

Blackwallet hacked, hackers stole $400,000 from users’ accounts through DNS hijacking
17.1.2018 securityaffairs Hacking
BlackWallet.co was victims of a DNS hijacking attack, on January 13 the attackers have stolen over $400,000 from users’ accounts (roughly 670,000 Lumens).
The spike in cryptocurrency values is attracting cybercriminals, the last victim is the BlackWallet.co a web-based wallet application for the Stellar Lumen cryptocurrency (XLM).
The platform was victims of a DNS hijacking attack, on January 13 the attackers have stolen over $400,000 from users’ accounts (roughly 670,000 Lumens).
According to Bleeping Computer, the attackers collected 669,920 Lumens, which is about $400,192 at the current XML/USD exchange rate.
Stellar Lumen today is considered as the eight most popular cryptocurrency.
The attackers hijacked the DNS entry of the BlackWallet.co domain and redirected it to a server they operated, as result of the attack, the application suspended its service.
Technically users were logging to the bogus domain entering their credentials, then the attackers used them to access the account and steal the funds.


Kevin Beaumont
✔
@GossiTheDog
Blackwallet (web wallet) has apparently been hacked
2:51 AM - Jan 14, 2018
5 5 Replies 98 98 Retweets 83 83 likes
Twitter Ads info and privacy
14 Jan
Kevin Beaumont
✔
@GossiTheDog
Blackwallet (web wallet) has apparently been hacked pic.twitter.com/HhewwBXnD9
Kevin Beaumont
✔
@GossiTheDog
The DNS hijack of Blackwallet injected code, if you had over 20 Lumens it pushes them to a different wallet. pic.twitter.com/Eiwb8UR1Nn
2:58 AM - Jan 14, 2018
View image on Twitter
4 4 Replies 32 32 Retweets 34 34 likes
Well I know now why XLM is dipping
Blackwallet got hacked and the worst part was that I laughed my ass off when reading the reddit…their misery is my gain and for a moment, I felt nothing but joy.
Okay maybe there's something wrong with me.
— Colton Miles (@Omgflamethrower) January 14, 2018
Users on Reddit and other communities promptly spread the news of the hack.
The attackers immediately started moving funds from the XLM account to Bittrex, a cryptocurrency exchange, in the attempt to launder them by converting in other digital currency.

The situation is critical, admins are asking Bittrex to block the attackers’ operations before is too late.
“I am the creator of Blackwallet. Blackwallet was compromised today, after someone accessed my hosting provider account. He then changed the dns settings to those of its fraudulent website (which was a copy of blackwallet).” the Blackwallet creator wrote on Reddit.
“Hacker wallet is: https://stellarchain.io/address/GBH4TZYZ4IRCPO44CBOLFUHULU2WGALXTAVESQA6432MBJMABBB4GIYI
I’ve contacted both SDF and Bittrex to ask them to block the bittrex’s account of the hacker. I’ve contacted my hosting provider to disable my account and my websites.
Hacker sent the funds to a bittrex account. This might lead to an identity.”
orbit84
@orbit0x54
Hello @BittrexExchange , please block the account with MEMO XLM 27f9a3e4d954449da04, he hacked https://blackwallet.co/ and is now sending all the funds to your exchange! This is URGENT! A lot of money is involved (>$300,000) https://stellarchain.io/address/GBH4TZYZ4IRCPO44CBOLFUHULU2WGALXTAVESQA6432MBJMABBB4GIYI … https://www.reddit.com/r/Stellar/comments/7q72pw/warning_blackwalletco_hacked_check_your_public_key/?sort=new …
3:35 AM - Jan 14, 2018
11 11 Replies 108 108 Retweets 63 63 likes
Twitter Ads info and privacy
According to the BlackWallet admin, the incident took place after someone accessed his hosting provider account.
The creator of the web-based wallet application is trying to collect more info about the hack from his hosting provider.
“If you ever entered your key on blackwallet, you may want to move your funds to a new wallet using the stellar account viewer,” he added. “Please note however that blackwallet was only an account viewer and that no keys were stored on the server!” he added in the statement.
In December, the popular cryptocurrency exchange EtherDelta suffered a similar incident, attackers conducted a DNS attack that allowed to steal at least 308 ETH ($266,789) as well as a large number of tokens.
Spectre/Meltdown patches had a significant impact on SolarWinds’s AWS infrastructure
17.1.2018 securityaffairs IT
Analysis conducted by SolarWinds on the impact on the performance of the Spectre/Meltdown patches on its own Amazon Web Services infrastructure revealed serious performance degradation.
SolarWinds, the vendor of IT Management Software & Monitoring Tools, has analyzed the impact on the performance of Meltdown and Spectre security patches on its own Amazon Web Services infrastructure.
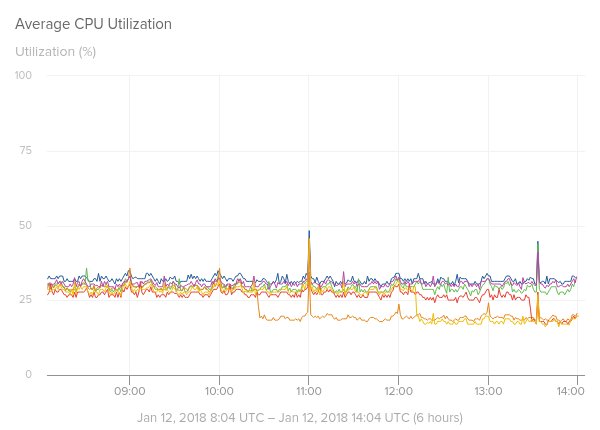
The results are disconcerting, the company has graphically represented the performance of “a Python worker service tier” on paravirtualized AWS instances.
The CPU usage jumped up to roughly 25% just after Amazon restarted the PV instance used by the company.
“As you can see from the following chart taken from a Python worker service tier, when we rebooted our PV instances on Dec 20th ahead of the maintenance date, we saw CPU jumps of roughly 25%.” states the analysis published by SolarWinds.

The company also monitored the performance of its EC2 instances noticing a degradation while Amazon was rolling out the Meltdown patches.
“AWS was able to live patch HVM instances with the Meltdown mitigation patches without requiring instance reboots. From what we observed, these patches started rolling out about Jan 4th, 00:00 UTC in us-east-1 and completed around 20:00 UTC for EC2 HVM instances in us-east-1. ” continues the analysis.
“CPU bumps like this were noticeable across several different service tiers:”
Summarizing, the packet rate drops up to 40% on its Kafka cluster, while CPU utilization spiked by around 25 percent on Cassandra.
The deployment of the patches had also some positive effects, CPU utilization rates decreased. The company issued an update on Jan 12, 2018.
“As of 10:00 UTC this morning we are noticing a step reduction in CPU usage across our instances. It is unclear if there are additional patches being rolled out, but CPU levels appear to be returning to pre-HVM patch levels.” states the firm.
Mike Heffner
@mheffner
New EC2 hot patches for Meltdown/Spectre rolling out? Previous CPU bumps appear to be dropping off starting after 10:00 UTC this morning.
3:06 PM - Jan 12, 2018
1 1 Reply 10 10 Retweets 22 22 likes
New KillDisk variant targets Windows machines in financial organizations in Latin America
17.1.2018 securityaffairs Virus
A new variant of the infamous disk-wiper malware KillDisk has been spotted by malware researchers at Trend Micro while targeting financial organizations in Latin America.
A new variant of the infamous disk-wiper malware KillDisk has been spotted by malware researchers at Trend Micro. This variant of KillDisk, tracked as TROJ_KILLDISK.IUB, was involved in cyber attacks against financial organizations in Latin America, it is delivered by a different piece of malware or it may be part of a bigger attack.
“We came across a new variant of the disk-wiping KillDisk targeting financial organizations in Latin America.” reads a preliminary analysis published by TrendMicro.
“Because KillDisk overwrites and deletes files (and doesn’t store the encryption keys on disk or online), recovering the scrambled files was out of the question.”
