Spam and phishing in Q2 2018
18.8.2018 Kaspersky Analysis Spam Phishing
Quarterly highlights
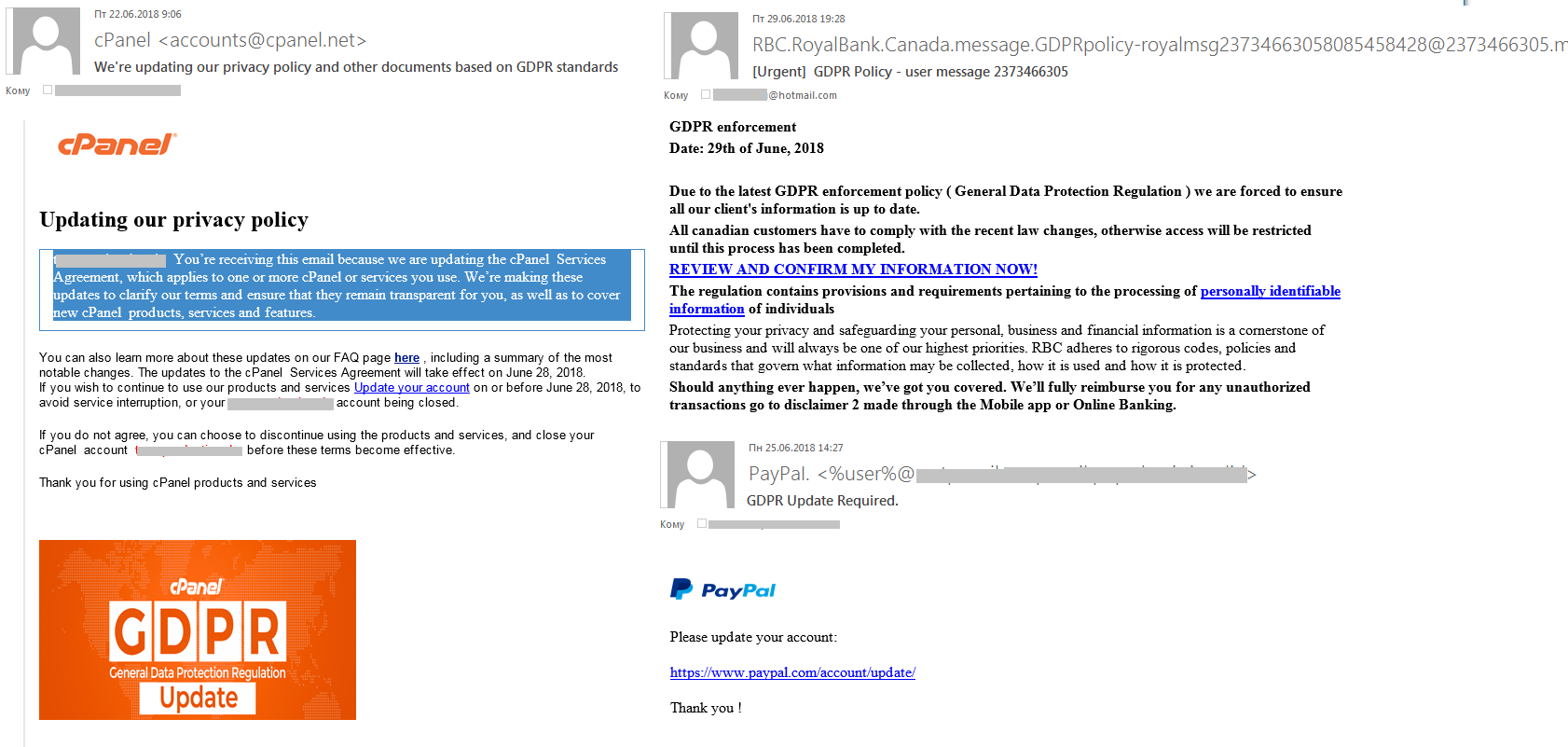
GDPR as a phishing opportunity
In the first quarter, we discussed spam designed to exploit GDPR (General Data Protection Regulation), which came into effect on May 25, 2018. Back then spam traffic was limited to invitations to participate in workshops and other educational events and purchase software or databases. We predicted that fraudulent emails were soon to follow. And we found them in the second quarter.
As required by the regulation, companies notified email recipients that they were switching to a new GDPR-compliant policy and asked them to confirm permission to store and process personal information. This was what criminals took advantage of. To gain access to the personal information of well-known companies’ customers, criminals sent out phishing emails referencing the GDPR and asking recipients to update their account information. To do this, customers had to click on the link provided and enter the requested data, which immediately fell into the hands of the criminals. It must be noted that the attackers were targeting customers of financial organizations and IT service providers.
Phishing emails exploiting GDPR
Malicious IQY attachments
In the second quarter, we uncovered several malspam incidents with never-before-seen IQY (Microsoft Excel Web Query) attachments. Attackers disguise these files as invoices, order forms, document copies, etc., which is a known ploy that is still actively used for malspamming. The From field contains addresses that look like personal emails, and names of attachments are generated in accordance with the following template: the name of the attachment, and then either a date or a random number sequence.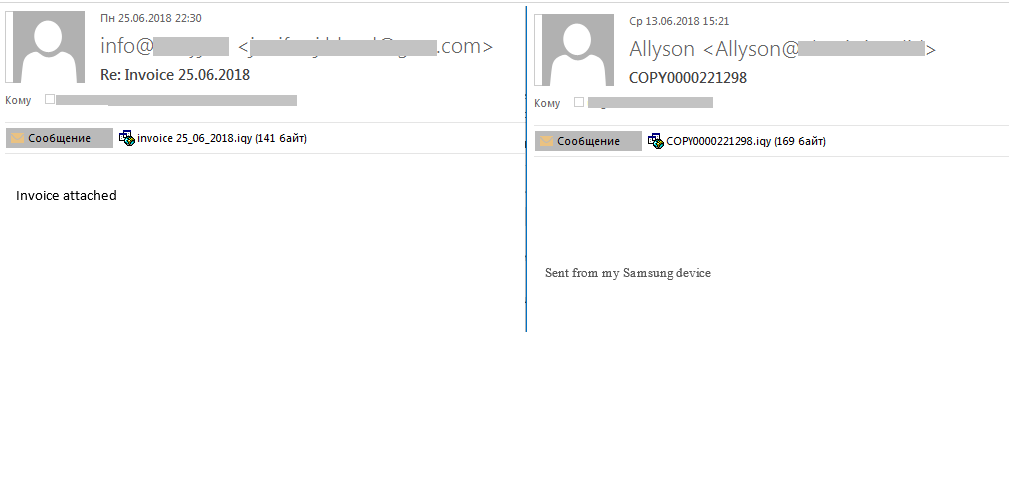
Harmful .iqy files
When the victim opens the IQY file, the computer downloads several trojan-downloaders, which install the Flawed Ammyy RAT backdoor. The infection chain may look like this: Trojan-Downloader.MSExcel.Agent downloads another downloader from the same family, which, in turn, downloads Trojan-Downloader.PowerShell.Agent, then this trojan downloads Trojan-Downloader.Win32.Dapato, which finally installs the actual Backdoor.Win32.RA-based.hf (also known as Flawed Ammyy RAT) used to gain remote access to the victim’s computer, steal files and personal information, and send spam.
It is rather difficult to detect these attachments because these files look like ordinary text documents which transfer web-inquiry data transfer parameters from remote sources to Excel spreadsheets. IQY files can also be a very dangerous tool in the hands of criminals because their structure is no different from the structure of legitimate files, yet they can be used to download any data at all.
It must be noted that malspam with IQY attachments is distributed via the largest botnet called Necurs. As a reminder, this is the botnet responsible for malspam (ransomware, macro-viruses, etc.), as well as pump-and-dump and dating spam. The botnet’s operation is characterized by periods of spiking and idling while infection and filter evasion mechanisms become ever more sophisticated.
Data leaks
The wave of confidential information leaks we discussed in the previous quarter is still on the rise. Here are some of the most notable events of the quarter:
Hacking and theft of personal information of 27M Ticketfly customers;
92M MyHeritage genealogy service users’ personal information was discovered on a public server;
340M individual records were lost by Exactis, a marketing company;
An unprotected Amazon server allowed access to the personal information of 48M Facebook, LinkedIn, Twitter, and Zillow users.
As a result of such leaks, cybercriminals get a hold of users’ names, email addresses, phone numbers, dates of birth, credit card numbers, and personal preferences. This information may later be used to launch targeted phishing attacks, which are the most dangerous type of phishing.
Cryptocurrency
In the second quarter, our antiphishing system prevented 58,000 user attempts to connect to phishing websites masquerading as popular cryptocurrency wallets and markets. In addition to classic phishing, which aims at gaining access to the victim’s accounts and private key information, cybercriminals try every way to entice a victim to willingly send them cryptocurrency. One of the examples of this are cryptocoin giveaways. Cybercriminals continue using the names of new ICO projects to collect money from potential investors that are trying to gain early access to new tokens. Sometimes phishing sites pop up before official project sites.
Ethereum (ETH) is currently the most popular cryptocurrency with phishers. The popularity of Ethereum with cybercriminals increases as more funds are attracted by ICOs on the Ethereum platform. According to our very rough estimate (based on data received from over a thousand ETH wallets used by malefactors), over the Q2 2018, cybercriminals exploiting ICOs managed to make $2,329,317 (end-of-July-2018 exchange rate), traditional phishing not included.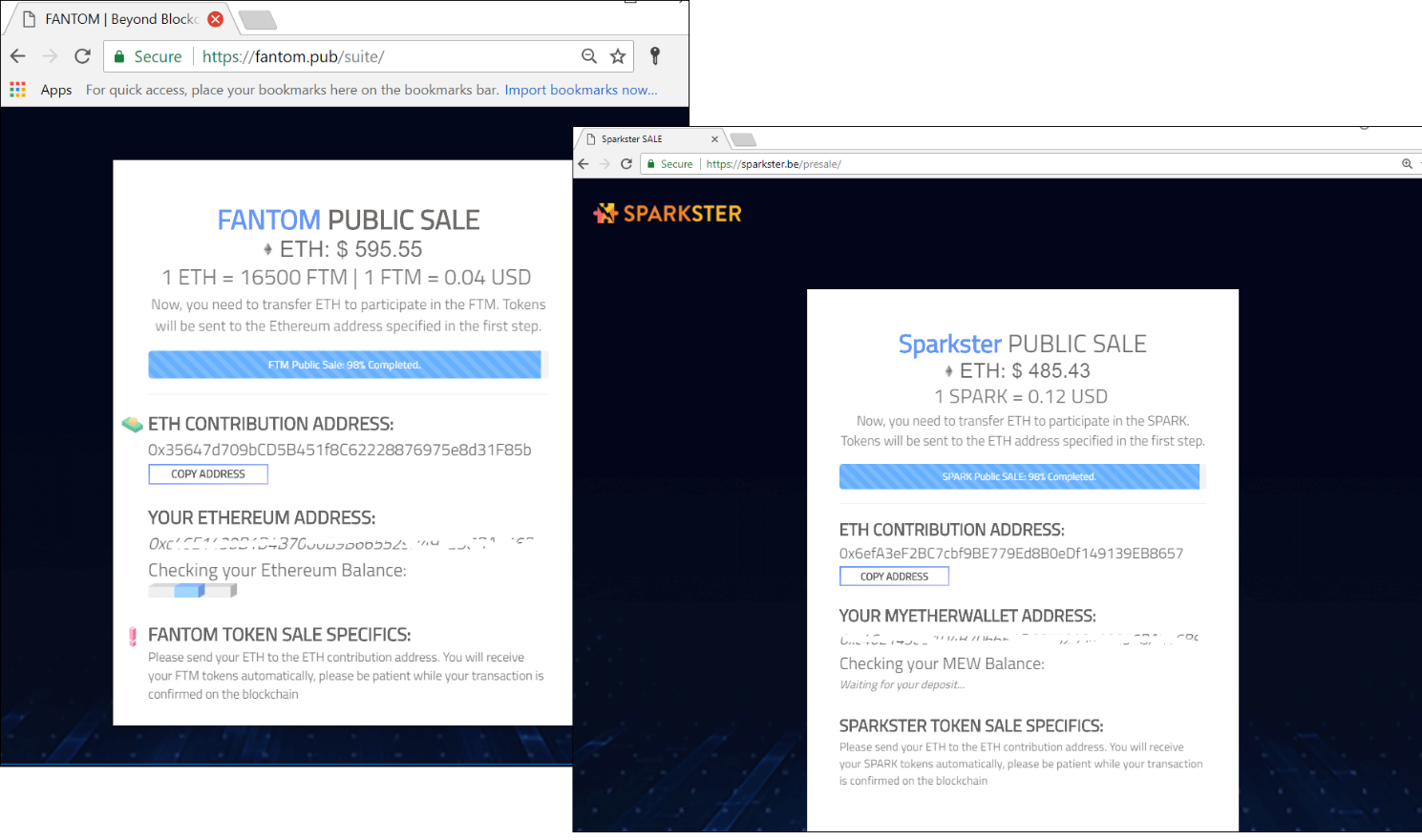
Fake ICO project pages: the first is located on fantom.pub and imitates fantom.foundation, the real site of the FANTOM project; the second one, found on sparkster.be, is an imitation of sparkster.me, the original SPARKSTER site
World Cup 2018
Cybercriminals from all over the world prepared for the World Cup as much as its organizers and soccer fans. The World Cup was used in many traditional scamming methods using social engineering. Cybercriminals created fake championship partner websites to gain access to victims’ bank and other accounts, carried out targeted attacks, and created bogus fifa.com account sign-in pages.
HTTPS
As mentioned in the 2017 report, more and more phishing pages are now found on certified domains. Those may include hacked or specially registered domains that cybercriminals use to store their content. This has to do with the fact that most of the Internet is switching to HTTPS and it has become easy to get a simple certificate. In the middle of the second quarter, this prompted Google to announce future efforts aimed at changing the way Chrome works with certificates. Starting in September 2018, the browser (Chrome 69) will stop marking HTTPS sites as “Secure” in the URL bar. Instead, starting in October 2018, Chrome will start displaying the “Not secure” label when users enter data on unencrypted sites.
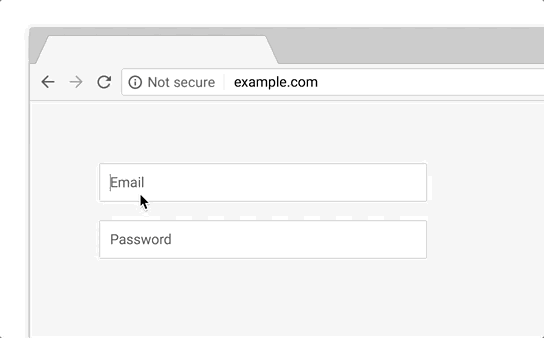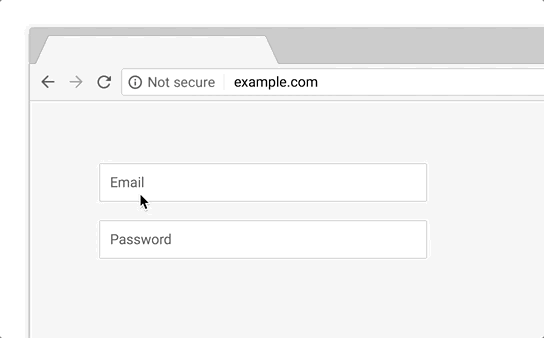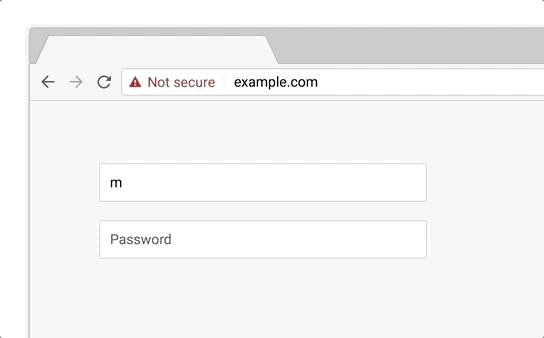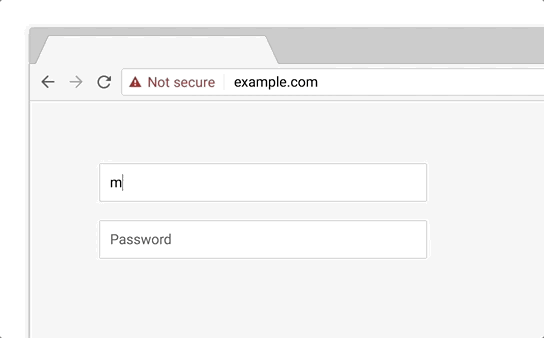
When Chrome 70 comes out in October 2018, a red “Not secure” marker will be displayed for all HTTP sites where users enter data.
