NCC Group Releases Open Source DNS Rebinding Attack Tool
21.8.18 securityweek Attack
Cyber security and risk mitigation company NCC Group has released a new open source tool designed to make it easier for penetration testers and others to perform DNS rebinding attacks.
DNS rebinding, an attack method that has been known for more than a decade, can allow a remote hacker to abuse a targeted entity’s web browser to directly communicate with devices on the local network. DNS rebinding can be leveraged to exploit vulnerabilities in services the targeted machine has access to.
Getting the target to access a malicious page or view a malicious ad is often enough to conduct an attack that can lead to theft of sensitive information or taking control of vulnerable systems.
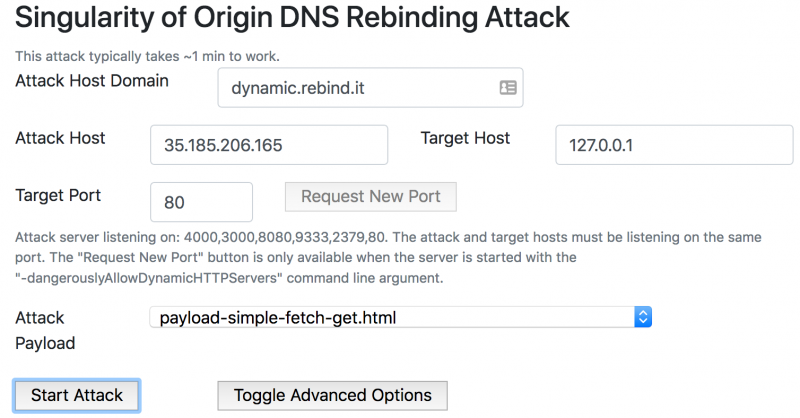
NCC Group on Friday announced the availability of Singularity of Origin, an open source tool designed for conducting DNS rebinding attacks.
“During recent security assessments, we’ve seen applications running on the localhost interface or exposing services on an internal network without authentication. This includes Electron-based applications or applications exposing Chrome Developer Tools and other various debuggers,” NCC Group Senior Security Consultant Roger Meyer said in a blog post.
“Exploiting such services is typically straight forward, but it takes a substantial effort to implement an attack in the context of a security assessment. There are tools available to exploit DNS rebinding vulnerabilities but they pose a number of challenges including the lack of support or documentation. They sometimes do not even work, are very specific and/or do not provide a full exploitation stack, requiring much effort to assemble and integrate all the missing bits and pieces,” Meyer noted.
According to NCC, Singularity provides a complete exploitation stack, including a custom DNS server that allows rebinding the DNS name and IP address of the attacker’s server to the targeted machine, an HTTP server for serving HTML and JavaScript code to targeted users, and various attack payloads. The payloads, which include grabbing an app’s homepage and remotely executing code, can be adapted for new and custom attacks.
NCC Group Senior Security Consultant Gerald Doussot told SecurityWeek that the purpose of Singularity is to provide penetration testers “a simple tool that rapidly exploits a DNS rebinding attack finding and illustrates graphically its potential impact, including remote code execution.”
Singularity also aims to increase awareness of DNS rebinding attacks among application developers and security teams.
“We wanted to increase awareness that DNS rebinding attacks are easy to exploit and damaging but can be remediated with appropriate controls,” Doussot explained.
Singularity source code is available on GitHub, where users can also find detailed instructions on how the tool can be set up and utilized. For demo purposes, NCC Group is also temporarily offering a test instance of the tool.

Google Project Zero researcher Tavis Ormandy earlier this year put the spotlight on DNS rebinding attacks after finding serious vulnerabilities in some popular BitTorrent apps and Blizzard games.
Tripwire researcher Craig Young showed recently how the technique can be used against Google Home and Chromecast devices to reveal a user’s precise physical location. A study published in July by IoT security firm Armis showed that DNS rebinding exposes nearly half a billion devices used by enterprises to attacks.