Opsec Mistakes Allowed U.S. to Link North Korean Man to Hacks
8.9.2018 securityweek BigBrothers
A 34-year-old North Korean national has been charged by U.S. authorities over his alleged involvement in the cyberattacks carried out by the Lazarus Group. An affidavit filed by an FBI special agent reveals how investigators linked the man to the notorious threat actor.
Park Jin Hyok has been charged with one count of conspiracy to commit computer fraud and abuse and one count of conspiracy to commit wire fraud. The FBI has added him to its Cyber Most Wanted list and the U.S. Department of Treasury announced sanctions against Park and the North Korean company he worked for.
The criminal complaint, filed on June 8 and made public on Thursday, describes both successful and unsuccessful campaigns of the Lazarus Group, but it focuses on four operations: the 2014 Sony Pictures Entertainment hack, the $81 million cyber heist from the central bank of Bangladesh in 2016, the 2017 WannaCry ransomware attack, and attempts to breach the systems of U.S. defense contractors in 2016 and 2017.
Governments and members of the cybersecurity industry previously linked most of these attacks to North Korea and the Lazarus Group (aka Hidden Cobra) based on shared code and infrastructure. However, the criminal complaint made public on Thursday reveals the apparent operational security (opsec) mistakes that led to investigators accusing Park of being involved in the campaigns.
Park is a North Korean programmer who until 2014, just before the Lazarus attack on Sony, worked in the China-based offices of Chosun Expo Joint Venture, also known as Korea Expo Joint Venture or KEJV. The company, which is said to be a front for the North Korean government, has been linked to the country’s military intelligence and it allegedly supports Pyongyang’s cyber activities.
According to investigators, Park worked at KEJV’s offices in Dalian, Liaoning, China, a province that borders North Korea. A résumé discovered by agents showed that he had been employed as a developer and that he had programming skills in – among many others – Visual C++, the language used to create many of Lazarus’ tools.
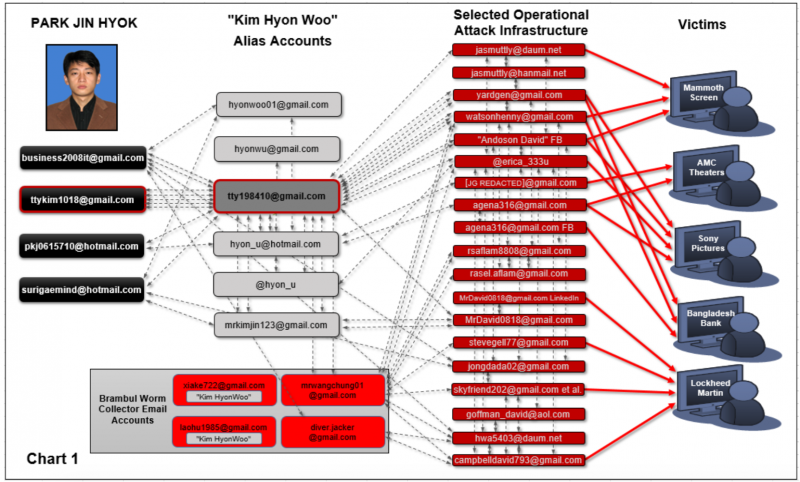
One of the personas used by Lazarus to set up its operations was “Kim Hyon Woo” and several links have been found between this moniker and Park’s online activities, including shared access to files, common names, and common IP addresses.

Agents discovered that one of the email accounts used by Park, ttykim1018(at)gmail.com, and one account used by Kim Hyon Woo, tty198410(at)gmail.com, both had the “tty” string in their names.
But that’s not the only connection. One email had been added to the other’s address book and the Kim Hyon Woo address was the only one allowed to access an archive file saved in a remote file storage account associated with Park’s address.
Park’s address was also used to register a video account that shared profile information with a video account and a payment account created by Kim Hyon Woo.
Lazarus’ tty198410 account was used to register a Gmail account named mrkimjin123(at)gmail.com. This address is noteworthy as it incorporates both the Kim and Jin names.
Another email address, which Park apparently used for official KEJV communications, surigaemind(at)hotmail.com, received and sent messages addressed to and signed by a “Mr. Kim Jin” and “Kim Jin.”
Another important piece of evidence linking Park’s KEJV and personal accounts to Lazarus operational accounts registered by the Kim Hyon Woo persona is the discovery of common IP addresses – based in North Korea and elsewhere – that were used to access the accounts.
Investigators also discovered that the Brambul malware, which the U.S. recently attributed to Hidden Cobra, used various collector email accounts to store information stolen from compromised devices. The same North Korean IP address was used to access one of the Brambul collector accounts and KEJV-linked email accounts.
The complaint also reveals that Park is not the only subject of the FBI’s investigation into the Lazarus attacks and he likely was not the only individual with access to the analyzed accounts.