Google believes that this will make more sites use encryption. After all, users should expect the web to be safe by default and receive warnings only in the event of any issues.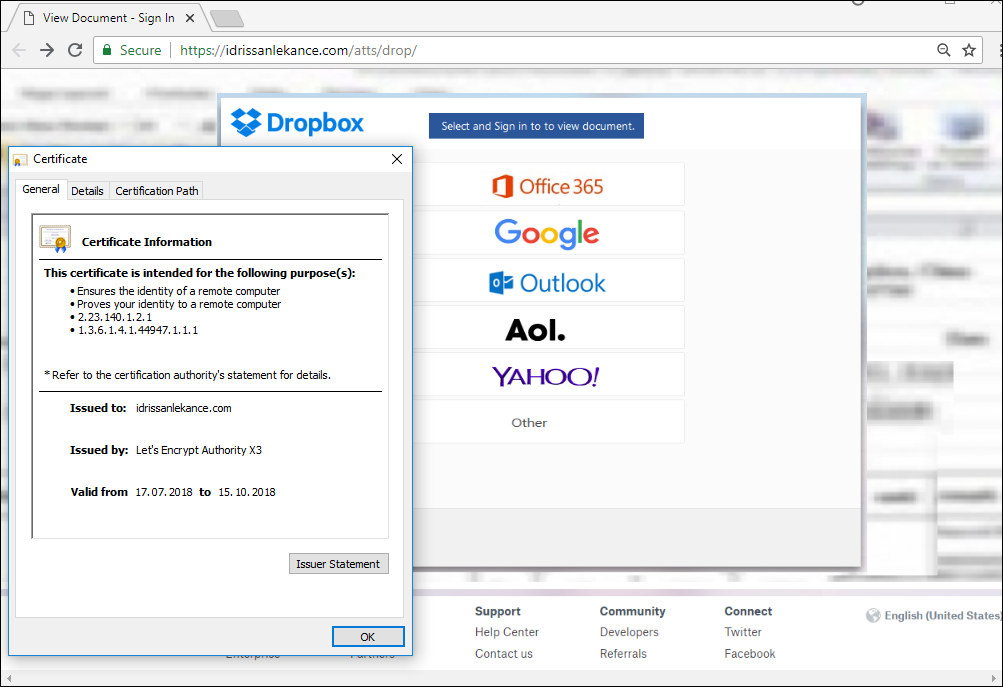
An example of a certified phishing website marked as “Secure”.
At the moment, the green Secure message in the URL bar is rather misleading for a user, especially when they visit a phishing website.
Vacation season
In anticipation of the vacation season, cybercriminals have used all of the possible topics that may interest travelers, from airplane ticket purchases to hotel bookings. For instance, we’ve found many websites that offer very tempting accommodations at absurd prices (e.g., an entire four-bedroom house in Prague with a pool and a fireplace at $1,000 a month). Such websites pose as Amazon, TripAdvisor, and other sites popular among travelers.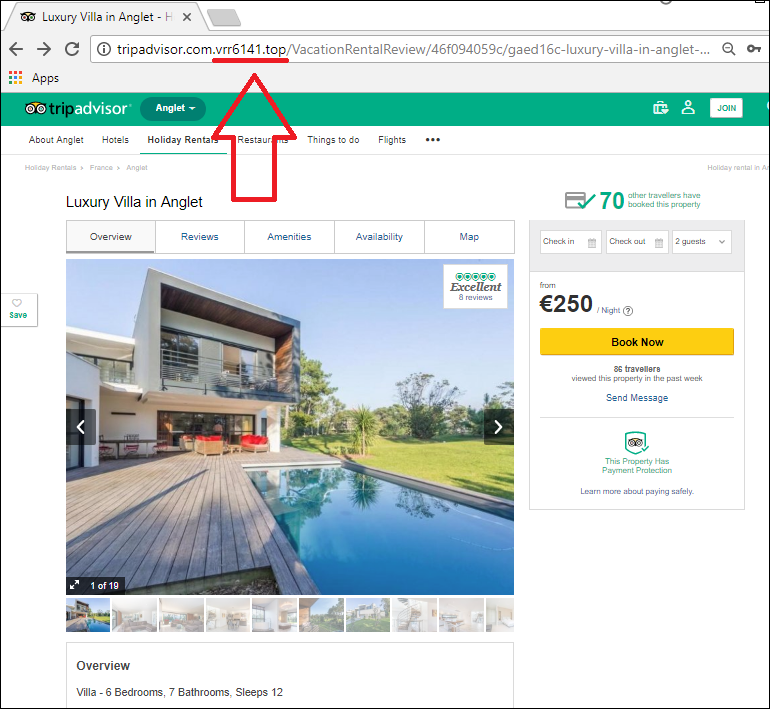
An example of a fake hotel booking website
A similar method is used to fake ticket aggregator websites. In these cases, the displayed flight information is real, but the tickets turn out to be fake.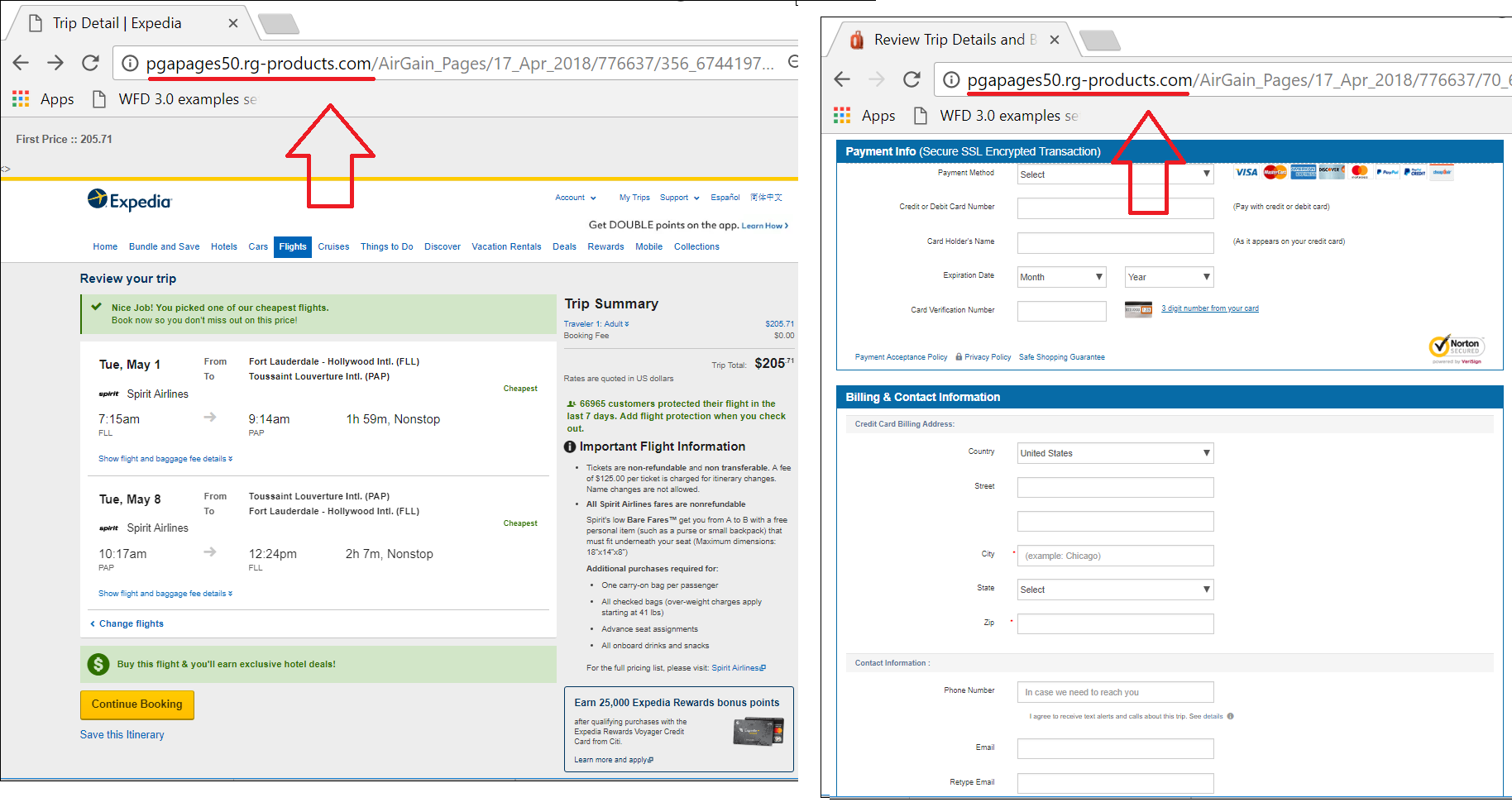
An example of fake airline ticket websites
Distribution channels
In our reports, we regularly point out you that phishing and other spam has gone way beyond email a long time ago. Attackers use every means of communication at their disposal and even recruit unsuspecting users themselves for malware distribution. In this quarter, most large-scale attacks were found in messengers and on social networks.
WhatsApp
