Hey there! How much are you worth?
7.11.2018 Hacking
Kaspersky Have you ever stopped to think just how much your life is worth? I mean really think about it. For instance, letís say you wanted to sell everything you have Ė your house, your car, your job, your private life, photos and home movies from your childhood, your accounts on various social media, your medical history and so on Ė how much would you ask for it all?
I thought about this myself and just the thought that someone else would be able to, for example, read the personal things Iíve written to friends, family and lovers on Facebook made me realize that those things are priceless. The same goes for someone getting access to my email and basically having the power to reset all my passwords for all the accounts Iíve registered using that email.
In the real non-digital world there are lots of insurance policies that cover things if they get damaged or stolen. If someone steals my car or I break my TV, I can replace them if they were insured. We donít really have that option in the digital world, and our digital life contains some very personal and sentimental information. The big difference is that our digital lives can never be erased Ė what weíve said or written, pictures weíve sent, or orders weíve made are basically stored forever in the hands of the service providers.
I decided to investigate the black market and see what kind of information is being sold there. We all know that you can buy drugs, weapons and stolen goods there, but you can also buy online identities. How much do you think your online identity is worth?
Hacked accounts
When investigating hacked accounts from popular services itís almost impossible to compile valid data because there are so many black-market vendors selling this stuff. It is also difficult to verify the uniqueness of the data being sold. But one thing is certain Ė this is the most popular type of data being sold on the black market. When talking about data from popular services, Iím referring to things like stolen social media accounts, banking details, remote access to servers or desktops and even data from popular services like Uber, Netflix, Spotify and tons of gaming websites (Steam, PlayStation Network, etc.), dating apps, porn websites.
