the company’s software.” continues Wired.
As said the experts also investigated Threema and Signal.
For Threema, the researchers found minor flaws, an attacker who controls the server can replay messages or add users to a group who have been removed. Once informed of the issues, Threema released a version to address the issues.
For Signal the attack is more difficult because the attacker would have to not only control the Signal server but also know an unguessable number called the Group ID. This means that to carry on the attack it is necessary the knowledge of the Group ID that can be obtained from one of the group member’s devices, in this case, the group is likely already compromised.
Italian researcher discovered that Gmail shutdown after sending a Zalgo text
11.1.2018 securityaffairs Vulnerebility
Researchers at security firm We Are Segment have discovered a vulnerability in Gmail, a “distorted” message shuts down the most famous webmail in the world.
This Cybersec company We Are Segment, part of the Interlogica group, discovered a severe vulnerability in Gmail.
Last month the Italian firm made the headlines due to the discovery of the Tormoil vulnerability.
The flaw in Gmail was discovered by the white hat hacker Roberto Bindi, the flaw could be exploited to shut down Gmail by sending to the victim a specially crafted message, impeding the user from accessing his/her email address.
“The test was born out of curiosity. Roberto wanted to see what would have happened if a Zalgo text was injected into a web browser.” reads the press release published by the company.
A Zalgo text is a type of text composed of characters and metacharacters (letters, numbers and other symbols) which extend sideways – above and under – the original text, thanks to the effect produced by the standard Unicode combiners.
The first experiment conducted by the expert demonstrated that the insertion of a Zalgo text (which can also be generated by web applications) containing a great number of metacharacters (more than 1.000.000) triggered the browser crash, namely, the web browser shut down for a few minutes. gmail
Despite the already interesting results, Roberto Bindi didn’t stop there, he decided to send a Zalgo text via Gmail again, expecting another browser crash. Unfortunately, he couldn’t even imagine what kind of results this test would reveal.
What he managed to discover surpassed his imagination: it wasn’t the browser crashing; instead, it was Gmail itself.
The email is effectively received by the recipient, but he cannot open it and, after just a few moments, Gmail shuts down showing the “Error 500” message (internal server failure due to unspecified reasons, like an irreversible code error).
The young researcher managed to find a technical artifice to bypass the block and reactivate the email account, in order to repeat the experiment and verify the duration of the Gmail shutdown. He discovered that the account went down for 4 entire days.
Since this discovery, Roberto decided to contact the Google’s team. After a few weeks, the team communicated that they had begun working on the issue.
“After discovering that by sending a series of special characters the Google’s mail system stopped working, I started worrying about the possible consequences and damages that this vulnerability might have caused when publicized. An ill-intentioned person might have blocked email accounts like “purchases@…” or other work emails, by sending a simple email.” explained Roberto Bindi.
“That’s why my company decided to publish this piece of information only after the issue had been solved by Google. Our choice was based on ethics and it mirrors our company’s ethics code, underlining how WeAreSegment is formed by ethical
hackers”
This Gmail vulnerability discovered by the researcher Roberto Bindi demonstrates how research is one of the most important aspects of cyber security.
“Thanks to this activity, we can directly contribute to the Cyber Security improvement worldwide” – says Filippo Cavallarin, We Are Segment CEO.
New Malware Dubbed LockPos Introduces New Injection Technique To Avoid Detection
11.1.2018 securityaffairs Virus
Security Researchers from Cyberbit have discovered a new malware injection technique being used by a variant of Flokibot malware named LockPoS.
A Point of Sale (PoS) malware is a malicious application that steals credit card data from the memory of computers connected to credit card equipment. Once infected the system, the LockPoS malware tries to gain access and read the memory of the current process in use and begin to search for data that have the pattern of credit card information to send to its command and control server.
“Cyberbit malware researchers recently discovered a stealthy new malware injection technique being used by LockPoS that appears to be a new variant of that used by Flokibot.” reads the analysis published by CyberBit.
“LockPoS is a Point-of-Sale (PoS) malware that steals credit card data from the memory of computers attached to point of sale credit card scanners. LockPos reads the memory of currently running processes on the system, searching for data that looks like credit card information and then sends them to the C&C.”
The same botnet associated with the propagation of Flokibot is being used by LockPoS and its source code have some similarities. In that regard, it is important to notice that the malware has some stages to unpack and decryption with different techniques and routines to call the API for injection-related with Flokibot.
There are three main routines used by PoS malware discovered by CyberBit to inject code in the remote process: NtCreateSection, NtMapViewOfSection, and NtCreateThreadEx. A core dll file native to Windows System, ntdll.dll, is used in the injection technique. The routines related with ntdll that have a “NT” prefix are associated with Windows API that separates user space from kernel space. The injection technique involves the creation of a section object in the kernel with the use of NtCreateSection to call NtMapViewOfSection as a map to view the section in other process and then copy the code into the section and create a remote thread by using NtCreateThreadEx or CreateRemoteThread to execute the code.
Once a routine from ntdll is called the hexadecimal value of the system call is copied to the EAX register, where a instruction is called to make the thread jump to the kernel mode. The kernel then executes the routine based on the value of EAX register. The parameters from the user stack are copied to the kernel stack and executed.
The malware does not call the routines from ntdll to inject code avoiding Anti Virus detection, instead, it maps the routines from ntdll on the disk to its own virtual address space. By doing so the malware maintains a clean copy of dll that is not detected by anti-virus software.
Also, as Cyberbit researchers noticed, a call to NtMapViewOfSection is handled by the malware for the process of explorer.exe.
“One LockPoS malware injection technique involves creating a section object in the kernel using NtCreateSection, calling NtMapViewOfSection to map a view of that section into another process, copying code into that section and creating a remote thread using NtCreateThreadEx or CreateRemoteThread to execute the mapped code.” continues the analysis.

The security researchers report also notice that improving memory analysis is the only effective way to detection since Windows 10 kernel functions can’t be monitored.
Sources:
https://www.cyberbit.com/new-lockpos-malware-injection-technique/
https://www.scmagazine.com/lockpos-malware-adopts-injection-technique-to-evade-detection/article/735425/
https://www.infosecurity-magazine.com/news/lockpos-takes-a-page-from-flokibot/
http://www.securityweek.com/lockpos-adopts-new-injection-technique
https://www.scmagazineuk.com/lockpos-malware-adopts-injection-technique-to-evade-detection/article/735729/
http://newsroom.trendmicro.com/news/endpoint/lockpos-malware-sneaks-onto-kernel-via-new-injection-technique/d/d-id/1330757
https://securityonline.info/lockpos-malware-use-new-injection-technology-to-sneaks-onto-kernel/
https://vulners.com/threatpost/NEW-POINT-OF-SALE-MALWARE-LOCKPOS-HITCHES-RIDE-WITH-FLOKIBOT/126795
https://www.darkreading.com/endpoint/lockpos-malware-sneaks-onto-kernel-via-new-injection-technique/d/d-id/1330757



