A new exploit for zero-day vulnerability CVE-18-8589
16.11.18 Kaspersky Exploit Vulnerebility
Yesterday, Microsoft published its security bulletin, which patches a vulnerability discovered by our technologies. We reported it to Microsoft on October 17, 18. The company confirmed the vulnerability and assigned it CVE-18-8589.
In October 18, our Automatic Exploit Prevention (AEP) systems detected an attempt to exploit a vulnerability in Microsoft’s Windows operating system. Further analysis revealed a zero-day vulnerability in win32k.sys. The exploit was executed by the first stage of a malware installer in order to gain the necessary privileges for persistence on the victim’s system. So far, we have detected a very limited number of attacks using this vulnerability. The victims are located in the Middle East.
Kaspersky Lab products detected this exploit proactively using the following technologies:
Behavioral Detection Engine and Automatic Exploit Prevention for endpoints
Advanced Sandboxing and Anti-Malware Engine for Kaspersky Anti Targeted Attack Platform (KATA)
Kaspersky Lab verdicts for the artifacts in this campaign are:
HEUR:Exploit.Win32.Generic
HEUR:Trojan.Win32.Generic
PDM:Exploit.Win32.Generic
More information about the attack is available to customers of Kaspersky Intelligence Reports. Contact: intelreports@kaspersky.com
Technical details
CVE-18-8589 is a race condition present in win32k!xxxMoveWindow due to improper locking of messages sent synchronously between threads.
The exploit uses the vulnerability by creating two threads with a class and associated window and moves the window of the opposite thread inside the callback of a WM_NCCALCSIZE message in a window procedure that is common to both threads.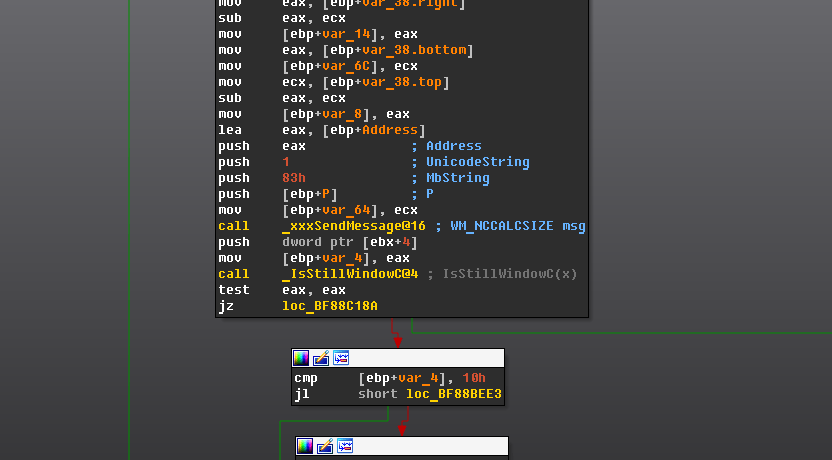
WM_NCCALCSIZE message in win32k!xxxCalcValidRects
Termination of the opposite thread on the maximum level of recursion inside the WM_NCCALCSIZE callback will cause asynchronous copyin of the lParam structure controlled by the attacker.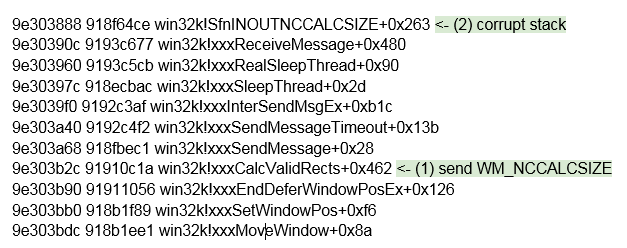
Lack of proper message locking between win32k!xxxCalcValidRects and win32k!SfnINOUTNCCALCSIZE
The exploit populates lParam with pointers to the shellcode and after being successfully copyied to kernel inside win32k!SfnINOUTNCCALCSIZE, the kernel jumps to the user level. The exploit found in the wild only targeted 32-bit versions of Windows 7.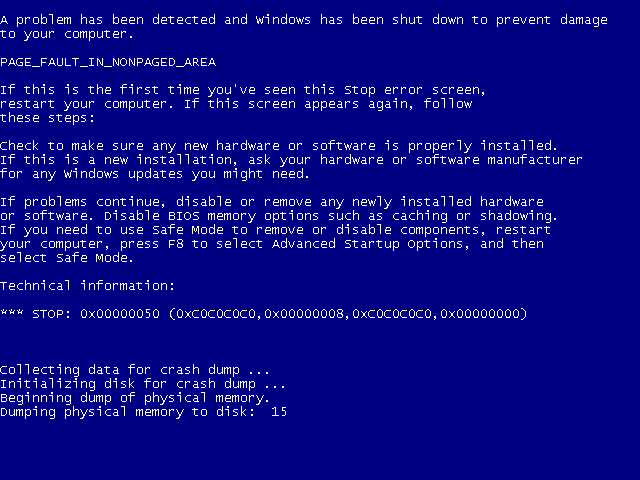
BSOD on an up-to-date version of Windows 7 with our proof of concept
As always, we provided Microsoft with a proof of concept for this vulnerability along with well-written source code.