Spam and phishing in Q1 18
27.5.18 Kaspersky Analysis Phishing
Quarterly highlights
Data leaks
Early 18 will be remembered for a series of data leak scandals. The most high-profile saw Facebook CEO Mark Zuckerberg grilled by US Congress, with many public figures supporting the Delete Facebook campaign. As a result, Zuckerberg promised to get tough and make it more difficult to harvest data from third-party apps.
But the buck doesn’t stop entirely with the tech giants—personal data often ends up in cybercriminal hands due to user carelessness. Some techniques may be timeworn, but one in particular still reels in the victims: Facebook users are one of the juiciest targets for cyberfraudsters looking to launch mass phishing attacks. Last year Facebook was one of the Top 3 most exploited company names. The schemes are numerous, but fairly standard: the user is asked to “verify” an account or lured into signing into a phishing site on the promise of interesting content.
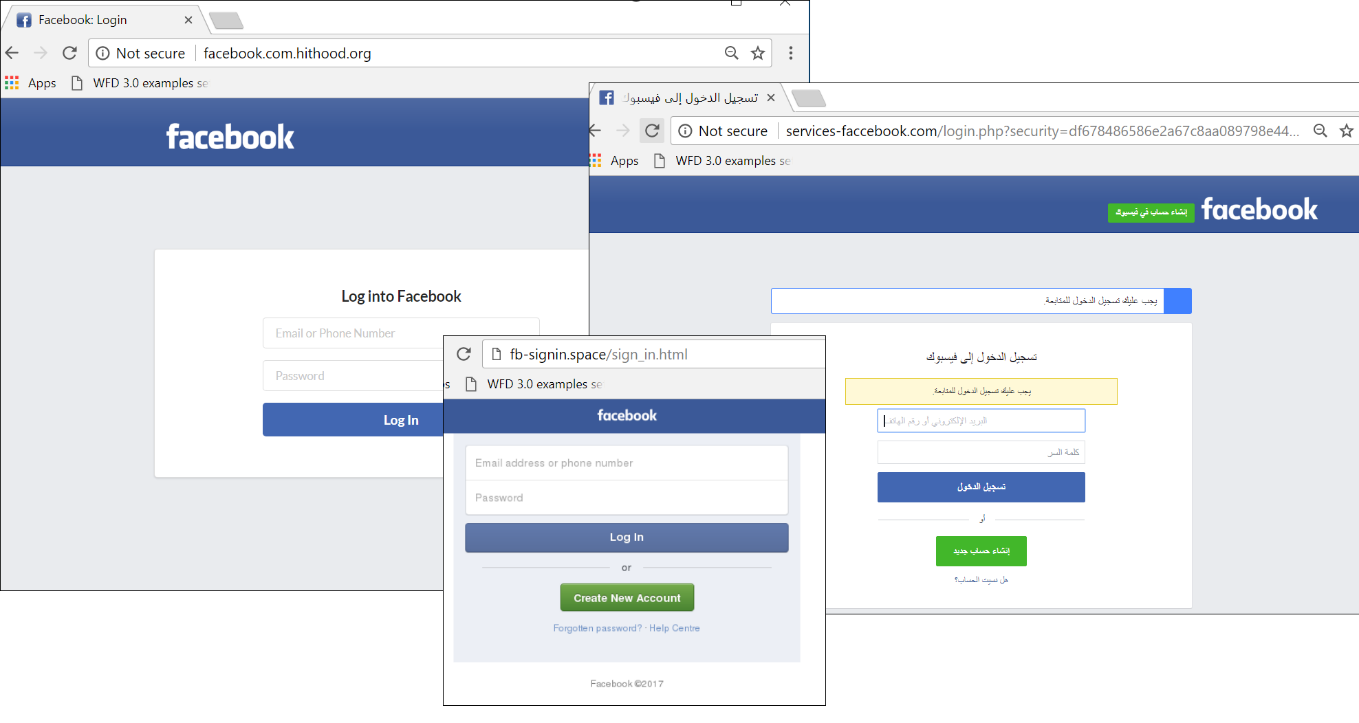
Examples of phishing pages mimicking Facebook login
Fake pages such as these exist in all languages supported by the social media. Sometimes the correct localization is selected automatically based on the victim’s IP address.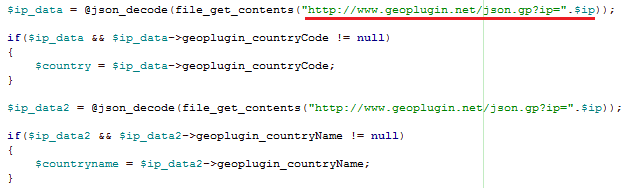
Example of code used by cybercriminals to determine the victim’s location and adapt the phishing page
Data often falls into the hands of cybercriminals through third-party apps that users themselves give access to their accounts and sometimes even allow to post messages on their own behalf.
In early March, for instance, several hundred VKontakte users were hit when third parties gained access to their private correspondence. This happened as a result of apps using the social network’s open API to request access to personal data without guaranteeing its safe storage and use.
In the headline-grabbing case of Cambridge Analytica’s This Is Your Digital Life app, users also handed over personal information voluntarily. Carelessness is the culprit: many people are unaware of just how much data they give away in personality quizzes.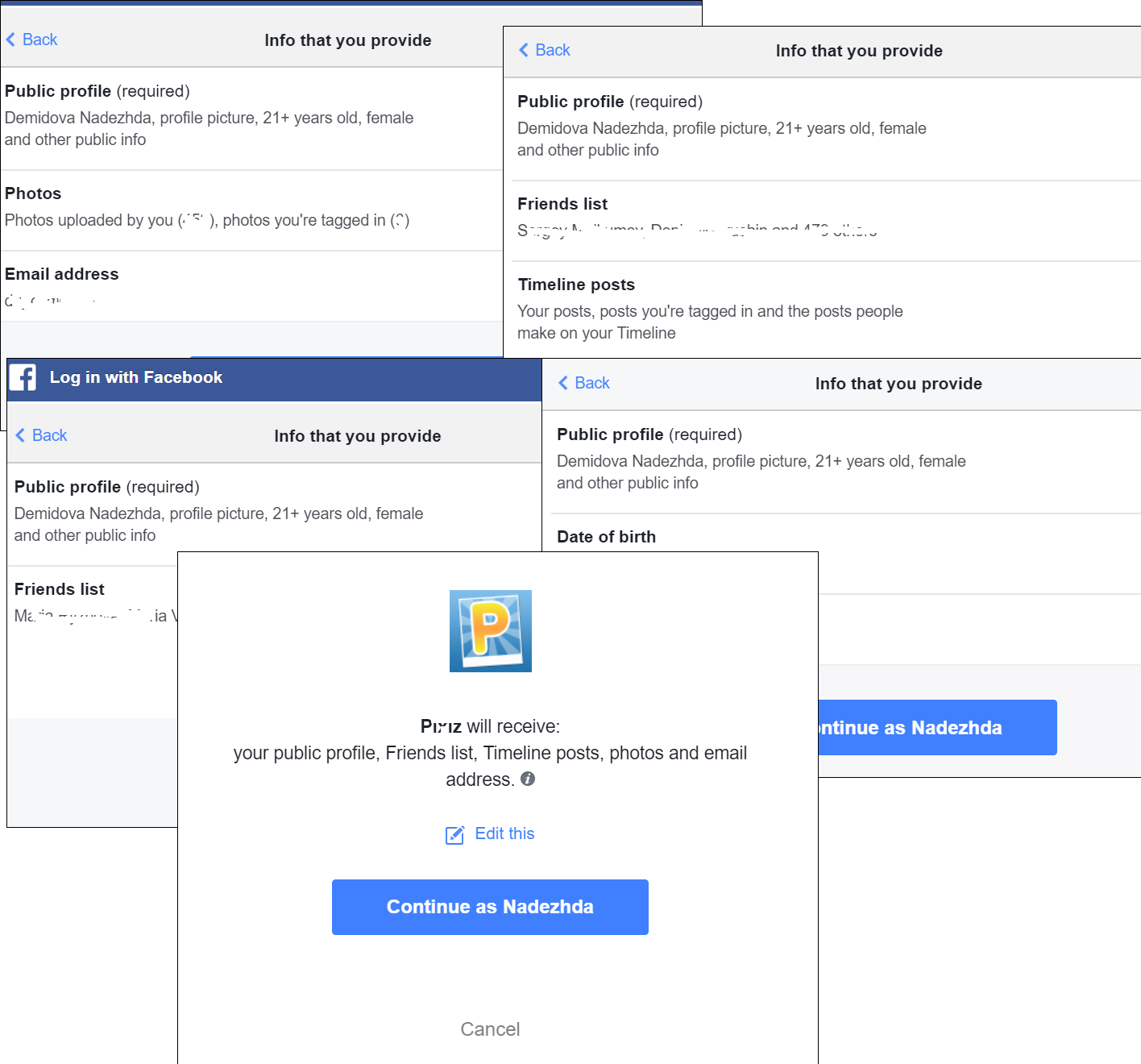
Social media quizzes often ask for a lot of user data,
Remember that cybercriminals often use social media to spread malicious content. For example, we wrote about fake airline giveaways, adult video spam, and even an Alberto Suárez phishing petition.
