IoT Botnets Found Using Default Credentials for C&C Server Databases
8.6.2018 thehackernews IoT BotNet
Not following cybersecurity best practices could not only cost online users but also cost cybercriminals. Yes, sometimes hackers don't take best security measures to keep their infrastructure safe.
A variant of IoT botnet, called Owari, that relies on default or weak credentials to hack insecure IoT devices was found itself using default credentials in its MySQL server integrated with command and control (C&C) server, allowing anyone to read/write their database.
Ankit Anubhav, the principal security researcher at IoT security firm NewSky Security, who found the botnets, published a blog post about his findings earlier today, detailing how the botnet authors themselves kept an incredibly week username and password combination for their C&C server's database.
Guess what the credentials could be?
Username: root
Password: root
These login credentials helped Anubhav gain access to the botnet and fetch details about infected devices, the botnet authors who control the botnet and also some of their customers (a.k.a. black box users), who have rented the botnet to launch DDoS attacks.
"Besides credentials, duration limit such as for how much time the user can perform the DDoS, maximum available bots for attack (-1 means the entire botnet army of the botmaster is available) and cooldown time (time interval between the two attack commands) can also be observed," Anubhav wrote.
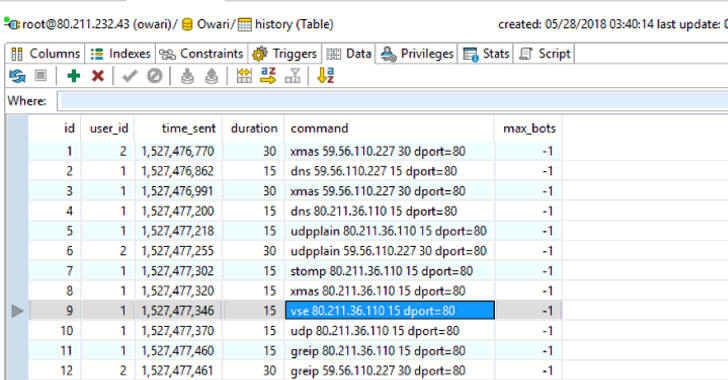
Besides this, Anubhav was also able to see the duration limit of the attack such as for how long a client can perform the DDoS attack, maximum available bots for an attack, and the list of various IPs targeted by the DDoS attack.
Anubhav also found another botnet, which was also built with a version of Owari and its database was also exposed via weak credentials.
The C&C servers of both the botnets were located at 80.211.232.43 and 80.211.45.89, which are now offline, as "botnet operators are aware that their IPs will be flagged soon due to the bad network traffic," Anubhav wrote. "Hence to stay under the radar, they often voluntarily change attack IPs."

