Snapchat Source Code Leaked
8.8.2018 securityweek Apple
iOS Update Led to Snapchat Source Code Leak
Hackers obtained some source code for the popular messaging application Snapchat and made it public on GitHub, claiming that they were ignored by the app’s developer.
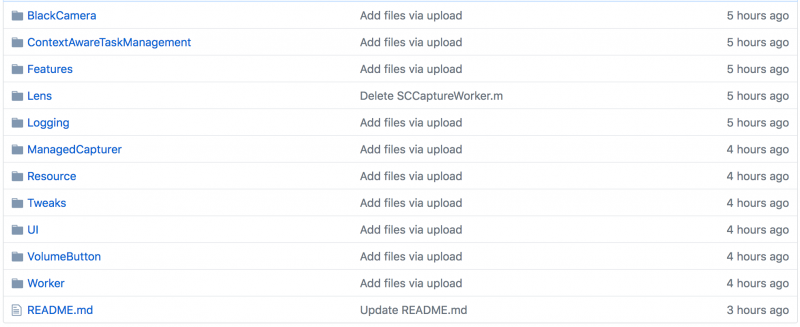
The source code appears to be for the frontend of Snapchat for iOS. The company behind Snapchat, Snap Inc., has confirmed that the code is genuine by getting GitHub to remove it using a DMCA (Digital Millennium Copyright Act) request.
When users file a DMCA request with GitHub, they are instructed to provide a detailed description of the original copyrighted work that has allegedly been infringed. In this section, a Snap representative wrote, “Snapchat source code. It was leaked and a user has put it in this GitHub repo. There is no URL to point to because Snap Inc. doesn't publish it publicly.”

Snapchat told several news websites that the leak is a result of an iOS update made in May that exposed a “small amount” of its source code. The issue has been addressed and the company says the incident has not compromised its application and had no impact on the Snapchat community.
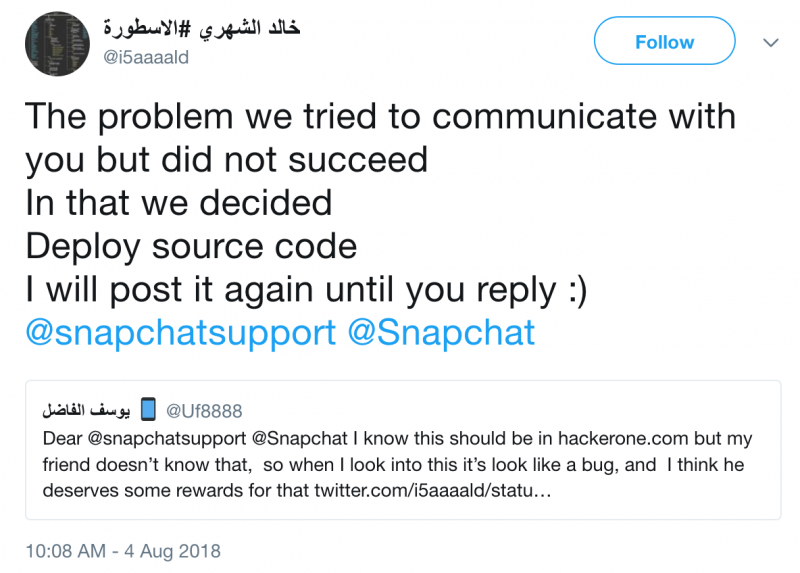
Messages posted on Twitter by the individuals who appear to be behind the source code leak suggest that they are expecting some sort of “reward” from Snapchat. It’s not uncommon for researchers who find vulnerabilities to quarrel with vendors over the impact or severity of a bug. However, Snapchat appears to be the target of an extortion attempt considering that the hackers say they will continue posting the code.
At least two individuals, allegedly based in Pakistan and France, appear to be involved in the incident. They have been posting messages written in Arabic and English on Twitter.
While Snap says the code posted online has been removed, at least two forks (i.e. copies) exist on GitHub and they suggest that the code has been online since May 24. A few hours before this article was published, the original hackers also re-uploaded the code to GitHub.
Snapchat does have an official bug bounty program powered by HackerOne and the company has been known to award significant rewards for critical vulnerabilities. Last year, two researchers earned a total of $20,000 for finding exposed Jenkins instances that allowed arbitrary code execution and provided access to sensitive data.