KillDisk and the ICS-SCADA malware BlackEnergy, were used in the attacks that caused the power outage in Ukraine in December 2015.
It was used in the same period also against mining companies, railways, and banks in Ukraine. The malware was later included in other malicious codes, including Petya.
In December 2016, researchers at security firm CyberX discovered a variant of the KillDisk malware that implemented ransomware features.
This latest variant targets Windows machines deleting any file stored on drives, except for system files and folders.
“The malware attempts to wipe \\.\PhysicalDrive0 to \\.\PhysicalDrive4. It reads the Master Boot Record (MBR) of every device it successfully opens and proceeds to overwrite the first 0x20 sectors of the device with “0x00”. It uses the information from the MBR to do further damage to the partitions it lists.” states Trend Micro. “If the partition it finds is not an extended one, it overwrites the first 0x10 and last sectors of the actual volume. If it finds an extended partition, it will overwrite the Extended Boot Record (EBR) along with the two extra partitions it points to.”
Once the malware has deleted and overwritten files and folders it attempts to terminate several processes to force the machine reboots.
The processed targeted by the malware are:
Client/server run-time subsystem (csrss.exe)
Windows Start-Up Application (wininit.exe)
Windows Logon Application (winlogon.exe)
Local Security Authority Subsystem Service (lsass.exe)
Trend Micro is still investigating this news KillDisk variant, meantime it is inviting companies to adopt a “defense in depth” approach securing the perimeters from gateways, endpoints, and networks to servers.
Customers reporting OnePlus payment website was hacked and reported credit card fraud
17.1.2018 securityaffairs Incindent
Several customers of the Chinese smartphone manufacturer. OnePlus claim to have been the victim of fraudulent credit card transactions after making purchases on the company webstore.
A large number of OnePlus users claim to have been the victim of fraudulent credit card transactions after making purchases on the official website of the Chinese smartphone manufacturer.
Dozens of cases were reported through the support forum and on Reddit, the circumstance that credit cards had been compromised after customers bought a smartphone or some accessories from the OnePlus official website indicating suggest it was compromised by attackers.
“I purchased two phones with two different credit cards, first on 11-26-17 and second on 11-28-17. Yesterday I was notified on one of the credit cards of suspected fraudulent activity, I logged onto credit card site and verified that there were several transactions that I did not make” claims one of the victims. “The only place that both of those credit cards had been used in the last 6 months was on the Oneplus website.”
Security researchers at Fidus analyzed the payment page after reading the claims on the official forum and discovered that card details are hosted ON-SITE exposing data to attacks.
“We stepped through the payment process on the OnePlus website to have a look what was going on. Interestingly enough, the payment page which requests the customer’s card details is hosted ON-SITE.” reads a blog post published by Fidus. “This means all payment details entered, albeit briefly, flow through the OnePlus website and can be intercepted by an attacker. Whilst the payment details are sent off to a third-party provider upon form submission, there is a window in which malicious code is able to siphon credit card details before the data is encrypted.”

The experts speculate the servers of the company website might have been compromised, likely the attackers exploited some flaws in the Magento eCommerce platform used by OnePlus.
There are two methods used by crooks to steal credit cards from Magento-based stores:
Using Javascript on client-side. The malicious JavaScript is hosted on the web page which causes the customer’s machine to silently send a crafted request containing the payment data to a server controlled by attackers. The researchers who analyzed the payment page on the OnePlus site did not find any malicious JavaScript being used.
The second method relies on the modification of the app/code/core/Mage/Payment/Model/Method/Cc.php file through a shell access to the server. The Cc.php file handles the saving of card details on the eCommerce website. Regardless if card details are actually saved or not, the file is called regardless. Attackers inject code into this file to siphon data.
OnePlus declared that it does not store any credit card data on its website and all payment transactions are carried out through a payment processing partner.
“At OnePlus, we take information privacy extremely seriously. Over the weekend, members of the OnePlus community reported cases of unknown credit card transactions occurring on their credit cards post purchase from oneplus.net. We immediately began to investigate as a matter of urgency, and will keep you updated. ” reads the statement published by the company.
“No. Your card info is never processed or saved on our website – it is sent directly to our PCI-DSS-compliant payment processing partner over an encrypted connection, and processed on their secure servers. “
“The Chinese smartphone maker also confirms that purchases involving third-party services like PayPal are not affected.”
OnePlus excluded that its website is affected by any Magento vulnerability, since 2014, it has entirely been re-built using custom code.
Canadian man charged over leak of billions hacked accounts through LeakedSource
17.1.2018 securityaffairs Hacking
A Canadian Man supposed to be the admin of the LeakedSource.com website was charged over the leak of 3 billion hacked accounts.
The Canadian man Jordan Evan Bloom (27) was charged with data leak of 3 billion hacked accounts, the man was running a website to collect personal data and login credentials from the victims.
The man was charged in December as part of an investigation dubbed “Project Adoration,” aiming at trafficking in personal data, unauthorized use of computers, and possession of an illicitly obtained property.
The RCMP alleges that Bloom was the administrators of the LeakedSource.com website.
According to a statement from the Royal Canadian Mounted Police, “Project Adoration” began in 2016, the investigation started after the Canadian police learned that LeakedSource.com was being hosted by servers located in Quebec.
The RCMP conducted the investigation along with The Dutch National Police and the FBI.
According to the Royal Canadian Mounted Police, Evan Bloom earned some 247,000 Canadian dollars (roughly $198,800 US) by selling the data via leakedsource.com.
“This investigation is related to claims about a website operator alleged to have made hundreds of thousands of dollars selling personal information,” said Rafael Alvarado, the officer in charge of the RCMP Cybercrime Investigative Team. “The RCMP will continue to work diligently with our domestic and international law enforcement partners to prosecute online criminality.”
The data was stolen during massive data breaches of popular websites such as LinkedIn and Ashley Madison online dating service.
Clearly, the availability of such kind of data exposes users at risk of identity theft especially if they share the same credentials on differed web services.
Law enforcement shut down Bloom’s website, unfortunately, another domain name operated by the man is still operating because it hosted on bulletproof servers in Russia.
Four malicious Chrome extensions affected over half a million users and global businesses
17.1.2018 securityaffairs Virus
Four malicious Chrome extensions may have impacted more than half million users likely to conduct click fraud or black search engine optimization.
More than half million users may have been infected by four malicious Chrome extensions that were likely used to conduct click fraud or black search engine optimization.
According to ICEBRG, the malicious extensions also impacted employees of major organizations, potentially allowing attackers to gain access to corporate networks.
“Recently, ICEBRG detected a suspicious spike in outbound network traffic from a customer workstation which prompted an investigation that led to the discovery of four malicious extensions impacting a total of over half a million users, including workstations within major organizations globally.” states the analysis published by ICEBRG. “Although likely used to conduct click fraud and/or search engine optimization (SEO) manipulation, these extensions provided a foothold that the threat actors could leverage to gain access to corporate networks and user information.”
The researchers noticed an unusual spike in outbound traffic volume from a customer workstation to a European VPS provider. The analysis of the HTTP traffic revealed it was to the domain ‘change-request[.]info’ and was generated from a Chrome extension with ID ‘ppmibgfeefcglejjlpeihfdimbkfbbnm’ named Change HTTP Request Header that was available via Google’s Chrome Web Store.

The extension does not contain any malicious code, but the combination of “two items of concern that” could allow attackers to inject and execute an arbitrary JavaScript code via the extension.
The experts highlighted that Chrome extensions are not allowed to retrieve JSON from an external source and execute JavaScript code they contain, but need to explicitly request its use via the Content Security Policy (CSP).
Once enable the ‘unsafe-eval’ (Figure 3) permission to retrieve the JSON from an external source the attacker can force the browser to execute malicious code.
“When an extension does enable the ‘unsafe-eval’ (Figure 3) permission to perform such actions, it may retrieve and process JSON from an externally-controlled server.” “This creates a scenario in which the extension author could inject and execute arbitrary JavaScript code anytime the update server receives a request.” continues the analysis.
