
ICS Vendors Assessing Impact of Meltdown, Spectre Flaws
17.1.2018 securityweek Vulnerebility
Organizations that provide solutions for critical infrastructure sectors, including medical device and industrial control systems (ICS) manufacturers, have started assessing the impact of the recently disclosed Meltdown and Spectre exploits on their products.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data. Billions of devices using Intel, AMD, ARM, Qualcomm and IBM processors are affected.
While affected companies have been working on releasing both software and firmware mitigations, the changes made to a system can introduce significant performance penalties and in some cases users reported that the patches had broken their operating system and various applications.Spectre and Meltdown affect industrial control systems
Considering that in the case of industrial systems availability and integrity are of the utmost importance, vendors have warned customers that extensive testing should be conducted before any patches are applied in an effort to avoid disruptions.
Several vendors have published advisories to inform customers that they are assessing the impact of the Spectre and Meltdown exploits. The list includes Siemens, Schneider Electric, ABB, Rockwell Automation, and medical technology company Becton Dickinson (BD). ICS-CERT has also published an advisory directing users to the advisories of some vendors.
Siemens
In an advisory published on Thursday, Siemens told customers that it’s analyzing the impact of the vulnerabilities and available mitigations. Several of the company’s products may be affected as they are typically installed on systems powered by one of the affected processors.
“Updates for operating systems, processor firmware, and other systems can help to mitigate these vulnerabilities. Siemens is testing the compatibility of the patches released for supported operating systems for several products,” the company said.
“Siemens is aware that some updates can result in compatibility, performance or stability issues on certain products and operating systems. Operating system vendors, such as Microsoft, are still working to address these compatibility issues with their updates. Siemens will therefore continue to evaluate the applicability of those updates,” it added.
Until patches and workarounds can be safely applied, Siemens has advised organizations to ensure that untrusted code cannot be executed on systems running its products, which is a requirement for launching Meltdown and Spectre attacks.
Rockwell Automation
Spectre and Meltdown affect industrial control systems
Rockwell Automation has also confirmed that its customers’ environments are potentially impacted by the vulnerabilities.
The company is working with software and hardware partners on addressing the problem in its E1000, E2000 and E3000 Industrial Data Center (IDC) offerings. Its employees are also working on testing the updates made available by Microsoft.
Rockwell Automation has warned organizations that some of the updates released by Microsoft are known to cause anomalies in FactoryTalk-based products, including Studio 5000, FactoryTalk View SE, and RSLinx Classic. Rockwell has been working with Microsoft on resolving the anomalies.
Schneider Electric
Schneider Electric is also monitoring the situation. The company has informed customers that the list of impacted products includes StruxureWare Data Center Expert (DCE), StruxureWare Data Center Operation (DCO), NetBotz Appliances, APC Network Management Cards, PowerChute Network Shutdown, PowerChute Business Edition, PowerChute Personal Edition, and 1ph and 3ph UPS.
“Many of the initial mitigations proposed by hardware and operating system vendors indicate a high level of potential performance impact, Schneider Electric recommends caution if mitigations or patches are applied to critical and/or performance constrained systems,” Schneider Electric said. “If you elect to apply recommended patches or mitigations in advance of further guidance from Schneider Electric, we strongly recommend evaluating the impact of those measures on a Test & Development environment or an offline infrastructure.”
Schneider Electric’s Wonderware warned users that one of Microsoft’s updates causes Wonderware Historian to become unstable.
ABB
Swiss power and automation solutions provider ABB told customers that it has launched an investigation, but all products running on affected processors are potentially impacted.
“The vulnerabilities do not target any ABB products specifically, but potentially affect products that use affected processors in general,” ABB said in an advisory published last week.
Until the company assesses the impact of the attacks on each of its products, it has advised customers to ensure that industrial networks are protected against unauthorized access. Unlike other vendors, ABB has advised customers to install operating system updates without mentioning the potential risks associated with applying unstable patches.
BD
BD pointed out to customers that the vulnerabilities are not exclusive to its products or medical devices in general, and the company believes the risk of attacks is low. BD has provided a list of impacted products.
The company has advised users to apply patches from Microsoft and any firmware updates that may become available. However, the updates from Microsoft should only be applied after they have been tested and approved by BD.
Testing needed before applying patches
While not all ICS vendors mentioned it, any patches and mitigations for the Spectre and Meltdown vulnerabilities should be tested before being deployed to critical systems, particularly since some of them may cause devices to become unstable.
“The changes needed to fix Spectre and Meltdown vulnerabilities more thoroughly are so extensive that costly and extensive testing will be needed before the updates can safely be applied to reliability-critical control systems,” explained Andrew Ginter, VP of Industrial Security at Waterfall Security.
“In the very short term, what every control system owner and operator will be asking is ‘how long can we safely delay this very costly testing process?’ and ‘do I need to drop everything and start testing and applying these fixes yesterday?’,” Ginter added.
AMD Working on Microcode Updates to Mitigate Spectre Attack
12.1.2018 securityweek Vulnerebility
AMD has informed customers that it will soon release processor microcode updates that should mitigate one of the recently disclosed Spectre vulnerabilities, and Microsoft has resumed delivering security updates to devices with AMD CPUs.
Shortly after researchers revealed the Spectre and Meltdown attack methods, which allow malicious actors to bypass memory isolation mechanisms and access sensitive data, AMD announced that the risk of attacks against its products was “near zero.”
The company has now provided additional information on the matter, but maintains that the risk of attacks is low.
According to AMD, its processors are not vulnerable to Meltdown attacks thanks to their architecture. They are, however, vulnerable to Spectre attacks.
Spectre attacks are made possible by two vulnerabilities: CVE-2017-5753 and CVE-2017-5715. The former does impact AMD processors, but the chipmaker is confident that operating system patches are sufficient to mitigate any potential attacks.
Microsoft announced a few days ago that it had suspended the delivery of security updates to devices with AMD processors due to some compatibility issues. AMD said the problem affected some older processors, including Opteron, Athlon and Turion families.
Microsoft said on Thursday that it had resumed the delivery of updates to a majority of AMD devices, expect for a “small subset” of older processors. AMD told customers it expects the issue to be corrected for the remaining processors by next week.
As for the second Spectre vulnerability, AMD believes it is difficult to exploit against its products. Nevertheless, the company has been working with operating system vendors to develop patches, and it has also promised to provide optional microcode updates.
The microcode updates should become available for Ryzen and EPYC processors in the next days, and for previous generation products sometime over the coming weeks. The updates will be available from system manufacturers and OS vendors.
AMD claims its GPUs are not impacted by the vulnerabilities. NVIDIA also says its GPUs are immune, but the company has still provided some display driver updates to help mitigate the CPU flaws.
Intel has already released patches, including processor microcode updates, for many of its processors. Linux users can install the microcode updates through the operating system’s built-in mechanism.
The fixes for the Spectre and Meltdown vulnerabilities appear to cause problems on some systems. Ubuntu users complained that their devices failed to boot after installing updates, forcing Canonical to release a new kernel update to address the issue.
Intel has also become aware of reports that systems with Broadwell and Haswell CPUs reboot more often as a result of the patches.
“We are working quickly with these customers to understand, diagnose and address this reboot issue. If this requires a revised firmware update from Intel, we will distribute that update through the normal channels. We are also working directly with data center customers to discuss the issue,” the company stated.
Proposed Legislation Would Create Office of Cybersecurity at FTC
12.1.2018 securityweek Cyber
Two Democratic senators, Elizabeth Warren, D-Mass., and Mark Warner, D-Va, introduced a bill Wednesday that would provide the Federal Trade Commission (FTC) with punitive powers over the credit reporting industry -- primarily Equifax, Credit Union and Experian -- for poor cybersecurity practices.
The bill is in response to the huge Equifax breach disclosed in September, 2017. "Equifax allowed personal data on more than half the adults in the country to get stolen, and its legal liability is so limited that it may end up making money off the breach," said Senator Warren in a Wednesday statement.
If the bill succeeds, it will become the Data Breach Prevention and Compensation Act of 2018. It will create an Office of Cybersecurity at the FTC, "headed", says the bill (PDF), "by a Director, who shall be a career appointee." This Office would be responsible for ensuring that the CRAs conform to the requirements of the legislation, and would have the power to establish new security standards going forwards.
The punitive power of the Act comes in the level of the potential fines, beginning with a base penalty of $100 for each consumer who had one piece of personal identifying information (PII) compromised and another $50 for each additional PII compromised per consumer. On this basis, were the Act already in force, Equifax would be facing a fine of at least $1.5 billion.
Under current law, say the lawmakers, it is difficult for consumers to get compensation when their personal data is stolen. Typical awards range from $1 to $2 per consumer. This bill requires the FTC to use 50% of its penalty to compensate consumers.
