OnePlus Site’s Payment System Reportedly Hacked to Steal Credit Card Details
17.1.2018 thehackernews CyberCrime

This year's first bad news for OnePlus users—a large number of OnePlus customers are reporting of fraudulent credit card transactions after buying products from the Chinese smartphone manufacturer's official online store.
The claim initially surfaced on the OnePlus support forum over the weekend from a customer who said that two of his credit cards used on the company's official website was suspected of fraudulent activities.
"The only place that both of those credit cards had been used in the last 6 months was on the Oneplus website," the customer wrote.
Later a good number of users posted similar complaints on OnePlus, Twitter and Reddit forums, saying they also became a victim of credit card fraud.
Many of the customers claimed that their credit cards had been compromised after they bought a new phone or some accessories directly from the OnePlus official website, indicating that the leak might have been through the company itself.
Cybersecurity firm Fidus also published a blog post detailing the alleged issue with the OnePlus website's on-site payment system. The firm suspected that the servers of the OnePlus website might have been compromised.
According to Fidus, OnePlus is currently conducting the transactions itself on-site, which means that all billing information along with all credit card details entered by its customers flow through the OnePlus official website and can be intercepted by attackers.
"Whilst the payment details are sent off to a third-party provider upon form submission, there is a window in which malicious code is able to siphon credit card details before the data is encrypted," Fidus wrote.
Fidus went on to clarify that their findings did not in any way confirm that the OnePlus website was breached; instead, they suggested the attacks might have come from the Magento eCommerce platform—which is used by OnePlus and is "a common platform in which credit card hacking takes place."
OnePlus has quickly responded to the issue on its forum, confirming that it does not store any credit card information on its website and all payment transactions are carried out through its PCI-DSS-compliant payment processing partner.
Only credit card-related information of users who have enabled the "save this card for future transactions" feature is stored on OnePlus' official servers, but even they are secured with a token mechanism.
"Our website is HTTPS encrypted, so it's very difficult to intercept traffic and inject malicious code, however we are conducting a complete audit," a company's staffer using the name 'Mingyu' wrote.
The Chinese smartphone maker also confirms that purchases involving third-party services like PayPal are not affected.
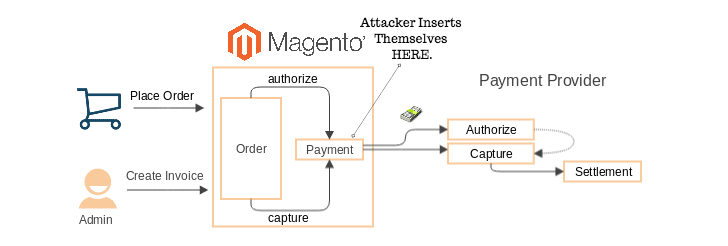
OnePlus does not reveal much information on the incident but confirms that its official website is not affected by any Magento vulnerability.
The company confirms that oneplus.net was indeed built on the Magento eCommerce, but said since 2014, it has entirely been re-built using custom code, adding that "credit card payments were never implemented in Magento's payment module at all."
There are almost 100 claims of fraudulent credit card transactions on the OnePlus support forums. OnePlus announces a formal investigation into the matter, and advises affected users to contact their bank to reverse the payment.
Flaw in Popular Transmission BitTorrent Client Lets Hackers Control Your PC Remotely
17.1.2018 thehackernews Virus
A critical vulnerability has been discovered in the widely used Transmission BitTorrent app that could allow hackers to remotely execute malicious code on BitTorrent users' computers and take control of them.
The vulnerability has been uncovered by Google's Project Zero vulnerability reporting team, and one of its researchers Tavis Ormandy has also posted a proof-of-concept attack—just 40 days after the initial report.
Usually, Project Zero team discloses vulnerabilities either after 90 days of reporting them to the affected vendors or until the vendor has released a patch.
However, in this case, the Project Zero researchers disclosed the vulnerability 50 days prior to the actual time limit because Transmission developers failed to apply a ready-made patch provided by the researchers over a month ago.
"I'm finding it frustrating that the transmission developers are not responding on their private security list, I suggested moving this into the open so that distributions can apply the patch independently. I suspect they won't reply, but let's see," Ormandy said in a public report published Tuesday.
Proof-of-Concept Exploit Made Publicly Available
The PoC attack published by Ormandy exploits a specific Transmission function that lets users control the BitTorrent app with their web browser.
Ormandy confirmed his exploit works on Chrome and Firefox on Windows and Linux (Fedora and Ubuntu) and believes that other browsers and platforms are also vulnerable to the attack.
Transmission BitTorrent app works on server-client architecture, where users have to install a daemon service on their systems in order to access a web-based interface on their browsers locally.
The daemon installed on the user system then interacts with the server for downloading and uploading files through the browser using JSON RPC requests.
Ormandy found that a hacking technique called the "domain name system rebinding" attack could successfully exploit this implementation, allowing any malicious website that user visits to execute malicious code on user's computer remotely with the help of installed daemon service.