The Change HTTP Request Header extension is able to download obfuscated JSON files from an external source (‘change-request[.]info’), by invoking the ‘update_presets()’ function.
The Chrome extension implemented an anti-analysis technique to avoid detection.
The extension checks the JavaScript for the presence of native Chrome debugging tools (chrome://inspect/ and chrome://net-internals/), and if detected, halts the injection of malicious code segment. The Chrome extension implemented an anti-analysis technique to avoid detection.
Once injected the code, the JavaScript creates a WebSocket tunnel with ‘change-request[.]info’ and uses it to proxy browsing traffic via the victim’s browser.
During the analysis, the experts observed that this feature was observed by threat actors for visiting advertising related domains likely to conduct click fraud scams.
“The same capability could also be used by the threat actor to browse internal sites of victim networks, effectively bypassing perimeter controls that are meant to protect internal assets from external parties.” continues the analysis.
The security experts discovered other Chrome extensions with a similar behavior and using the same C&C server.
Nyoogle – Custom Logo for Google
Lite Bookmarks
Stickies Chrome’s Post-it Notes
Powerful Skygofree spyware was reported in November by Lukas Stefanko and first analyzed by CSE CybSec
17.1.2018 securityaffairs Android
The Skygofree spyware analyzed by Kaspersky today was first spotted by the researcher Lukas Stefanko and the first analysis was published last year by the CSE Cybsec ZLab.
Security researchers at Kaspersky Lab have made the headlines because they have spotted a new strain of a powerful Android spyware, dubbed Skygofree, that was used to gain full control of infected devices remotely.
Skygofree is an Android spyware that could be used in targeted attacks and according to the experts it has infected a large number of users for the past four years.
The name Skygofree is not linked to Sky Go, which is the subsidiary of Sky and does not affect its services.
The malware has been in the wild at least since 2014, and it was improved several times over the years.
“At the beginning of October 2017, we discovered new Android spyware with several features previously unseen in the wild. In the course of further research, we found a number of related samples that point to a long-term development process. We believe the initial versions of this malware were created at least three years ago – at the end of 2014.” reads the analysis published by Kaspersky.
“Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.”
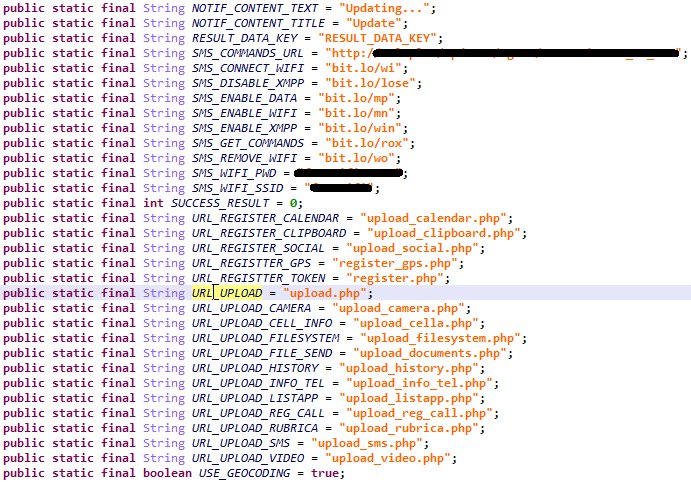
In this post, I’ll show you that the malware was first found by the security researcher at ESET Lukas Stefanko and the first detailed analysis of the spyware (titled “Malware Analysis Report: Fake 3MobileUpdater“) was published by the experts at the CSE Cybsec ZLab.
Lukas Stefanko
@LukasStefanko
The Android Italian Job 🇮🇹
Android Spy Trojan steals sensitive info from victims
Spreads in #Italy 🇮🇹 as fake telecommunication company @Tre_It
Remotely controlled, capable of: install apps, upload files, uses accessibility, take pics, record audio, get sms/location, XMPP...
10:02 AM - Nov 9, 2017
7 7 Replies 113 113 Retweets 110 110 likes
Twitter Ads info and privacy
According to Kaspersky, Skygofree has being distributed through fake web pages mimicking leading mobile network operators. The attackers registered some of the domains used in the attack since 2015.
The most recently observed domain was registered on October 31, 2017, according to Kaspersky data the malicious code was used against several infected individuals, exclusively in Italy.
The team of researchers at CSE CybSec ZLab analyzed in November a fake 3 Mobile Updater that was used pose itself as a legitimate application of the Italian Telco company, TRE Italia.
“The most classic and efficient method used to lure the users is to believe that the application does something good. This is just what 3 Mobile Updater does. In fact, this malicious Android application looks like a legitimate app used to retrieve mobile system update and it improperly uses the logo of the notorious Italian Telco company, TRE Italia, in order to trick victims into trusting it.” reads the report published by CSE CybSec.

The analysis conducted by Kaspersky suggests the involvement of an Italian firm due to the presence in the code of strings in Italian.
“As can be seen from the comparison, there are similar strings and also a unique comment in Italian, so it looks like the attackers created this exploit payload based on android-rooting-tools project source code.” states Kaspersky.
The CSE CybSec researchers arrived atthe same conclusion, below a portion of the code analyzed by the members of the ZLab.

“Moreover, both in the logcat messages and in the code, the malware writers used the Italian language. So, we can say with high confidence that this malicious app has been written by an Italian firm that intended to target users of the Italian telco company Tre.” CSE wrote in the analysis.
The artifacts analyzed by Kaspersky in the malware code and information gathered on the control infrastrucure suggest the developer of the Skygofree implants is an Italian IT company that works for surveillance solutions.

Kaspersky Lab has not confirmed the name of the Italian company behind this spyware, we at the CSE CybSec ZLab opted for the same decision in October due to the possible involvement of law enforcement or intelligence Agencies.
Unfortunately, the OPsec implemented by the firm is very poor. The name of the company is present in multiple reference of the code. Not only, one of the domains used to control registered by the attacker is linked to an Italian technology company.
“Although the security firm has not confirmed the name of the Italian company behind this spyware, it found multiple references to Rome-based technology company “Negg” in the spyware’s code. Negg is also specialized in developing and trading legal hacking tools.” states the blog post published by THN.
Once installed, Skygofree hides its icon and starts background services to conceal its malicious actions from the victim, one interesting feature implemented by the malicious code prevents its services from being killed.
“Interestingly, a self-protection feature was implemented in almost every service. Since in Android 8.0 (SDK API 26) the system is able to kill idle services, this code raises a fake update notification to prevent it” continues Kaspersky.
According to Kaspersky, the Skygofree malware was enhanced since October implementing a sophisticated multi-stage attack and using a reverse shell payload.
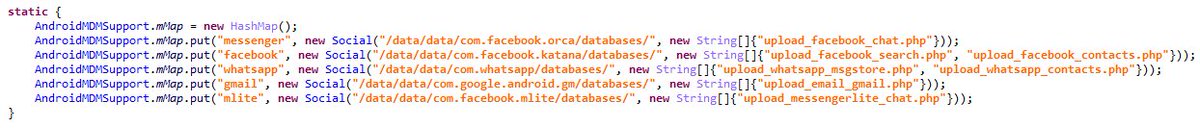
The malicious code includes multiple exploits to escalate privileges for root access used by attackers to execute sophisticated payloads, including a shellcode used to spy on popular applications such as Facebook, WhatsApp, Line, and Viber.
The same spying abilities were implemented in the app we analyzed at the CSE CybSec.
“The capabilities of this malicious app are enormous and include the information gathering from various sources, including the most popular social apps, including Whatsapp, Telegram, Skype, Instagram, Snapchat. It is able to steal picture from the gallery, SMS and calls registry apps. All this data is first stored in a local database, created by the malicious app, and later it is sent to the C2C.” reads the preliminary analysis published on SecurityAffairs.
“There are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, [and] never-before-seen surveillance features,” the researchers said.
Skygofree is able to take pictures and videos remotely, monitor SMS, call records and calendar event, of course, it also able to gather target’ location and access any information stored on the mobile.