The most common way to steal this data is via phishing campaigns or by exploiting a web-related vulnerability such as an SQL injection vulnerability. The password dumps contain an email and password combination for the hacked services, but as we know most people reuse their passwords. So, even if a simple website has been hacked, the attackers might get access to accounts on other platforms by using the same email and password combination.
These kinds of attacks are not very sophisticated, but they are very effective. It also shows that cybercriminals are making money from hackers and hacktivists; the people selling these accounts are most likely not the people who hacked and distributed the password dump.
The price for these hacked accounts is very cheap, with most selling for about $1 per account, and if you buy in bulk, youíll get them even cheaper.
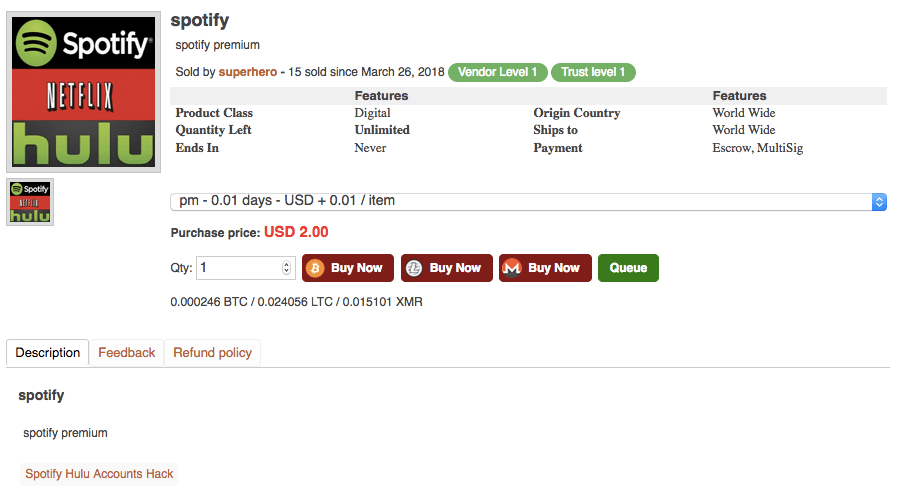
Some vendors even give a lifetime warranty, so if one account stops working, you receive a new account for free. For example, below is a screenshot that shows a vendor selling Netflix accounts.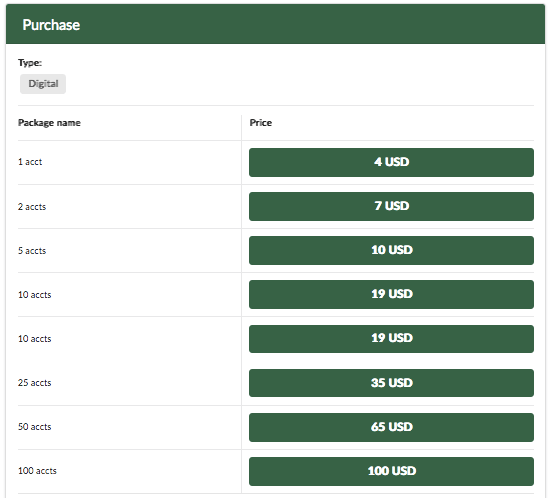
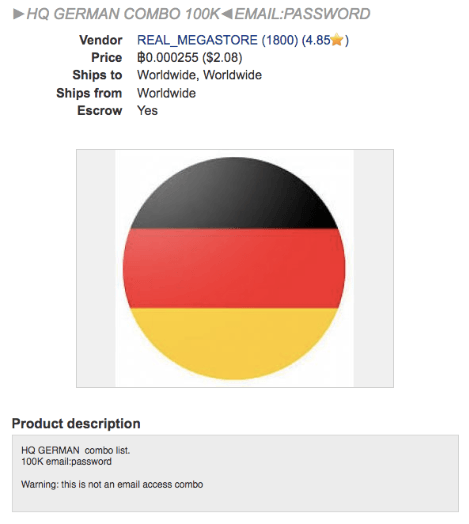
100 000 email and password combinations
250 000 email and password combinations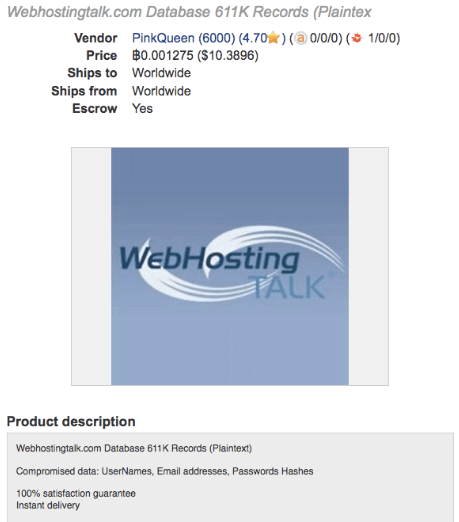
Passports and identity papers
When lurking around underground marketplaces I saw a lot of other information being traded, such as fake passports, driving licenses and ID cards/scans. This is where things get a bit more serious Ė most of the identity papers are not stolen, but they can be used to cause problems in the non-digital world.
People can use your identity with a fake ID card to acquire, for example, phone subscriptions, open bank accounts and so on.
Below is a screenshot of a person selling a registered Swedish passport, and the price is $4000. The same vendor was offering passports from almost all European countries.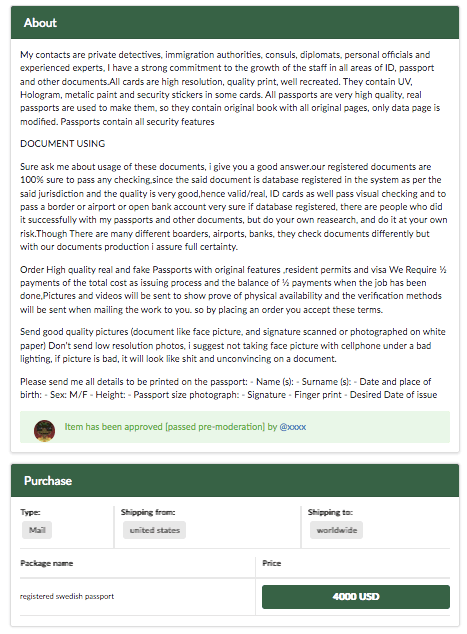
Scammersí toolbox
Most of the items being sold in the underground marketplaces are not new to me; they are all things the industry has been talking about for a very long time. What was interesting was the fact that stolen or fake invoices and other papers/scans such as utility bills were being sold.
People actually steal other peopleís mail and collect invoices, for example, which are then used to scam other people. They will collect and organize these invoices by industry and country. The vendors then sell these scans as part of a scammer toolbox.