The maximum penalty is capped at 50% of the credit agencies' gross revenue from the previous year. This dwarf's even the EU's General Data Protection Regulation (GDPR) maximum fine set at 4% of global revenue -- but it gets worse: it could increase to 75% of gross revenue where the offending CRA fails to comply with the FTC's data security standards or fails to timely notify the agency of a breach.
The bill requires CRAs to notify the FTC of a breach within 10 days of the breach -- it doesn't at this stage specify whether that is 10 days from the breach occurring, or 10 days from discovery of the breach. Within 30 days of being so notified, the FTC is then required to "commence a civil action to recover a civil penalty in a district court of the United States against the covered consumer reporting agency that was subject to the covered breach."
While 50% of any recovered money is to compensate the victims of the breach, the remaining 50% is to be used for cybersecurity research and inspections by the FTC's new Office of Cybersecurity.
"In today's information economy, data is an enormous asset. But if companies like Equifax can't properly safeguard the enormous amounts of highly sensitive data they are collecting and centralizing, then they shouldn't be collecting it in the first place," said Sen. Warner. "This bill will ensure that companies like Equifax -- which gather vast amounts of information on American consumers, often without their knowledge -- are taking appropriate steps to secure data that's central to Americans' identity management and access to credit."
How much traction this bill will receive in the Senate remains to be seen, but it reflects the general dismay felt by the size of the Equifax breach -- which could have been prevented if patches had been applied. It is not the first Equifax-related legislative proposal, but it is by far the most punitive. In November 2017, New York State Attorney General Eric T. Schneiderman introduced the Stop Hacks and Improve Electronic Data Security Act (SHIELD Act) to improve security specifically within New York State.
SHIELD fines are capped at $250,000, and the disclosure requirement is vague: "The disclosure shall be made in the most expedient time possible and without unreasonable delay, consistent with the legitimate needs of law enforcement..." Put very simply, both proposals are designed to improve the security of their respective 'covered entities' (CRAs are covered in both bills), but SHIELD seeks to do so in a 'business friendly' manner, while the Data Breach Prevention and Compensation Act of 2018 seeks to do so in a 'consumer friendly' manner.
Bogus Passwords Can Unlock AppStore Preferences in macOS
12.1.2018 securityweek Apple
A security vulnerability impacting macOS High Sierra allows admins to unlock the AppStore Preferences in System Preferences by providing any password.
The issue was found to affect macOS 10.13.2, the latest iteration of the platform, and can be reproduced only if the user is logged in as administrator. For non-admin accounts, the correct credentials are necessary to unlock the preferences pane.
macOS High Sierra 10.13.2 users interested in reproducing the bug should log into their machines as administrators, then navigate to the App Store preferences in System Preferences.
Next, users should click on the padlock icon to lock it if necessary, then click it again. When prompted to enter the login credentials, they can use any password and still unlock the Prefpane.
One thing that should be noted is that the App Store setting is opened up unlocked by default when the user is logged as admin and that no sensitive user information can be accessed by triggering the bug.
Eric Holtam notes the security oversight only impacts the App Store preferences and no other system preferences menu can be unlocked in a similar manner. The admin password is still required when attempting to change user and other system preferences.
The issue, however, is not as dangerous as it might look. For starters, the bug can only be triggered if the user is logged in as admin, which clearly minimizes the vulnerability’s impact, given that the admin can unlock the specific settings.
Users affected by the flaw would be those who, although logged as admins, would still keep the App Store preferences locked. In such cases, if the machine was left unattended, anyone with physical access to it could change the respective settings.
Apple, however, is already working on addressing the issue. A patch has been included in the latest beta seed of macOS High Sierra (10.13.3) and will be released to all Mac users in a future software update.
In late November, the tech giant patched a critical authentication bypass vulnerability in macOS High Sierra 10.13.1, where anyone could login as root by providing any password. The attack however, was possible only if the root account hadn’t been enabled or a password hadn’t been set for it. However, experts revealed that remote attacks were also possible.
Never too late, Skype supports end-to-end encryption for new Private Conversations feature
12.1.2018 securityaffairs Social
It’s official, Microsoft’s Skype is rolling out a new feature called Private Conversations, which uses end-to-end encryption.
The latest version of Skype implements end-to-end encryption and introduces the support for the Signal protocol. which is the protocol used by WhatsApp, Facebook Messenger, Google Allo, and Signal.
Attackers will not able to snoop on Skype Private Conversations will support text, audio calls, and file transfers, thanks to the introduction of the end-to-end encryption.