Here's How the Attack Works:
The loophole resides in the fact that services installed on localhost can be manipulated to interact with third-party websites.
"I regularly encounter users who do not accept that websites can access services on localhost or their intranet," Ormandy wrote in a separate post, which includes the patch.
"These users understand that services bound to localhost are only accessible to software running on the local machine and that their browser is running on the local machine—but somehow believe that accessing a website "transfers" execution somewhere else. It does not work like that, but this is a common source of confusion."
Attackers can exploit this loophole by simply creating a DNS name they're authorized to communicate with and then making it resolve to the vulnerable computer's localhost name. Here's how the attack works:
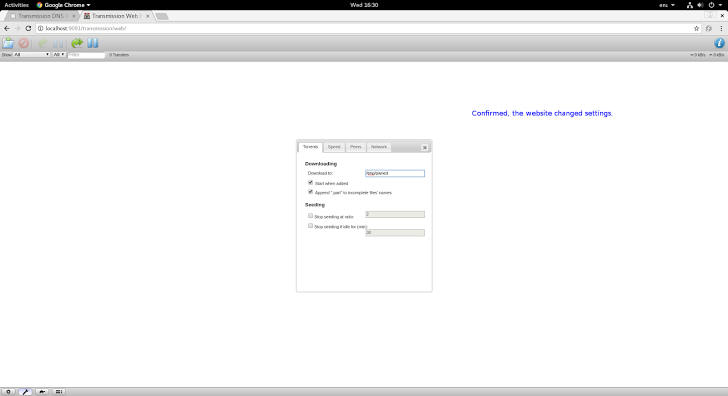
A user visits malicious site (http://attacker.com), which has an iframe to a subdomain controlled by the attacker.
The attacker configures their DNS server to respond alternately with 127.0.0.1 and 123.123.123.123 (an address controlled by the attacker) with a very low TTL.
When the browser resolves to 123.123.123.123, it serves HTML that waits for the DNS entry to expire (or force it to terminate by flooding the cache with lookups), then it has permission to read and set headers.
Ormandy said the vulnerability (CVE-2018-5702) was the "first of a few remote code execution flaws in various popular torrent clients," though he did not name the other torrent apps due to the 90-day disclosure timeline.
A fix is expected to be released as soon as possible, a development official with Transmission told ArsTechnica, without specifying an actual date.
LeakedSource Founder Arrested for Selling 3 Billion Stolen Credentials
17.1.2018 thehackernews CyberCrime

Canadian authorities have arrested and charged an Ontario man for operating a website that collected 'stolen' personal identity records and credentials from some three billion online accounts and sold them for profit.
According to the Royal Canadian Mounted Police (RCMP), the 27-year-old Jordan Evan Bloom of Thornhill is the person behind the notorious LeakedSource.com—a major repository that compiled public data breaches and sold access to the data, including plaintext passwords.
Launched in late 2015, LeakedSource had collected around 3 billion personal identity records and associated passwords from some of the massive data breaches, including LinkedIn, VK.com, Last.Fm, Ashley Madison, MySpace, Twitter, Weebly and Foursquare, and made them accessible and searchable to anyone for a fee.
LeakedSource was shut down, and its associated social media accounts have been suspended after the law enforcement raided its operator earlier last year.
However, another website with the same domain name hosted by servers in Russia is still in operation.
Bloom is accused of operating the notorious website and claimed to have earned nearly US$200,000 by selling stolen personal identity records and associated passwords for a "small fee" via his site.
Appeared in a Toronto court on Monday, January 15, Bloom charged with trafficking in identity information, mischief to data, unauthorised use of a computer, and possession of property obtained by crime, the RCMP said.
"This investigation is related to claims about a website operator alleged to have made hundreds of thousands of dollars selling personal information," the RCMP Cybercrime Investigative Team said in a statement.
"The RCMP will continue to work diligently with our domestic and international law enforcement partners to prosecute online criminality."
Bloom was arrested and charged on December 22, 2017, as part of the RCMP's national cybercrime division investigation, dubbed 'Project Adoration.'
The RCMP said the Dutch national police and the United States' FBI assisted in the operation, adding the case could not have been cracked without international collaboration.
Bloom is currently in custody and due back in court on February 16.
Cybersecurity lawyer Imran Ahmad told Reuters that Bloom could face a maximum sentence 10 years in prison.
New Intel AMT Security Issue Lets Hackers Gain Full Control of Laptops in 30 Seconds
17.1.2018 thehackernews Attack

It's been a terrible new-year-starting for Intel.
Researchers warn of a new attack which can be carried out in less than 30 seconds and potentially affects millions of laptops globally.
As Intel was rushing to roll out patches for Meltdown and Spectre vulnerabilities, security researchers have discovered a new critical security flaw in Intel hardware that could allow hackers to access corporate laptops remotely.
Finnish cyber security firm F-Secure reported unsafe and misleading default behaviour within Intel Active Management Technology (AMT) that could allow an attacker to bypass login processes and take complete control over a user's device in less than 30 seconds.