Skygofree also can record audio via the microphone, the attacker can also force the victim’s device to connect to compromised Wi-Fi networks it controls in order to conduct man-in-the-middle attacks.
Kaspersky also found a variant of Skygofree targeting Windows users, a circumstance that suggests the same company is also targeting machines running Windows OS.
The best way to prevent yourself from being a victim is to avoid downloading apps via third-party websites, app stores or links provided in SMS messages or emails.
Comparative analysis fake 3 Mobile Updater vs SkyGoFree
I asked my colleague Dr. Antonio Pirozzi, Director of the CSE CybSec ZLab, to compare the stubs of code shared by Kaspersky with the ones related to the code we analyzed back in November.
This is what has emerged:
These classes are identical:


The spyware we analyzed did not contain the Android exploits found by Kaspersky, as well as the reverse shell PRISM and the busy box.
The class used for parsing are similar;
The DNS used are the same;

The IoCs published by Kaspersky includes the URL of the C&C (url[.] plus) which was the same of the Spyware analyzed by CSE CybSec.
Conclusion
Many parts of the code are identical, both source codes include strings in Italian and the reference to the Italian firms are the same. The version analyzed by Kaspersky is a new version of the malware analyzed by CSE CybSec ZLab.
Kaspersky also shared the URL from which the spyware is downloaded and one of them was related to the version we analyzed (Fake 3 mobile updater).
The two version of the malware shared numerous classes, C&C server, Whois records and many other info. The sample analyzed by CSE was probably still under development.
Oracle Fixes Spectre, Meltdown Flaws With Critical Patch Update
17.1.2018 securityweek Vulnerebility
Oracle on Tuesday released its first Critical Patch Update for 2018 to deliver 237 new security fixes across its product portfolio. Over half of the addressed vulnerabilities could be remotely exploited without authentication.
As part of the January 2018 Critical Patch Update, Oracle released fixes for the Critical processor vulnerabilities made public in the beginning of the year, namely Spectre and Meltdown. Impacting modern processors, the bugs put billions of devices at risk, and vendors have been working hard to address them over the past several weeks.
“The January 2018 Critical Patch Update provides fixes for certain Oracle products for the Spectre (CVE-2017-5753, CVE-2017-5715) and Meltdown (CVE-2017-5754) Intel processor vulnerabilities,” Oracle notes in its advisory. Specific details, however, are included in a separate note, accessible only to its customers.
The security updates Oracle released for the Sun Systems Products Suite also include a fix for Oracle X86 Servers to address the CVE-2017-5715 Spectre flaw. The fix “includes Intel microcode that enables OS and VM level mitigations,” but the patch is necessary only for servers using non Oracle OS and Virtualization software.
“Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode,” the company said.
A patch for the same bug was also included in the security updates for Oracle VM VirtualBox.
An article from The Register claims that Oracle admitted in a document on its customer portal that Solaris on SPARCv9 might be impacted by the Spectre flaws. The company reportedly said that patches are being developed, but didn’t provide information on when they would be released or on the performance impact they might have.
The product with the largest number of fixes in the January 2018 Critical Patch Update is Financial Services Applications, at 34 patches. 13 of the flaws could be remotely exploitable without authentication.
Fusion Middleware was the second most impacted Oracle product, at 27 fixes (21 of the bugs being remotely exploitable without authentication), followed by MySQL (25 fixes – 6 remotely exploitable bugs), and Java SE (21 – 18) and Hospitality Applications (21 – 15).
Oracle also resolved bugs in PeopleSoft Products (15 – 8), Supply Chain Products Suite (14 – 12), Virtualization (14 – 3), Sun Systems Products Suite (13 – 7), Retail Applications (11 – 8), Communications Applications (10 – 8), Health Sciences Applications (7 – 5), E-Business Suite (7 – 4), Database Server (5 – 3), Hyperion (4 – 1), Support Tools (3 – 1), JD Edwards Products (2 – 2), Siebel CRM (2 – 0), Construction and Engineering Suite (1 – 0), and Java Micro Edition (1 – 0).
Affecting Apache Log4j, CVE-2017-5645 was the vulnerability with the largest number of occurrences in this set of patches, at 21. It affects Communications Applications, WebLogic Server, PeopleSoft Products, Retail Applications, and Supply Chain Products Suite.
The vulnerability with the highest CVSS score (10) was addressed in Sun ZFS Storage Appliance Kit (AK). The most commonly encountered Critical vulnerabilities had a CVSS score of 9.8. Over 20 such flaws were found in Communications Applications, Fusion Middleware, PeopleSoft, Retail Applications, and Virtualization products.
Backdoor Found in Lenovo, IBM Switches
17.1.2018 securityweek Virus
A high severity vulnerability described as a backdoor has been patched in several Flex System, RackSwitch and BladeCenter switches from Lenovo and IBM.
The flaw, tracked as CVE-2017-3765, affects the Enterprise Network Operating System (ENOS) running on affected devices. The vulnerability allows an attacker to gain access to the management interface of a switch.
“An authentication bypass mechanism known as ‘HP Backdoor’ was discovered during a Lenovo security audit in the Telnet and Serial Console management interfaces, as well as the SSH and Web management interfaces under certain limited and unlikely conditions,” Lenovo said in its advisory.
“This bypass mechanism can be accessed when performing local authentication under specific circumstances using credentials that are unique to each switch. If exploited, admin-level access to the switch is granted,” the company added.
ENOS is the operating system that powers Lenovo’s RackSwitch and Flex System embedded switches. ENOS was initially developed by Nortel’s Blade Server Switch Business Unit (BSSBU), which spun off in 2006 to become BLADE Network Technologies (BNT). IBM acquired BNT in 2010 and in 2014 sold it to Lenovo.
The problematic feature, introduced by Nortel in 2004 at the request of a customer, can be found in Lenovo devices and IBM Flex System, BladeCenter and RackSwitch switches that still use the ENOS firmware.
Lenovo patched the security hole with the release of ENOS 8.4.6.0 and also provided workarounds. The company says devices running the CNOS (Cloud Network Operating System) firmware are not vulnerable. IBM has also released firmware updates to fix the vulnerability in impacted switches.
Lenovo pointed out that the backdoor can only be exploited under specific circumstances.
“Lenovo is not aware of this mechanism being exploited, but we assume that its existence is known, and customers are advised to upgrade to firmware which eliminates it,” Lenovo said.
World Economic Forum Publishes Cyber Resiliency Playbook
17.1.2018 securityweek Cyber
World Economic Forum Publishes Playbook for Developing Cyber Resiliency Through Public/Private Collaboration
The World Economic Forum (WEF) has released a playbook for public-private collaboration to improve cyber resiliency ahead of the launch of a new Global Centre for Cybersecurity at the Annual Meeting 2018 taking place on January 23-26 in Davos, Switzerland.
The background to the WEF playbook is the complexity and sometimes conflicting requirements for governments to provide physical and cyber security for their citizens without unnecessarily intruding on personal privacy, and without damaging legitimate multinational businesses. Success, it claims, "depends on collaboration between the public and private sectors."
Word Economic Forum LogoThere are two sections to the playbook: a reference architecture for public-private collaboration, and cyber policy models. There is no attempt to provide a global norm in this process, nor a methodology for implementing individual policy models. It is an intra-country model, and implementation will depend upon each nation's unique values.
Fourteen separate policy topics are included, ranging from research and data sharing, through attribution, encryption, and active defense to cyber-insurance. Five key themes cross these topics: a clearly defined safe harbor for data sharing; legal clarity for the work of white hat researchers; the impact of a symmetrical international policy response; the cost and effect of compliance requirements; and software coding quality standards.
Each policy topic is then analyzed in relation to five areas: security, privacy, economic value, accountability and fairness. It is important at this point to note that the playbooks are designed for governments to develop public/private co-operation -- civil society issues are not seriously discussed.