Another major personal data story was the appearance in Russia of the GetContact app for smartphones, which not only tells users who’s calling, but shows the names under which their contacts are saved in other app users’ phone books. For this, the program needs to be fed not just the user’s own data, but the entire address book (photos, email addresses, even conversation history). That earned GetContact a ban in several countries (even before it appeared in Russia).
Telegram, ICOs, cryptocurrencies
In Q1 a battle royale broke out over the Telegram messenger. It all began late last year with talk of an upcoming ICO. That provided the backdrop for cybercriminals to create, which by the end of Q1 had allegedly raked in as much as the company’s rumored private ICO.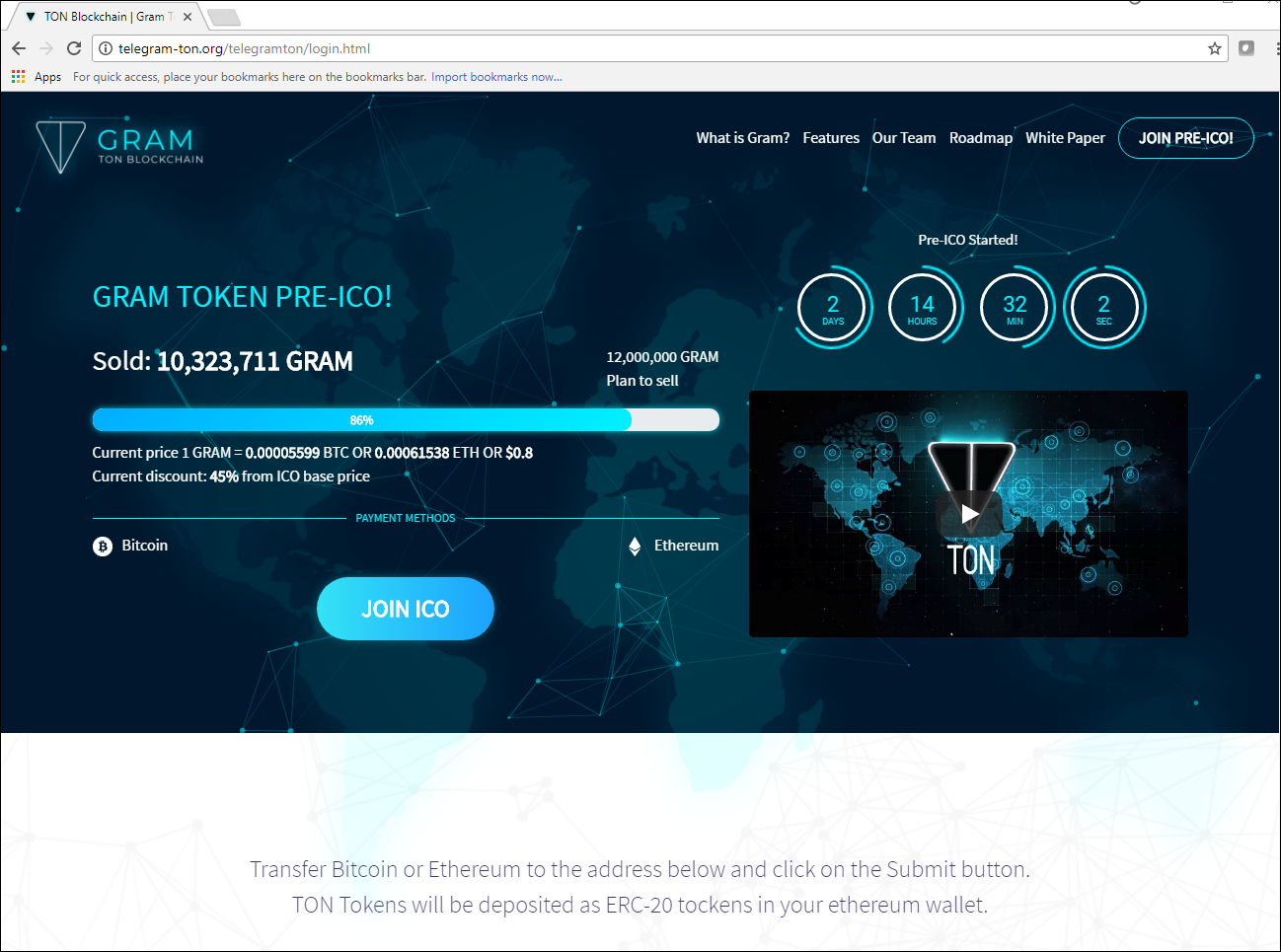
Fake site offering the chance to participate in the Telegram ICO
That was followed by a wave of phishing mailshots to owners of major Russian channels in Telegram. An account under the name Telegram (or something similar) sent a message informing potential victims that suspicious activity had been detected on their account and that confirmation was required to avoid having it blocked. A link was provided to a phishing site masquerading as the login page for the web version of Telegram.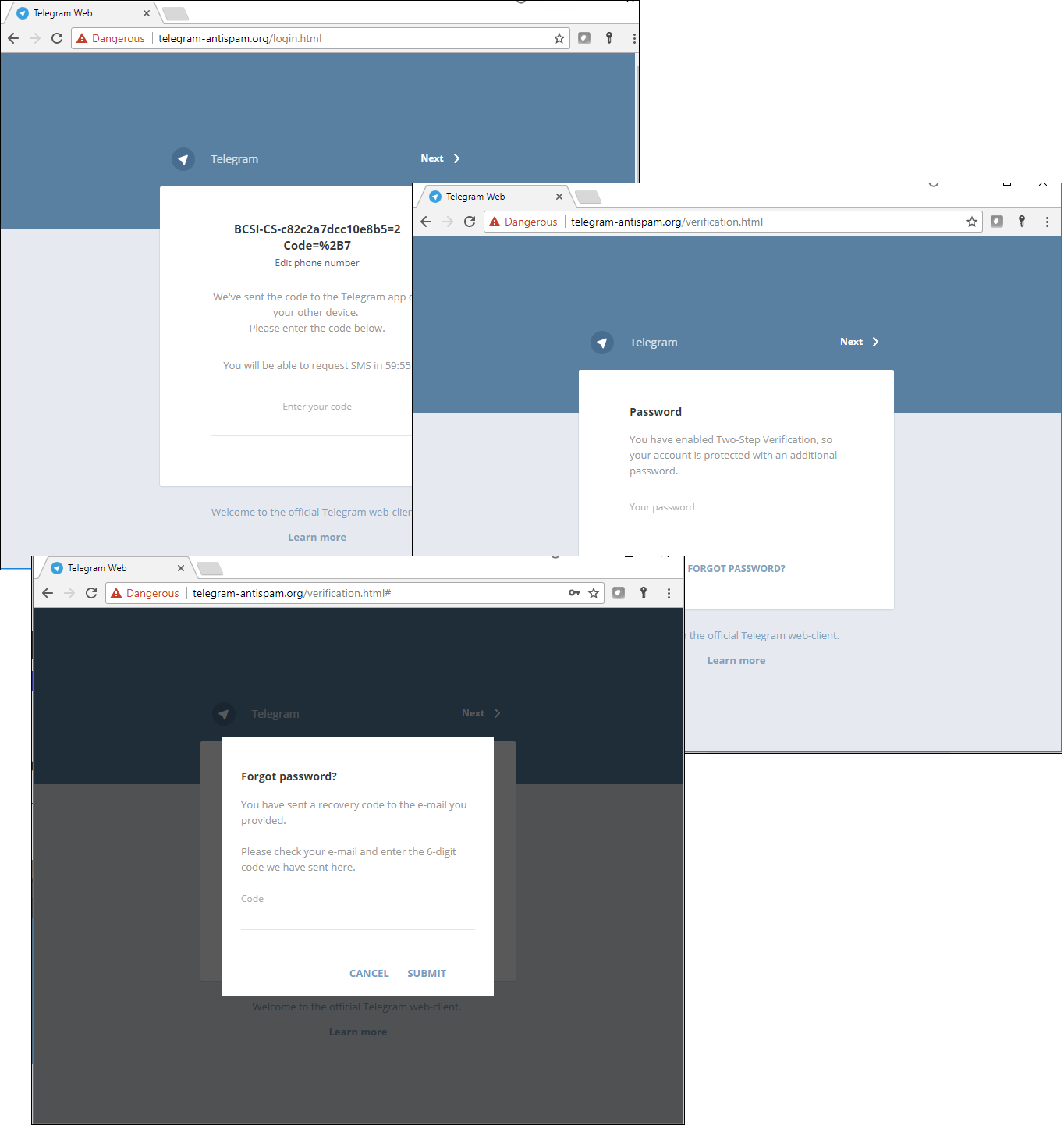
Phishing site mimicking the web version of the Telegram app
If the victim agreed to fill out the form, the cybercriminals gained access to their account, plus the ability to link it to another phone number.