AMT is a feature that comes with Intel-based chipsets to enhance the ability of IT administrators and managed service providers for better controlling their device fleets, allowing them to remotely manage and repair PCs, workstations, and servers in their organisation.
The bug allows anyone with physical access to the affected laptop to bypass the need to enter login credentials—including user, BIOS and BitLocker passwords and TPM pin codes—enabling remote administration for post-exploitation.
In general, setting a BIOS password prevents an unauthorised user from booting up the device or making changes to the boot-up process. But this is not the case here.
The password doesn't prevent unauthorised access to the AMT BIOS extension, thus allowing attackers access to configure AMT and making remote exploitation possible.
Although researchers have discovered some severe AMT vulnerabilities in the past, the recently discovered issue is of particular concern because it is:
easy to exploit without a single line of code,
affects most Intel corporate laptops, and
could enable attackers to gain remote access to the affected system for later exploitation.
"The attack is almost deceptively simple to enact, but it has incredible destructive potential," said F-Secure senior security researcher Harry Sintonen, who discovered the issue in July last year.
"In practice, it can give a local attacker complete control over an individual’s work laptop, despite even the most extensive security measures."
According to the researchers, the newly discovered bug has nothing to do with the Spectre and Meltdown vulnerabilities recently found in the microchips used in almost all PCs, laptops, smartphones and tablets today.
To exploit this issue, all an attacker with physical access to a password (login and BIOS) protected machine needs to do is reboot or power-up the targeted PC and press CTRL-P during boot-up, as demonstrated by researchers at F-Secure in the above video.
The attacker then can log into Intel Management Engine BIOS Extension (MEBx) with a default password.
Here, the default password for MEBx is "admin," which most likely remains unchanged on most corporate laptops.
Once logged in, the attacker can then change the default password and enable remote access, and even set AMT's user opt-in to "None."
Now, since the attacker has backdoored the machine efficiently, he/she can access the system remotely by connecting to the same wireless or wired network as the victim.
Although exploiting the issue requires physical access, Sintonen explained that the speed and time at which it can be carried out makes it easily exploitable, adding that even one minute of a distraction of a target from its laptop is enough to do the damage.
"Attackers have identified and located a target they wish to exploit. They approach the target in a public place—an airport, a café or a hotel lobby—and engage in an 'evil maid' scenario," Sintonen says.
"Essentially, one attacker distracts the mark, while the other briefly gains access to his or her laptop. The attack doesn't require a lot of time—the whole operation can take well under a minute to complete."
Along with CERT-Coordination Center in the United States, F-Secure has notified Intel and all relevant device manufacturers about the security issue and urged them to address it urgently.
Meanwhile, users and IT administrators in an organisation are recommended to change the default AMT password of their device to a strong one or disable AMT if this option is available, and never leave their laptop or PC unattended in a public place.
Skype Finally Adds End-to-End Encryption for Private Conversations
17.1.2018 thehackernews Social

Good news for Skype users who are concerned about their privacy.
Microsoft is collaborating with popular encrypted communication company Signal to bring end-to-end encryption support to Skype messenger.
End-to-end encryption assured its users that no one, not even the company or server that transmits the data, can decrypt their messages.
Signal Protocol is an open source cryptographic protocol that has become an industry-wide standard—which is used in Facebook Messenger, Whatsapp, and Google Allo for secure messaging.
Dubbed Private Conversations, the new feature which is about to be introduced in Skype will offer end-to-end encryption for audio calls, text, and multimedia messages like videos and audio files.
"Skype Private Conversations give you enhanced security through end-to-end encryption with an additional layer of security for conversations between you and your friends and family," the company announced.
"Private Conversations can only be between you and one other contact. This is not supported in groups."
How to Start Skype End-to-End Encrypted Calls and Chats
Private Conversations is already available to the Skype Insider program—a platform that allows Skype users to test new features before they rolled out to the rest of its over 300 million of users worldwide.
To initiate a new secure communication with your Skype contact, you need to tap or click on the (+) icon, select 'New Private Conversation' and then select the contact you would like to start the secure communication with.
A Private Conversation will have a lock icon next to your Skype contact's name. Preview messages from Private Conversations will not appear in the chat list or notifications.
Unlike WhatsApp, end-to-end encryption feature is not enabled by default in Skype and users need to select 'New Private Conversation' from the app's "Compose" menu, or from another user's profile to initiate a secure communication—it's like Facebook Messenger's Secret Conversations, which is also based on of Signal.
Unfortunately, Private Conversations also doesn't currently support video calling, but this is secured by the standard encryption that Microsoft already provides with its Skype service.
Also, even with Private Conversations enabled, Skype will still be able to access some information (metadata) about your secure communications, like when you initiate them, and how long the conversation last.
Skype Insider users can test Private Conversations using Skype build version 8.13.76.8 for iOS, Android, Linux, Mac, and Windows Desktop.
