Researchers Defeat AMD's SEV Virtual Machine Encryption
7.6.18 thehackernews Safety
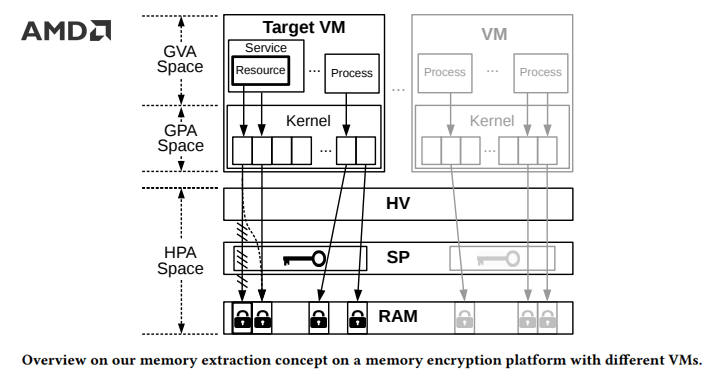
German security researchers claim to have found a new practical attack against virtual machines (VMs) protected using AMD's Secure Encrypted Virtualization (SEV) technology that could allow attackers to recover plaintext memory data from guest VMs.
AMD's Secure Encrypted Virtualization (SEV) technology, which comes with EPYC line of processors, is a hardware feature that encrypts the memory of each VM in a way that only the guest itself can access the data, protecting it from other VMs/containers and even from an untrusted hypervisor.
Discovered by researchers from the Fraunhofer Institute for Applied and Integrated Security in Munich, the page-fault side channel attack, dubbed SEVered, takes advantage of lack in the integrity protection of the page-wise encryption of the main memory, allowing a malicious hypervisor to extract the full content of the main memory in plaintext from SEV-encrypted VMs.
Here's the outline of the SEVered attack, as briefed in the paper:
"While the VM’s Guest Virtual Address (GVA) to Guest Physical Address (GPA) translation is controlled by the VM itself and opaque to the HV, the HV remains responsible for the Second Level Address Translation (SLAT), meaning that it maintains the VM’s GPA to Host Physical Address (HPA) mapping in main memory.
"This enables us to change the memory layout of the VM in the HV. We use this capability to trick a service in the VM, such as a web server, into returning arbitrary pages of the VM in plaintext upon the request of a resource from outside."
"We first identify the encrypted pages in memory corresponding to the resource, which the service returns as a response to a specific request. By repeatedly sending requests for the same resource to the service while re-mapping the identified memory pages, we extract all the VM's memory in plaintext."
During their tests, the team was able to extract a test server's entire 2GB memory data, which also included data from another guest VM.
In their experimental setup, the researchers used a with the Linux-based system powered by an AMD Epyc 7251 processor with SEV enabled, running web services—the Apache and Nginx web servers—as well as an SSH server, OpenSSH web server in separate VMs.
As malicious HV, the researchers used the system's Kernel-based Virtual Machine (KVM) and modified it to observe when software within a guest accessed physical RAM.
While Apache and Nginx web servers the extraction of memory data was high (at a speed of 79.4 KB/sec), OpenSSH had a higher response time which reduced the extraction speed to only 41.6 KB/sec.
"Our evaluation shows that SEVered is feasible in practice and that it can be used to extract the entire memory from an SEV-protected VM within a reasonable time," the researchers said. "The results specifically show that critical aspects, such as noise during the identification and the resource stickiness are managed well by SEVered."
The researchers also recommended a few steps AMD could take to isolate the transition process between the host and Guest Physical Address (GPA) to mitigate the SEVered attack.
The best solution is to provide "a full-featured integrity and freshness protection of guest-pages additional to the encryption, as realized in Intel SGX. However, this likely comes with a high silicon cost to protect full VMs compared to SGX enclaves."
However, securely combine the hash of the page’s content with the guest-assigned GPA could be a low-cost, efficient solution, which ensures "pages cannot easily be swapped by changing the GPA to HPA mapping."
The research was carried out by four Fraunhofer AISEC researchers—Mathias Morbitzer, Manuel Huber, Julian Horsch and Sascha Wessel—which has been published in their paper [PDF] titled, "SEVered: Subverting AMD’s Virtual Machine Encryption."
