Equifax Sent Breach Victims to Fake Website
21.9.2017 securityweek Cyber
Equifax has made another blunder following the massive data breach suffered by the company – it advised some customers on Twitter to access a fake support website set up by a security researcher.
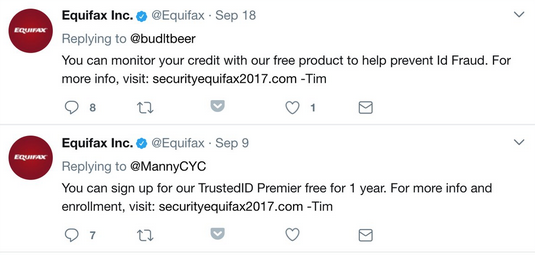
Equifax staff advised breach victims on Twitter at least 8 times to access securityequifax2017.com instead of equifaxsecurity2017.com, the website created by the credit reporting agency following the hacker attack that affected as many as 143 million consumers in the U.S., 400,000 in the U.K. and 100,000 in Canada.
Securityequifax2017.com is a fake Equifax support website set up by Nick Sweeting to show how easily cybercriminals can impersonate such a domain. The researcher believes the company should have hosted its consumer notification website on equifax.com, instead of a domain that can be easily faked.
Shortly after Equifax announced that its systems were breached, security experts started warning consumers that they would likely be targeted in phishing attacks leveraging the incident. A list of possible phishing domains impersonating equifaxsecurity2017.com was published on Pastebin.
While it’s unclear how many phishing pages have been set up, the fact that Equifax itself directed breach victims to a fake website clearly demonstrates the risks associated with the company’s decision to set up this domain.
Equifax has removed the tweets referencing the fake support website. Sweeting said that his site, which did contain a form for entering data just like the legitimate Equifax site, did not actually store any information.

This was not the only problem with equifaxsecurity2017.com. When it was launched, the site was riddled with flaws and some security services flagged it as a phishing website.
Following the data breach, researchers and cybersecurity firms started highlighting Equifax’s failings, including serious website vulnerabilities, the lack of basic protections on the company’s site, and employee credentials up for sale on the dark web.
The company also admitted that it had been aware of the Apache Struts 2 vulnerability that was used to breach its systems. The flaw had been exploited in the wild for two months before attackers leveraged it against Equifax.