Cloudflare Helps Boost DNSSEC Adoption as Key Rollover Nears
20.9.2018 securityweek Safety
Cloudflare announced on Monday the introduction of a new feature that will allow some users to enable the Domain Name System Security Extensions (DNSSEC) protocol with the click of a button.
Cloudflare customers and supported registries can now easily enable DNSSEC from the Cloudflare dashboard. This takes the burden off of website owners, who normally need to manually add a DS record in their account at their registrar.
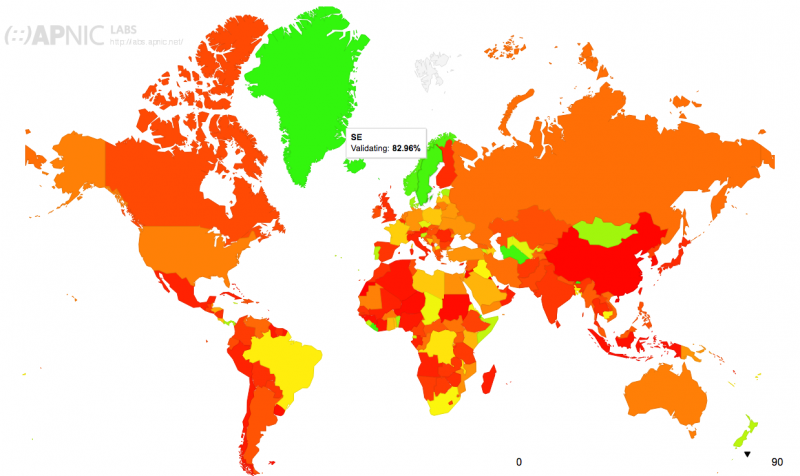
Data from APNIC shows that many domain owners have attempted to activate DNSSEC, but failed to complete the process. Globally, less than 14 percent of DNS requests have DNSSEC validated by the resolver. Some countries, such as Norway and Sweden, have validation rates of roughly 80%, but China for instance validates less than 1% of requests. The validation rate in the United States is just over 23%.
DNSSEC validation rates
“Locating the part of the registrar UI that houses DNSSEC can be problematic, as can the UI of adding the record itself. Additional factors such as varying degrees of technical knowledge amongst users and simply having to manage multiple logins and roles can also explain the lack of completion in the process. Finally, varying levels of DNSSEC compatibility amongst registrars may prevent even knowledgeable users from creating DS records in the parent,” Cloudflare explained in a blog post.
Cloudflare’s ability to allow customers to easily enable DNSSEC is a result of support for CDS and CDNSKEY records. These mirror the DS and DNSKEY record types and are designed to alert the parent or registrar that a domain wants to enable DNSSEC and have a DS record presented.
“Cloudflare will publish CDS and CDNSKEY records for all domains who enable DNSSEC. Parent registries should scan the nameservers of the domains under their purview and check for these rrsets. The presence of a CDS key for a domain delegated to Cloudflare indicates that a verified Cloudflare user has enabled DNSSEC within their dash and that the parent operator (a registrar or the registry itself) should take the CDS record content and create the requisite DS record to start signing the domain,” Cloudflare said.

DNSSEC aims to prevent DNS spoofing attacks, which allow malicious actors to redirect users to their own websites. It does this by cryptographically signing DNS information, and the master crypto key is called a key signing key (KSK).
Since keeping a cryptographic key alive for a long period of time is considered a bad security practice given the fact that it could get compromised, the Internet Corporation for Assigned Names and Numbers (ICANN) plans to periodically change the KSK.
This change also requires that network operators update their systems with the new KSK. Failure to do so will result in clients using their DNS resolvers not being able to reach websites and email addresses.
ICANN initially planned a KSK rollover for October 11, 2017. However, as the date approached, the organization determined that many network operators and ISPs were unprepared, which could lead to tens of millions of users going offline. The KSK rollover was pushed back one year and it’s currently set for October 11, 2018, although this date is still pending ratification by the ICANN Board.
ICANN expects the impact of the root KSK rollover to be minimal if it takes place on October 11, but it will still affect a “small percentage” of users, who may not be able to access websites.
A small number of DNSSEC validating resolvers are misconfigured and some of the users relying on these resolvers may experience problems.
Users who rely on resolvers that do not perform DNSSEC validation will not be impacted, and ICANN believes roughly two-thirds of users are in this situation.