
CSE CybSec ZLAB Malware Analysis Report: APT28 Hospitality malware
5.10.2017 securityaffairs APT
The CSE CybSec Z-Lab Malware Lab analyzed the Hospitality malware used by the Russian APT28 group to target hotels in several European countries.
The Russian hacker group APT28, also known as Sofacy or Fancy Bear, is believed to be behind a series of attacks in last July against travelers staying in hotels in Europe and Middle East.
This attack is performed by sending spear phishing emails to the victims, masquerading as a hotel reservation form that, if opened and macros are enabled, installs a malware in the machine’s victim.
Why should Fancy bear do this? According to FireEye and other security firms, Sofacy is a cyberespionage group and a good tool to get info about people (possibly businessmen and politicians) hosted in important hotels, is to deceive them to install a spyware with a Command and Control that monitors the actions of all the victims.

Figure 1 – Screen of Word dropper.
The above figure shows an example of the weaponized document used by hackers as an attachment in spear phishing emails. The document contains a payload achievable when macro is enabled. In fact, the macro is a Visual Basic script used to decode the malicious payload and to create a series of files, according to the following scheme: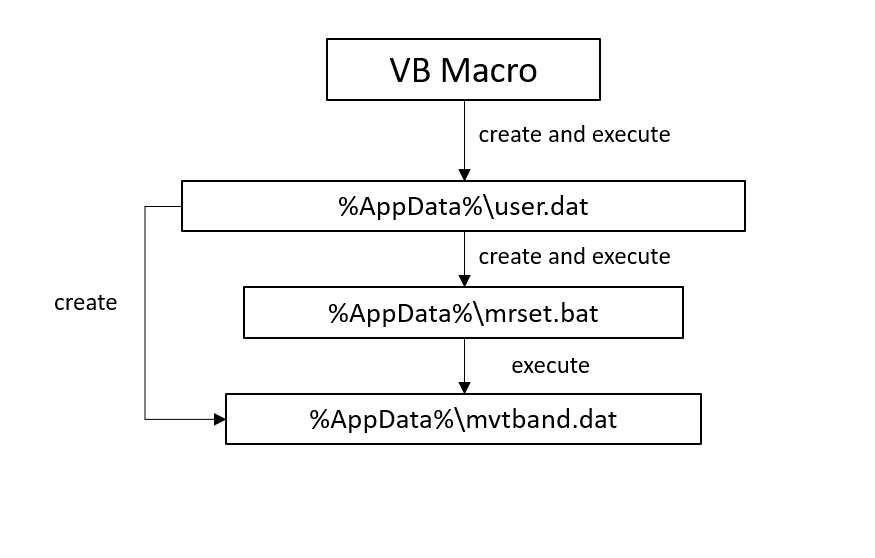
Figure 2 – Files’ creation and execution scheme
The file “mvtband.dat” is the core of the malware that contains a C2C client, which tries to connect to servers, “mvtband.net” and “mvband.net” in order to send the info gathered about the victim’s host and receive new commands to execute on it. In particular, the malware contacts these C&C servers with POST request on a random path. The body contains some info, among them the list of the executing processes, info about system settings, browser preferences, encrypted using its own algorithm. Moreover, from our advanced analysis, we discovered that Hospitality Malware takes screenshots of the machine that most likely it sends to the C2C together with other info. But, nowadays, these servers are blacklisted so we can’t analyze all the complete behavior of Hospitality Malware.
You can download the full ZLAB Malware Analysis Report at the following URL: