Shipping Giant COSCO Hit by Ransomware
26.7.18 securityweek Ransomware
Chinese state-owned shipping and logistics company COSCO was reportedly hit by a piece of ransomware that disrupted some of its systems in the United States.
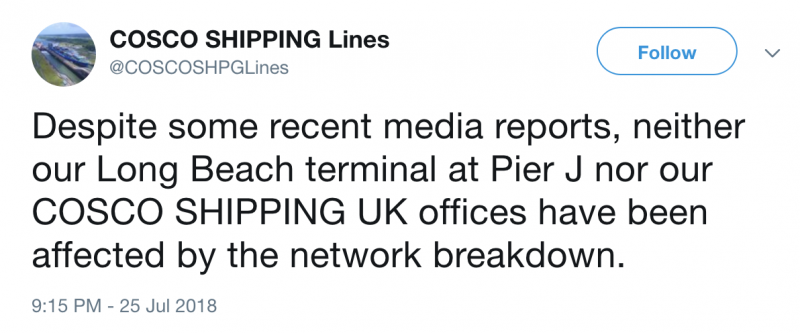
COSCO, one of the world’s largest shipping companies, described the incident as a “local network breakdown” in the Americas region. The firm says it has suspended connections with other regions while it conducts an investigation.
“So far, all vessels of our company are operating normally, and our main business operation systems are stable. We are glad to inform you that we have taken effective measures and aside from the Americas region, the business operation within all other regions will be recovered very soon. The business operations in the Americas are still being carried out, and we are trying our best to make a full and quick recovery,” COSCO stated.
While COSCO’s statement does not mention a cyberattack, the company told some news outlets that the disruptions are the result of a ransomware attack.

According to researcher Kevin Beaumont, the impacted infrastructure hosts COSCO’s website (cosco-usa.com), phone and email systems, and WAN and VPN gateways. The expert pointed out that the company resorted to using Twitter and Yahoo email accounts to communicate with customers.
The company’s U.S. systems still appear to be offline at the time of writing. It’s unclear if this was a targeted attack or if COSCO’s systems became infected as part of an opportunistic ransomware campaign.
If COSCO was truly hit by ransomware – it’s not uncommon for companies to misclassify cyber threats in the initial phases of an investigation – it would not be the first time a major shipping company has fallen victim to this type of attack.
One of the victims of last year’s NotPetya campaign, which caused losses of hundreds of millions of dollars for several major companies, was Danish shipping giant A.P. Moller–Maersk, which revealed that the incident forced its IT team to reinstall software on its entire infrastructure, including 45,000 PCs and 4,000 servers.
As a result of the attack, Maersk employees had to manually process 80 percent of the work volume while systems were being restored and the incident cost the company over $300 million.