Adobe Patches Vulnerability Affecting Internal Systems
22.7.18 securityweek Vulnerebility
Adobe has patched what researchers describe as a potentially serious security issue in its internal systems, but the company has downplayed the impact of the vulnerability.
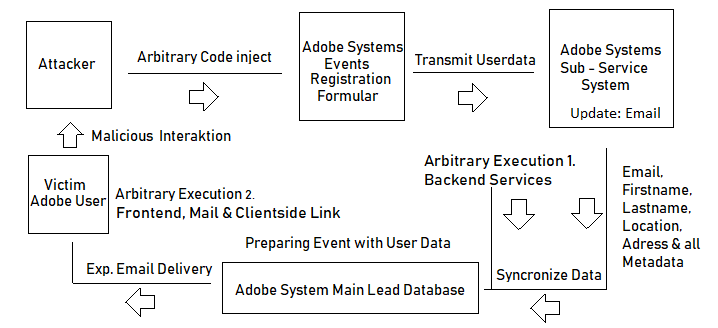
White hat hackers at Germany-based security research firm Vulnerability Lab claim to have discovered that code submitted through some of Adobe’s event marketing registration forms ultimately made its way to one of the company’s main databases, from where it propagated to emails and web services.
Adobe told SecurityWeek that the issue was a cross-site scripting (XSS) bug in a form used for event marketing registration and said a fix had been implemented. If Adobe’s classification of the flaw is accurate, it was likely a persistent XSS.
Vulnerability Lab told SecurityWeek that it analyzed the issue between November 2017 and February 18, when it reported its findings to the vendor. The company claims it took until May for Adobe to identify the cause of the problem, with a patch being implemented in mid-June.
Following the disclosure, Adobe included Vulnerability Lab on its industry partners page, which also lists CERT/CC, FireEye, Microsoft, Google, Tencent, Qihoo 360, Kaspersky, Palo Alto Networks and others.
The researchers said there were multiple domains where malicious code could have been inserted and there were multiple places where the code would be executed.
“The code was injected to a micro service, from there it was taken to the main application management service. Then it was synced into the main lead database of Adobe and we had several domains where we were able to place our codes with executable content,” explained Benjamin Kunz Mejri, CEO and founder of Vulnerability Lab.
The exploit code was delivered via emails sent out by Adobe and on some of the company’s domains, Kunz Mejri said.

Vulnerability Lab has published a blog post and an advisory to describe the vulnerability.