“We know extra protection is important as you share sensitive information over Skype so we’re excited to announce the preview of end-to-end encrypted Private Conversations, available now for Skype Insiders.” states the announcement published by Microsoft.
“With Private Conversations, you can have end-to-end encrypted Skype audio calls and send text messages or files like images, audio, or videos, using the industry standard Signal Protocol by Open Whisper Systems. The content of these conversations will be hidden in the chat list as well as in notifications to keep the information you share private.”
Currently, Presently, Private Conversations are only available in the Insider builds of Skype that is already included in the desktop version of the app, along with the iOS, Android, Linux, and macOS clients.
Unfortunately, Private Conversations still don’t support video calling, and this is a very big limitation.
Experts criticized Skype in the past because it always failed in implementing end-to-end encryption, this limitation advantaged many other instant messaging services like WhatsApp and Facebook Messenger.
The adoption of the Signal protocol is very important, this is the first time Microsoft doesn’t use a proprietary encryption Skype protocol.
If you want to test the new feature, select “New Private Conversation” from the compose menu or from the recipient’s profile.
“After the recipient accepts your invite, all calls and messages in that conversation will be encrypted end-to-end until you choose to end it.” continues Microsoft. “You can only participate in a private conversation from a single device at a time. You can switch the conversation to any of your devices, but the messages you send and receive will be tied to the device you’re using at the time.”

Security Operations Firm Arctic Wolf Raises $16 Million
11.1.2018 securityweek IT
Arctic Wolf Networks, a Sunnyvale, Calif.-based company that offers outsourced security operations center (SOC) services, announced on Wednesday that it has raised $16 million in new funding.
According to the company, the new injection of cash will help support overall business growth, and fuel sales and marketing, product development and strategic alliance initatives.
With security operations teams overwhelmed by the sheer volume of vulnerabilities across the enterprise, they are falling behind in efforts to remediate them. According to a mid 2017 report published by EMA, seventy-four per cent of security teams admit they are overwhelmed by the volume of maintenance work required.
This is a problem that Artic Wolf aims to help with. The company offers a turnkey “SOC-as-a-Service” that includes what the company calls a “Concierge Security Engineer” (CSE) that is a single point of contact for a customer and an extension of a customer’s internal security team.
“Security operations centers are an essential element of modern cybersecurity, and every company needs one,” said Brian NeSmith, CEO and co-founder of Arctic Wolf. “We are transforming how companies look at cybersecurity from a product-centric view to one focused on proactive detection and response. The new funding allows us to invest in key areas of the business and maintain our extraordinary growth trajectory.”
The funding round was led by Sonae Investment Management with participation from Lightspeed Venture Partners, Redpoint Ventures and Knollwood Investment Advisory.
Hackers Leak Olympic Committee Emails in Response to Russia Ban
11.1.2018 securityweek Hacking
A group of hackers linked to Russia has leaked several emails apparently exchanged between officials of the International Olympic Committee (IOC) and other individuals involved with the Olympics. The leak comes in response to Russia being banned from the upcoming Pyeongchang 2018 Winter Games in South Korea.
The group, calling itself Fancy Bears and claiming to be a team of hacktivists that “stand for fair play and clean sport,” previously released confidential athlete medical records stolen from the systems of the World Anti-Doping Agency (WADA), and also targeted the International Association of Athletics Federations (IAAF). One of their most recent leaks included emails and medical records related to football (soccer) players who used illegal substances.
The first leaks from Fancy Bears came shortly after Russian athletes were banned from the 2016 Rio Olympics following reports that Russia had been operating a state-sponsored doping program.
While Fancy Bears claim to be hacktivists, researchers have found ties between the group and Fancy Bear, a sophisticated Russian cyber espionage team also known as APT28, Pawn Storm, Sednit, Sofacy, Tsar Team and Strontium.
The latest leak includes emails apparently exchanged between IOC officials and other individuals involved with the Olympics. Some of the messages discuss the recent decision to ban Russia from the upcoming Winter Games based on the findings of the IOC Disciplinary Commission.
“These emails and documents point to the fact that the Europeans and the Anglo-Saxons are fighting for power and cash in the sports world. WADA headquartered in Montreal, Canada supported by the United States Olympic Committee declared the crusade against the IOC on the pretext of defending clean sport,” the hackers said. “However, the genuine intentions of the coalition headed by the Anglo-Saxons are much less noble than a war against doping. It is apparent that the Americans and the Canadians are eager to remove the Europeans from the leadership in the Olympic movement and to achieve political dominance of the English-speaking nations.”