Cybercriminals have been using WhatsApp more frequently to distribute their content lately. WhatsApp users copy and resend spam messages themselves, just like they used to do with luck chain letters many years ago. Most of these messages contain information about fictional lotteries or giveaways (we have already discussed these types of scams many times). Last quarter, cybercriminals brought back the airplane ticket giveaways. This quarter in Russia, for instance, they used names of popular retailers such as Pyaterochka and Leroy Merlin, and also McDonald’s. Some fake messages come from popular sportswear brands, as well as certain stores and coffee shops.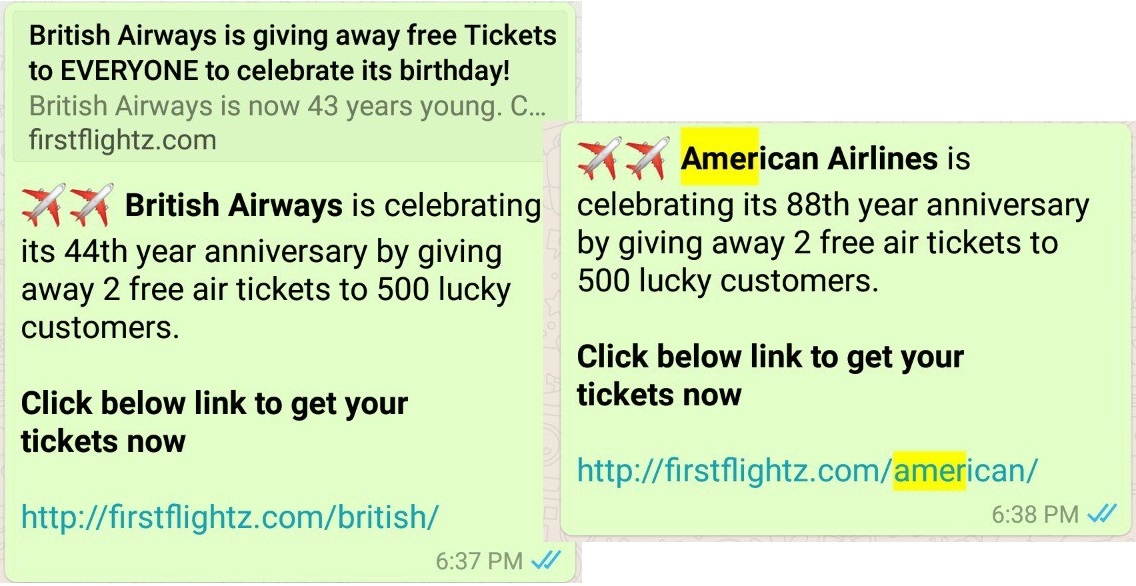
Users share messages about ticket raffles with their contacts via a messenger since it’s one of the conditions for winning
Once a user has sent the message to some friends, he or she is redirected to another resource, the content of which changes depending on the victim’s location and device. If the user visits the site from their smartphone, most often they are automatically subscribed to paid services. The user may also be redirected to a page containing a survey or a lottery or to some other malicious website. For instance, a user may be invited to install a browser extension which will later intercept the data they enter on other websites and use their name to do other things online, such as publish posts on social media.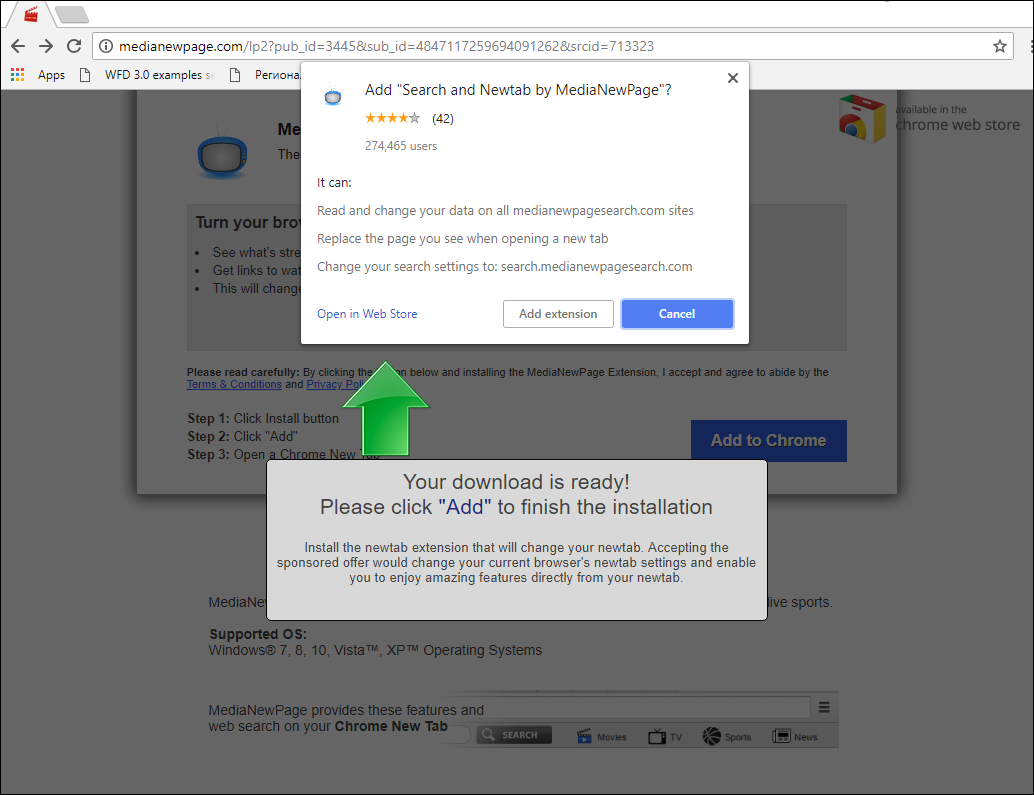
An example of a page which a user is redirected to after a survey, at the end of which they were promised a coupon to be used in a popular retail chain. As you can see, no coupon has been received, but the user is invited to install a browser extension with suspicious permissions.
