Half a Billion Enterprise Devices Exposed by DNS Rebinding
23.7.18 securityweek Hacking
Nearly half a billion devices used by enterprises are exposed to cyberattacks by DNS rebinding, according to a study conducted by IoT security firm Armis.
DNS rebinding, an attack method that has been known for more than a decade, allows a remote hacker to bypass the targeted entity’s network firewall and abuse their web browser to directly communicate with devices on the local network and exploit any vulnerabilities they may have. Getting the target to access a malicious page or view a malicious advertisement is often enough to conduct an attack that can lead to theft of sensitive information and taking control of vulnerable devices.
Google Project Zero researcher Tavis Ormandy revealed a few months ago that DNS rebinding could be used to exploit critical flaws in BitTorrent’s uTorrent application and the Transmission BitTorrent client.
More recently, researcher Brannon Dorsey showed how malicious actors could exploit vulnerabilities in Google Home and Chromecast devices, Roku TVs, Sonos Wi-Fi speakers, routers, and smart thermostats via DNS rebinding.
Armis, the firm that discovered the Bluetooth flaws dubbed BlueBorne, conducted its own research on the impact of DNS rebinding on enterprises.
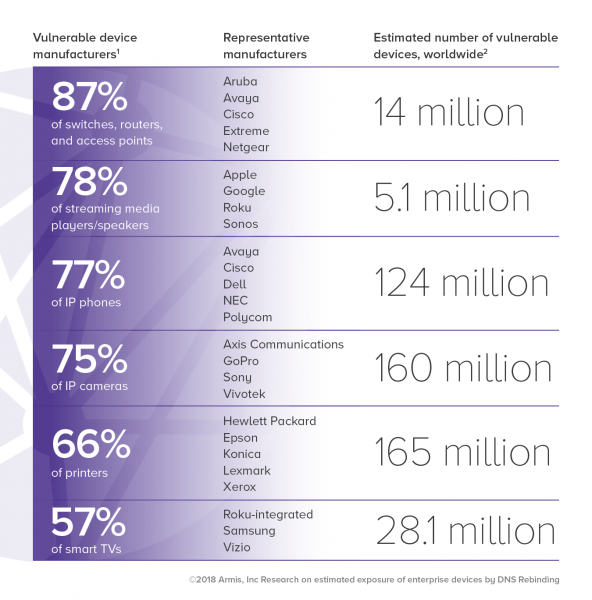
The company estimates that there are 496 million enterprise devices worldwide that are exposed due to DNS rebinding. This includes 165 million printers, 160 million IP cameras, 124 million IP phones, 28 million smart TVs, 14 million switches and routers, and 5 million media players.

“Because of the widespread use of the types of devices listed above within enterprises, Armis can say that nearly all enterprises are susceptible to DNS rebinding attacks,” Armis said.
As an example of vulnerabilities that can be exploited as a result of DNS rebinding, the company highlighted the flaws patched this month by Cisco in its IP phones. Armis also pointed to the critical security holes discovered recently in Axis and Foscam cameras.
As for printers, researchers noted, “Unfortunately, printers are one of the least managed, most poorly configured devices in the enterprise. Aside from adjusting basic network configurations, enterprises typically deploy printers with default settings, making them an ideal target for a DNS rebinding attack.”
In an attack scenario described by Armis, the attacker simply needs to trick the targeted user into visiting a specially crafted website which hosts JavaScript code that will be executed in the victim’s browser. The JavaScript code instructs the browser to scan local IP addresses in search of vulnerable devices.
Once vulnerable systems are identified, the attacker can use DNS rebinding to send arbitrary commands (e.g. log into the web server) directly to the IP address of the compromised IoT device. The attacker can also establish an outbound connection to the C&C server and chances are that none of these communications will be detected or blocked by security products.
Since DNS rebinding is possible due to how DNS and web browsers work, Armis believes the best way for enterprises to protect their networks against attacks is to monitor all devices for signs of a breach, perform a risk analysis of IoT devices to determine which systems are vulnerable, and ensure that the devices are secure, including by applying software patches and disabling unnecessary services.