Black Friday alert
16.11.2018 Kaspersky Security
Banking Trojans target popular e-commerce brands to steal data
Banking Trojans traditionally target users of online financial services; looking for financial data to steal or building botnets out of hacked devices for future attacks. However, over time, several of these banking Trojans have enhanced their functionality, launching new variants and extending their range. Some are now able to obtain root access to infected devices, perform transactions, inject other malicious code, record video, and more. And the victims of such malware are not just people who bank online but online shoppers in general.
According to Kaspersky Lab data, 14 malware families are targeting e-commerce brands to steal from victims. The main ones are Betabot, Panda, Gozi, Zeus, Chthonic, TinyNuke, Gootkit2, IcedID and SpyEye. They are all banking Trojans. Detections of their e-commerce-related activity has increased steadily over the last few years, from 6.6 million in 2015 to an estimated 12.3 million by the end of 2018 (based on the extrapolation of a detection number of 9.2 million at the end of Q3, 2018), with a 12% increase between 2016 and 2017, and a 10% expected rise between 2017 and 2018.
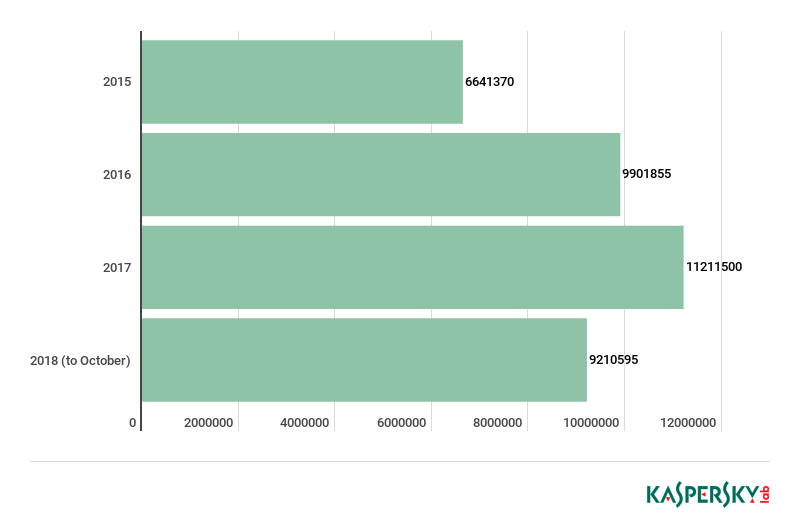
Overall detection data for main malware Trojans targeting users of e-commerce brands, 2015 – 2018. Source: KSN (download)
Attack method
The Trojans are using the e-commerce brands to hunt user credentials like login, password, card number, phone number, and more. In order to do so, the malware can intercept input data on target sites, modify online page content, and/or redirect visitors to phishing pages.
For example, the Trojans enable the cybercriminals behind them to monitor users’ online behavior: tracking which sites are visited on the infected device. If the Trojan spots the user browsing to a target e-commerce website, it activates its form-grabbing functionality. ‘Form grabbing’ is a technique used by criminals to save all the information that a user enters into forms on a website. And on an e-commerce website, such forms are almost certain to contain: login and password combination as well as payment data such as credit card number, expiration date and CVV. If there is no two-factor transaction confirmation in place, then the criminals who obtained this data can use it to steal money.
Target brands
The 14 malware families were found to be targeting a total of 67 consumer e-commerce sites between them. This includes 33 ‘consumer apparel’ sites (clothing, footwear, gifts, toys, jewelry and department stores), eight consumer electronics sites, eight entertainment and gaming sites, three popular telecoms sites, two online payment sites, and three online retail platforms, among others.
Betabot targets as many as 46 different brands, and was the only Trojan to target entertainment and gaming sites, while Gozi targets 36 brands overall, and Panda 35.
