14.3.2017 thehackernews Android
With the rise in the mobile market, Adware has become one of the most prevalent mobile threats in the world. Adware has traditionally been used to aggressively push ads like banners or pop-ups on mobile screens to make money.
The troublesome part is that Adware is now becoming trojanized and more sophisticated, as it aggressively collects personal data from the mobile device it's installed on, including name, birth date, location, serial number, contacts, and browser data without users' consent.
However, the risk is a bit higher on Android than other platforms because of the extra permissions that apps enjoy.
Although Google has stepped up its efforts to remove potentially harmful apps from its Play Store in the past years and added more stringent malware checks for new apps, Adware app eventually finds its way into its mobile app marketplace to target millions of Android users.
In its recent efforts to make its Play Store ecosystem safe, Google has recently discovered a new massive ad-fraud family of a botnet that was infecting Android users through apps hosted on its official Play Store.
Dubbed Chamois, the family of PHAs (potentially harmful applications) was capable of bombarding users with pop-up ads, boosting app promotion by automatically installing other applications in the background, subscribing users to premium services by sending text messages and downloading additional plugins without their knowledge.
Google engineers said they caught Chamois after they discovered suspicious ad traffic while performing a routine ad traffic quality evaluation.
Despite the fact that the app uses obfuscation and anti-analysis techniques to evade detection, Google engineers eventually uncovered a massive network of developers that had tricked users into installing malicious apps on their phones.
The goal behind the malware-laced apps appears to have been ad fraud and make money by employing different techniques to bypass Google's detection and prevention systems.
"We analyzed malicious apps based on Chamois, and found that they employed several methods to avoid detection and tried to trick users into clicking ads by displaying deceptive graphics," security software engineers at Google said in a blog post.
"This sometimes resulted in downloading of other apps that commit SMS fraud. So we blocked the Chamois app family using Verify Apps and also kicked out bad actors who were trying to game our ad systems."
The Chamois apps had a multi-stage payload structure, including a custom encrypted storage area for configuration files and additional code, which required deeper analysis to understand the malicious part.
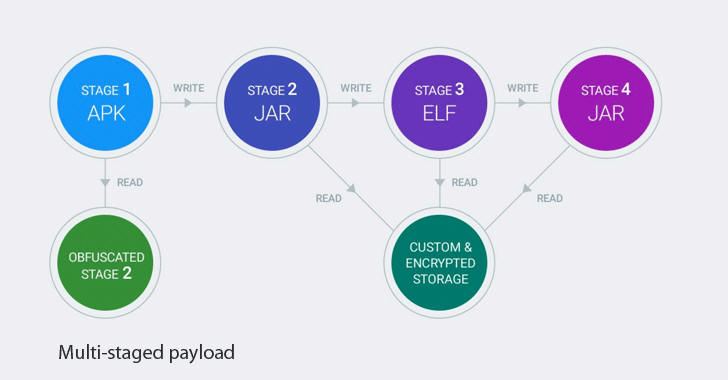
According to the Google engineers, their security teams had to look through more than 100,000 lines of sophisticated code written by seemingly professional developers in an effort to figure out exactly what the Chamois-related apps were up to.
After the discovery of Chamois, Google blocked the Chamois app family using its Verify Apps and also banned some people who were trying to take advantage of its ad system to make money on the adware apps.
Google also updated its app testing system that is now capable of detecting this new Chamois-related threat.