Plaintext Passwords Often Put Industrial Systems at Risk: Report
24.10.2018 securityweek Cyber
ATLANTA — SECURITYWEEK 2018 ICS CYBER SECURITY CONFERENCE — Plaintext passwords crossing the network, outdated operating systems, direct connections to the Internet, and the lack of automated updates for security solutions often put industrial systems at risk of attacks, according to a new report published on Tuesday by industrial cybersecurity firm CyberX.
The "Global ICS & IIoT Risk Report" is based on the analysis of more than 850 production industrial networks around the world between September 2017 and September 2018.
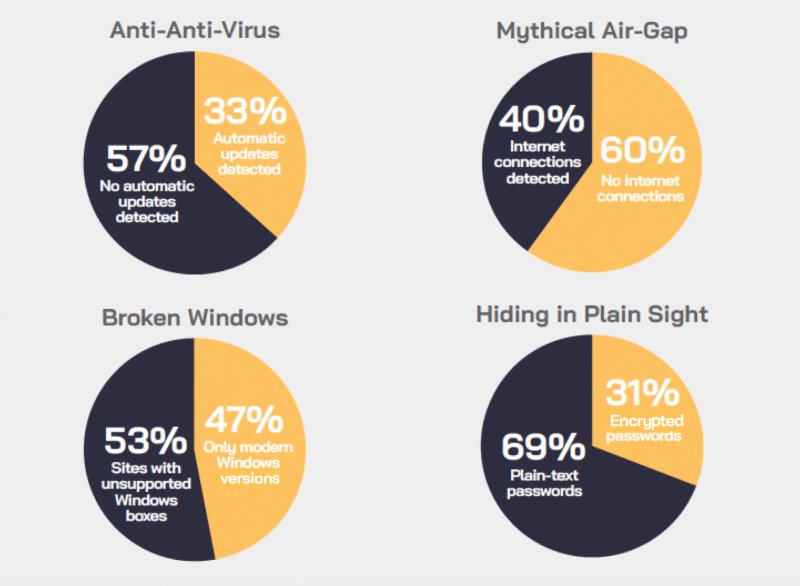
The analysis showed that 69 percent of industrial sites had their networks traversed by plaintext passwords. The problem is often related to the use of legacy protocols, such as SNMP and FTP, which can expose sensitive credentials and make it easier for malicious actors to conduct reconnaissance and hack systems, CyberX warned.
It also found that many industrial companies don’t air-gap systems, and they actually often connect them directly to the Internet. CyberX discovered that 40 percent of industrial sites have at least one connection to the Internet.
In comparison, last year’s report from CyberX revealed that roughly one-third of industrial sites had been connected to the Internet. It’s worth noting that the 2017 report was based on the analysis of 375 OT networks.
Even more worrying is that CyberX claims to have found at least one remotely accessible device in 84 percent of the industrial networks it has analyzed.
“Remote management and access protocols like RDP, VNC, and SSH make it easier for administrators to remotely configure devices — but they also make it easier to attackers with stolen credentials to learn exactly how equipment is configured and eventually manipulate it,” the company said in its 2018 report.
CyberX clarified that this does not necessarily mean these systems are remotely accessibly from the Internet. Instead, it means that malicious actors gaining access to a network could leverage the remote management and access protocols used by admins for legitimate purposes to more easily navigate through the ICS network.
The report also reveals a problem with cybersecurity software, specifically automatic updates. CyberX determined that 57 percent of industrial sites don't have automatic antivirus updates.
Phil Neray, VP of Industrial Cybersecurity at CyberX, told SecurityWeek that the company looks for the network communications typically associated with automatic antivirus signature updates on clients. If these connections are not present, it’s likely that security software is not being updated automatically, but it could also mean that there is no security software whatsoever.
“In some organizations, the updates are performed periodically via sneakernet and USB drives -- such as once per quarter or once per year -- which means that the AV software is providing very weak protections, since signatures are changing on a daily basis,” Neray explained.
He added, “For many years, the ICS automation vendors did not permit installation of any AV on their devices since the AV scanning was believed to cause latency issues that would negatively affect time-critical processes This has now changed and most vendors have certified both AV as well as application whitelisting solutions. So the lack of AV might be a ‘hangover’ effect from the past, or it might be that many organizations haven't bothered to configure an automated update process.”
Another fairly common security issue identified by CyberX during its monitoring was the presence of wireless access points, which it found in 16 percent of industrial sites. The problem with these access points is that if they are misconfigured, they open the door to various types of threats, particularly malware designed to target networking devices, such as the recently discovered VPNFilter.
Finally, the report says obsolete operating systems, such as Windows XP, have been found in over half of the monitored industrial networks.
While many of CyberX’s recent findings are similar to the ones described in the company’s previous report, this is an area where significant improvements have been recorded. In 2017, there were legacy Windows systems in 76 percent of sites and now it has dropped to 53 percent.
The firm’s experts believe this improvement is the result of the WannaCry and NotPetya attacks, which clearly demonstrated to boards and C-level executives that vulnerabilities in their production environments could have significant consequences.

*Updated with clarifications from CyberX regarding remote access