How do file partner programs work?
7.8.2018 Kaspersky Analysis
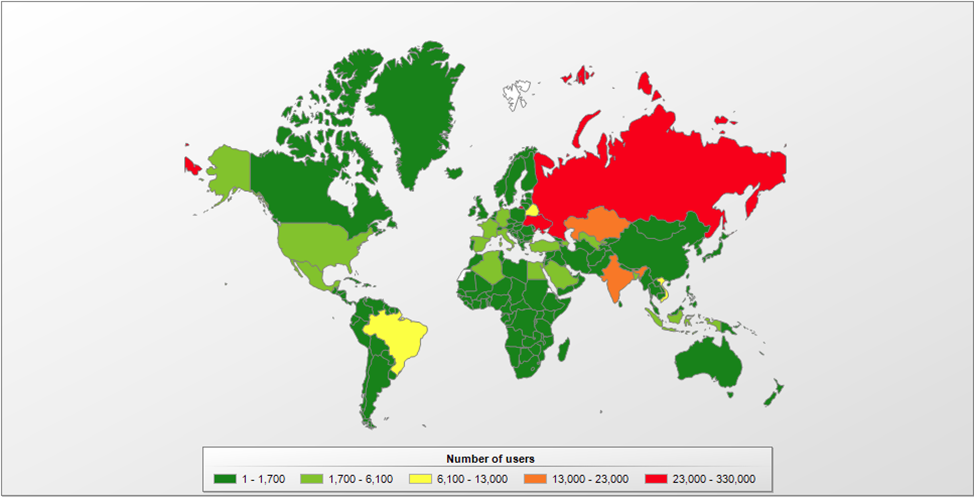
Itís easy to notice if youíve fallen victim to an advertising partner program: the system has new apps that you didnít install, ad pages spontaneously open in the browser, ads appear on sites where they never used to, and so on. If you notice these symptoms on your computer, and in the list of installed utilities there is, for example, setupsk, Browser Enhancer, Zaxar game browser, ďPC optimizersĒ (such as Smart Application Controller or One System Care), or unknown browsers, 99% of the time itís pay-per-install network. Every month, Kaspersky Lab security solutions prevent more than 500,000 attempts to install software that is distributed through advertising partner programs. Most such attempts (65%) happen in Russia.
Geography of attempts to install advertising partner programs apps, June 2018
The partner program acts as an intermediary between software vendors who wish to distribute their apps and owners of file hosting sites. When the user clicks the Download or similar button on such sites, the partner program provides a special installer that downloads the required file, but also determines which set of additional software should be installed on the PC.