How to hack Facebook accounts exploiting CSRF in Oculus app
17.1.2018 securityaffairs Social
Facebook has fixed a couple of vulnerabilities that could have been exploited by attackers to hijack accounts by abusing integration with the Oculus virtual reality headset.
In March 2014, Facebook founder Mark Zuckerberg announced the acquisition of Oculus VR and included the handsets produced by the company to its bug bounty program.
White hat hackers discovered several vulnerabilities in Oculus platform since, including the ones addressed now by Facebook.
The flaws were reported in October by the security consultant Josip Franjković who analyzed the Oculus application for Windows.
“Oculus enables users to connect their Facebook accounts for a more “social” experience. This can be done using both the native Windows Oculus application and using browsers.” wrote Franjković. “I took a deeper look at the native Windows flow, and found a CSRF vulnerability which allowed me to connect a victim’s Facebook account to attacker’s Oculus account. Once connected, the attacker could extract the victim’s access token, and use Facebook’s GraphQL queries to take over the account.”

One of the features implemented by the Oculus application is the authentication to a Facebook account, Franjkovic discovered that attackers could have exploited specially crafted GraphQL queries to connect any user’s Facebook account to their Oculus account.
GraphQL is a query language created by Facebook in 2012 for describing the capabilities and requirements of data models for client‐server applications, a GraphQL query is a string that is sent to a server to be interpreted and fulfilled, which then returns JSON back to the client.
Franjkovic discovered that a specially crafted query allowed an attacker to obtain the victim’s access token and use it to impersonate the victim by accessing his account.
In a proof of concept attack, Franjkovic shows how to use a specially crafted query to add a new mobile phone number to the targeted account and use it to reset the victim’s password.
The vulnerability was reported to Facebook on October 24, the social network giant temporary solved the issue by disabling the facebook_login_sso endpoint.
On October 30, Facebook rolled out a patch to address definitively the problem, but a few weeks later, the expert discovered a login cross-site request forgery (CSRF) flaw that could have been exploited to bypass Facebook’s patch.
The experts informed Facebook on November 18 that disabled again the facebook_login_sso endpoint to mitigate the problem. A complete patch was rolled out after a few weeks.
Facebook paid the expert for his discoveries and classified the vulnerabilities as critical.
Step by step procedure exploited by the researcher is described on its blog, below the timeline of the hack:
24th of October, 2017, 03:20 – Report sent to Facebook
24th of October, 2017, 10:50 – First reply from Facebook
24th of October, 2017, 11:30 – Temporary fix for the bug (disabled /facebook_login_sso/ endpoint)
30th of October, 2017 – Bug is now fixed.
Game of Drones – Researchers devised a technique to detect drone surveillance
17.1.2018 securityaffairs IT
A group of Israeli researchers at Ben Gurion University have built a proof-of-concept system against surveillance operated a surveillance drone.
Drones have created a new threat to people’s privacy. Anyone with a drone equipped with a video camera can potentially violate our privacy by streaming the subject in his/her private space over an encrypted first person view (FPV) channel.
Experts suggested many methods to detect nearby drones, but they all suffer from the same shortcoming: they cannot identify exactly what is being captured, and therefore they fail to distinguish between the legitimate use of a drone (for example, to use a drone to film a selfie from the air) and illegitimate use that invades someone’s privacy (when the same operator uses the drone to stream the view into the window of his neighbor’s apartment), a distinction that in some cases depends on the orientation of the drone’s video camera rather than on the drone’s location.
A group of Israeli researchers at Ben Gurion University in Beer Sheva (Ben Nassi, Raz Ben-Netanel, Adi Shamir, Yuval Elovici) have built a proof-of-concept system against surveillance operated with spying drones that is able to determine whether a certain person or object is under drone surveillance.
The system first generates a recognizable pattern on whatever subject someone might want to guard spy on with aerial surveillance, then researchers remotely intercept a drone’s radio signals and scan the streaming video the drone sends to the operator scanning for that pattern.
“In this paper, we shatter the commonly held belief that the use of encryption to secure an FPV channel prevents an interceptor from extracting the POI that is being streamed. We show methods that leverage physical stimuli to detect whether the drone’s camera is directed towards a target in real time.” wrote the researchers,
“We investigate the influence of changing pixels on the FPV channel (in a lab setup). Based on our observations we demonstrate how an interceptor can perform a side-channel attack to detect whether a target is being streamed by analyzing the encrypted FPV channel that is transmitted from a real drone (DJI Mavic) in two use cases: when the target is a private house and when the target is a subject.”
The experts leverage the “delta frames” technique, instead of encoding video as a series of raw images, it’s compressed into a series of changes from the previous image in the video. A streaming video related to a still object contains fewer bytes of data compared with a streaming video of an object in motion or images that continuously change color.
That compression feature can reveal key information about the content of the video to someone who’s intercepting the streaming data, the technique works even when data is encrypted.