For example, the first policy model deals with potential government approaches to zero-day vulnerabilities. The life-cycle of a zero-day comprises unknown existence in code; discovery; and exploitation and mitigation. While secure coding practices can limit the occurrence of zero-days, they "will continue to exist due to human error and other factors." Therefore, there needs to be a government policy towards zero-days.
The two primary options are for governments to "completely exit the zero-day market and avoid research dedicated to finding software vulnerabilities;" or to stockpile for own use, and/or disclose to vendors. The implications of the latter option are then discussed. Stockpiling without disclosure increases the likelihood that bad actors might also independently discover the vulnerability. Purchasing zero-days weakens the bug bounty programs since researchers are likely to sell to the highest bidder -- which is likely to be government.
The effect of a zero-day policy is then related to the five security areas. Increased exploitation of zero-days will hurt commerce (economy) and result in more breaches (privacy). Increased research and more sharing will be beneficial (security); while the sharing of zero-days applies pressure on vendors to more rapidly mitigate the vulnerabilities (accountability). Fairness is not implicated in the different policy choices
This basic model of analyzing the policy topic, and then discussing the trade-offs with each of the five security areas (and their interaction) is applied to each of the 14 discussed policy topics. For example, 'active defense' is first defined to range from "technical interactions between a defender and an attacker" to "reciprocally inflicting damage on an alleged adversary".
One obvious danger is the potential for retaliatory escalation. "Responding to a nation-state adversary may trigger significant collateral obligations for a host state of would-be active defenders," warns the playbook. "As such, policy-makers may consider curtailing attempts to attack nation-states. Policy-makers might also consider curtailing the use of active defence techniques against more sophisticated non-state adversaries, as those adversaries may have a greater ability to obfuscate their identity and dangerously escalate a conflict."
The trade-offs on an active defense policy are then related to the five security areas. Expansive use of active defense will increase costs without necessarily having an economic return (economy). It would diminish privacy for both the alleged adversary and for any third-party collateral damage organizations (privacy). Any actual effect on overall security will likely depend upon its effectiveness as a deterrent (security). Only larger companies, and especially nation-backed industries such as the defense sector will likely have the means to employ active defense (fairness); but it is only a realistic option with more accurate attribution (accountability).
The intention of the playbook is simple, despite the thoroughness and complexity of its content. "The frameworks and discussions outlined in this document," it concludes, "endeavour to provide the basis for fruitful collaboration between the public and private sectors in securing shared digital spaces."
"We need to recognize cybersecurity as a public good and move beyond the polarizing rhetoric of the current security debate. Only through collective action can we hope to meet the global challenge of cybersecurity," said Daniel Dobrygowski, Project Lead for Cyber Resilience at the World Economic Forum.
While public/private dialog on security will of necessity be led by individual governments, the document provides an excellent overview of many of the security issues faced by commercial security teams. Although it contains no technical detail on security problems, it provides a detailed picture of the different implications from different approaches to the main security issues faced by all companies today.
Fake Meltdown/Spectre Patch Installs Malware
17.1.2018 securityweek Virus
Cybercriminals are already taking advantage of the massive attention the recently detailed Meltdown and Spectre CPU flaws have received, in an attempt to trick users into installing malware instead, Malwarebytes warns.
Made public in early January, Meltdown and Spectre are two new side-channel attack methods against modern processors and are said to impact billions of devices. Based on vulnerabilities at the CPU level, the flaws allow malicious apps to access data as it is being processed, including passwords, photos, documents, emails, and the like.
Chip makers and vendors were alerted on the bugs last year, and some started working on patches for their users several months ago, but waited for a coordinated public disclosure set for last week. Apple, Microsoft, Google, Canonical, and IBM are just a few of the vendors that have already deployed patches.
Soon after the patches began rolling out, however, attacks taking advantage of the Meltdown/Spectre fever surfaced. One of them, Malwarebytes reports, is targeting German users with the SmokeLoader malware.
The attack was spotted soon after the German authorities issued a warning on phishing emails trying to take advantage of infamous bugs started to appear.
The emails appeared to come from the German Federal Office for Information Security (BSI), and Malwarebytes discovered a domain that also posed as the BSI website. Recently registered, the SSL-enabled phishing site isn’t affiliated with a legitimate or official government entity, but attempts to trick users into installing malware.
The website is offering an information page that supposedly provides links to resources about Meltdown and Spectre, bug also links to a ZIP archive (Intel-AMD-SecurityPatch-11-01bsi.zip) that contains malware instead of the promised security patch.
Once a user downloads and runs the file, the SmokeLoader malware, which is capable of downloading and running additional payloads, is installed. The security researchers have observed the threat attempting to connect to various domains and sending encrypted information.
By analyzing the SSL certificate used by the fraudulent domain, the security researchers discovered other properties associated with the .bid domain, including a German template for a fake Adobe Flash Player update.
The security researchers have already contacted Comodo and CloudFlare to report the fraudulent website, and the domain stopped resolving within minutes after CloudFlare was informed on the issue.
“Online criminals are notorious for taking advantage of publicized events and rapidly exploiting them, typically via phishing campaigns. This particular one is interesting because people were told to apply a patch, which is exactly what the crooks are offering under disguise,” Malwarebytes concludes.
"PowerStager" Tool Employs Unique Obfuscation
17.1.2018 securityweek Virus
A malicious tool that has managed to fly under the radar since April 2017 is showing great focus on obfuscation, in an attempt to evade detection, Palo Alto Networks warns.
Dubbed PowerStager, the tool has shown an uptick in usage for in-the-wild attacks around December 2017. Developed as a Python script that generates Windows executables using C source code, it uses multiple layers of obfuscation to launch PowerShell scripts to execute a shellcode payload.
PowerStager uses a unique obfuscation technique for PowerShell segments, while also offering increased flexibility, due to multiple configuration options.
Some of these options include the ability to target both x86 and x64 platforms, support for additional obfuscation on top of defaults, support for customized error messages/executable icon for social engineering, and the ability to use Meterpreter or other built-in shellcode payloads. The tool can also fetch remote payloads or embed them into the executable and can escalate privileges using UAC.
Analysis of executables created with the help of this tool revealed that they were being generated programmatically and that an embedded string for the file that gets created was included in each executable, Palo Alto’s Jeff White explains. The filename is also randomized between samples.
White discovered seven total PowerShell scripts that can be generated from the script.
As of late December 2017, Palo Alto has observed 502 unique samples of PowerStager, mainly targeting Western European media and wholesale organizations. A large number of samples, however, were being used for testing and sales proof-of-concepts demonstrations, the researcher says.
White also discovered that certain attributes that PowerStager defines when building the samples can be used to track them. There are also a series of characteristics specific to the generated samples. Although they are usually different between samples, they can prove useful for identification, especially when coupled with said unique obfuscation and PowerShell methods during dynamic analysis.
“While it’s not the most advanced toolset out there, the author has gone through a lot of trouble in attempting to obfuscate and make dynamic detection more difficult. PowerStager has covered a lot of the bases in obfuscation and flexibility well, but it hasn’t seen too much usage as of yet; however, it is on the rise and another tool to keep an eye on as it develops,” White concludes.
New KillDisk Variant Spotted in Latin America
17.1.2018 securityweek Virus
A new variant of the disk-wiper malware known as KillDisk has been spotted by Trend Micro researchers in attacks aimed at financial organizations in Latin America.
The security firm is in the process of examining the new variant and the attacks, but an initial analysis showed that the Trojan appears to be delivered by a different piece of malware or it may be part of a bigger attack.
Early versions of KillDisk were designed to wipe hard drives in an effort to make systems inoperable. The malware was used by the Russia-linked threat actor BlackEnergy in the 2015 attack aimed at Ukraine’s energy sector.
Roughly one year after the Ukraine attack, researchers reported that its developers had turned KillDisk into file-encrypting ransomware. However, the samples analyzed at the time used the same encryption key for all instances, making it possible for victims to recover files.
Experts later reported seeing a KillDisk ransomware designed to target Linux machines, but the malware did not save encryption keys anywhere, making it impossible to recover files.