File partner programs benefit everyone except the user. The site owner receives money for installing ďpartnerĒ apps, and the partner program organizer collects a fee from the advertisers, who in turn get what they wanted, since their software is installed.
Propagation methods
To illustrate the process, we chose a scheme used by several partner programs. Letís look at a real page offering to download a plugin for the S.T.A.L.K.E.R. game.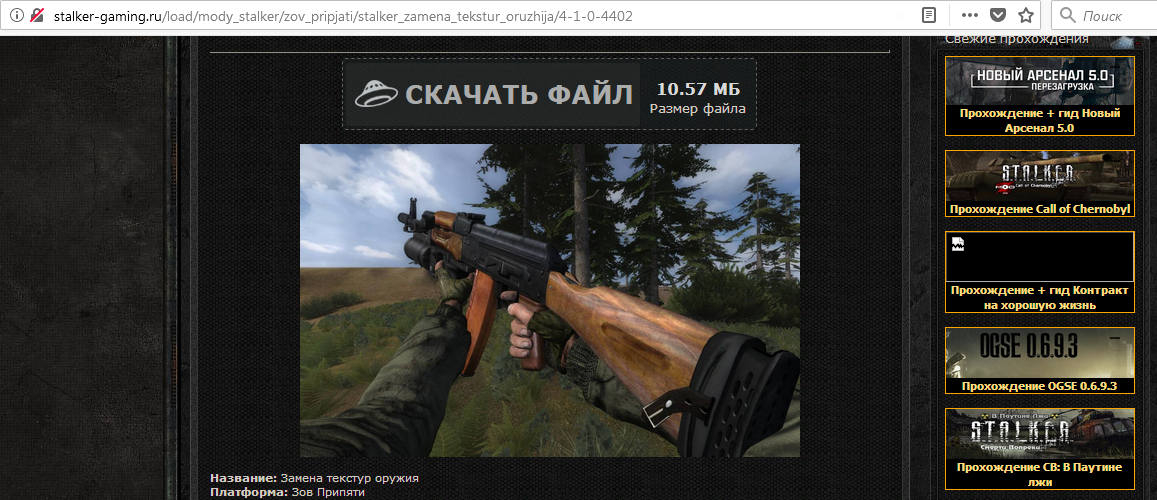
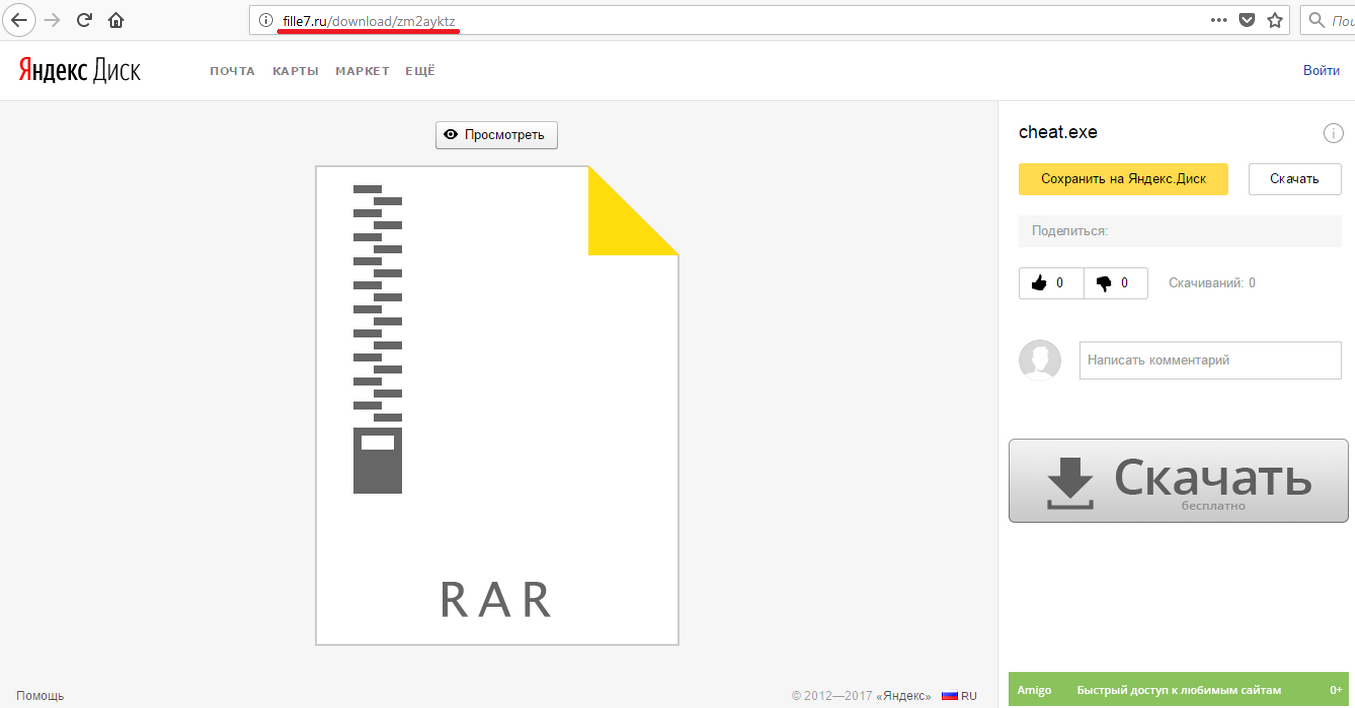
On attempting to download it, the user is redirected to a landing page selected by the administrator of the file-sharing site when loading the file onto the partner program server. Such pages often mimic the interface of popular cloud services: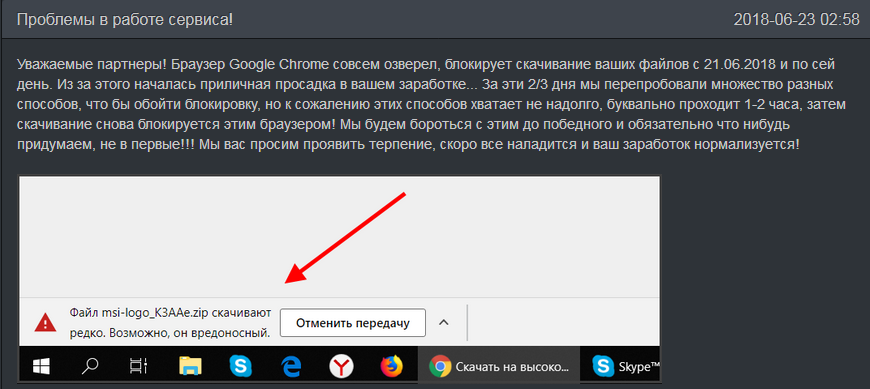
Example of a fake page to which the user is redirected
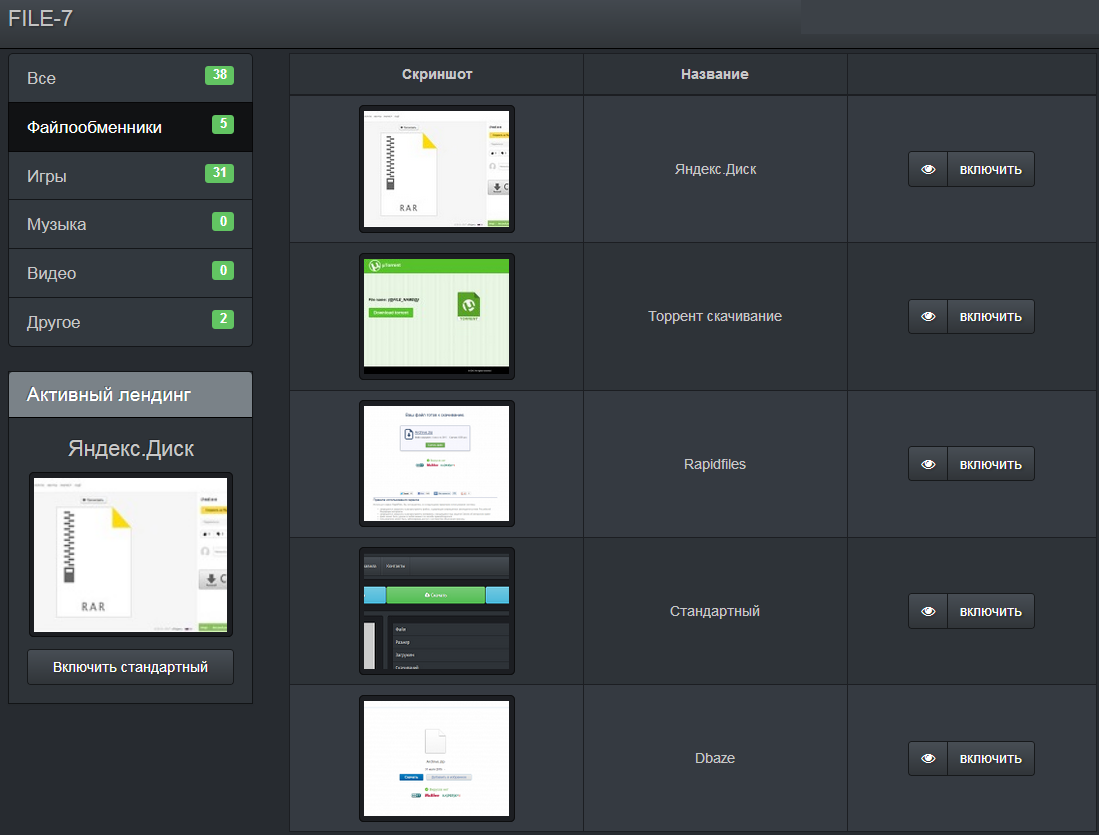
This is what the landing page chooser looks like in the File-7 partner program settings