The Ben Gurion researchers used in the tests a “smart film” to toggle the opacity of several panes of a house’s windows. They used a DJI Mavic quadcopter to spy on the house, they demonstrated that the technique was able to detect the changing from opaque to transparent and back again of the panes. Then they used a parabolic antenna and a laptop to intercept the drone’s radio signals sent back to the operator and search the pattern in the encrypted data stream to detect if the UAV was used for aerial surveillance of the house.

“In another test, they put blinking LED lights on a test subject’s shirt, and then were able to pull out the binary code for “SOS” from an encrypted video focused on the person, showing that they could even potentially “watermark” a drone’s video feed to prove that it spied on a specific person or building.” reported Wired.
But Nassi confirmed that their technique works at ranges where it’s very difficult to spot a surveillance drone in the sky, the researchers tested their technique from a range of about 150 feet. The range is scalable by using a more powerful antenna.
Mobile App Flaws of SCADA ICS Systems Could Allow Hackers To Target Critical Infrastructe
17.1.2018 securityaffairs ICS
IOACTIVE researchers warn that critical infrastructure mobile applications are being developed without secure coding compliance that could allow hackers to target SCADA Systems.
In a report released today, by IOACTIVE, researchers’ advice that critical infrastructure mobile applications are being developed without secure coding compliance that could allow hackers to target Supervisory Control and Data Acquisition Industrial Control Systems.
SCADA-ICS stands for Supervisory Control and Data Acquisition Industrial Control System, that represents the industrial automated systems operating on critical infrastructure. These systems are responsible for the control and operation of critical services like clean water and energy respectively. Researchers of IOACTIVE released a report analyzing the impact on the security of SCADA-ICS systems operating connected to the internet of things (IoT) and mobile applications.
The report states that mobile applications are present in many ICS segments and can be divided into two groups, Local (Wi-Fi, Bluetooth) and remote applications (Internet, VPN), which are exposed to three types of attacks such as Unauthorized physical access to the device or “virtual” access to device data, Communication channel compromise (MiTM), Application compromise.

Considering these attacks mobile SCADA applications can lead to Directly/indirectly influencing an industrial process or industrial network infrastructure and compromising an operator to unwillingly perform a harmful action on the system.
The research was conducted based on OWASP 2016 and analyzed 34 vendors that released the app on Google Play Store. The mobile app analyzed revealed that 147 security issues were identified related to secure coding programming that would allow code tampering.
The researchers noticed that hackers could gain remote control to smartphones to further launch attacks on ICS vulnerable app used on hardware and software. Also, the researchers pointed out that there was an increase of 16 vulnerabilities per application.
Regarding the vulnerabilities, researchers found out that insecure authorization was present with some apps failing to include any form of authentication. Other vulnerabilities live reverse engineering were present due to the absence of code obfuscation. insecure data storage and unintended data leakage were present which could allow hackers to access the app or data related to ‘Supervisory Control And Data Acquisition’ system.
The security of society is at stake since these new vulnerabilities pose a great threat, even more than the damage caused by the 2016 Ukrainian attack. The report recommends to app developers to consider secure coding in the development planning due to the impacts on society that these flaws represent.
New MaMi Malware targets macOS systems and changes DNS settings
17.1.2018 securityaffairs Apple
The popular security researcher Patrick Wardle spotted MaMi malware, a new threat malware designed to hijack DNS settings on macOS devices.
The cyber security expert and former NSA hacker Patrick Wardle made the headline once again, this time the researcher has spotted a new strain of malware dubbed MaMi designed to hijack DNS settings on macOS devices.
Wardle first obtained a sample of the MaMi malware after a user reported on the Malwarebytes forums that the Mac of its teacher was infected by a malware that set DNS servers to 82.163.143.135 and 82.163.142.137.

At the time of its discovery, it was undetected by all engines on VirusTotal. The OSX/MaMi isn’t particularly advanced, but the researcher remarked that it does alter infected systems in rather nasty and persistent ways.
“Since there are already several (IMHO unrelated) malware specimens that perform DNS hijackering (that are named ‘DNSChanger’, etc), I decided to call is OSX/MaMi due to a core class the malware named: ‘SBMaMiSettings’ ” wrote Wardle.
“Ok, that’s a wrap. OSX/MaMi isn’t particular advanced – but does alter infected systems in rather nasty and persistent ways. By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle’ing traffic (perhaps to steal credentials, or inject ads). “
The malicious code acts as a DNS hijacker, but it also implements other features for taking screenshots, simulating mouse events, downloading and uploading files, and executing commands.
The researcher discovered the malware on several websites, unfortunately, it was not able to determine the distribution channel. It is likely the MaMi malware has been delivered via email, fake security alerts and pop-ups on websites, or social engineering attacks.
Wardle noticed that the malware does not appear to execute any of implement feature, likely because it requires some attacker-supplied input or other preconditions that were not simulated in the virtualized test lab used by the expert.
Once MaMi has infected a mac system, it invokes the security tool and uses it to install a new certificate (dcdata.bin) it’s downloaded from the internet.