Some links have also been found between KillDisk and the NotPetya malware, which initially appeared to be a piece of ransomware but later turned out to be a disk wiper. NotPetya hit machines in more than 65 countries and major companies reported losing hundreds of millions of dollars as a result of the attack.
The latest variant, which Trend Micro tracks as TROJ_KILLDISK.IUB, goes back to its roots and focuses on deleting files and wiping the disk. The malware, designed to target Windows systems, goes through all drives in order to delete files, except for system files and folders.
It then proceeds to wipe the disk, which includes reading the master boot record (MBR) and overwriting the extended boot record (EBR). The file removal and disk wiping procedures involve overwriting files and disk sectors in order to make recovery more difficult.
Once files and partitions have been deleted and overwritten, the malware attempts to terminate several processes in an effort to reboot the infected machine. By targeting processes associated with the client/server runtime subsystem (csrss.exe), Windows start-up (wininit.exe), Windows logon (winlogon.exe), and the Local Security Authority Subsystem Service (lsass.exe), the malware can force a blue screen of death (BSOD), a logout, or a restart.
Trend Micro has promised to share more information on the new KillDisk variant as its investigation continues.
Half Million Impacted by Four Malicious Chrome Extensions
17.1.2018 securityweek Virus
Four malicious Chrome extensions managed to infect over half a million users worldwide, including employees of major organizations, ICEBRG reports.
The extensions were likely used to conduct click fraud and/or search engine optimization (SEO) manipulation, but they could have also been used by threat actors to gain access to corporate networks and user information, the security company warns.
The malicious extensions were discovered after observing an unusual spike in outbound traffic volume from a customer workstation to a European VPS provider, ICEBRG reveals. The HTTP traffic was associated with the domain ‘change-request[.]info’ and was generated from a Chrome extension named Change HTTP Request Header.
While the extension itself does not contain “any overtly malicious code,” the researchers discovered the combination of “two items of concern that” could result in the injection and execution of arbitrary JavaScript code via the extension.
Chrome can execute JavaScript code contained within JSON but, due to security concerns, extensions aren’t allowed to retrieve JSON from an external source, but need to explicitly request its use via the Content Security Policy (CSP).
When the permission is enabled, however, the extension can retrieve and process JSON from an externally-controlled server, which allows extension authors to inject and execute arbitrary JavaScript code when the update server receives a request.
What ICEBRG researchers discovered was that the Change HTTP Request Header extension could download obfuscated JSON files from ‘change-request[.]info’, via an ‘update_presets()’ function. The obfuscated code was observed checking for native Chrome debugging tools and halting the execution of the infected segment if such tools were detected.
After injection, the malicious JavaScript creates a WebSocket tunnel with ‘change-request[.]info’ and uses it to proxy browsing traffic via the victim’s browser.
“During the time of observation, the threat actor utilized this capability exclusively for visiting advertising related domains indicating a potential click fraud campaign was ongoing. Click fraud campaigns enable a malicious party to earn revenue by forcing victim systems to visit advertising sites that pay per click (PPC),” ICEBRG reports.
The capability, however, can also be used by the threat actor to browse internal sites of victim networks, thus effectively bypassing perimeter controls.
The security researchers also discovered that Change HTTP Request Header wasn’t the only Chrome extension designed to work in this manner. Nyoogle - Custom Logo for Google, Lite Bookmarks, and Stickies - Chrome's Post-it Notes show similar tactics, techniques, and procedures (TTPs) and feature the same command and control (C&C).
The Stickies extension was also observed using a different code injection pathway, but injecting JavaScript code nearly identical to that of other malicious extensions. It appears that the extension has a history of malicious behavior, as it was observed in early 2017 to be using the new code injection technique following an update.
“The inherent trust of third-party Google extensions, and accepted risk of user control over these extensions, allowed an expansive fraud campaign to succeed. In the hands of a sophisticated threat actor, the same tool and technique could have enabled a beachhead into target networks,” ICEBRG notes.
Considering the total installed user base of these malicious Chrome extensions, the malicious actor behind them has a substantial pool of resources to use for financial gain. Google, the National Cyber Security Centre of The Netherlands (NCSC-NL), the United States Computer Emergency Readiness Team (US-CERT), and customers who were directly impacted have been alerted on the issue.
Canadian Man Charged Over Leak of Three Billion Hacked Accounts
17.1.2018 securityweek Hacking
An Ontario man made his first court appearance Monday to answer charges of running a website that collected personal and password data from some three billion accounts, and sold them for profit.
Jordan Evan Bloom, 27, of Thornhill earned some Can$247,000 ($198,800 US) by selling the data for a "small fee" via leakedsource.com, the Royal Canadian Mounted Police said in a statement.
The information was stolen during massive hacks of websites including LinkedIn and the Ashley Madison online dating service.
Some of the data could also be used to access other popular websites if the hacked user used the same password and username combination, according to police.
Bloom was charged in December as part of a criminal probe dubbed "Project Adoration" focusing on trafficking in personal data, unauthorized use of computers, and possession of illicitly obtained property.
The probe lasted more than a year.
Authorities have shut down Bloom's website, but another with the same domain name hosted by servers in Russia is still operating.
"The RCMP will continue to work diligently with our domestic and international law enforcement partners to prosecute online criminality," inspector Rafael Alvarado said in a statement.
Police noted that help from the Dutch National Police and the FBI were "essential" to the investigation.
Shared Accounts Increasingly Problematic for Critical Infrastructure: ICS-CERT
17.1.2018 securityweek ICS
Assessments conducted last year by the U.S. Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) showed that boundary protection remains the biggest problem in critical infrastructure organizations, but identification and authentication issues have become increasingly common.
Critical infrastructure owners and operators can ask ICS-CERT to conduct onsite cybersecurity assessments of their industrial control systems (ICS) in order to help them strengthen their cybersecurity posture.
In 2017, ICS-CERT conducted 176 assessments, which represents a 35 percent increase compared to the previous year. The agency analyzed organizations in eight critical infrastructure sectors, but more than two-thirds of the assessments targeted the energy and water and wastewater systems sectors.
The highest number of assessments were conducted in Texas (27), followed by Alaska (20), Nebraska (15), New York (14), Washington (13), Idaho (12), Nevada (10) and Arizona (10).
ICS-CERT identified 753 issues as part of 137 architecture design reviews and network traffic analyses. The six most common weaknesses, which accounted for roughly one-third of the total, were related to network boundary protection, identification and authentication, allocation of resources, physical access controls, account management, and least functionality.

Improper network boundary protection, which includes inadequate boundaries between enterprise and ICS networks and the inability to detect unauthorized activity on critical systems, has been the most common type of weakness since 2014.
As for identification and authentication issues, these can include the lack of mechanisms for tracing user actions if an account gets compromised, and increased difficulty in securing accounts belonging to former employees, particularly ones with administrator access.
Identification and authentication issues first made ICS-CERT’s top six weakness categories in 2015, when it was on the fourth position. In 2016 it jumped one position and last year it was the second most common security weakness.
Of all the identification and authentication issues, shared and group accounts are particularly concerning.
“[Shared and group accounts] make it difficult to identify the actual user and they allow malicious parties to use them with anonymity. Accounts used by a shared group of users typically have poor passwords that malicious actors can easily guess and that users do not change frequently or when a member of the group leaves,” ICS-CERT said in its latest Monitor report.
Allocation of resources for cybersecurity is also a problem in many critical infrastructure organizations. ICS-CERT’s assessment teams noticed that many sites are short-staffed and in many cases there is no backup personnel.
“Although some sites had started planning or attrition of staff, many did not have a plan to address loss of key personnel. One site had seven key personnel, four of whom would be eligible for retirement next year,” the agency said.
While its assessments do not focus on physical access controls, ICS-CERT has often noticed that organizations fail to ensure that ICS components are physically accessible only to authorized personnel.
“The team observed cases where infrastructure (i.e., routers and switches) was in company space but accessible to staff with no need to have physical access. Other cases included ICS components in public areas without any physical restrictions (i.e., locked doors or enclosures) to prevent access from a passerby. Some sites did not have locked doors to the operations plant, which would allow anyone to walk in and potentially have access to control system components,” ICS-CERT explained.
