4.5.2017 thehackernews Mobil
Your smartphone may have some apps that are continuously listening inaudible, high-frequency ultrasonic sounds from your surroundings and they know where you go, what you like and dislike — all without your knowledge.
Ultrasonic Cross-Device Tracking is a new technology that some marketers and advertising companies are currently using to track users across multiple devices and have access to more information than ever before for ad targeting.
For example, retail stores you visit, a commercial on TV or an advertisement on a web page can emit a unique "ultrasonic audio beacon" that can be picked up by your device’s mobile application containing a receiver.
This information helps advertisers to create your personalized profile and collect your interests by figuring out that both devices probably belongs to you, allowing them to target you with interest-based advertisements.
More & More Apps Have Started Using Ultrasonic Tracking Technology
In fact, while presenting research last week at the IEEE European Symposium on Security and Privacy, security researchers said they discovered 234 Android applications that ask permission to access your smartphone’s microphone to incorporate a particular type ultrasonic beacon to track consumers.
Moreover, the researchers found that 4 of the 35 retail stores they visited in Germany have ultrasonic beacons installed at the entrance.
According to investigators, SilverPush, Lisnr, and Shopkick are three SDKs that use ultrasonic beacons to send messages to the mobile device. While SilverPush allows developers to track users across multiple devices, Lisnr and Shopkick perform location tracking.
The researchers analyzed millions of Android apps and discovered few that were using the Shopkick and Lisnr SDKs, but there were much more that were using the SilverPush SDK.
Serious Privacy Concerns
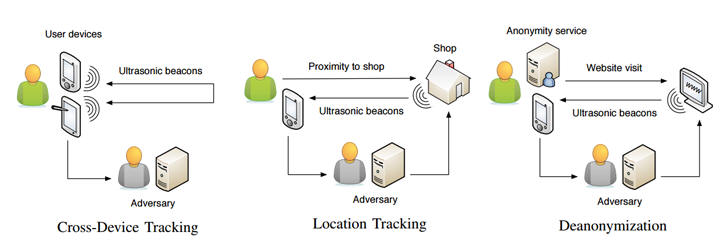
Although cross-device user tracking technologies are currently being used for the legitimate purposes, it has already raised some serious privacy concerns.
Since an app requires no mobile data nor Wi-Fi connection, but only microphone access to listen to beacons, tracking works even when you have disconnected your phone from the Internet.
In fact, a team of researchers last year demonstrated that how ultrasonic sounds emitted by ads on a web page accessed through Tor can be used to deanonymize Tor users by making nearby phones or computers send identification information, such as location and IP, back to advertisers.
"The case of SilverPush emphasizes that the step between spying and legitimately tracking is rather small. SilverPush and Lisnr share essential similarities in their communication protocol and signal processing. While the user is aware of Lisnr location tracking, SilverPush does not reveal the application names with the tracking functionality," research paper reads.
In 2014, Snowden revelations disclosed that how spying agencies were tracking foreign travelers’ movements across the city by capturing their device’ unique MAC address at the airport and then comparing it with the data collected by free WiFi hotspots installed in various coffee shops, restaurants, and retail stores.
This incident could also be another great example, showcasing how intelligence agency could use this ultrasonic cross-device tracking technology to track your movements across the country.
How can You Protect Yourself?
Since you can not stop ultrasonic beacons from emitting sound frequencies around you, the best way to reduce the chance of your smartphone listening for beacons and feed data to a third party is to simply restrict unnecessary permissions you have granted to the apps installed on your device.
In other words, use your common sense.
For example, Skype wants microphone access? Fair enough, as it is necessary for Skype to work as intended. But what about if an app for beauty or clothing store wants microphone access? No way.
To revoke such unnecessary app permissions, some Android phone manufacturers, like One Plus provide a feature called Privacy Guard that allowed its users to block unnecessary app permissions of certain apps on a smartphone that do not have anything to do with the primary function of the apps.
Navigate to Settings → Personal → Privacy → Privacy Guard. Now select any from the list of apps and edit unnecessary permissions you have granted it.
A similar feature has been included in Android 7. Navigate to Settings → Apps → App Permissions. Now edit the privileges you’ve granted each app.
For iOS 10 users: Go to Settings → Privacy → Microphone to see which apps have requested access to it, and which apps you have granted it to.