“By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle’ing traffic (perhaps to steal credentials, or inject ads).” explained Wardle.
How to discover is a macOS system is infected with the MaMi malware?
Users can check DNS settings, the malicious code set DNS servers to 82.163.143.135 and 82.163.142.137.
Patrick Wardle also created a free open-source firewall for macOS named ‘LuLu,’ which is able to block suspicious traffic and neutralize OSX/MaMi’s.
MaMi isn’t only one of the DNS-changer malware discovered since today, the most popular malware with these characteristics is DNSChanger, a threat that targeted both Windows and OS X machines, infecting millions of devices worldwide.
Fappening – A fourth man has been charged with hacking into over 250 Apple iCloud accounts belonging to celebrities
17.1.2018 securityaffairs Apple
Fappening – A fourth hacker, George Garofano (26), of North Branford, has been charged with hacking into over 250 Apple iCloud accounts belonging to celebrities.
A fourth hacker, George Garofano (26), of North Branford, has been charged with hacking into over 250 Apple iCloud accounts belonging to celebrities.
Garofano had been arrested by the FBI and a federal court has accused him of violating the Computer Fraud and Abuse Act.
From April 2013 through October 2014, Garofano used phishing attacks against the victims to obtain their iCloud accounts credentials, access the accounts and steal personal information, including private photographs and videos.
“According to the plea agreement, from April 2013 through October 2014, Garofano engaged in a phishing scheme to obtain usernames and passwords for iCloud accounts. Garofano admitted that he sent e-mails to victims that appeared to be from security accounts of Apple and encouraged the victims to send him their usernames and passwords, or to enter them on a third-party website, where he would later retrieve them.” reads the press release published by the DoJ.
“Garofano used the usernames and passwords to illegally access his victims’ iCloud accounts, which allowed him to steal personal information, including sensitive and private photographs and videos, according to his plea agreement. In some instances, Garofano traded the usernames and passwords, as well as the materials he stole from the victims, with other individuals.”
As part of the Fappening case, nude pictures of many celebrities were leaked online, the list of victims is long and includes Kim Kardashian, Kate Upton, and Jennifer Lawrence.
Garofano also traded the stolen credentials, as well as the information he stole from the victims’ accounts, with other individuals.
In a plea agreement signed last week in U.S. District Court in Los Angeles, Garofano agreed to plead guilty to one count of unauthorized access to a protected computer to obtain information.
The man is now facing up to 5 years in federal prison.

Garofano is the fourth man charged in connection with the Fappening saga, in past months Emilio Herrera, Edward Majerczyk, Ryan Collins, pleaded guilty to being involved in the attacks on the celebrities’ iCloud accounts.
Collins was sentenced to 18 months in federal prison, Majerczyk to nine months and Herrera is waiting for sentencing next month.
Lenovo spotted and fixed a backdoor in RackSwitch and BladeCenter networking switches
17.1.2018 securityaffairs Vulnerebility
Lenovo discovered a firmware backdoor in RackSwitch and BladeCenter networking switch families during an internal security audit.
Security experts at Levono have spotted a firmware backdoor, tracked CVE-2017-3765, in RackSwitch and BladeCenter networking switch families during an internal security audit.
An authentication bypass affects only in RackSwitch and BladeCenter switches running ENOS (Enterprise Network Operating System), the tech giant promptly addressed it with firmware updates last week.
The Enterprise Network Operating System (ENOS) is the firmware that powers some Lenovo and IBM RackSwitch and BladeCenter switches.
According to the security advisory published by Lenovo, the backdoor (dubbed “HP backdoor”) was added to ENOS in 2004 when ENOS was owned by Nortel’s Blade Server Switch Business Unit.
The backdoor was intentionally inserted by Nortel that added it at the request of a BSSBU OEM customer.
“An authentication bypass mechanism known as “HP Backdoor” was discovered during a Lenovo security audit in the Telnet and Serial Console management interfaces, as well as the SSH and Web management interfaces under certain limited and unlikely conditions.” states the security advisory.
“A source code revision history audit revealed that this authentication bypass mechanism was added in 2004 when ENOS was owned by Nortel’s Blade Server Switch Business Unit (BSSBU). The mechanism was authorized by Nortel and added at the request of a BSSBU OEM customer.”
The backdoor was never removed from the firmware even after three acquisitions of the unit. Nortel spun BSSBU off in 2006 as BLADE Network Technologies (BNT), IBM acquired BNT in 2010, and Lenovo bought IBM’s BNT portfolio in 2014 … but the HP backdoor was never removed.
This bypass mechanism can be accessed when performing local authentication under specific circumstances using credentials that are unique to each switch. the exploitation of the backdoor could grant the attacker admin-level access.
