
Botnet of Smart Heaters, ACs Can Cause Power Disruptions: Researchers
16.8.2018 securityweek BotNet

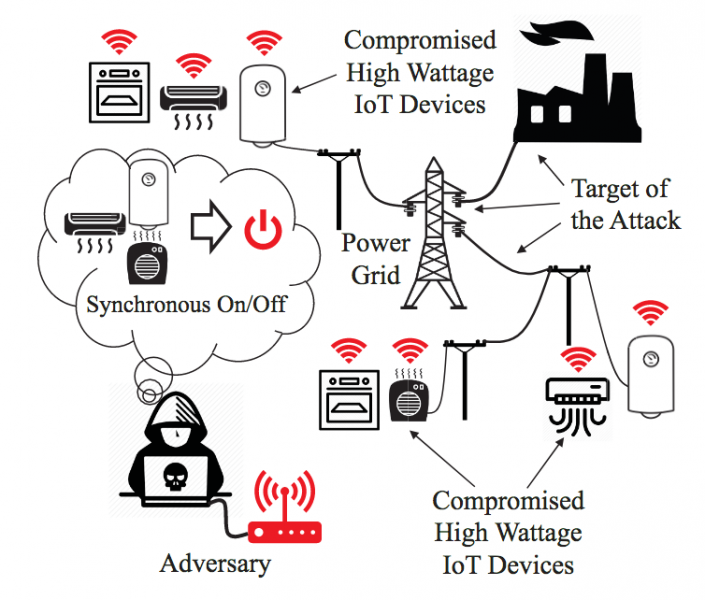
A research paper published this week at the 27th USENIX Security Symposium describes a new type of attack that could cause energy grid disruptions. The method involves a botnet powered by tens of thousands of compromised high-wattage IoT devices such as heaters and air conditioners.
Wi-Fi enabled air conditioners, ovens, water heaters and space heaters that can be controlled remotely over the Internet are increasingly popular. The power usage of these devices ranges between 1,000 and 5,000 watts.
Researchers from the Department of Electrical Engineering at Princeton University claim that these types of high-wattage IoT devices can be exploited in what they call “Manipulation of demand via IoT” (MadIoT) attacks to cause local power outages and even large-scale blackouts.
In a MadIoT attack, a threat actor takes control of smart high-wattage devices in order to manipulate (i.e. increase or decrease) power consumption.
The experts tested their theory using state-of-the-art simulators of real-world power grid models.
One attack scenario involves frequency instability. The researchers noted that the normal operation of a power grid relies on the balance between supply and demand. They believe that this balance can be disrupted using an IoT botnet of air conditioners and heater that are simultaneously switched on or off by the attacker.
“If the resulting sudden increase in the demand is greater than a threshold, which depends on the inertia of the system, it can cause the system’s frequency to drop significantly before the primary controllers can react,” the researchers wrote in their paper. “This consequently may result in the activation of the generators’ protective relays and loss of generators, and finally a blackout. Sudden decrease in the demand may also result in the same effect but this time by causing a sudden rise in the frequency.”
Using a simulator based on the power grid model of the Western Electricity Coordinating Council (WECC), which is responsible for compliance monitoring and enforcement in the Western part of the United States and Canada, researchers calculated that a 30 percent increase in power demand would lead to all generators tripping.
In order to launch such an attack, experts determined that an attacker would need a botnet of 90,000 air conditioners and 18,000 electric water heaters within the targeted geographical area.
Register for SecurityWeek’s 2018 ICS Cyber Security Conference
A botnet of roughly 100,000 IoT systems may not seem like an impossible task considering that the Mirai botnet, at its peak, infected over 600,000 devices. However, those devices were distributed across more than 160 countries and they included low-wattage devices such as cameras. In the case of a MadIoT botnet, the bots would need to be concentrated in the region of the targeted power grid and they would need to be high-wattage devices for the attack to have an impact.
If the attack leads to a blackout, the grid operator will need to perform what is known as a black start in order to get the power back on. During this process, power is restored in one area at a time to avoid frequency instability. The attacker can use the botnet to suddenly increase demand once power is restored in one area, which can cause the grid to shut down once again.
Another type of attack, which can also lead to a widespread blackout, involves line failures that lead to further line failures in what is known as a cascading failure. Tests for this type of attack were conducted using a simulation of the power grid in Poland, which researchers say is one of the largest and most detailed publicly available real-world power grids.
Calculations showed that an increase of one percent in the demand in Poland’s grid during the summer of 2008 would result in a cascading failure with 263 line failures and an 86 percent load outage. Such an attack would require a botnet of 210,000 compromised air conditioners.
Researchers noted that even if the botnet does not cause frequency instability or line failures, simultaneously turning on tens of thousands of devices within a region can significantly increase costs for the grid operator. These types of attacks could be launched by utilities that operate reserve generators, which provide grid operators electric power – at a higher-than-normal cost – if the demand is higher than estimated, experts said.
“The MadIoT attacks’ sources are hard to detect and disconnect by the grid operator due to their distributed nature. These attacks can be easily repeated until being effective and are black-box since the attacker does not need to know the operational details of the power grid. These properties make countering the MadIoT attacks challenging,” they wrote in their paper.
The same team of Princeton researchers has published a separate paper focusing on how the power grid can be protected against IoT botnets of high wattage devices.
Experts and government authorities have often warned that there is an increasing risk of cyber attacks aimed at the energy sector. However, most warnings involve scenarios in which actors target energy organizations directly.
Earlier this year, researchers warned that threat actors may be able to cause blackouts by remotely manipulating residential or commercial AC units via RF signals to create a surge. However, other experts argued that such attacks would not be easy to carry out in the real world – at least in the United States – due to how power distribution works.