While the hackers claim the emails they leaked prove the accusations, a majority of the messages don’t appear to contain anything critical. Furthermore, Olympics-related organizations whose systems were previously breached by the hackers claimed at the time that some of the leaked files had been doctored.
WADA representatives told Wired that Fancy Bears are looking to “undermine the work of WADA and others,” and claimed that everything they leaked this week is “dated.” WADA officially accused Russia of being behind previous attacks.
It’s unclear how the emails have been obtained by the hackers, but the group has been known to launch phishing attacks involving fake WADA domains. It’s possible that they tricked some of the individuals whose emails have been compromised into handing over their credentials on a phishing site.
Russia has been accused by several experts of disguising some of its cyber campaigns as hacktivism. For instance, a hacker using the moniker Guccifer 2.0 has taken credit for an attack on the U.S. Democratic Party, which may have influenced last year’s presidential election.
Many believe the Fancy Bears attacks are Russia’s response to its athletes being banned. Perhaps unsurprisingly, articles from two major pro-Russia English-language news organizations suggest that the latest leak from Fancy Bears shows that Russia’s exclusion from the Olympics was politically motivated.
Security firm McAfee reported last week that several organizations associated with the Olympics had received emails set up to deliver information-stealing malware, but it’s unclear who is behind the attacks.
Endgame Lands $1 Million Contract From U.S. Navy
11.1.2018 securityweek IT
Endgame, an Arlington, VA-based supplier of advanced endpoint protection software, has been awarded a $1 million contract by the U.S. Fleet Cyber Command/U.S. Tenth Fleet. The purpose of the contract is to protect more than 500,000 computers and ships' hull, mechanical and electrical systems, weapons and navigation systems, aviation systems, and the technology controlling physical devices on bases and facilities.
"Endgame is honored to enter this partnership with the U.S. Navy," said Nate Fick, Endgame CEO and U.S. military combat veteran. "The Navy is widely known as being on the cutting-edge of cybersecurity defenses, and we were happy to exceed their protection requirements during this competitive process. Safeguarding the most targeted organizations across the Department of Defense is an important part of our mission, and we look forward to continuing it with the Navy."
Endgame LogoFleet Cyber Command is the central cyber authority for the entire U.S. Navy, serving (in its own words), "to direct Navy cyberspace operations globally to deter and defeat aggression and to ensure freedom of action to achieve military objectives in and through cyberspace."
Specifically, the contract is for the acquisition of the Endgame Hunt Team Platform with 10,000 sensors, plus maintenance and support.
Endgame credits the contract to its existing history in protecting both federal government and the U.S. military, and its ability to protect against targeted attack techniques and technologies outlined in the MITRE ATT&CK Matrix. In 2016 it was awarded an $18.8 million contract by the U.S. Air Force.
The Navy's contract justification and approval document is more specific: "Delivered as a single agent, replacing the functions of AV, NGAV, IR, EDR, and exploit prevention agents, Endgame stops all targeted attacks and their components." It scans for vulnerabilities, compares against current STIG checklists, and conducts "if-then scenarios with secondary and tertiary effects (also known as a blast radius)..."
The STIG checklist is a NIST Windows 10 Security Technical Implementation Guide designed to improve the security of Department of Defense information systems. Endgame automatically maps the network against the STIG checklist to evaluate the network's security posture.
While stressing that FLTCYBER will continue to monitor the evolution of EDR, EPP and Next Gen AV technologies that could compete with Endgame in the future, it found that no other single technology currently provides all of its requirements. While combinations of other products could provide much of its required functionality, some requirements could still only be found in Endgame.
Of particular note is Endgame's ability to calculate the "blast radius" on a compromised box. Applied to cybersecurity, the blast radius is the potential effect on the overall network from a compromise. Network segmentation can, for example, limit the blast radius. Endgame's ability to apply 'what-if' scenarios can help security teams determine whether their network configuration is able to contain a potential compromise.
"No other product has been found by the FLTCYBER team at this time that can perform the blast radius function of Endgame," the Navy explained. "This has been identified as a key requirement by FLTCYBER."
Endgame was founded in 2008 by Chris Rouland and other executives who previously worked with the CIA and Internet Security Systems. It originally discovered and sold 0-day vulnerabilities, but shifted away from this around 2014. Under Fick's leadership it has grown its commercial offering using a $23 million Series B funding round in March 2013 followed by a $30 million Series C round in November 2014.
