Cross-Domain Transient Execution Attack
Anatomy of a cross-domain transient execution attack

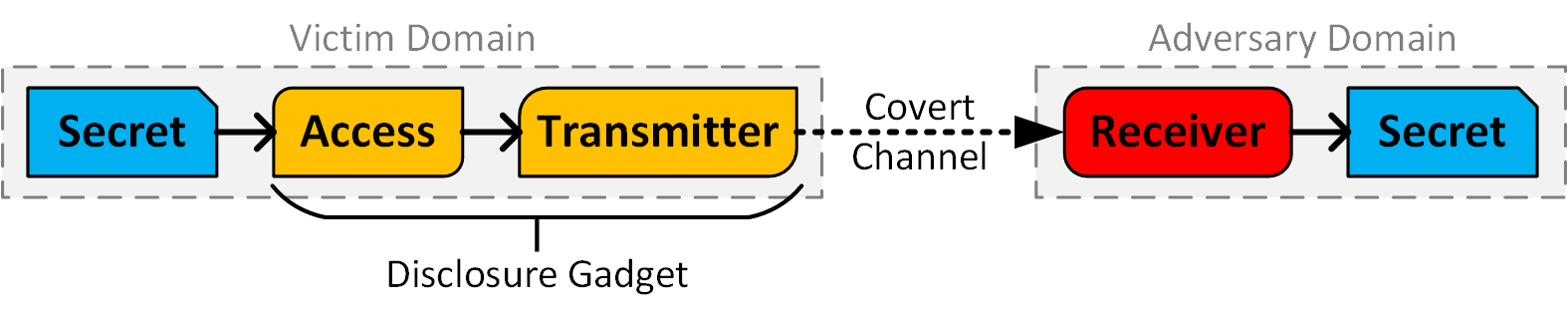
Figure 3. Anatomy of a cross-domain transient execution attack: Snipped blue boxes show data; the rounded red box shows adversary code; semi-rounded orange boxes show victim code being manipulated by the adversary; arrows depict the secret's data flow during the attack.
A cross-domain transient execution attack5 requires the adversary to find a disclosure gadget in the victimís domain which, when executed transiently, can transiently access6 and transmit a secret over a covert channel.
Cross-domain transient execution attacks are generally the most difficult to launch successfully because the adversary is unable to construct the disclosure gadget. It is non-trivial to find a disclosure gadget in an existing victim program that can transiently access and transmit a secret prior to being squashed. If the adversary is in ring 3, then noise from other processes can substantially weaken the fidelity of the covert channel. Synchronizing with the victim (as required by Prime+Probe) may also prove challenging for a ring 3 adversary.
An example of a cross-domain transient execution attack is Branch Target Injection (Spectre variant 2) where a malicious ring 3 application (the adversary) trains a branch predictor that is shared with another ring 3 application (the victim) to predict a memory address chosen by the adversary. The target address could be a disclosure gadget that can transiently access memory and transmit secret data before the branch misprediction is squashed.