In-Domain Transient Execution Attack
Anatomy of an in-domain transient execution attack

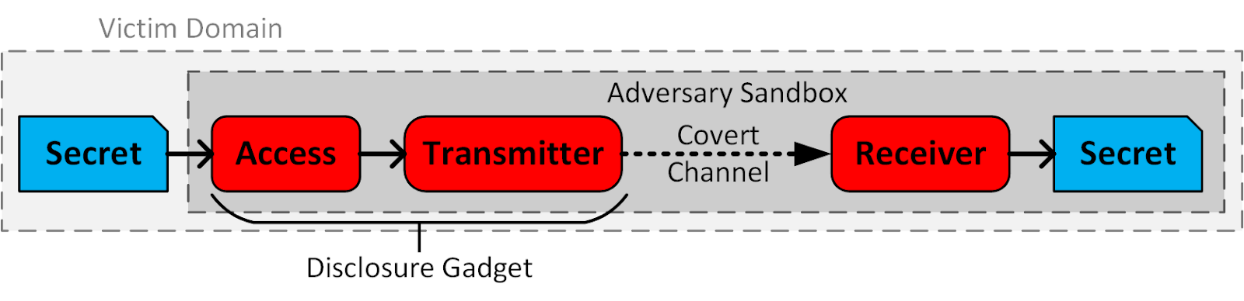
Figure 4. Anatomy of an in-domain transient execution attack: Snipped blue boxes show data; rounded red boxes show adversary code; arrows depict the secret´s data flow during the attack.
An in-domain transient execution attack allows a sandboxed adversary to access a secret within the same domain by circumventing software-based access controls. For example, when a JavaScript program attempts a random access on an array object, the access is subjected to a bounds check that may involve a conditional branch. If the program attempts an out-of-bounds access—but the branch predicts the in-bounds path—the access and transmit instructions may be allowed to execute transiently before the mispredicted path is squashed. This example is a Bounds Check Bypass (Spectre variant 1) attack applied by sandboxed software against its domain.
Figure 4 is intended to be representative of in-domain transient execution attacks, though other variations may exist. For instance, the adversary-controlled receiver could be in another sandbox within the same domain, or it could be in a different domain. As an alternative to software sandboxing, it is also possible to use language-based security or other software fault isolation techniques to isolate software components that share the same domain. These approaches also employ software-based access controls that can be potentially circumvented by transient instructions.