Below the list of ENOS interfaces and authentication configurations affected by the issue:
Telnet and Serial Console when performing local authentication, or a combination of RADIUS, TACACS+, or LDAP and local authentication under specific circumstances described below
Web when performing a combination of RADIUS or TACACS+ and local authentication combined with an unlikely condition under specific circumstances described below
SSH for certain firmware released in May 2004 through June 2004 (only) when performing a combination of RADIUS or TACACS+ and local authentication under specific circumstances described below; the vulnerable code is present in more recent firmware, but not used

Lenovo has provided the firmware source code to a third-party security partner to enable independent investigation of the issue, the company declined any responsibility and expressed its disappointment for the presence of the backdoor:
“The existence of mechanisms that bypass authentication or authorization are unacceptable to Lenovo and do not follow Lenovo product security or industry practices. Lenovo has removed this mechanism from the ENOS source code and has released updated firmware for affected products.” continues the advisory
“Lenovo is not aware of this mechanism being exploited, but we assume that its existence is known, and customers are advised to upgrade to firmware which eliminates it.”
Lenovo released firmware updates for both newer and older (IBM-branded) RackSwitch and BladeCenter networking switch families.
The full list of impacted switches and associated links for the latest firmware were included in the advisory.
Lenovo confirmed that the backdoor doesn’t affect the switches running CNOS (Cloud Network Operating System).
Mirai Okiru botnet targets for first time ever in the history ARC-based IoT devices
17.1.2018 securityaffairs BotNet
Researcher @unixfreaxjp spotted the first time ever in the history of computer engineering a Linux malware designed to infect ARC CPU, this new Linux ELF malware was dubbed MIRAI OKIRU.
In August 2016 the researcher @unixfreaxjp from @MalwareMustDie team first spotted the dreaded Mirai botnet, now the same researcher is announcing a new big earthquake in the malware community.
unixfreaxjp spotted the first time ever in the history of computer engineering a Linux malware designed to infect ARC CPU, this new Linux ELF malware was dubbed MIRAI OKIRU.
This is the first time that a malware specifically targets ARC-based systems, the Mirai Okiru was undetected by almost all the antivirus engines at the time of its discovery.

“!! Please be noted of this fact, and be ready for the bigger impact on infection Mirai (specially Okiru) to devices that hasn’t been infected yet.” said #MalwareMustDie
The Linux IoT threat landscape is rapidly changing, crooks will start targeting IoT devices based on ARC CPU.
“From this day, the landscape of #Linux #IoT infection will change. #ARC cpu has produced #IoT dervices more than 1 billion per year. So these devices are what the hackers want to aim to infect #ELF #malware with their #DDoS cannons. It’s a serious threat will be. #MalwareMustDie!” wrote MMD.
As highlighted by the colleague the impact of such botnet could be devastating, it has been estimated that ARC embedded processors are shipped in more than 1.5 billion products per year. This means that the number of the potentially exposed devices is enormous, and a so powerful botnet could be used for a multitude of malicious purposes.
“ARC (Argonaut RISC Core) embedded processors are a family of 32-bit CPUs originally designed by ARC International. They are widely used in SoC devices for storage, home, mobile, automotive, and Internet of Things applications. ARC processors have been licensed by more than 200 organizations and are shipped in more than 1.5 billion products per year.” reads Wikipedia.
View image on TwitterView image on Twitter
@_odisseus
This is the FIRST TIME ever in the history of computer engineering that there is a malware for ARC CPU, & it is #MIRAI OKIRU!!
Pls be noted of this fact, & be ready for the bigger impact on infection Mirai (specially #Okiru) to devices hasn't been infected yet.#MalwareMustDie
9:40 PM - Jan 14, 2018
13 13 Replies 324 324 Retweets 295 295 likes
Twitter Ads info and privacy
“#Mirai #Okiru variant is very dangerous, if you see how the coder made specific “innovative modification” in its variant codes+encryption you’ll see what I mean, & now they are the 1st malware to aim #ARC core. These guys can make greater chaos if not be stopped. Mark my word” wrote MalwareMustDie.
It is very important to understand that the Mirai Satori variant is very different from Okiru as explained by MalwareDustdie.
“From what we observe so far. these two types are very different, (among of several common similar characteristic), we think it is good to have different rules to detect Mirai variant Okiru and Satori
Some simple highlights to differ Okiru to Satori variant:
The config is different, Okiru variant’s config is encrypted in two parts w/ telnet bombardment password encrypted, Satori does not split it in 2parts and doesn’t encrypt brute default passwords. Also Okiru’s telnet attack login information is a bit longer (can be up to 114 credentials, max counted), while Satori is having different and shorter database.
Satori seem to have “TSource Engine Query” common Distributed “Reflective” (DRDoS) attack function via random UDP, while Okiru does not seem to have this function,
The infection follow up commands written in both Okiru and Satori in their configurations are a bit different, showing possibility that they don’t seem sharing a same “herding environment”,
(up to) Four types of router attack exploit code has only being spotted hard coded in Okiru variant, yet Satori does not use these exploits at all,
Satori (see VT comment part for reversed code) is using small embedded ELF trojan downloaders to download other architecture binaries which were coded differently compared to Okiru ones (see reversed code is in VT comment),
(there are more minors stuff too that you can notice using the pictures shown in previous points, like differences in usage of watchdog, the usage of command “echo -en \x…” etc)
” wrote MalwareMustDie.