On clicking the download button, the user receives a file with one of the following formats:
ZIP-archive
Torrent file
ISO image
HTML document
Moreover, archives are often multi-layered and, in many cases, password-protected. Such protective measures and choice of format are not accidental ó partner programs engage a wide range of tricks to prevent browser from blocking the download of their installers.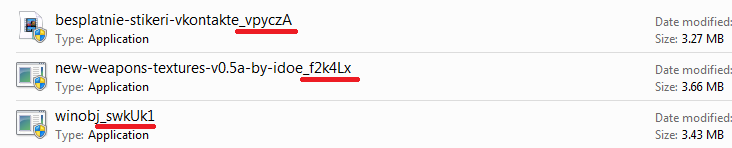
Notification about installer download blocks in a partner programís news feed
The victim is often guided through the loader installation with hints on the download pages as to how to find the program, which password to use for the archive, and how to run the installer. Some versions contain readme attachments with a description of the actions required for the installation. Regardless of the type of file that the user wanted to download, the end product is an executable. Interestingly, every time one and the same file is downloaded, its hash sum changes, and the name always contains a set of some characters.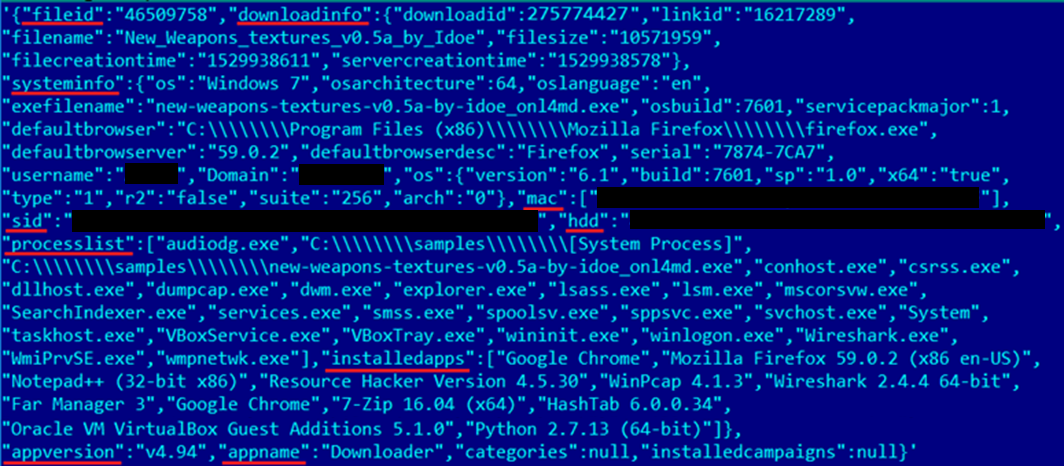