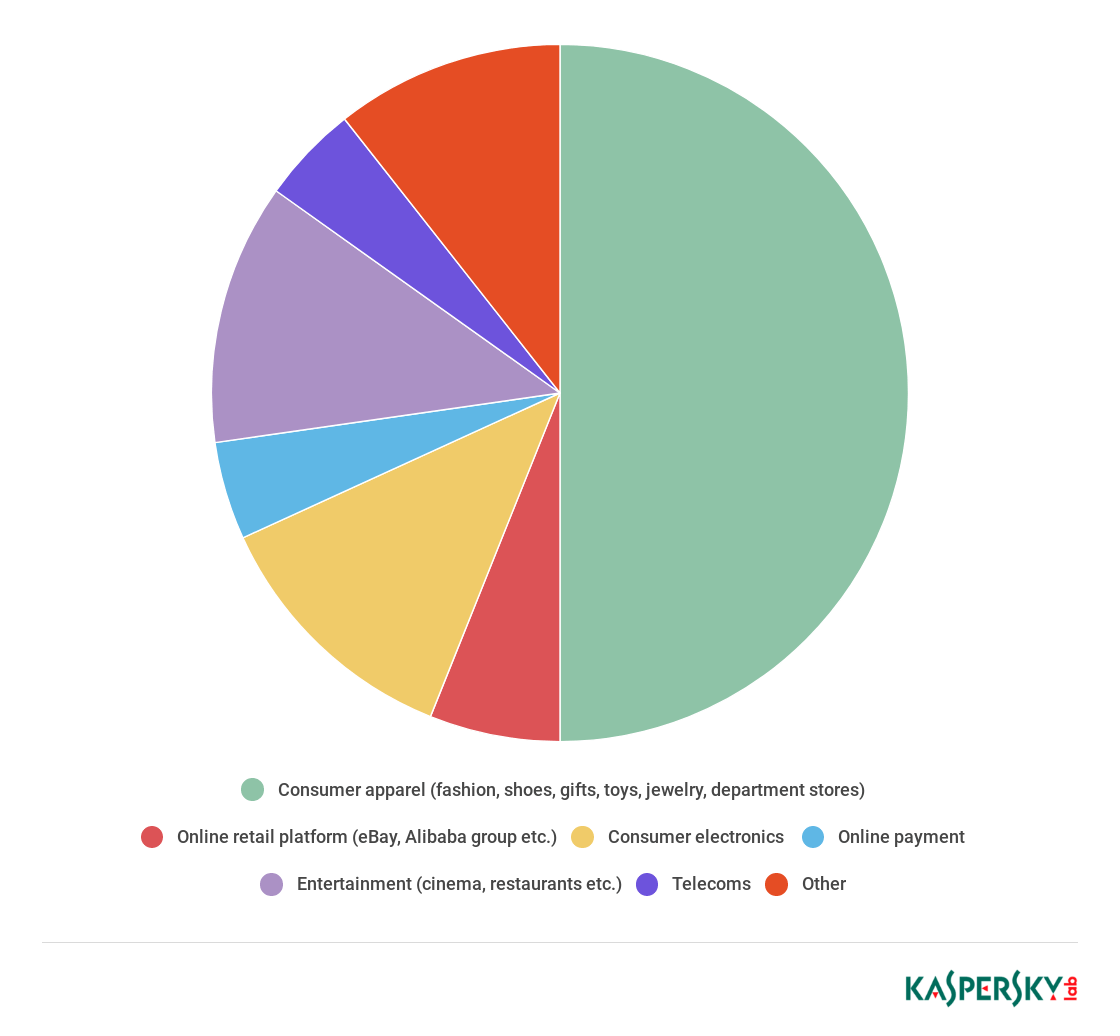
Proportion of e-commerce categories targeted by malware, 2018 (download)
Why would banking Trojans target e-commerce sites?
One possibility is financial gain by selling the credentials: our research uncovered over three million sets of e-commerce credentials up for sale on a marketplace easily accessible through the Google search engine. The highest prices are charged for what appear to be hacked merchant accounts.
Another way of making money could be to use rather than sell the compromised credentials. Cybercriminals could, for example, use the stolen accounts in money-laundering schemes: buying things from a website using victims’ credentials so they look like known customers and don’t trigger any anti-fraud measures, and then selling those items on again.
Target geography
In 2018, malware attacks to steal data through e-commerce brands were particularly active in European countries, including Italy, Germany and France, as well as in North America, Russia and emerging markets.
For example, most of those affected by Betabot attacks through e-commerce sites were located in Italy (where 14.13% of users affected by any malware in the first eight months of 2018 were targeted by this threat), Germany (6.04%), Russia (5.5%) and India (4.87%). For Gozi the pattern was similar: 19.57% of users affected by any malware in Italy were targeted by this threat, with Russia second (13.89%), followed by Brazil (11.96%) and France (5.91%).
Advice and recommendations
To stay safe from such threats during the busy festive shopping season, Kaspersky Lab recommends taking the following security measures:
If you are a consumer
A powerful, updated security solution is a must for all devices you use to shop online. Avoid buying anything online from websites that look potentially dangerous or resemble an incomplete version of a trusted brand’s website.
Don’t click on unknown links in email or social media messages, even from people you know, unless you were expecting the message.
If you are an online brand or trader
Use a reputable payment service and keep your online trading and payment platform software up to date. Every new update may contain critical patches to make the system less vulnerable to cybercriminals.
Use a tailored security solution to protect your business and customers.
Pay attention to the personal information used by customers to buy from you. Use a fraud prevention solution that you can adjust to your company profile and the profile of your customers.
Think about how much money you wish to keep in an online payment transaction account at any one time. The greater the balance, the higher the value of that account to hackers.
Restrict the number of attempted transactions and always use two-factor authentication (Verified by Visa, MasterCard Secure Code, etc.).
The research is based on data obtained with user consent and processed using Kaspersky Security Network (KSN). All malware belonging to the banking Trojans covered in the report are detected and blocked by Kaspersky Lab security solutions.