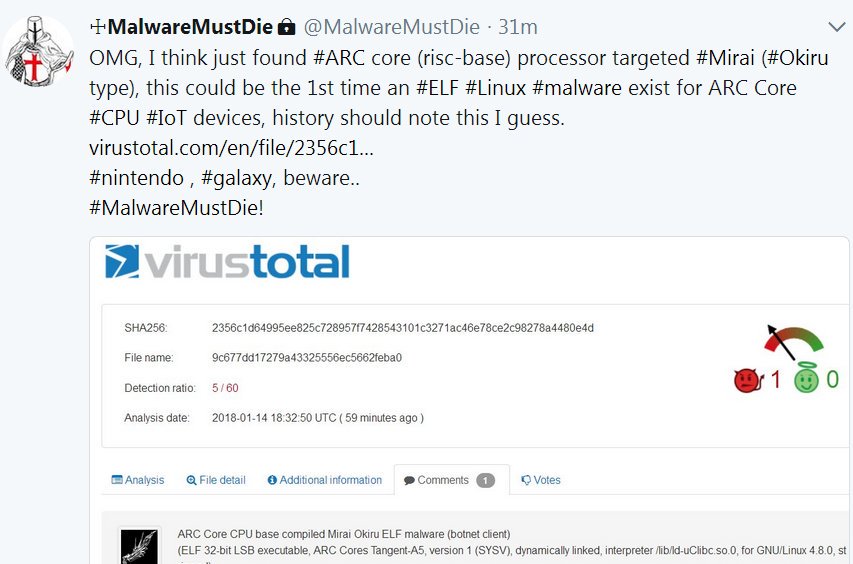
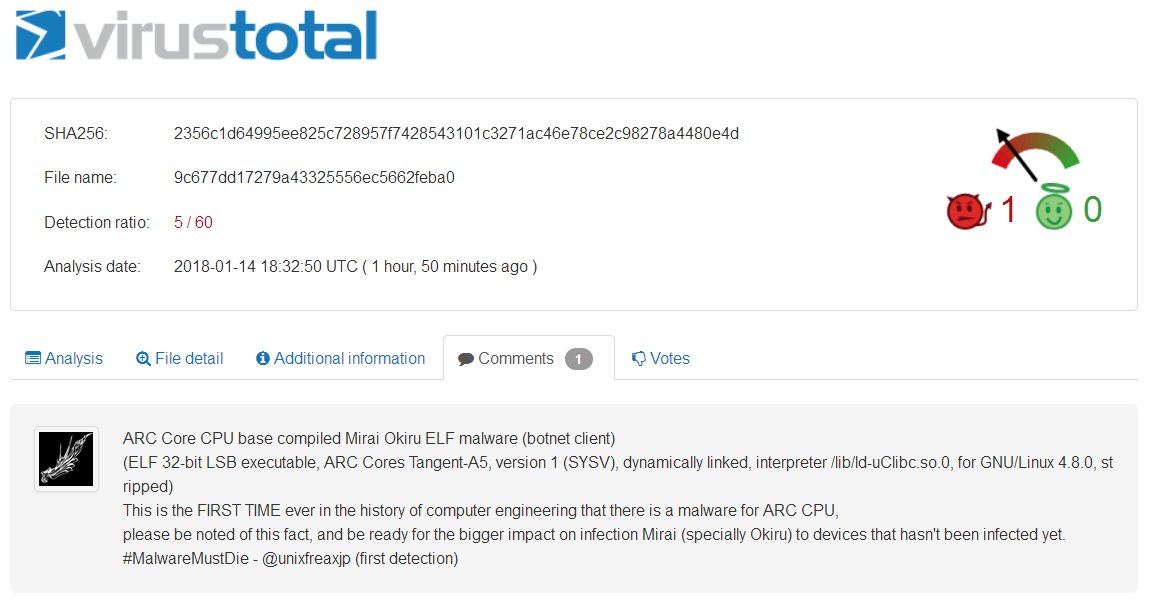
ARC Core CPU base compiled Mirai Okiru ELF malware (botnet client) (ELF 32-bit LSB executable, ARC Cores Tangent-A5, version 1 (SYSV), dynamically linked, interpreter /lib/ld-uClibc.so.0, for GNU/Linux 4.8.0, stripped).
The risk that someone could build a powerful Mirai Okiru botnet composed of a billion device is concrete.
Researchers from MalwareMustDie published the Yara rules for the threat
https://github.com/unixfreaxjp/rules/blob/master/malware/MALW_Mirai_Okiru_ELF.yar
and IoCs:
MD5: 9c677dd17279a43325556ec5662feba0
MD5: 24fc15a4672680d92af7edb2c3b2e957
