Example of how loader files are named
Communicating with the server
At the preparatory stage, the partner program installer exchanges data with the C&C server. Every message transmitted uses encryption, usually rather primitive: first it is encoded in Base64, then the result is inverted, and again encoded in Base64.
At stage one, the loader transmits information about the downloaded installer, plus data for identifying the victim to the server. The message includes confidential information: user name, PC domain name, MAC address, machine SID, hard drive serial number, lists of running processes and installed programs. Naturally, the data is collected and transmitted without the consent of the device owner.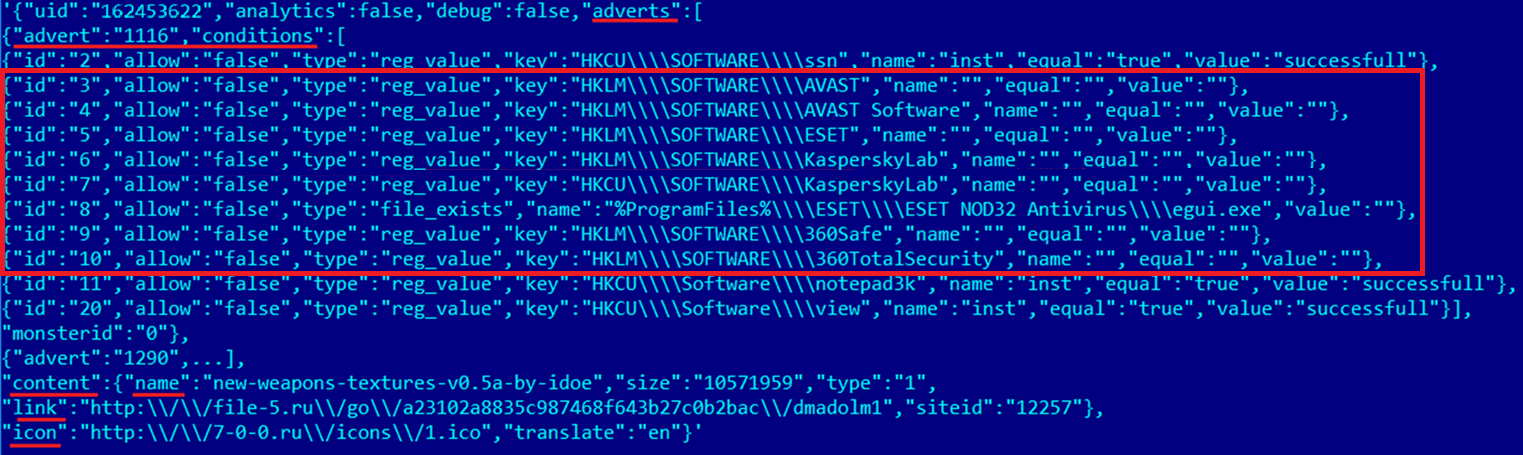
The server responds with a message containing the following information fields:
adverts list ó with the installation conditions for certain partner software
content ó contains the name of the file that the user originally intended to download and a link to it
icon ó contains a link to an icon that is later downloaded and used when starting the graphical interface of the loader.