Security Flaws Found in Majority of SCADA Mobile Apps
11.1.2018 securityweek Mobil
Researchers from IOActive and Embedi have conducted an analysis of SCADA mobile applications from 34 vendors and found vulnerabilities in a vast majority of them, including flaws that can be exploited to influence industrial processes.
Two years ago, researchers Alexander Bolshev and Ivan Yushkevich analyzed 20 mobile apps designed to work with industrial control systems (ICS) software and hardware. At the time, they had found roughly 50 security issues – at least one in each application.
Bolshev, who now works for IOActive, and Yushkevich, currently an employee of Embedi, have once again decided to analyze mobile applications used for supervisory control and data acquisition (SCADA) systems in an effort to determine how the landscape has evolved now that the Industrial Internet of Things (IIoT) has become more prevalent.
This time, the experts randomly selected SCADA applications offered on the Google Play Store by 34 vendors – in most cases different than the ones tested back in 2015. The analysis focused on the client apps and backend systems, and it targeted both local and remote applications.
Local applications are typically installed on the tablets used by engineers and they connect directly to industrial devices via Bluetooth, Wi-Fi or a serial connection. Since these programs can be used to control devices such as PLCs, RTUs and industrial gateways, they are typically only used within the plant perimeter, which is considered safe. Remote applications, on the other hand, allow engineers to connect to ICS via the Internet and private cell networks. While in most cases they are only designed for monitoring processes, some of them do allow users to control processes.
Bolshev and Yushkevich set out to find vulnerabilities described in the 2016 OWASP Mobile Top 10 list. These flaws can allow attackers with local or remote access to a device – and ones in a man-in-the-middle (MitM) position – to directly or indirectly influence an industrial process, or trick an operator into performing a harmful action.
Apps from both independent developers and major vendors were tested, which led to the discovery of 147 vulnerabilities in clients and their backend systems.
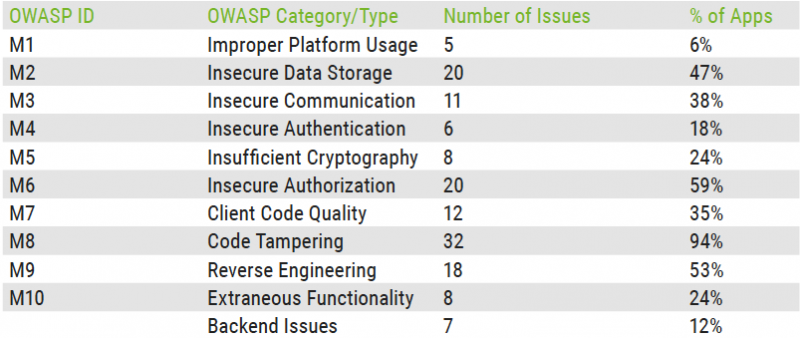
Researchers found that all but two of the applications failed to implement protections against code tampering. The two apps that had such a mechanism only implemented a basic root detection feature. It is easier for malicious hackers to exploit vulnerabilities on rooted Android devices and some malware families are designed to root smartphones and tablets.
More than half of the tested applications also lacked secure authorization mechanisms – only 20 percent of the local apps implemented an authorization system correctly. The most common problems are the lack of password protection and the presence of a “remember password” feature, which defeats the purpose of setting password protection.
The experts also found that more than half of the apps lacked code obfuscation and other mechanisms designed to prevent reverse engineering. Allowing attackers to reverse engineer an application makes it easier for them to find and exploit vulnerabilities.
Nearly half of the tested apps also failed to store data securely. Data is often stored on the SD card or on a virtual partition, and it’s not protected with access control lists (ACLs) or other permission mechanisms.
Unsurprisingly, more than one-third of the analyzed applications failed to secure communications, including via poor handshakes, incorrect SSL versions, and cleartext data transmission. Researchers noted that their tests did not cover applications using Modbus and other ICS protocols, which are insecure by design.
As for backend issues, researchers discovered various types of vulnerabilities, including SQL injection, memory corruption, DoS, and information leakage flaws.
Back in 2015, Bolshev and Yushkevich predicted that the problems they had found would disappear in the future as a result of the rapidly developing nature of mobile software and the growth of IoT. However, their predictions have not proved to be correct, with the latest tests showing that more than 20 percent of the discovered issues allow malicious actors to misinform operators and influence industrial processes.