Twitter and Instagram
Cybercriminals have been using Twitter to distribute fraudulent content for a long time. However, it has recently become a breeding ground for fake celebrity and company accounts.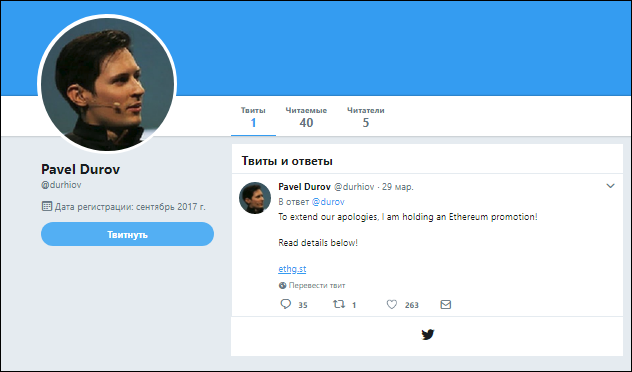
Fake account for Pavel Durov
The most popular cover used by cybercriminals is cryptocurrency giveaways on behalf of celebrities. The user is asked to transfer a small amount of cryptocurrency to a certain wallet to get double or triple coins back. To enhance trust, the wallet may be located on a separate website, which also contains a list of fake transactions that the victim can see “updating” in real time, which confirms that any person who transfers money to the fake wallet gets back several times the amount transferred. Of course, the victim does not receive anything. Despite the simplicity of this scheme, it makes cybercriminals millions of dollars. This quarter, cybercriminals favoured the names of Elon Musk, Pavel Durov, and Vitalik Buterin in their schemes. These names were chosen for a reason — Elon Musk is an entrepreneur, inventor, and investor, while Durov and Buterin made it to the cryptocurrency market leader list published by Fortune.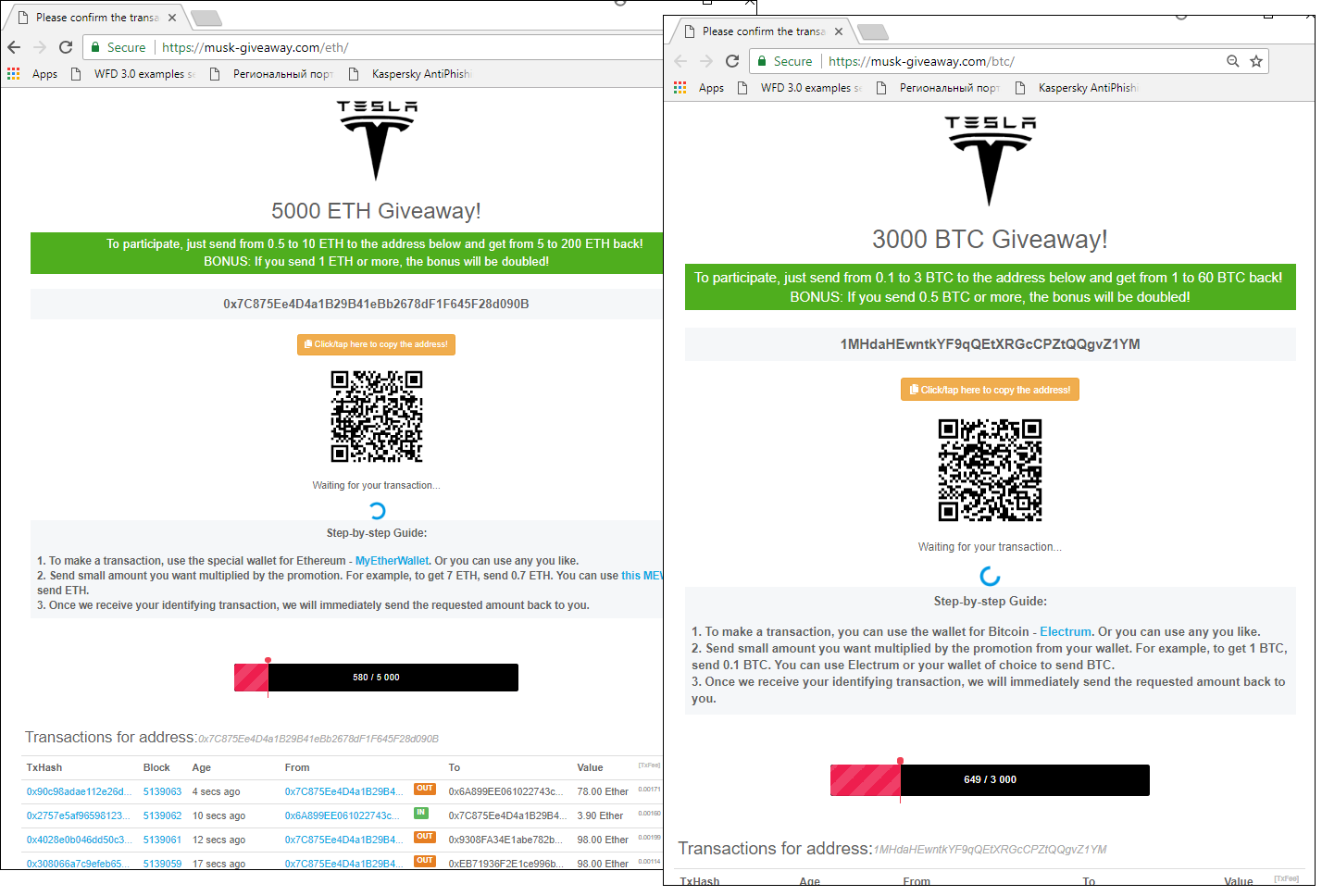
An example of a website advertised on Elon Musk’s fake account
News sensations make these schemes even more effective. For instance, the shutdown of the Telegram messenger generated a wave of fake messages from “Pavel Durov” promising compensation. In this case cybercriminals use similarly-spelled account names. For example, if the original account name contains an underscore, cybercriminals register a new user with two underscores in the name and publish messages about cryptocurrency giveaways in comments to the celebrities’ authentic Twitter posts. As a result, even a detail-oriented person may have a hard time spotting the fake.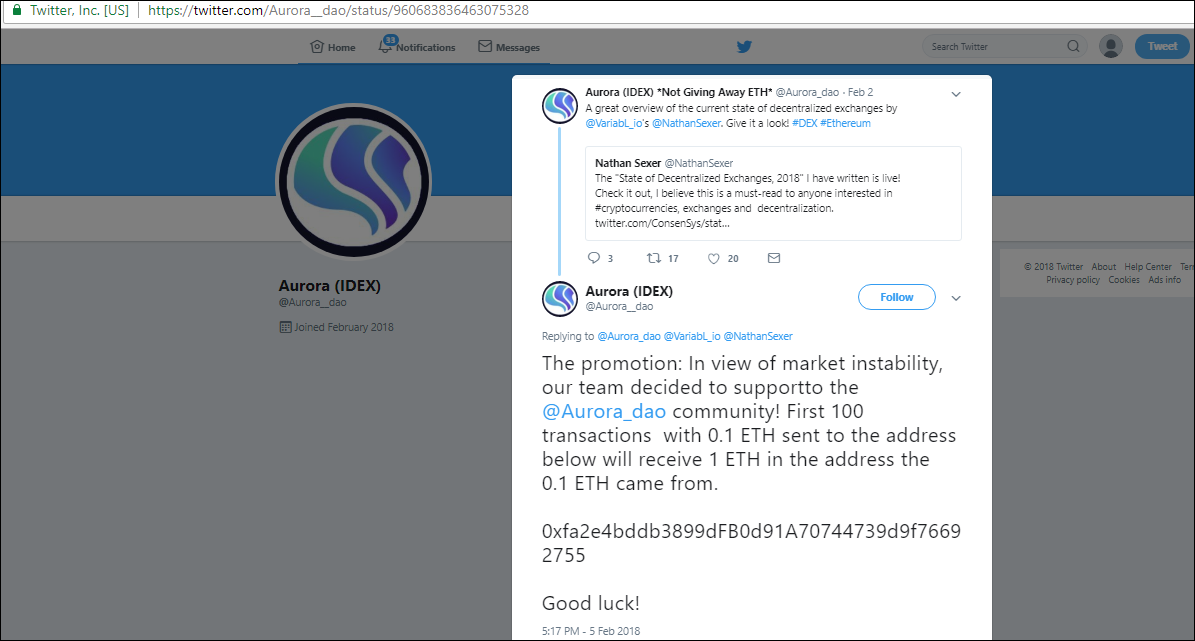
Twitter administration promised to stop this type of fraud a long time ago. One of their first steps involved blocking accounts that tried to change the user’s name to Elon Musk, and most probably other names commonly used by cybercriminals as well. However, it is easy to keep the account from being blocked by entering a Captcha and a code sent via text, after which the user can keep Elon’s name or change it to anything they want— the account will not be blocked again. It is also unclear whether Twitter will block the obfuscated names of famous people that are often exploited by cybercriminals.