Flaws Allowed Facebook Account Hacking via Oculus App
17.1.2018 securityweek Social
Facebook recently patched a couple of vulnerabilities that could have been exploited by malicious hackers to hijack accounts by abusing integration with the Oculus virtual reality headset.
Facebook announced the acquisition of Oculus VR back in July 2014 and added Oculus assets to its bug bounty program a few weeks later. Several vulnerabilities have been found in Oculus services since, including a series of flaws that earned a researcher $25,000.
In October, web security consultant Josip Franjkoviæ decided to analyze the Oculus application for Windows, which includes social features that allow users to connect their Facebook account.
Franjkovic discovered that a malicious actor could have used specially crafted GraphQL queries to connect a targeted user’s Facebook account to the attacker’s Oculus account. GraphQL is a query language created by Facebook in 2012 and later released to the public.
According to the researcher, a specially crafted query allowed an attacker to obtain the victim’s access token, which under normal circumstances should not be accessible to third-party apps, and use it to take control of their Facebook account.
Franjkovic demonstrated an account takeover method by using a specially crafted query to add a new mobile phone number to the targeted account and then leveraging that number to reset the victim’s password.
The vulnerability was reported to Facebook on October 24 and a temporary fix, which involved disabling the facebook_login_sso endpoint, was implemented on the same day. A permanent patch was rolled out on October 30.
A few weeks later, the expert discovered a login cross-site request forgery (CSRF) flaw that could have been exploited to bypass Facebook’s patch.
This second flaw was reported to Facebook on November 18 and again the facebook_login_sso endpoint was disabled on the same day as a temporary fix. A complete patch was implemented roughly three weeks later.
The researcher has not disclosed the amount of money he earned from Facebook for finding the vulnerabilities, but he told SecurityWeek that the social media giant classified the issues as critical and he was happy with the reward he received.
Facebook revealed last week that it had paid a total of $880,000 in bug bounties in 2017, with an average of roughly $1,900 per submission.
Technical details for the vulnerabilities can be found on Franjkovic’s blog. In the past years, the expert reported several vulnerabilities to Facebook, including ones that could be exploited to hijack accounts.
BlackBerry Launches Security Product for Automotive, Other Industries
17.1.2018 securityweek IT
BlackBerry announced on Monday the launch of Jarvis, a new cybersecurity service designed to help companies in the automotive and other sectors find vulnerabilities in their software.
Jarvis has been described by BlackBerry as a cloud-based static binary code analysis software-as-a-service (SaaS) product. The tool is currently used by automakers, including Britain’s largest car maker, Jaguar Land Rover, but BlackBerry says it is ideal for other types of organizations as well, including in the healthcare, aerospace, defense, and industrial automation sectors.
Modern cars use hundreds of software components, including many provided by third-party vendors across several tiers. While this approach has some advantages, it also increases the chances of vulnerabilities making it into the software somewhere along the supply chain.BlackBerry launches Jarvis code scanning service
Jarvis aims to address this issue by scanning code and offering actionable information within minutes. In addition to finding vulnerabilities, the service also helps ensure compliance with various standards.
BlackBerry claims the new product performs tasks that would require a large number of experts and a lot of time, which should help companies save money. The tool can be integrated with existing development tools and APIs.
“Connected and autonomous vehicles require some of the most complex software ever developed, creating a significant challenge for automakers who must ensure the code complies with industry and manufacturer-specific standards while simultaneously battle-hardening a very large and tempting attack surface for cybercriminals,” said John Chen, executive chairman and CEO of BlackBerry.
“Jarvis is a game-changer for OEMs because for the first time they have a complete, consistent, and near real-time view into the security posture of a vehicle's entire code base along with the insights and deep learning needed to predict and fix vulnerabilities, ensure compliance, and remain a step ahead of bad actors,” Chen added.
Jarvis is an online tool that can be used by companies as a pay-as-you-go service. The product can be customized for each organization’s needs and their specific supply chain, allowing them to scan code at every stage of the development process.
Kaspersky Discovers Powerful Mobile Spyware
17.1.2018 securityweek Android
Kaspersky Lab has shared details of a sophisticated, multi-stage mobile spyware that gives attackers the ability to take over an infected Android device, with advanced features that have never been seen before in other mobile threats.
Named Skygofree, the mobile implant has been active since 2014 and has the ability to record nearby conversations and noise when an infected device enters a specified location.
Other advanced functions that have never been seen before include using Android’s Accessibility Services to access WhatsApp messages and the ability to connect an infected device to Wi-Fi networks controlled by the attackers.
“The implant carries multiple exploits for root access and is also capable of taking pictures and videos, seizing call records, SMS, geolocation, calendar events and business-related information stored in the device’s memory,” Kaspersky explained.
Furthermore, a special feature enables it to circumvent a battery-saving technique used on China-made Huawei devices by adding itself to the list of ‘protected apps’ so that it is not switched off automatically when the screen is off.
"Due to this feature, it is clear that the developers paid special attention to the work of the implant on Huawei devices," Kaspersky's researchers noted.
Designed for targeted cyber-surveillance, Kaspersky said the malware could be an offensive security product used for law enforcement purposes, similar to products offered by Hacking Team, a controversial Italy-based company that develops and sells surveillance technology to governments around the world.
Kaspersky did not provide statistics on the number of Android devices that may have been infected, but the number appears to be relatively small. There are “several infected individuals,” all located in Italy, Kaspersky said.
“Given the artefacts we discovered in the malware code and our analysis of the infrastructure, we have a high level of confidence that the developer behind the Skygofree implants is an Italian IT company that offers surveillance solutions, rather like HackingTeam,” said Alexey Firsh, Malware Analyst, Targeted Attacks Research, Kaspersky Lab.
The operators used spoofed landing pages that mimic the sites of mobile operators for spreading the implant, and Kaspersky’s researchers found 48 different commands that can be leveraged by the attackers.
Kaspersky provided technical analysis on Skygofree in an associated blog post, including an overview of the various commands, along with details on a number of modules that target computers running Microsoft Windows.
“High end mobile malware is very difficult to identify and block and the developers behind Skygofree have clearly used this to their advantage: creating and evolving an implant that can spy extensively on targets without arousing suspicion,” Firsh said.
The attacks are ongoing and the most recent domain was registered in October 2017.
North Korean Hackers Prep Attacks Against Cryptocurrency Exchanges: Report
17.1.2018 securityweek BigBrothers
Researchers Say a North Korea-Linked Hacking Campaign is Ready to Go Against South Korean Cryptocurrency Exchanges
North Korean hackers, loosely categorized as the Lazarus Group, have continued their attacks against South Korean interests, with particular emphasis on cryptocurrency exchanges.
Recorded Future has published details of a campaign it discovered in late 2017, which does not yet appear to be active. This may be in recognition of, or because of, the current discussions between North and South over North Korea's potential involvement in South Korea's Winter Olympics being held in Pyeongchang in February -- or it could simply be that the campaign development has not yet been put in action.
Recorded Future said they discovered a spear-phishing campaign that uses the CVE-2017-8291 Ghostscript vulnerability triggered from within a Hangul Word Processor (popular in South Korea) document.
For now, the bilateral discussions between North and South seem to be fruitful. It is reported that North Korea will send a 140-member orchestra to the Games, and there are ongoing discussions over the two countries fielding a joint women's hockey team. Nevertheless, Recorded Future researcher Priscilla Moriuchi told SecurityWeek that the campaign is in place and could be easily invoked.
Earlier this month, McAfee described a separate attack against North Korean defectors from a group -- almost certainly North Korean -- that does not appear to be related to any known cybercrime group.
Recorded Future notes that the techniques used in that attack "are unusual for the Lazarus Group. These include leveraging PowerShell, HTA, JavaScript, and Python, none of which are common in Lazarus operations over the last eight years." This new campaign, however, "showcases a clear use of Lazarus TTPs to target cryptocurrency exchanges and social institutions in South Korea."
