Domain-Bypass Transient Execution Attack
Anatomy of a domain-bypass transient execution attack

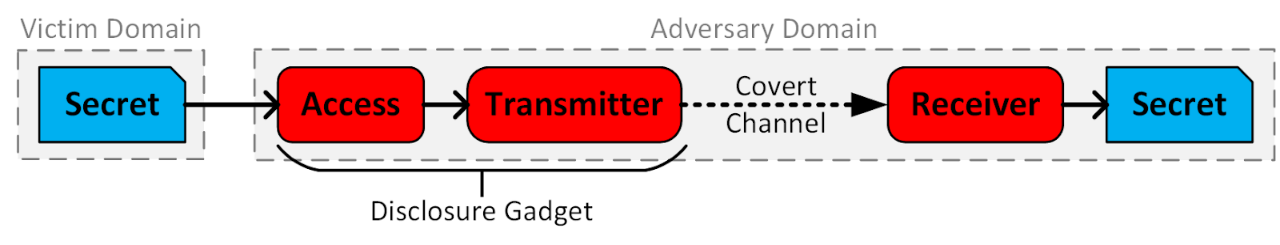
Figure 2. Anatomy of a domain-bypass transient execution attack: Snipped blue boxes show data; rounded red boxes show adversary code; arrows depict the secret's data flow during the attack.
In a domain-bypass transient execution attack, the adversary executes transient instructions that circumvent hardware-based access controls, allowing access to a secret outside of the adversary’s domain. This sequence of transient instructions must also contain a transmitter such as a memory access that encodes the secret into the CPU’s cache state. Non-transient receiver code can recover the secret by applying a cache analysis technique such as Flush+Reload.
As a specific example, consider Rogue Data Cache Load (Meltdown). The adversary’s domain is a ring 3 application, and the victim domain is the operating system kernel (ring 0). When the adversary attempts to access kernel memory sharing the same virtual address space, transient instructions may allow kernel data to be read and transmitted before hardware-enforced permission checks are resolved. Other examples of domain-bypass transient execution attacks include Microarchitectural Data Sampling (MDS) and L1 Terminal Fault (L1TF).