Another measure taken by the social network is blocking accounts that post links to Elon Musk’s account. Just like in the previous example, the account can be unblocked by entering a Captcha and confirming a phone number via a code received in a text message.
This scam has started spreading to other platforms as well. Fake accounts can also be found on Instagram.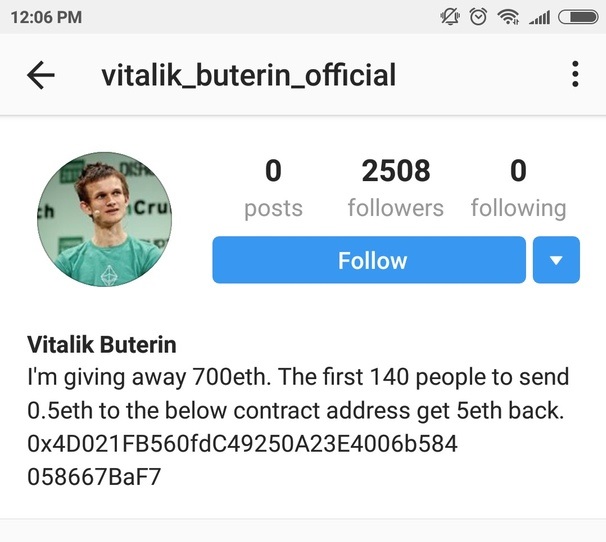
Vitalik Buterin’s fake Instagram account
Facebook
On Facebook, in addition to the aforementioned content distribution through viral threads, cybercriminals often use the advertising mechanisms offered by the social network. We have recorded instances of get-rich-quick schemes being spread through Facebook ads.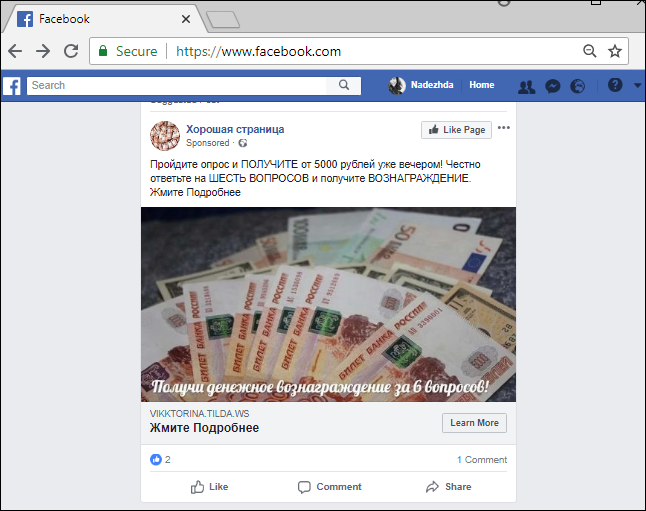
Fraudulent website ad on Facebook
After clicking on the ad, the user is redirected to a website where, after completing a few steps, they are offered a reward. To receive this reward, the user must either pay a fee, enter their credit card information, or share some personal details. Of course, the user does not receive any reward in the end.
Search results
Ads with malicious content and links to phishing sites can be found not only on social networks, but also in the search results pages of major search engines. This has recently become a popular method of advertising fake ICO project websites.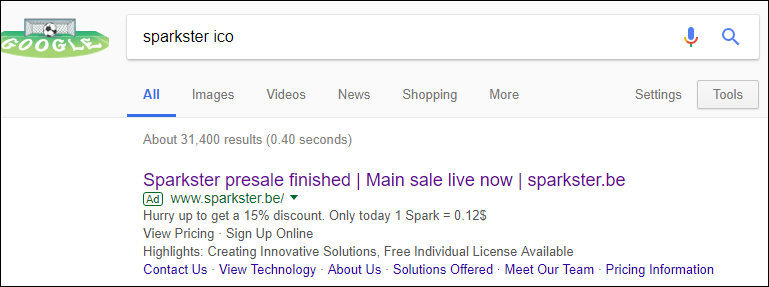
Users do not always notice the “Ad” label next to the ads
Spammer tricks
Last quarter, spammers tried to use the following new tricks to evade filters.
Double email headers
When generating spam emails, spammers use two From fields in the email header. The first From field contained a legitimate address, usually one from a well-known organization (whose reputation is untarnished by spam scandals) while the second contained the actual spammer email address, which has nothing to do with the first one. Spammers were expecting the email to be treated as legitimate by filters, forgetting that modern anti-spam solutions rely not only on the technical part of the email, but also on its content.
Subscription forms
In these events, spam messages in the form of an automatic mailing list subscription confirmations arrive in recipient inboxes. Regular websites capable of unlimited user registration were employed to create them (especially when they allowed using the same email address multiple times). Spammers used a script that auto-filled subscription forms inserting recipient addresses from previously collected (or purchased) databases. Spam content was a short phrase with a link to a spam resource inserted into one of the mandatory fields in the form (in particular, the recipient name). As a result, the user received a notification sent from a legitimate mail address containing a spam link instead of their name.