Another spike in scamming activity was recorded when the Internet was buzzing about the imminent takedown of the messenger in Russia. And when the messenger suffered a power outage in a server cluster, it was widely perceived as the start of the ban. Replying to Pavel Durov’s tweet about the malfunction, enterprising cybercriminals offered compensation on his behalf in cryptocurrency. To claim it, users had to follow a link to a site where they were asked to transfer a sum of money to a specified wallet number to receive their “compensation.”
But Telegram does not have a monopoly over the cryptocurrency topic this quarter. We repeatedly encountered phishing sites and email messages exploiting the launch of new ICOs. Cryptocurrency scams often bring in millions of dollars, which explains why cybercriminals are so fond of them.
For instance, on January 31–February 2 the Bee Token startup held an ICO for which participants had to register in advance on the project website, specifying their email address. Cybercriminals managed to get hold of a list of email addresses of potential investors and send out a timely invitation containing e-wallet details for making Ethereum-based investments.
Phishing email supposedly sent from the ICO organizers
123,3275 ether were transferred to this wallet (around $84,162.37). Fraudsters also set up several phishing sites under the guise of the platform’s official site.
A similar scam occurred with the Buzzcoin ICO. The project website invited users to subscribe to a newsletter by leaving an email address. The day before the official ICO start, subscribers received a fraudulent message about the start of pre-sales with a list of cryptowallets to which money should be transferred.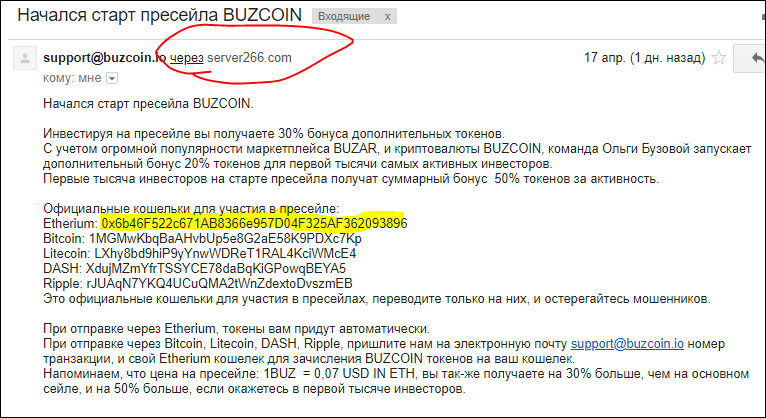
Phishing email supposedly sent from the ICO organizers
Cybercriminals scooped about $15,000 before the organizers took action.
GDPR
One measure that addresses user safety is the General Data Protection Regulation (GDPR), a general policy on the protection and privacy of individuals. This EU regulation has a direct bearing on all companies that process data belonging to EU residents, and therefore has an international scope. The GDPR becomes enforceable on May 25 this year and stipulates large fines (up to EUR 20 million or 4% of annual revenue) for companies whose information activity does not comply with the regulation.
Such a landmark event in the IT world could hardly fail to attract cybercriminals, and in recent months (since the end of last year) we have registered a large number of spam emails related one way or another to the GDPR. It is generally B2B spam—mostly invitations to paid seminars, webinars, and workshops promising to explain the ins and outs of the new regulation and its ramifications for business.
We also came across spam offers to install on the target company’s main website or landing page special fee-based software providing web resources with everything necessary to comply with the new rules. Moreover, the site owner would supposedly be insured against problems relating to user data security.
Spam traffic also contained offers to acquire ready-made specialized databases of individuals and legal entities broken down by business division or other criteria. The sellers had no scruples about stressing that all addresses and contacts for sale were already GDPR-compliant. In fact, harvesting user data and reselling it to third parties without the consent of the owners and data carriers violates not only this regulation, but also the law in general.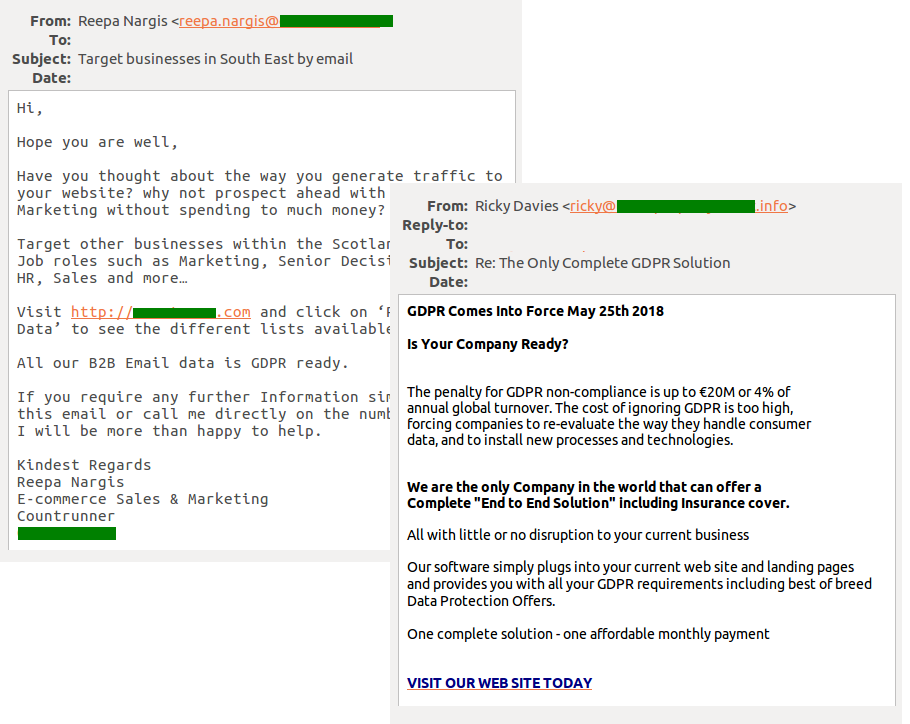
Example of a spam message exploiting the GDRP topic
Note that legitimate mailers also became more active. They are already sending notices to users describing the new rules and asking for consent to use and process their data under the new policy. When the new regulation enters into force, the number of such notices will skyrocket, so we predict a surge in scam mailings aimed at obtaining personal info and authentication data for access to various accounts. We urge users to pay close attention to the new regulation and carefully study any notifications related to it. Links should be checked before clicking: they should not contain redirects to third-party sites or domains unrelated to the service on whose behalf the message was sent.
