Automation Software Flaws Expose Gas Stations to Hacker Attacks
7.2.2018 securityweek CyberCrime
Gas stations worldwide are exposed to remote hacker attacks due to several vulnerabilities affecting the automation software they use, researchers at Kaspersky Lab reported on Wednesday.
The vulnerable product is SiteOmat from Orpak, which is advertised by the vendor as the “heart of the fuel station.” The software, designed to run on embedded Linux machines or a standard PC, provides “complete and secure site automation, managing the dispensers, payment terminals, forecourt devices and fuel tanks to fully control and record any transaction.”
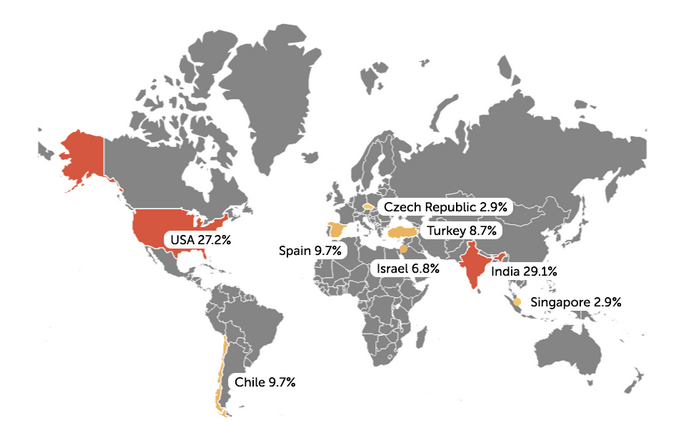
Kaspersky researchers discovered that the “secure” part is not exactly true and more than 1,000 of the gas stations using the product allow remote access from the Internet. Over half of the exposed stations are located in the United States and India.

“Before the research, we honestly believed that all fueling systems, without exception, would be isolated from the internet and properly monitored. But we were wrong,” explained Kaspersky’s Ido Naor. “With our experienced eyes, we came to realize that even the least skilled attacker could use this product to take over a fueling system from anywhere in the world.”
According to the security firm, the vulnerabilities affecting SiteOmat could be exploited by malicious actors for a wide range of purposes, including to modify fuel prices, shut down fueling systems, or cause a fuel leakage.
The security holes can also allow hackers to move laterally within the targeted company’s network, gain access to payment systems and steal financial data, and obtain information on the station’s customers (e.g. license plates, driver identity data). Another possible scenario described by Kaspersky involves disrupting the station’s operations and demanding a ransom.
These attacks are possible due to a series of vulnerabilities, including hardcoded credentials (CVE-2017-14728), persistent XSS (CVE-2017-14850), SQL injection (CVE-2017-14851), insecure communications (CVE-2017-14852), code injection (CVE-2017-14853), and remote code execution (CVE-2017-14854). Exploiting the flaws does not require advanced hacking skills, Naor said.
The fact that the vendor has made available technical information about the device and a detailed user manual made it easier for experts to find the security holes.
The systems analyzed by Kaspersky were often embedded in fueling systems and researchers believe they had been connected to the Internet for more than a decade.
Orpak was informed about the flaws in September and the company told researchers a month later that it had been in the process of rolling out a hardened version of its system, but it has since not shared any updates on the status of patches. SecurityWeek has reached out to the vendor for comment and will update this article if the company responds.