An example of spam mail sent using the subscription service on a legal site
Statistics: spam
Proportion of spam in email traffic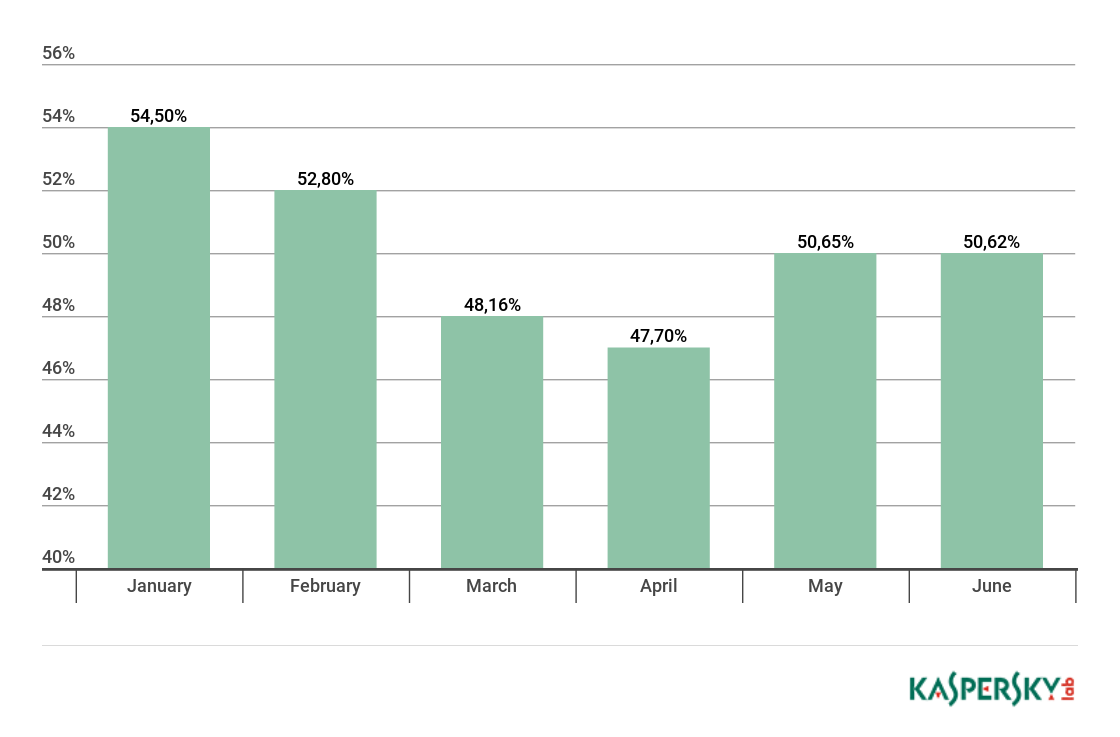
Proportion of spam in global email traffic, Q1 and Q2 2018 (download)
In the Q2 2018, the largest percentage of spam was recorded in May at 50.65%. The average percentage of spam in world mail traffic is 49.66%, which was 2.16 p.p. lower than the previous reporting period.
Sources of spam by country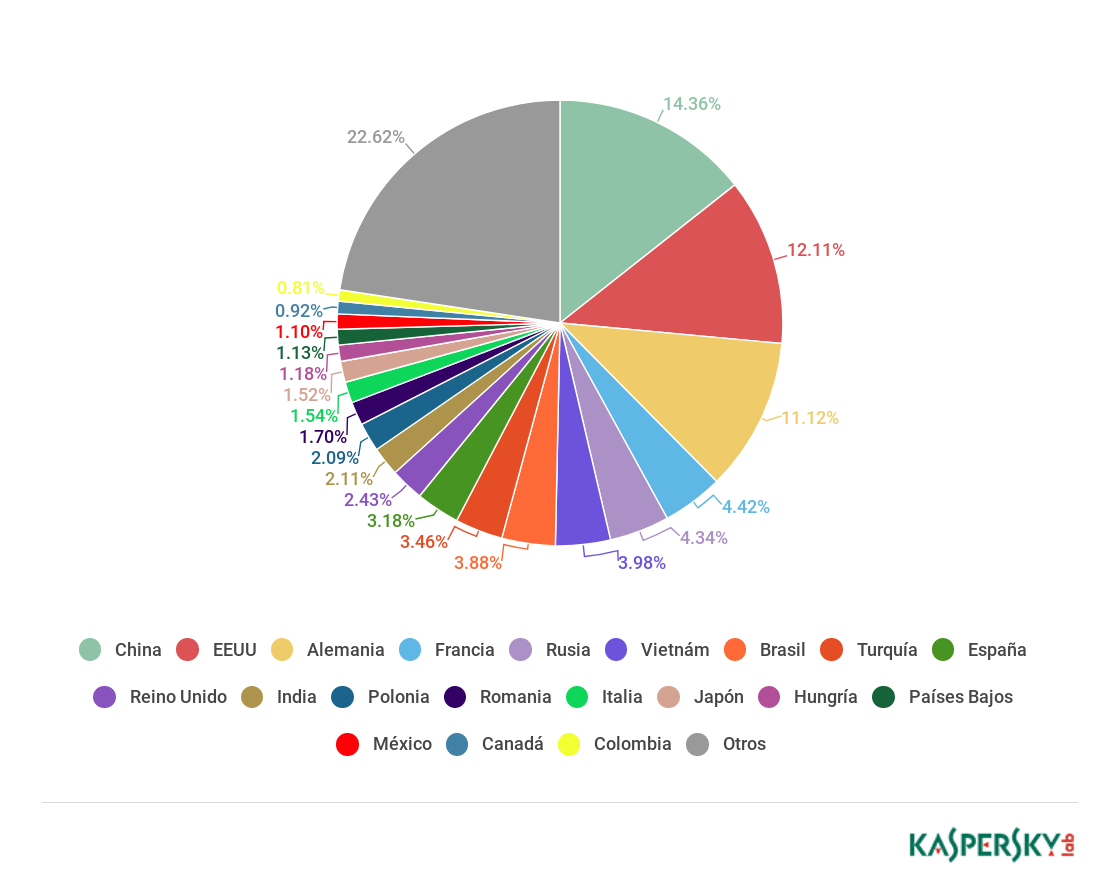
Spam -originating countries, Q2 2018 (download)
The leading spam-originating country in Q2 2018 was Vietnam (3.98%), which fell to seventh place in the second quarter, replaced by China (14.36%). The second and third places, the USA in Germany, are only one percentage point apart, with 12.11% and 11.12% shares, respectively. France occupied the fourth place (4.42%), and the fifth was occupied by Russia (4.34%). Great Britain occupied the tenth place (2.43%).
Spam email size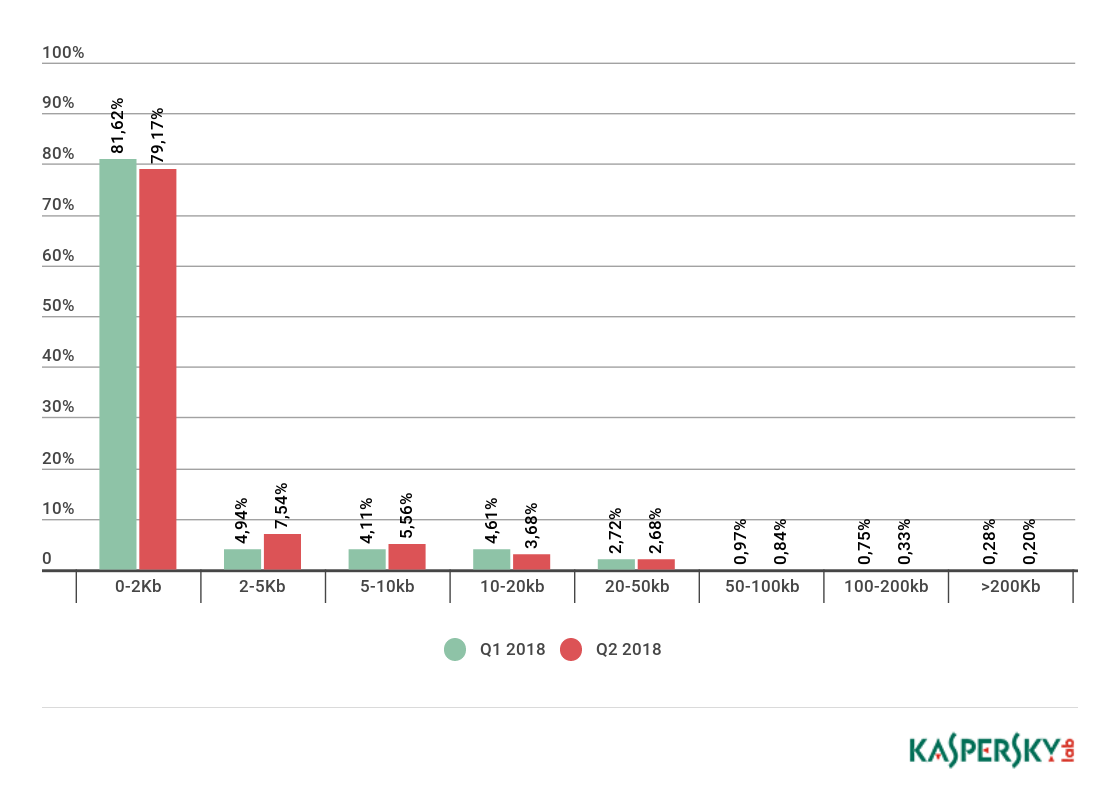
Spam email size, Q1 and Q2 2018 (download)
The results of the Q2 2018 indicate that the share of very small spam messages (up to 2 KB) fell 2.45 p.p. to 79.17%. The percentage of 5-10 KB spam messages, on the other hand, grew somewhat (by 1.45 p.p.) in comparison with the previous quarter and amounted to 5.56%.