A scammer can use these scans to target victims in specific countries and even narrow their attacks down to gender, age and industry.
During the research I got to thinking about a friendís (Inbar Raz) research on Tinder bots and, through my research, I managed to find links between stolen accounts and Tinder bots. These bots are used to earn even more money from stolen accounts. So, the accounts are not just sold on the black market, they are also used in other cybercriminal activities.
Whatís interesting about the fake Tinder profiles is that they have the following characteristics in common that make them easy to identify:
Lots of matches all at once.
Most of the women look like super models.
No job title or education info.
Stolen Instagram pictures/images but with info stolen from Facebook accounts.
Scripted chat messages.
Most of the bots that Iíve researched are related to traffic redirection, clickbait, spam and things like that. So far, I havenít seen any malware Ė most of the bots will try to involve you in other crime or to steal your data. Hereís an example of what it might look like.
The first step is that youíre matched with the bot. The bot doesnít always contact you directly, but waits for you to interact with it before it replies. In some cases the introduction is scripted with some text about how it wants to show you nude photos or something similar and then it posts a link.![]()
When you click on the link you go through several websites redirecting you in a chain. This chain does a lot of things, such as place cookies in your browser, enumerate your settings such as location, browser version and type and probably a lot more. This is done so that when you end up at the landing page they know which page to serve you. In my case, I came from a Swedish IP and the website I was offered was obviously in Swedish, which indicates that they are targeting victims globally.
These websites always have statements and quotes from other users. Most of the information used, including profile photos, name and age, is also taken from stolen accounts. The quote itself is obviously fake, but this approach looks very professional.
This particular website was asking for your email to sign up to a website which basically offered you a job. The actual campaign is called the ĎProfit Formula Scamí and is a binary option auto-trading scam. Itís been covered in the media before, so I wonít go into any detail here.
Summary
People are generally very naive when it comes to their online identity, especially when it comes to services that donít appear to affect their privacy in any way. I often hear people say that they donít care if someone gets access to their account, for example, because they assume that the worst thing that can happen is that their account will be shared with someone they donít know. But we need to understand that even if it all looks very innocent, we donít know what the criminals do with the money they earn.
What if they are spending it on drugs or guns, which are then sold to teenagers? What if they finance platforms and servers to spread child porn? We need to understand that criminals often work together with other criminals, which means that maybe drugs are bought from the money they make from selling stolen Netflix accounts on the black market.
One of the most alarming things I noticed was how cheap everything was. Just think about the information someone could gather about you if they got access to your Facebook account Ė there is surely no way you would be okay with someone selling access to parts of your private life for one dollar.
But people use more than just Facebook. I would assume that most people aged between 15 and 35 have registered for over 20 different services and maybe use about 10 of them frequently. The services that you hardly ever use are a problem because you often forget that you even have an account there.
The most frequently used accounts probably include the likes of Facebook, Instagram, Skype, Snapchat, Tinder (or other dating services) email, and entertainment services such as Spotify, Netflix, HBO and YouTube. Besides this, you may have an account on a governmental or financial website such as your bank, insurance company, etc. We also need to remember that some of these services use Google or Facebook as authentication, which means you donít use an email and password combination Ė you simply login with your Facebook or Google account.
SERVICE DESCRIPTION PRICE
Gaming Any type of gaming account, Steam, PSN, Xbox etc. $1 per account
Email Email and Password combination from various leaks. Most likely sold in bulk Various
Facebook Direct access to Facebook account $1 per account
Spotify Spotify premium account $2 per account
Netflix Netflix account $1-5 per account
Desktop Username and password for RDP services, including VNC $5-50 per account
Server Username and password for telnet/ssh $5-50 per account
Ecommerce Access to various ecommerce sites, including Airbnb and similar services $10 per account
When looking at the data itís quite mind-blowing that you can basically sell someoneís complete digital life for less than $50 dollars. Weíre not talking about getting access to bank accounts, but you do get access to services where a credit card might be included such as Spotify, Netflix, Facebook and others.
Besides just taking full control of someoneís digital life, access to these services is used by other criminals, for example, to spread malware or conduct phishing attacks.
The level of availability of these hacked or stolen accounts is very impressive; basically anyone with a computer can get access Ė you donít have to be an advanced cybercriminal to know where to find them.