Political spam
In the runup to the Russian presidential elections, we observed a range of political spam, including messages promoting or slurring various candidates. The election topic was used for fraud: cybercriminals sent email messages offering a financial reward for taking part in public opinion polls, as a result of which money ended up being transferred in the opposite direction.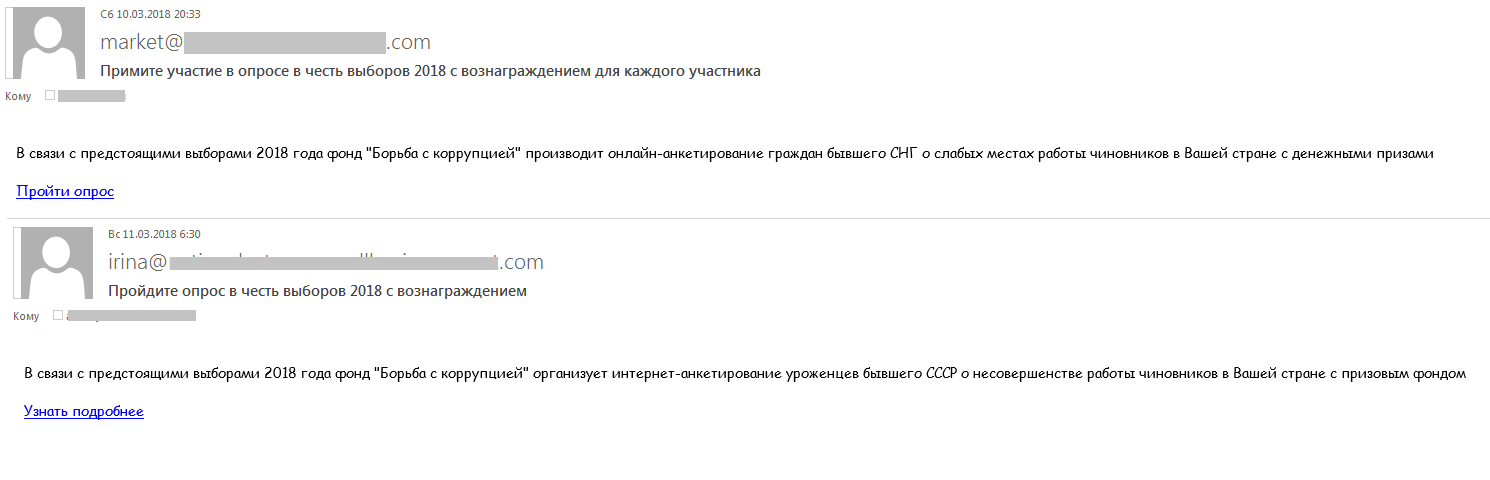
Example of a message inviting recipients to take part in a poll
Phishing for taxpayers
Every country has its own tax year, but as a rule the most active period for dealing with tax services comes at the start of the year. In Q1 we registered many phishing pages mimicking the IRS, HMRC, and other countries’ tax services.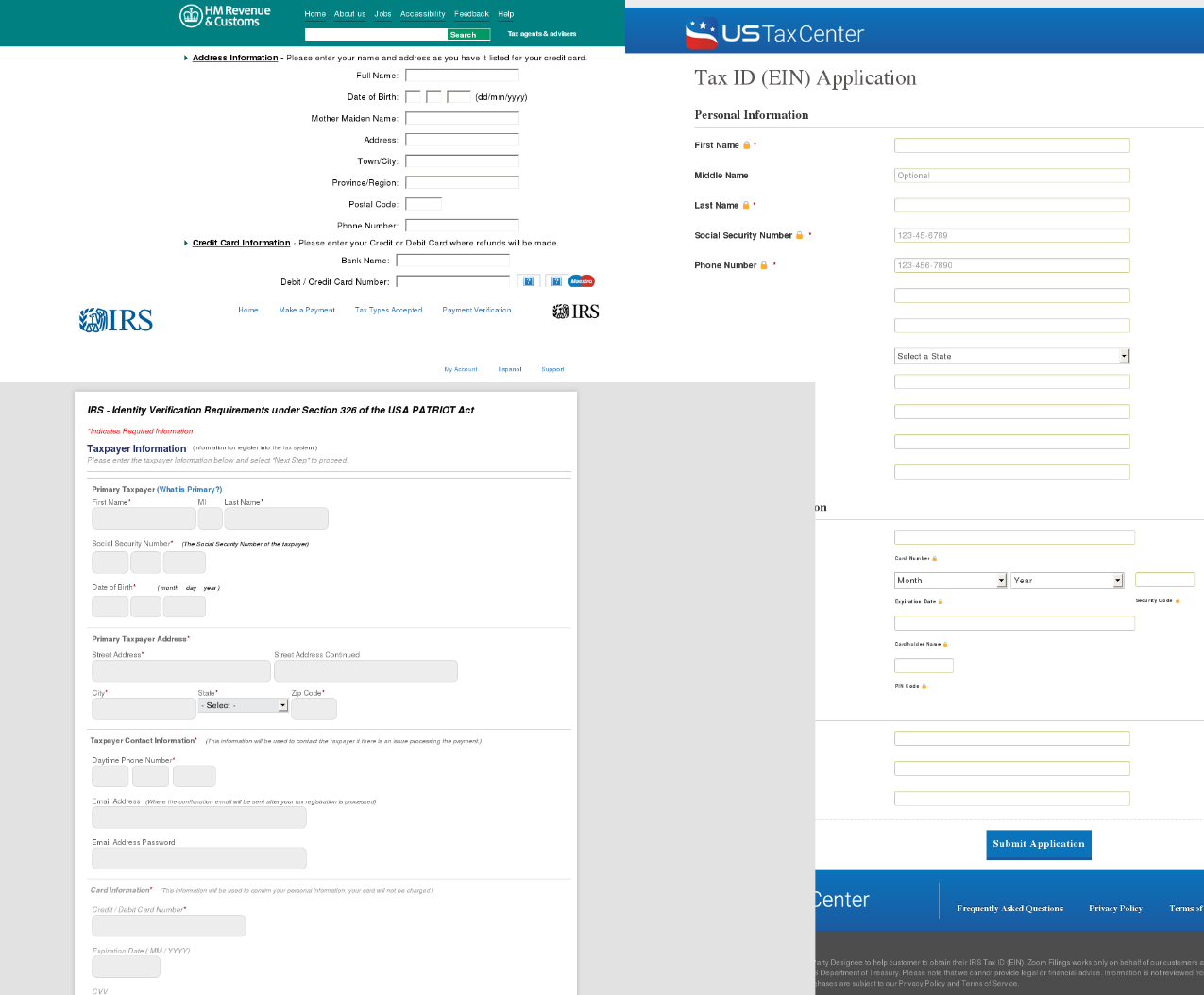
Fake tax service websites
Spam-based malware
Back in Q1 2017 we wrote about a mailout disguised as a resume concealing a malicious file from the Fareit Trojan spyware family. The same quarter 18, cybercriminals attempted to infect users’ computers with the Smoke Loader backdoor, also known as Dofoil. Its toolbox includes downloading and installing malware such as cryptocurrency miners, banking Trojans, and ransomware. Smoke Loader could also disable some antivirus software and hide from detection by integrating itself into system processes.
