North Korean Attacks on Banks Attributed to 'APT38' Group
5.10.2018 securityweek APT
A report published on Wednesday by FireEye details the activities of a financially motivated threat actor believed to be operating on behalf of the North Korean government.
The group, tracked by FireEye as APT38, focuses on targeting financial institutions, and the company’s researchers estimate that it has stolen at least a hundred million dollars from banks worldwide. It’s believed that the group has attempted to steal over $1.1 billion.
Much of the North Korea-linked cyber activity has been attributed to the notorious Lazarus, but cybersecurity firms have begun to realize that, similar to other countries, there are actually several groups that appear to be launching attacks on behalf of the government. The fact that their tools, techniques and infrastructure often overlap makes it difficult to accurately attribute an operation to a certain group.
FireEye noted that there are many similarities between APT38 and attacks launched by other North Korea-linked groups, including Lazarus and the activity it tracks as TEMP.Hermit. However, it believes APT38’s tools and its tactics, techniques and procedures (TTPs) are distinct enough for it to be tracked separately.
Some other security firms have also noticed that the financially motivated attacks linked to Lazarus may have actually been carried out by a subgroup of Lazarus. Kaspersky has tracked this subgroup as Bluenoroff, while CrowdStrike has dubbed it Stardust Chollima. CrowdStrike has been tracking a total of four subgroups, which it has named Stardust Chollima, Silent Chollima, Labyrinth Chollima and Ricochet Chollima.
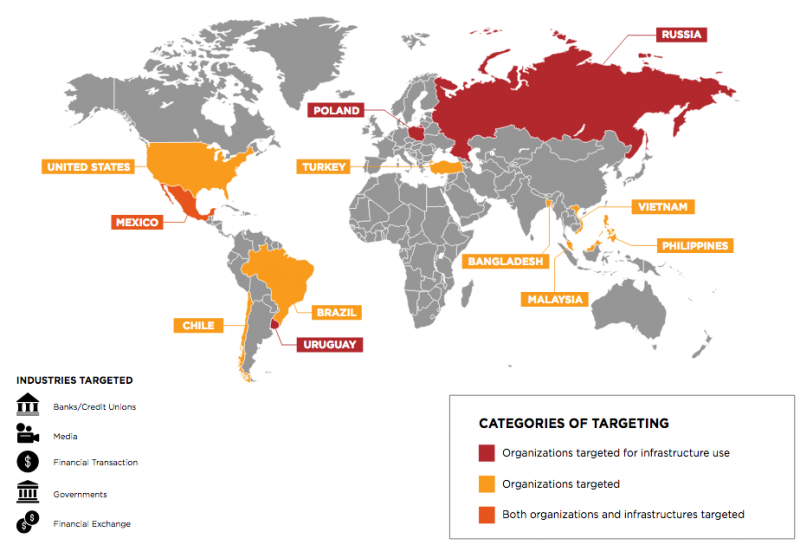
According to FireEye, APT38 has been active since at least 2014 and it has been observed targeting over 16 organizations across 11 countries – researchers believe the actual number of targets may be higher.

Several of these attacks made headlines in the past years and the researchers who analyzed them reported seeing significant similarities to Lazarus campaigns. However, FireEye says the attacks were actually carried out by APT38. The attacks, many of which targeted the SWIFT banking system, were aimed, among others, at Vietnam’s TP Bank in 2015, Bangladesh’s central bank in 2016, Taiwan’s Far Eastern International in 2017, Bancomext in Mexico in 2018, and Banco de Chile also in 2018.
“Attribution to both the ‘Lazarus’ group and TEMP.Hermit was made with varying levels of confidence primarily based on similarities in malware being leveraged in identified operations,” FireEye said in its report on APT38. “Over time these malware similarities diverged, as did targeting, intended outcomes, and TTPs, almost certainly indicating that TEMP.Hermit activity is made up of multiple operational groups primarily linked together with shared malware development resources and North Korean state sponsorship.”
FireEye believes that several other attacks that made the news – involving banks in Africa, Vietnam, Malaysia, the Philippines, Ecuador, and India – may have also been carried out by APT38 based on timing, location, malware, general TTPs and the fact that they targeted SWIFT systems.
Unlike other North Korean threat groups, APT38’s attacks are almost exclusively cyber heists whose likely goal is to raise money for the regime. On the other hand, unlike typical cybercrime operations, APT38’s campaigns are more similar to espionage.
“APT38 executes sophisticated bank heists typically featuring long planning, extended periods of access to compromised victim environments preceding any attempts to steal money, fluency across mixed operating system environments, the use of custom developed tools, and a constant effort to thwart investigations capped with a willingness to completely destroy compromised machines afterwards,” FireEye said.
Experts believe APT38 was created by North Korea as a result of the sanctions imposed on the country. The group was first spotted in February 2014, roughly one year after the UN blocked the regime from making bulk cash transfers and restricting its ties to international banking systems. As more and more sanctions were imposed on North Korea in the following years, APT38 escalated its activities and the frequency of attacks increased.
FireEye has warned that APT38 continues to be active, even after the United States named and charged an alleged North Korean hacker who is said to have been involved in the development of Lazarus tools.