New Tool Detects Evil Maid Attacks on Mac Laptops
25.4.2018 securityweek Apple
A security researcher has developed a simple tool that helps Mac laptop owners detect unauthorized physical access to their device, also known as an evil maid attack, by monitoring its lid.
The free tool, named DoNotDisturb (DND), was created by Patrick Wardle, co-founder and chief research officer at enterprise macOS security company Digita Security.
Leaving a laptop unattended – for example, leaving it in the hotel room while traveling – puts the device at risk of evil maid attacks. An attacker who has physical access to the targeted device may steal data from it or install malicious software without leaving any obvious evidence behind.
The DND tool attempts to address this issue on Mac laptops by monitoring lid events. A majority of evil maid attacks require the attacker to open the device’s lid. However, there are some types of physical attacks that do not require opening the device’s lid, and the tool works based on the premise that the user closes the device’s lid when leaving it unattended.
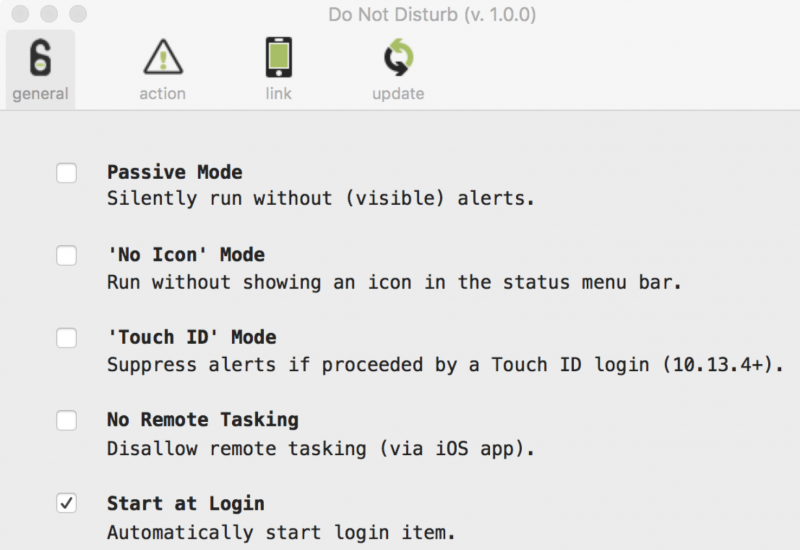
DND is a simple tool, but it does include some interesting features and options. Users can configure the app to start at login and run in passive mode, which means it will run silently without any visible alerts. The “No Icon” mode ensures that an icon is not displayed in the macOS/OS X menu bar, making the tool even stealthier.

The main tool installed on the monitored Mac laptop can be paired with an iOS application that allows the user to view alerts and respond. The iOS app can be used to dismiss an alert, take a picture of the individual using the monitored laptop, and remotely shut down the device. While the macOS tool is free, users have to pay a monthly or yearly subscription fee ($9.99 per year) to use the iOS companion for more than one week. The iOS app is optional, but users will not receive alerts and they cannot take any action remotely in case of an attack.
DND can be configured to take specific actions when the device’s lid is opened. For example, it can execute a script or a binary file, or it can start tracking the attacker’s activities, including new processes, new logins, and USB device insertions.
For users who want to keep DND active on their device at all times but do not want the app to trigger an alert whenever they open the laptop’s lid themselves, the tool can be configured to ignore lid events in specific cases. However, this setting requires a newer model Mac laptop that has a touch bar and is running macOS 10.13.4 or newer.
“When this mode is enabled, DND will ignore any lid open events if proceeded by a successful touch ID authentication event within 10 seconds. The idea is that this allows one to tell DND to trust (or ignore) a lid event that is a result of you (vs. somebody else) opening your laptop,” Wardle explained.
Wardle is well known on the Mac hacking scene thanks to the useful apps he has released and the vulnerabilities he has found in both Apple’s own code and third-party software.