The text of the malicious mailshot varied, with some messages imitating the business correspondence of real company employees. To open the password-protected DOC attachment, the user had to enter the password specified in the message, which triggered a request to enable macros (disabled by default); confirmation proved fatal for message recipients. We observed a trend for password-protected malicious attachments in Q1 18: such protection hinders detection and increases the chances that the message will reach the recipient.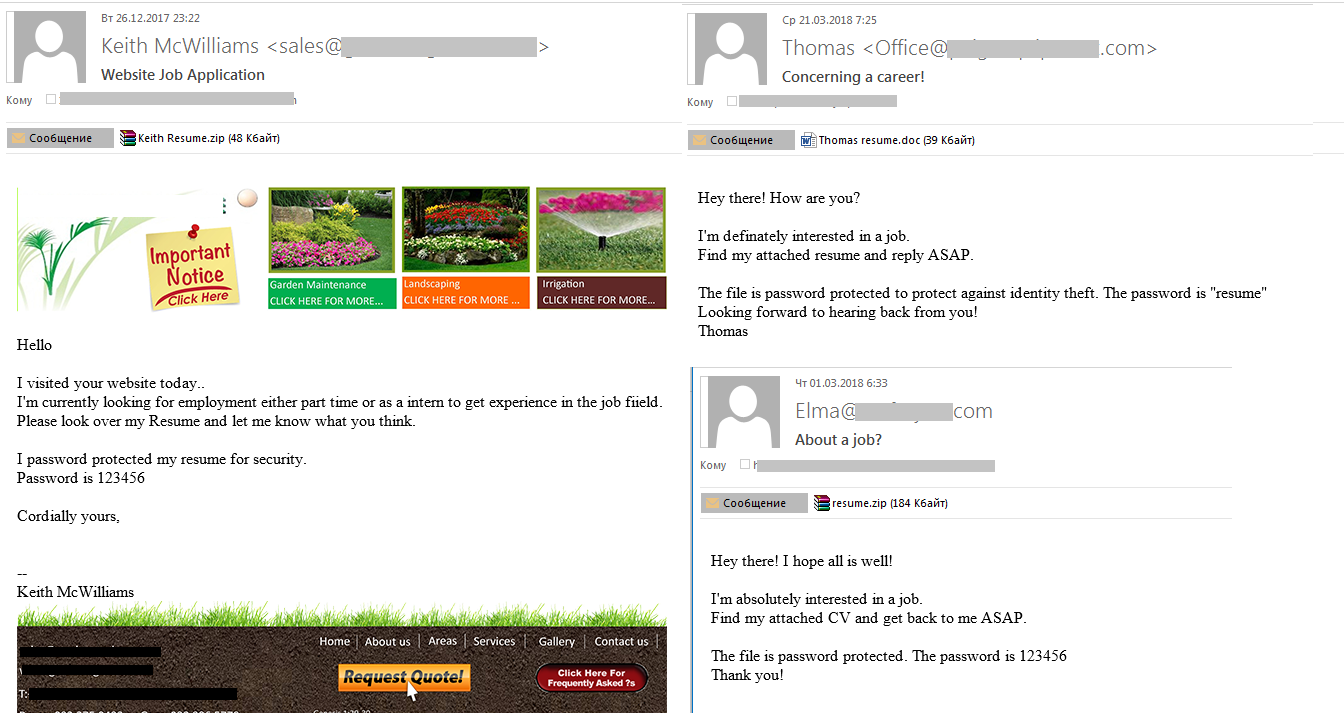
Examples of emails with malicious attachments
Another long-established social engineering method exploits user fears of infection, data leakage, access denial, and other bugbears. In Q1, this old trick was used to dupe users into parting with cryptocurrency. Most messages tried to scare recipients by reporting that malware was installed on their computer and that personal info (lists of contacts, monitor screenshots, webcam videos, etc.) was compromised. If the scammers didn’t receive a hush payment, it was said, the harvested information would be sent to all the victim’s contacts.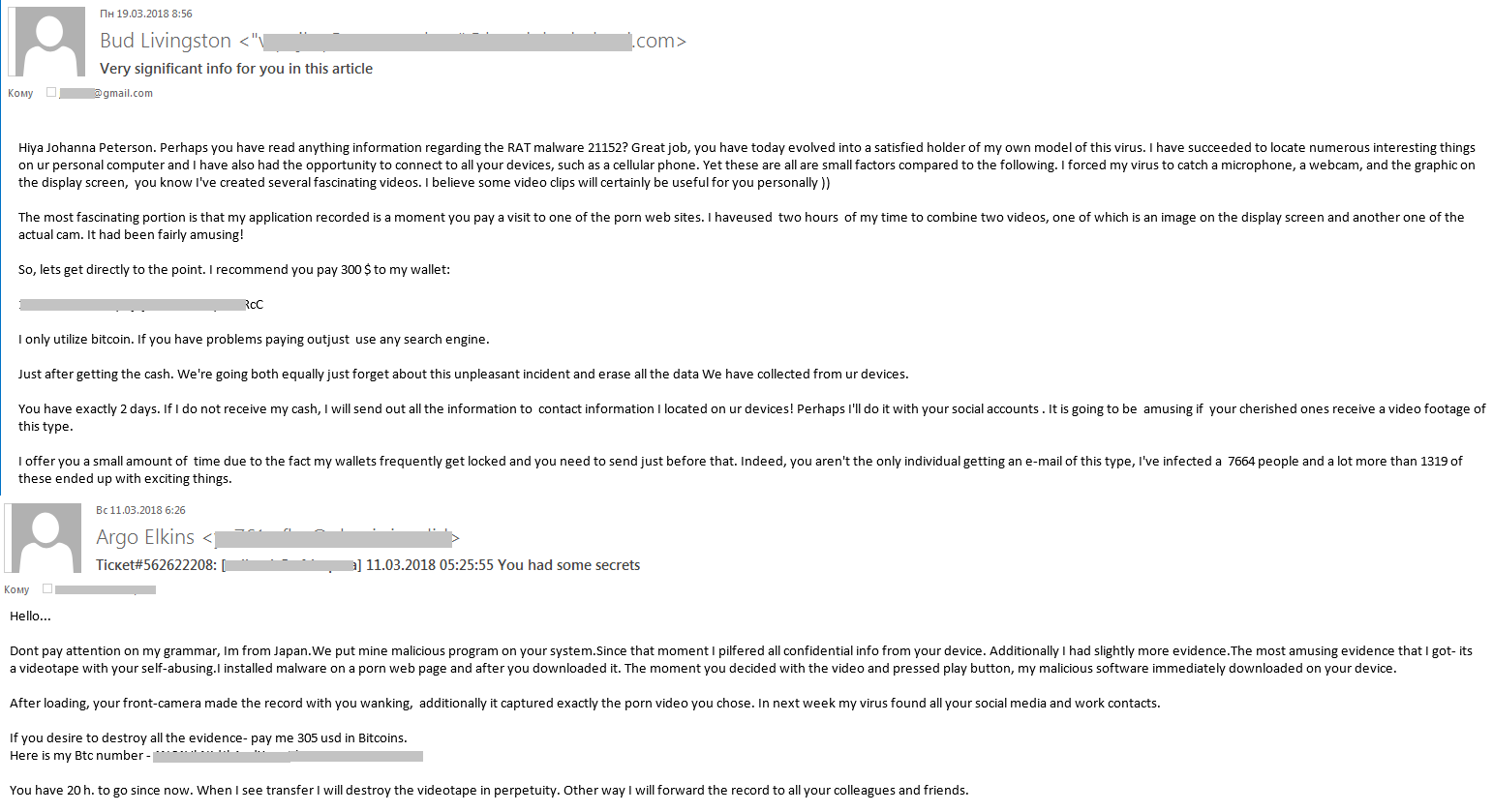
Example of a message with a ransom demand in exchange for not publicizing the victim’s personal data
