New Firmware Flaws Resurrect Cold Boot Attacks
14.9.2018 securityweek Attack
Researchers discovered that the firmware running on nearly all modern computers is vulnerable to cold boot attacks that can allow hackers to recover highly sensitive data from the device’s memory.
A cold boot attack is a side-channel attack that allows an attacker with physical access to a computer to obtain encryption keys, passwords and other data from the device’s random access memory (RAM) after a cold or hard reboot (i.e. the computer is restarted suddenly without going through the normal shutdown process). The data can remain in memory for tens of seconds or several minutes, but the time window for an attack can be extended to hours by cooling memory modules with liquid nitrogen or compressed air to slow down the degradation process.
Cold boot attacks have been known for a decade and device manufacturers have implemented mechanisms that should prevent them by overwriting the content of the memory once the system boots again.
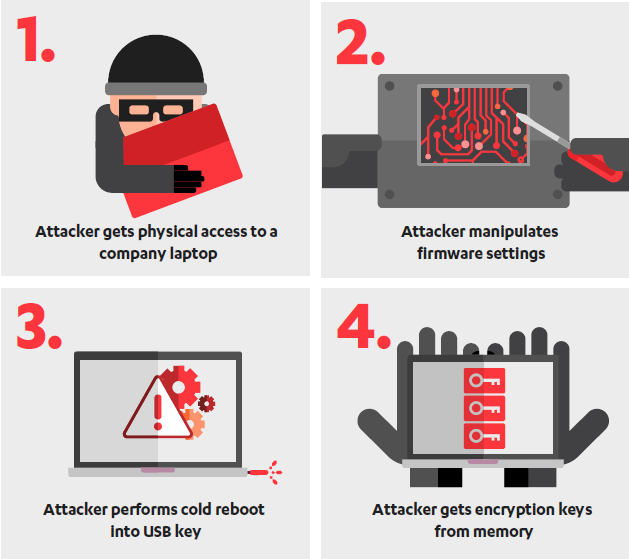
However, researchers at Finland-based cybersecurity firm F-Secure claim to have found a way to resurrect cold boot attacks using weaknesses found in the firmware of many modern computers. Since the method requires physical access to the targeted device, the attack can be highly efficient against laptops, which can more easily be stolen.
The vulnerabilities found by researchers are said to affect devices from several major vendors, including Dell, Lenovo, and Apple. F-Secure has reported its findings to companies such as Intel, Apple and Microsoft, but says there is no easy fix.
F-Secure security consultants Olle Segerdahl and Pasi Saarinen have found a way to perform cold boot attacks by making physical changes to the device’s hardware.
Manipulating the hardware can allow an attacker to disable the feature designed to overwrite memory after a reboot, and configure the device to boot from an external device. The attacker can then perform a cold boot attack using a specially crafted USB device. The USB drive will contain software that allows the attacker to dump the content of the pre-boot memory to a file.

“It’s not exactly easy to do, but it’s not a hard enough issue to find and exploit for us to ignore the probability that some attackers have already figured this out,” Segerdahl explained. “It’s not exactly the kind of thing that attackers looking for easy targets will use. But it is the kind of thing that attackers looking for bigger phish, like a bank or large enterprise, will know how to use.”
Until permanent patches are made available, users can mitigate attacks by configuring devices to shut down or hibernate instead of sleeping when they’re not used, and, in the case of Windows computers, configure BitLocker to prompt for a PIN whenever the device starts.
Implementing these measures still allows cold boot attacks, but ensures that no valuable data is left in the memory.
After being notified by F-Secure, Microsoft updated its BitLocker countermeasures page with instructions on how attacks can be mitigated. Apple said Macs equipped with T2 chips include security mechanisms that should protect devices against cold boot attacks, and advised users of devices without the T2 chips to set a firmware password.
Experts have advised enterprises to implement an incident response plan for scenarios where their devices are lost or stolen.
“A quick response that invalidates access credentials will make stolen laptops less valuable to attackers. IT security and incident response teams should rehearse this scenario and make sure that the company’s workforce knows to notify IT immediately if a device is lost or stolen,” said Segerdahl. “Planning for these events is a better practice than assuming devices cannot be physically compromised by hackers because that’s obviously not the case.”