The installer checks that the conditions listed for each ďadvertĒ are fulfilled. If all conditions are met, the id of the advert is added to the adverts_done list. In the example above, for instance, the registry is checked for paths indicating that one of the selected antiviruses is installed on the computer. If this is the case, the partner software with id 1116 is not added to the adverts_done list and will not subsequently be installed on the userís computer. The purpose of such a check is to prevent the installation of a program that would trigger antivirus software. Next, the generated list is sent to the server:![]()
The server selects several idís (usually 3-5) from the resulting adverts_done list and returns them to the campaigns list. For each id, this list has a checkboxes field containing the text to be displayed in the installation consent window, the url field containing a link to the installer of the given advert, and the parameter field containing a key for installing the unwanted software in silent mode.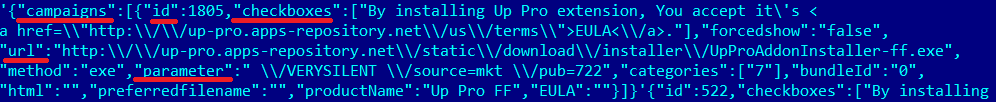
After that, a window opens that simulates the download process in Internet Explorer. The loader does not explicitly notify the user that additional programs will be installed on the computer along with the downloaded file. Their installation can be declined only by clicking a barely discernible slider in the bottom part of the window.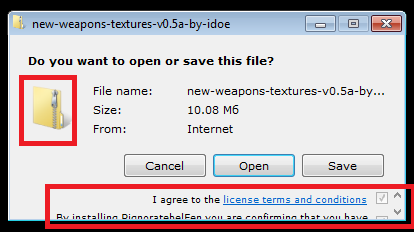
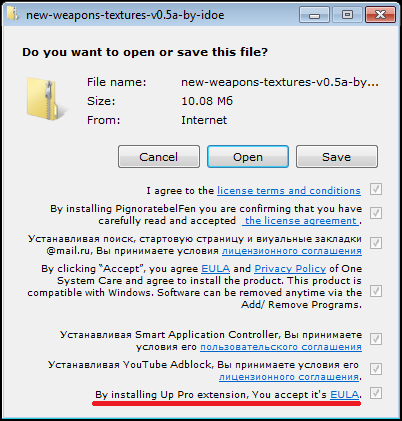
File loader window
During the file download process, software that the user does not deselect is installed inconspicuously. At the final stage of operation, the loader reports to the server about the successful installation of each individual product:![]()
Installed software analysis
By analyzing the loader process, we managed to get some links to various programs that can be installed secretly. Although most of the software relates to different advertising families (thatís how Pbot finds its way onto user devices, for example), that is not the only thing distributed via file partner programs. In particular, around 5% of the files were legitimate browser installers. About 20% of the files are detected as malicious (Trojan, Trojan-Downloader, etc.).
Conclusion
Owners of file-sharing sites that cooperate with similar partner programs often do not even check what kind of content visitors get from the resource. As a result, anything at all can be installed on the userís computer besides legitimate software. Therefore, in the absence of security solutions, such resources need to be used with extreme caution.
Kaspersky Lab products detect the loaders of file partner programs with the following verdicts:
AdWare.Win32.AdLoad
AdWare.Win32.FileTour
AdWare.Win32.ICLoader
AdWare.Win32.DownloadHelper
IoCs:
1F2053FFDF4C86C44013055EBE83E7BD
FE4932FEADD05B085FDC1D213B45F34D
38AB3C96E560FB97E94222740510F725
F0F8A0F4D0239F11867C2FD08F076670
692FB5472F4AB07CCA6511D7F0D14103