Some messages from cybercriminals tried not only to extract money, but to install malware on recipients’ computers. The malware was located in a protected archive attachment that the attackers claimed was proof that they had the victim’s data.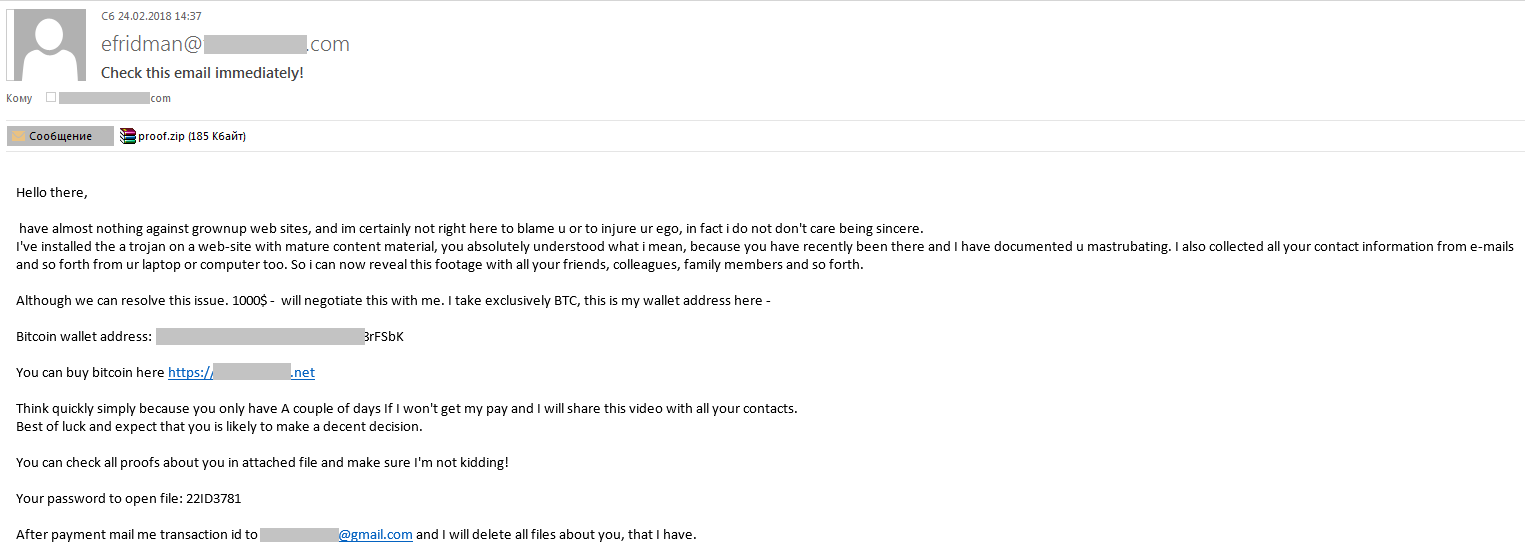
Malware under the guise of proving cybercriminal intent
Statistics: spam
Proportion of spam in email traffic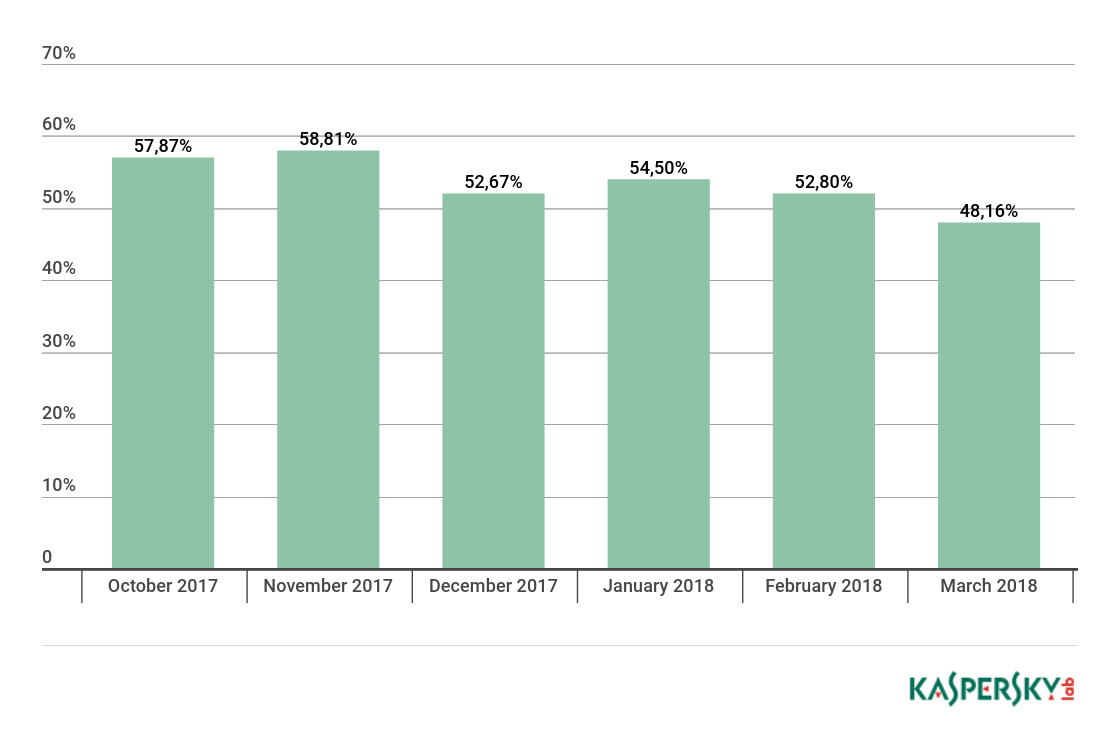
Proportion of spam in global email traffic, Q4 2017 and Q1 18
In Q1 18, the largest share of spam was recorded in January (54.50%). The average share of spam in global email traffic was 51.82%, down 4.63 p.p. against the figure for Q4 2017
Sources of spam by country
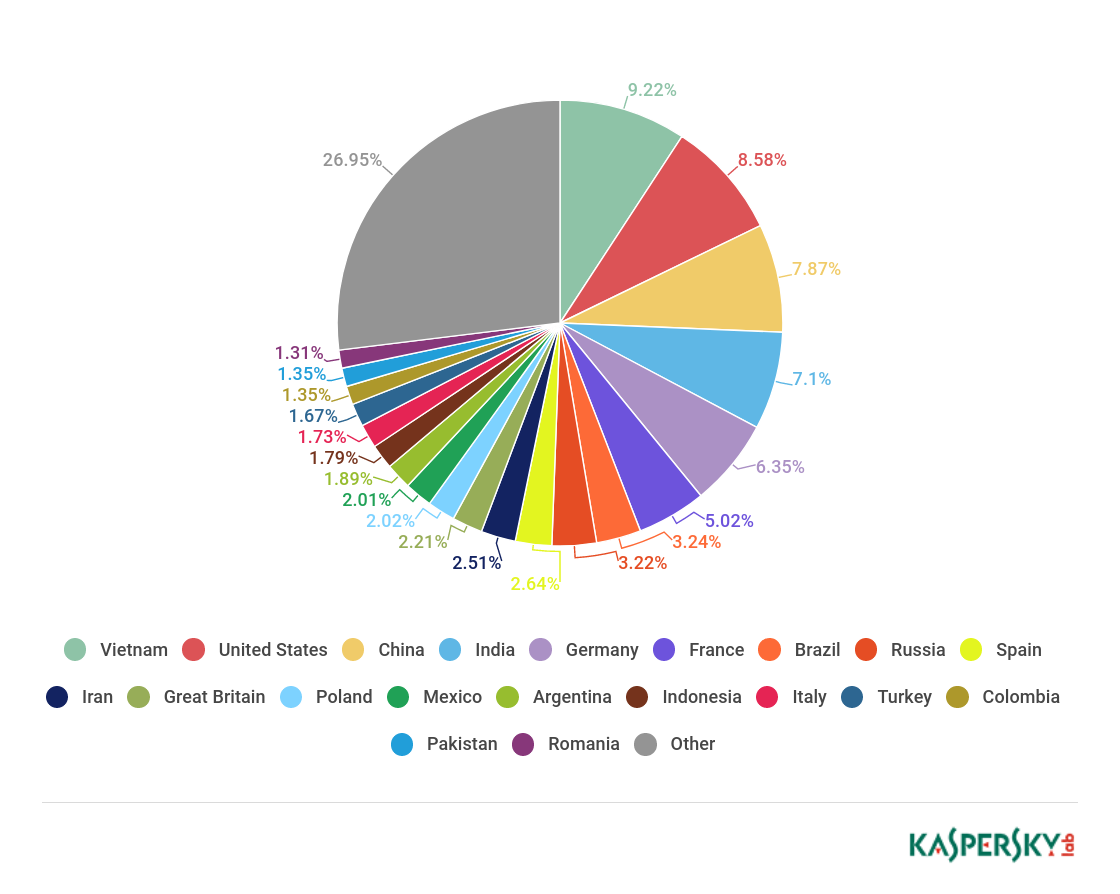
Sources of spam by country, Q1 18
Q1 18 results put Vietnam (9.22%) top of the leaderboard of spam sources by country. In second place, just 0.64 p.p. behind, came the US (8.55%). The rating’s frequent leader China (7.87%) slipped to third, while India (7.10%) and Germany (6.35%) claimed fourth and fifth. The Top 10 is rounded off by Iran (2.51%).
Spam email size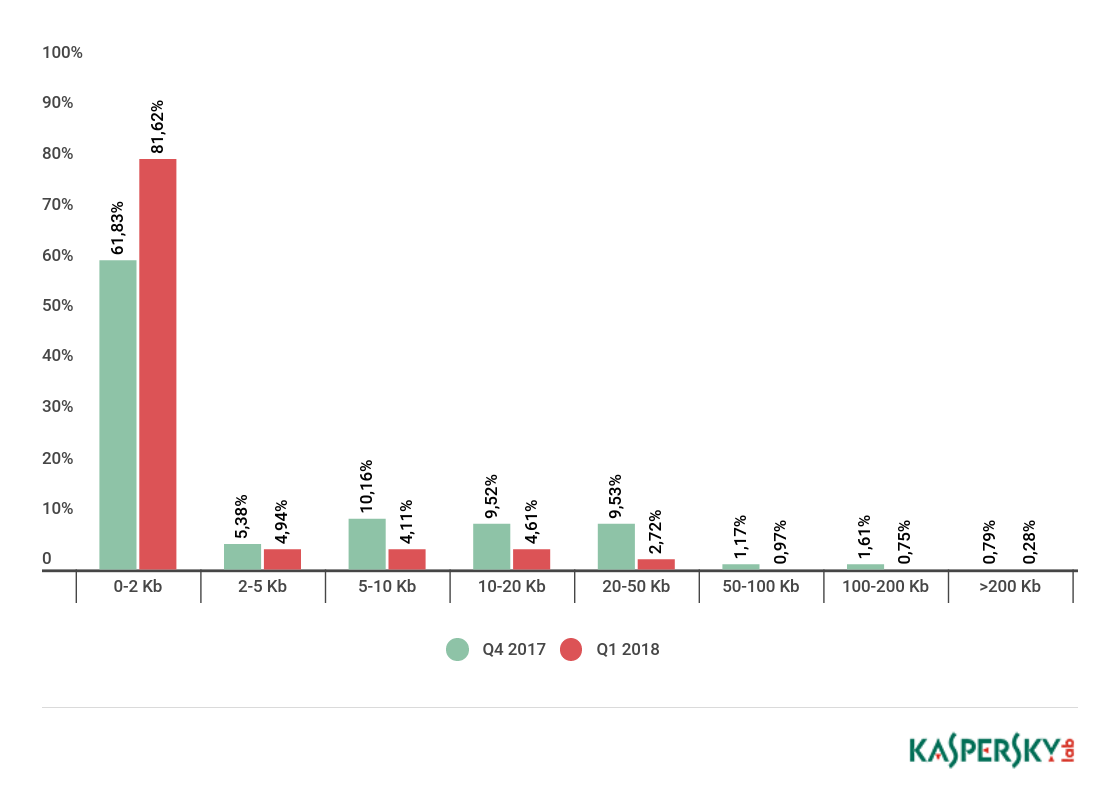
Spam email size, Q4 2017 and Q1 18
In Q1 18, the share of very small emails (up to 2 KB) in spam increased by 19.79 p.p. to 81.62%. Meanwhile,the proportion of emails between 5 and 10 KB in size fell (by 6.05 p.p.) against the previous quarter to 4.11%.