The Lazarus targets are users of the Coinlink cryptocurrency exchange, other exchanges, and a group known as 'Friends of MOFA (Ministry of Foreign Affairs)'.
The cryptocurrency target is typical Lazarus. "Beginning in 2016," notes Recorded Future, "researchers discovered a shift in North Korean operations toward attacks against financial institutions designed to steal money and generate funds for the Kim regime." Lazarus is believed to be behind the 2016 attacks on the SWIFT global banking network, including the theft of $81 million from the Bangladesh central bank in February 2016.
In December 2017, the South Korean Youbit cryptocurrency exchange went bankrupt following its second hack of the year. In the first attack it lost 4000 bitcoin or around 40% of its reserves (around $5 million at the time), and a further 17% of its assets in the December breach. Some reports suggest that the attacks were undertaken by BlueNoroff, a sub-group of Lazarus.
South Korean exchanges have been strengthening their network defenses, while the government has been considering regulations to tighten control over cryptocurrencies. One mooted option has been the shutdown of all virtual cryptocurrency exchanges, although a statement from the Office for Government Policy Coordination on Monday downplayed a comment from Justice Minister Park Sang-ki last week. The Justice Minister's statement suggested the government is already working on legislation to ban virtual exchanges in the country. The current view is that a ban is not imminent, although stricter regulation is likely.
Whatever happens, hacking South Korean cryptocurrency exchanges will become more difficult in the future. "The majority of North Korean cryptocurrency operations have targeted South Korean users and exchanges, but we expect this trend to change in 2018. We assess that as South Korea responds to these attempted thefts by increasing security, they will become harder targets, forcing North Korean actors to look to exchanges and users in other countries as well."
Noticeably, Recorded Future warns that although this campaign and toolset are specific to the Hangul Word Processor, the actul vulnerability it exploits is not. "This vulnerability is for the Ghostscript suite and affects a wide range of products, and while this particular version is triggered from within an embedded PostScript in an HWP document, it could easily be adapted to other software."
"The main targets and victims of North Korean cryptocurrency operations in 2017 were South Korean," Moriuchi told SecurityWeek. "As a result of that targeting, the South Korean regulators are attempting to impose stricter financial controls on exchanges, and the exchanges are also implementing stricter security measures both for their users and within their networks. We believe that these factors will lead North Korea -- which is clearly invested in cryptocurrency operations -- to pursue other targets in other countries because the South Korean targets are becoming harder to get at."
This campaign is delivered by spear-phishing emails. Four separate lures have been identified: one aimed at users of Coinlink; two that appear to be resumes stolen from two genuine South Korean computer scientists who work at cryptocurrency exchanges; and one lifted from a blog run by the Friends of MOFA. All of the lure documents were created between mid-October and late November.
"This campaign relies on multiple payloads fashioned out of the Destover infostealer code to collect information about the victim system and exfiltrate files," reports Recorded Future. Destover further implicates Lazarus in the campaign. It was used in the Sony Pictures Entertainment attack in 2014, the Polish banking attacks in January 2017, and in the first WannaCry victim discovered by Symantec.
Recorded Future does not believe that any improving relations between North and South Korea will stop Lazarus targeting South Korea. The campaign could kick off at any time. But the suggestion is that as attacking South Korean exchanges becomes more difficult and less fruitful, the same attack could relatively easily be re-engineered for different exchanges in different countries.
Code Execution Flaw Found in Transmission BitTorrent App
17.1.2018 securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy has discovered a critical remote code execution vulnerability in the Transmission BitTorrent client. The expert has proposed a fix, but it has yet to be implemented by the application’s developers.
Transmission is a popular open source BitTorrent client that is available for Windows, Mac and Linux. Ormandy has been analyzing several popular torrent clients and found that Transmission has a serious vulnerability.
According to the researcher, an attacker can execute code on a system running Transmission by getting the targeted user to access a specially crafted website.
“The Transmission bittorrent client uses a client/server architecture, the user interface is the client and a daemon runs in the background managing the downloading, seeding, etc,” Ormandy explained in an advisory. “Clients interact with the daemon using JSON RPC requests to a web server listening on port 9091. By default, the daemon will only accept requests from localhost.”
However, the expert showed that the localhost requirement can be bypassed using a type of attack called “DNS rebinding.”
The attacker sets up a website and adds an iframe that points to a subdomain of that site. The DNS server is configured to respond alternatively with an address controlled by the attacker and localhost (127.0.0.1), with a short time to live (TTL). When the victim visits the malicious website, the browser resolves to the attacker-controlled DNS server and then switches to localhost.
“Exploitation is simple, you could set script-torrent-done-enabled and run any command, or set download-dir to /home/user/ and then upload a torrent for ‘.bashrc’,” Ormandy explained.
The expert says he has successfully tested his proof-of-concept (PoC) exploit with Chrome and Firefox running on Windows and Linux.
The vulnerability, tracked as CVE-2018-5702, was reported to Transmission developers on November 30, and Ormandy even provided a fix the next day. However, an official patch still has not been released, which the researcher says is highly unusual for open source projects.
Ormandy pressed the developers and last week they agreed to make his patch public on GitHub so that at least downstream distributions such as Debian and Fedora can roll out their own patches. It’s unclear when an official patch will become available, but it should be included in the next 2.93 release.
Transmission developers pointed out that the macOS and Linux versions are only vulnerable if remote access is enabled; the feature is disabled by default.
Sebastian Lekies, who also works for Google, said he reported the same vulnerability to Transmission developers five years ago, but never heard back from them.
Back in 2016, hackers broke into the Transmission website and planted a malicious installer designed to deliver a new OS X ransomware.
Mirai Variant Targets ARC CPU-Based Devices
17.1.2018 securityweek BotNet
A newly discovered variant of the Mirai Internet of Things (IoT) botnet is targeting devices with ARC (Argonaut RISC Core) embedded processors, researchers warn.
Dubbed Okiru, the new malware variant appears to be different from the Satori botnet, although the latter was also called Okiru by its author. Security researchers analyzing the new threat have discovered multiple differences between the two Mirai versions, aside from the targeting of the ARC architecture.
Originally designed by ARC International, the ARC processors are 32-bit CPUs widely used in system on chip (SOC) devices for storage, home, mobile, automotive, and IoT applications. Each year, over 1.5 billion devices are shipped with ARC processors inside.
Mirai Okiru represents the very first known malware targeting ARC processors, independent security researcher Odisseus, who analyzed the threat, notes.
The botnet was discovered by @unixfreaxjp from malwaremustdie.org, the security researcher who spotted the first Mirai variant in August 2016. In a post on reddit, the researcher explained that, although distributed denial of service (DDoS) is the main purpose of the last two Mirai versions, they are very different.
One of the characteristics that sets them apart is the configuration, which in Okiru is encrypted in two parts with telnet bombardment password encrypted. Satori doesn’t split it in two and doesn't encrypt brute default passwords either. Moreover, the new malware variant can use up to 114 credentials for telnet attack, while Satori uses a different and shorter database.
The researcher also explains that Okiru seems to lack the "TSource Engine Query" common Distributed "Reflective" (DRDoS) attack function via random UDP that Satori has. The two also have different infection follow up commands written in their configurations and show differences in usage of watchdog.
Okiru was found to have four types of router attack exploit code hard coded in it, none of which is found in Satori. Furthermore, there are small embedded ELF Trojan downloaders in Satori, which are used to download other architecture binaries (these were coded differently compared to Okiru ones).
Last week, when the researchers first noticed Okiru’s attacks, the malware enjoyed low detection in VirusTotal. Thus, and because the new threat is targeting devices that haven’t been hit by malware previously, researchers expect an uptick in Mirai infections.
It is also clear that the actor behind the botnet is actively following reports on the malware. Within minutes after ENISA (European Union Agency for Network and Information Security) Threat Landscape Stakeholder Group member Pierluigi Paganini wrote about Okiru, the website was hit with a DDoS attack that lasted over an hour, Italy’s CERT-PA revealed (translated).