Prioritizing Flaws Based on Severity Increasingly Ineffective: Study
10.11.2018 securityweek Vulnerebility
The large number of vulnerabilities found every year has made it increasingly difficult for organizations to effectively prioritize the security holes exposing their applications and networks, according to a new report published on Wednesday by Tenable.
The company, which helps organizations reduce their cyber risk, has conducted a detailed analysis of the flaws discovered last year and in the first half of 2018.
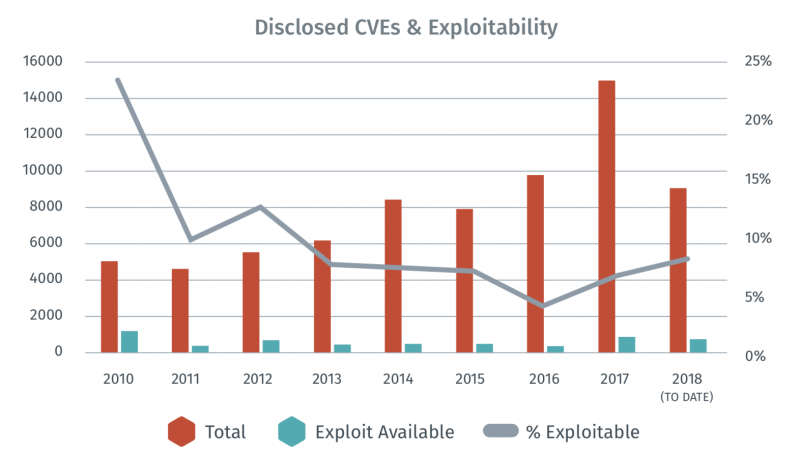
Tenable has counted all the common vulnerabilities and exposures (CVE) identifiers assigned last year and determined that there were 15,038 new flaws discovered, compared to 9,837 in 2016, which represents an increase of more than 50%. There has been an increase of 27% in the number of vulnerabilities disclosed in the first half of 2018 compared to the same period of 2017, and the security firm estimates that this year the count could reach 18,000-19,000.
In 2017, over half of the vulnerabilities were rated “critical” or “high severity” - CVSSv3 assigns higher scores to flaws compared to CVSSv2. However, exploits were only made public for 7% of the total and only a small subset of those were actually weaponized and exploited by malicious actors.

According to Tenable, enterprises find, on average, 870 unique vulnerabilities per day, including newly discovered flaws and unpatched issues that were disclosed previously. Of all the vulnerabilities discovered so far, roughly 12% have been rated “critical,” which means organizations have to deal with roughly 100 weaknesses per day even if they prioritize only the most serious findings.
“Trying to remediate and mitigate all disclosed vulnerabilities, even when prioritizing High and Critical vulnerabilities, is an exercise in futility, as our data shows,” Tenable said in its report.
“Managing vulnerabilities at volume and scale across different teams requires actionable intelligence. Otherwise, we’re not making informed decisions – we’re guessing. An intelligence deficit in vulnerability management is causing real-world implications – with 34 percent of breached organizations stating they were aware of the vulnerability that led to their breach before it happened,” it added.
The company has found that roughly a quarter of all 107,000 CVEs assigned until October 2018 impact enterprise environments and nearly two-thirds of the vulnerabilities found by enterprises are “high severity” or “critical.”
The security holes most commonly found in enterprises impact software from Microsoft, Google, Oracle, and Adobe, including the .NET Framework, Chrome, Java, Internet Explorer, Flash Player and Outlook. More than a quarter of enterprises are also exposed to attacks due to issues related to SSL.
“The problem is we have too much information and not enough intelligence. Turning information into intelligence requires interpretation and analysis – something that doesn’t scale easily. The solution lies in operationalizing intelligence based on your organization’s unique characteristics – your most critical digital assets and vulnerabilities,” Tenable said.
The complete Tenable Vulnerability Intelligence Report is available on the company’s website in PDF format.