The number of emails between 10 and 20 KB also decreased (by 4.91 p.p.). Likewise, there were fewer emails sized 20 to 50 KB—this quarter they made up just 2.72% of the total, which represents a drop of 6.81 p.p. compared to the previous reporting period.
Malicious attachments in email
Top 10 malware families
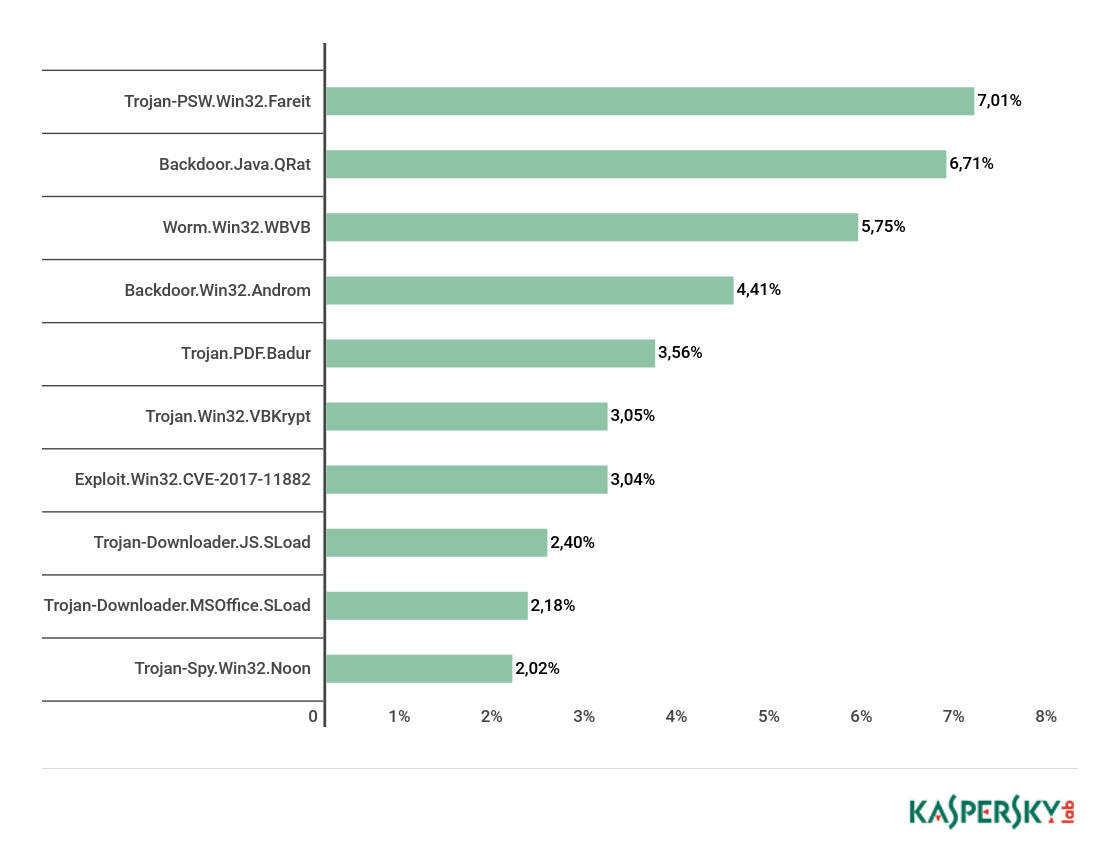
Top 10 malware families, Q1 18
The most widespread malware family in email traffic this quarter was Trojan-PSW.Win32.Fareit (7.01%), with Backdoor.Java.QRat (6.71%) and Worm.Win32.WBVB (5.75%) completing the Top 3. Fourth place went to Backdoor.Win32.Androm (4.41%), and Trojan.PDF.Badur (3.56%) rounds off the Top 5.
Countries targeted by malicious mailshots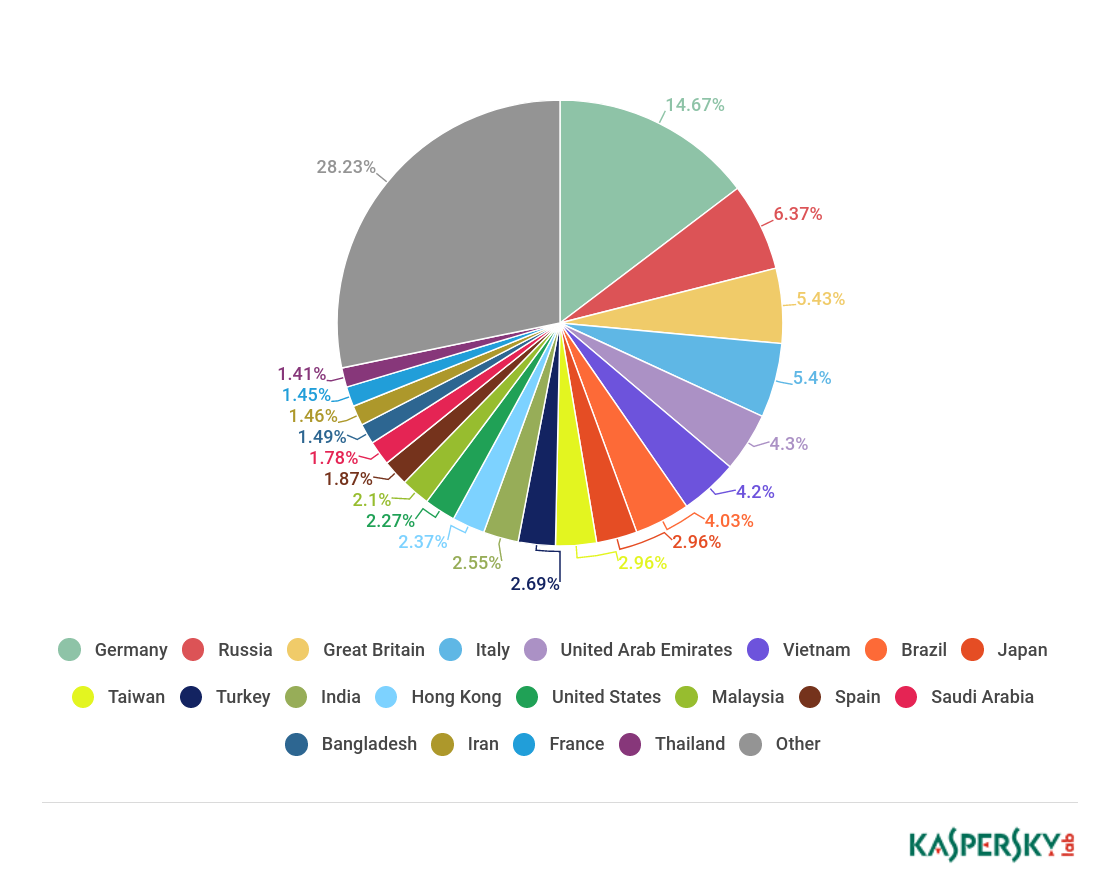
Distribution of Mail Anti-Virus triggers by country, Q1 18
Germany (14.67%) was this quarter’s leader by number of Mail Anti-Virus triggers, followed by Russia on 6.37% and Britain with a score of 5.43%. Fourth and fifth positions were occupied by Italy (5.40%) and the UAE (4.30%).
Statistics: phishing
In Q1 18, the Anti-Phishing module prevented 90,245,060 attempts to direct users to scam websites. The share of unique users attacked made up 9.6% of all users of Kaspersky Lab products worldwide.
Geography of attacks
The country with the largest percentage of users affected by phishing attacks in Q1 18 was Brazil (19.07%, -1.72 p.p.).
