Iran-Linked 'Leafminer' Espionage Campaign Targets Middle East
28.7.18 securityweek CyberSpy
A group of cyberspies believed to be operating out of Iran has targeted government and other types of organizations in the Middle East since at least early 2017, Symantec revealed on Wednesday.
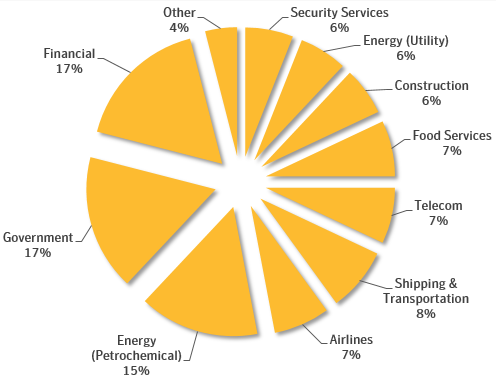
According to the security firm, which tracks the threat actor as Leafminer, this is a previously undocumented campaign. Symantec has detected malware and tools associated with this group on 44 systems in Saudi Arabia, Lebanon, Israel, Kuwait and other countries, but researchers uncovered a list – written in Iran’s Farsi language – of more than 800 targets whose systems were apparently scanned by the attackers. This list shows that the targeted countries also include the United Arab Emirates, Qatar, Bahrain, Egypt and Afghanistan.
A significant percentage of targets were in the financial, government and energy sectors, but several other industries were targeted as well.

Leafminer has used both custom-built malware and publicly available tools in its campaign. Its attack techniques include the use of compromised web servers as watering holes, scanning and exploitation of vulnerable network services, and dictionary attacks aimed at authentication services.
One of the servers used by Leafminer stored 112 files, including malware, tools and log files generated as a result of scans and post-compromise activities.
Some of the tools in Leafminer’s arsenal were linked to other groups with apparent ties to Iran. The hackers have also leveraged widely available tools and exploits, such as the Inception Framework leaked by Shadow Brokers, which includes the infamous EternalBlue exploit.
Leafminer has also developed its own malware, including Trojan.Imecab and Backdoor.Sorgu. Sorgu provides the attackers remote access to compromised machines, while Imecab provides persistent access with a hardcoded password.
Another custom tool used by the threat actor is a modified version of the popular Mimikatz post-exploitation tool. The attackers attempt to avoid detection using a technique dubbed Process Doppelgänging, which researchers disclosed late last year. Symantec has also seen attempts to find systems vulnerable to Heartbleed attacks.
Leafminer also appears to be inspired by the Russia-linked Dragonfly group. A technique used by Dragonfly in watering hole attacks has also been spotted in the Leafminer campaign, researchers said.
Symantec pointed out that the group is “eager to learn from and capitalize on tools and techniques used by more advanced threat actors” and that it has been “tracking developments in the world of cyber security.”
“However, Leafminer’s eagerness to learn from others suggests some inexperience on the part of the attackers, a conclusion that’s supported by the group’s poor operational security. It made a major blunder in leaving a staging server publicly accessible, exposing the group’s entire arsenal of tools,” Symantec said.