HackerOne Bug Bounty Programs Paid Out $11 Million in 2017
18.7.18 securityweek Safety
White hat hackers who responsibly disclosed vulnerabilities through bug bounty programs hosted by HackerOne earned more than $11 million last year, according to the company’s 18 Hacker-Powered Security Report.
HackerOne hosts roughly 1,000 programs that over the past years have received over 72,000 vulnerability reports from researchers in more than 100 countries. The bounties paid out since the launch of the company until June 18 reached over $31 million.
Of the total, more than $25 million was paid out by organizations in the United States, which was also the country where the highest percentage of money went to ($5.3 million).
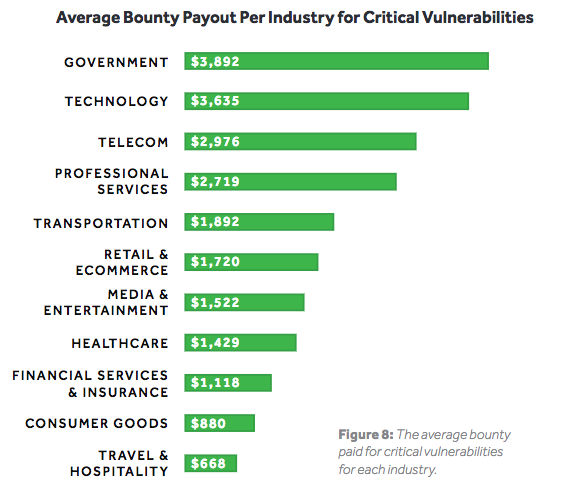
According to the company, 116 of the bug reports submitted last year resulted in payouts that exceeded $10,000, and the average amount paid out by companies for critical issues has increased to over $2,000, with organizations such as Microsoft and Intel offering as much as $250,000.

An increasing number of companies have launched public bug bounty programs, but still nearly 80% of programs were private last year. The majority of public programs are launched by organizations in the tech sector, which accounts for 63%.
The government sector recorded the biggest increase in new program launches, with the European Commission, and Singapore’s Ministry of Defense announcing initiatives. The U.S. government has also continued to run programs, including Hack the Air Force and Hack the Army.
Roughly 27,000 valid vulnerabilities were reported last year and cross-site scripting (XSS) remained the most common type of flaw, followed by information disclosure bugs.
When it comes to the time it takes organizations to patch security holes, the consumer goods industry was the fastest, with an average of 14 days. At the other end of the chart we have the government sector, which patched vulnerabilities, on average, in 68 days.
The highest bug bounty paid out last year was $75,000. A technology firm awarded the sum for three vulnerabilities that could have been chained for remote code execution without user interaction. Successful exploitation could have allowed an attacker to access credit card information, hijack user and employee accounts, access infrastructure code, or deploy mass ransomware campaigns.
The complete 18 Hacker-Powered Security Report is available from HackerOne in PDF format.