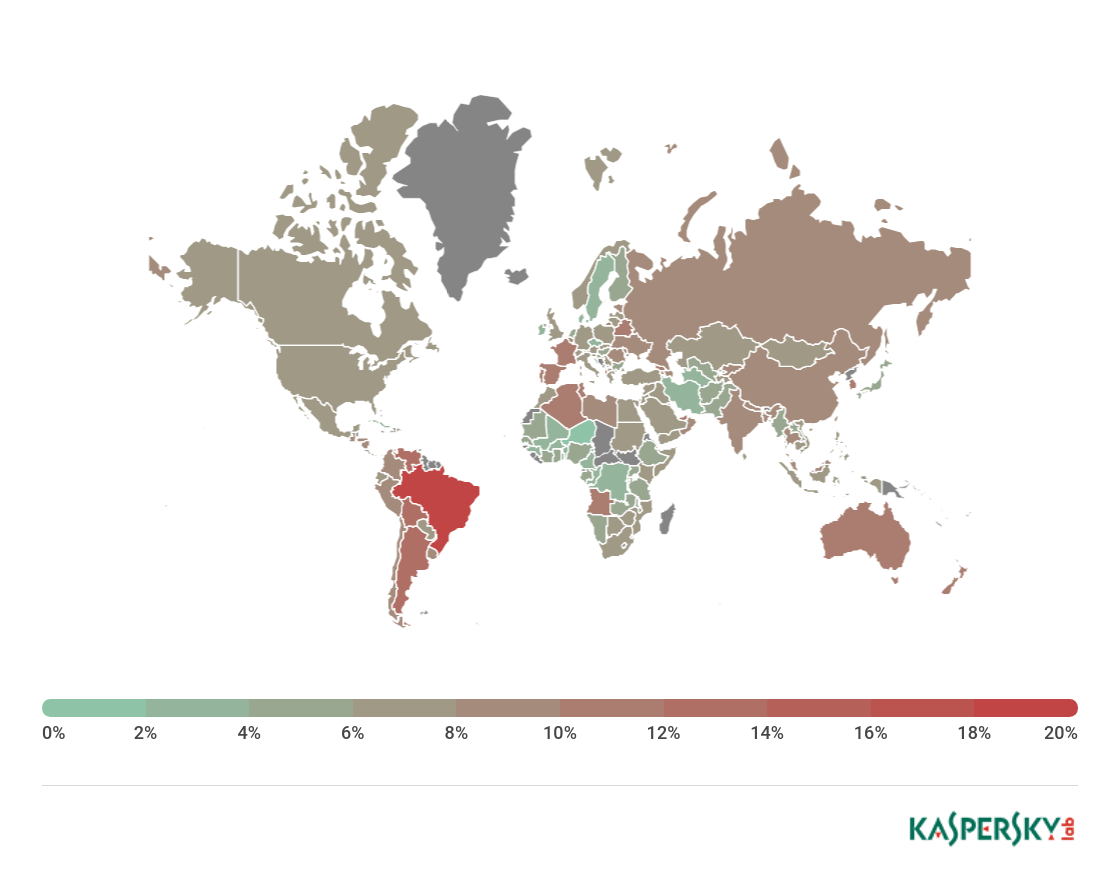
Geography of phishing attacks*, Q1 18
* Number of users on whose computers Anti-Phishing was triggered as a percentage of the total number of Kaspersky Lab users in that country
Second came Argentina (13.30%), and third place was taken by Venezuela (12.90%). Fourth and fifth went to Albania (12.56%) and Bolivia (12.32%).
Country %
Brazil 19.07
Argentina 13.30
Venezuela 12.90
Albania 12.56
Bolivia 12.32
Réunion 11.88
Belarus 11.62
Georgia 11.56
France 11.40
Portugal 11.26
Top 10 countries by percentage of users attacked by phishers
Organizations under attack
Rating of categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Lab’s heuristic Anti-Phishing component. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
In Q1 18, the Global Internet Portals category again took first place with 23.7% (-2.56 p.p.).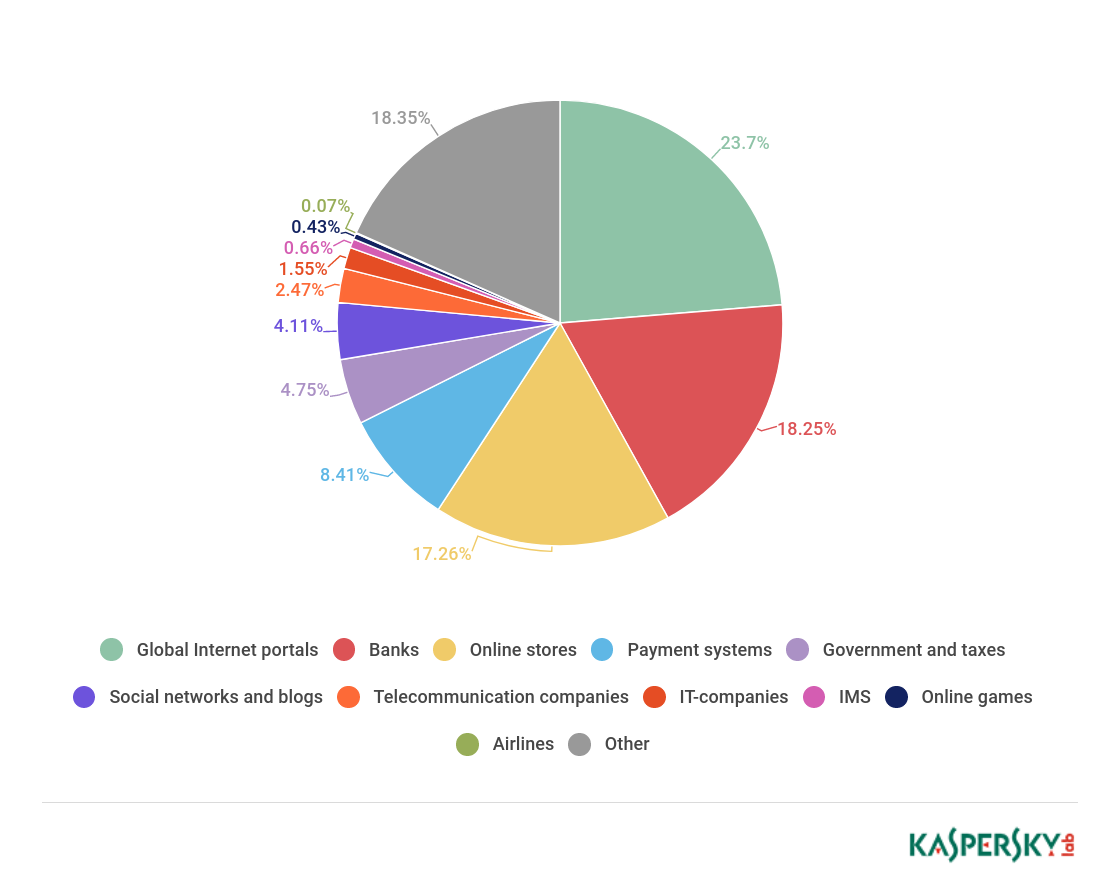
Distribution of organizations affected by phishing attacks by category, Q1 18
However, the combined financial category—banks (18.25%), online stores (17.26%), payment systems (8.41%)—still accounted for almost half of all attacks (43.92%), which is up 4.46 p.p. against the previous quarter . The next categories in descending order were Government Organizations (4.75%), Social Networks and Blogs (4.11%), Telecommunications Companies (2.47%), IT Companies (1.55%), Messengers (0.66%), Online Games (0.43%), and Airlines (0.07%).
Conclusion
The quarter’s main topic, one that we will likely return to many times this year, is personal data. It remains one of the most sought-after wares in the world of information technology for app and service developers, owners of various agencies, and, of course, cybercriminals. Unfortunately, many users still fail to grasp the need to protect their personal information and don’t pay attention to who and how their data is transferred in social media.
Cybercriminal interest in personal data is confirmed by our analysis of spam traffic, where one of the main topics remains mail phishing employing a range of social and technical engineering methods. Throughout the quarter, we observed fake notifications on behalf of social media and popular services, bank phishing, and “Nigerian prince” emails.
The GDPR, set to come on stream in late May, is intended to correct the situation regarding personal data, at least in the EU . Time will tell how effective it is. But one thing is clear: even before its introduction, the new regulation is being actively exploited as a topic by cybercriminals and many others. Regrettably, the GDPR is unlikely to fix the situation.
In Q1 18, the average share of spam in global email traffic was 51.82%, down 4.63 p.p. against Q4 2017; the Anti-Phishing module blocked 90,245,060 attempts to direct users to fraudulent pages; and Brazil (19.07%, -1.72 p.p.) had the largest share of users attacked by phishers.
Based on the quarter results, it is safe to predict that scammers will continue to exploit “fashionable” topics, two of which are cryptocurrencies and new ICOs. Given that these topics have begun to attract interest from the general public, a successful attack can reap vast rewards.