The percentage of 10-20 KB spam messages was practically unchanged — it went down by 0.93 p.p. to 3.68%. 20-50 KB spam messages saw a similar trend, their share decreasing by 0.4 p.p. (to 2.68%) in comparison with the previous reporting period.
Malicious attachments: malware families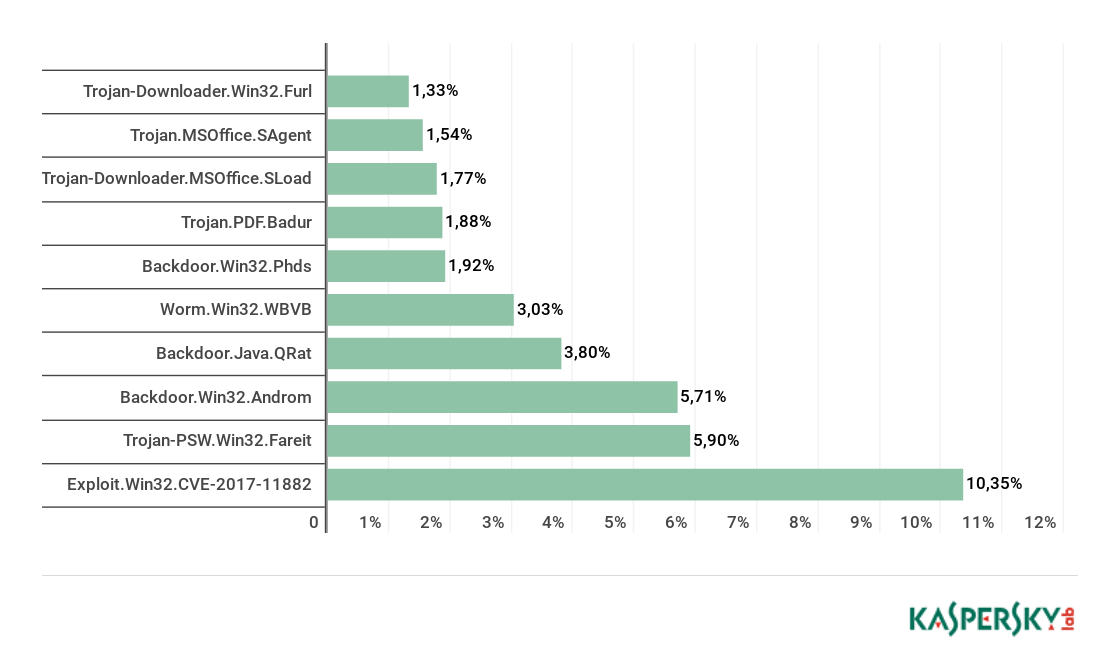
Top 10 malware families, Q2 2018 (download)
According to the results of the Q2 2018, the most widely-distributed family of malware by-mail was Exploit.Win32.CVE-2017-11882 (with 10.35%)/ This is the verdict attributed to various malware that exploited the CVE-2017-11882 vulnerability in Microsoft Word. The amount of mail with the Trojan-PSW.Win32.Fareit malware family in it, which steals user information and passwords, decreased during the second quarter, losing the first place and now occupying the second place (with 5.90%). The third and fourth places are occupied by Backdoor.Win32.Androm (5.71%) and Backdoor.Java.QRat (3.80%). The Worm.Win32.WBVB family was the fifth most popular malware with cybercriminals.
Countries targeted by malicious mailshots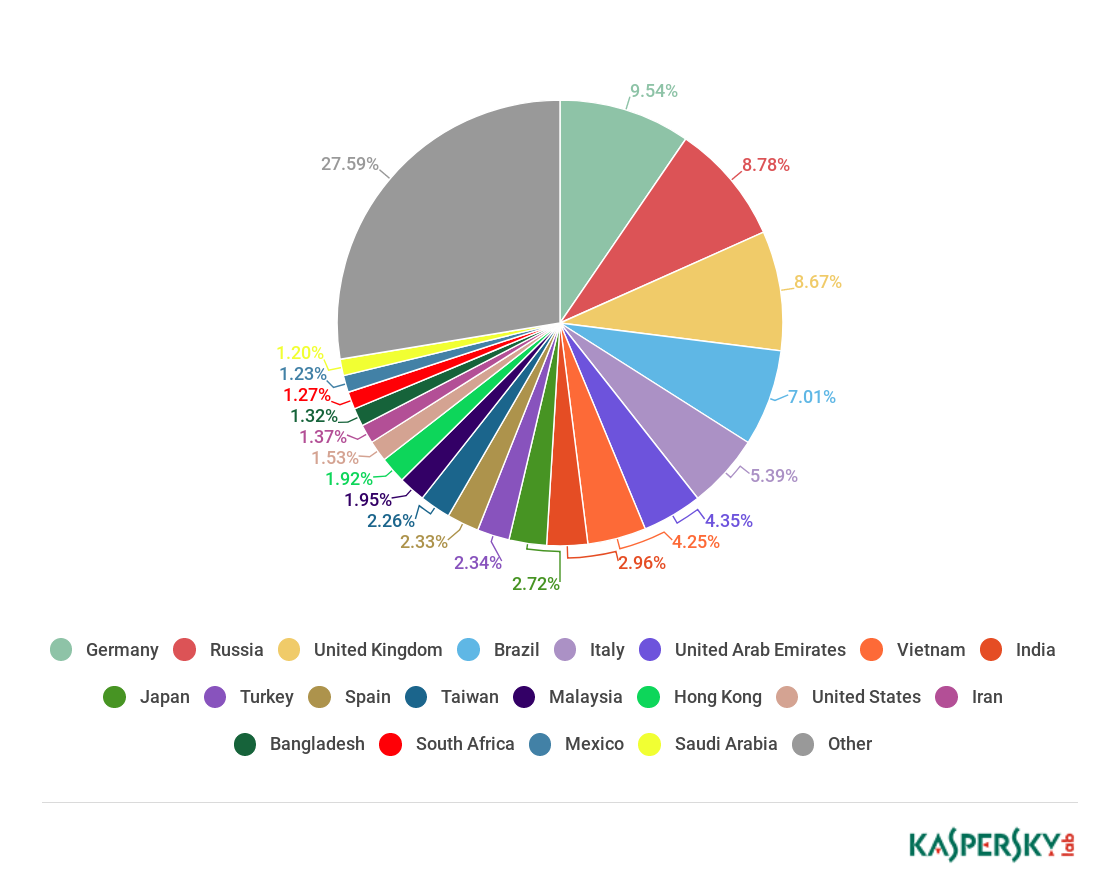
Distribution of Mail Anti-Virus triggers by country, Q2 2018 (download)
The first, second, and third places among the countries with the highest quantity of Mail Anti-Virus triggers in Q2 2018 were unchanged. Germany remained in the first place (9.54%), and the second and third places were taken by Russia and Great Britain (8.78% and 8.67%, respectively). The fourth and fifth places were taken by Brazil (7.07%) and Italy (5.39%).
Statistics: phishing
In the Q2 2018, the Antiphishing prevented 107,785,069 attempts to connect users to malicious websites. 9.6% of all Kaspersky Lab users around the world were subject to attack.
Geography of attacks
The country with the highest percentage of users attacked by phishing in Q2 2018 was again Brazil, with 15.51% (-3.56 p.p.).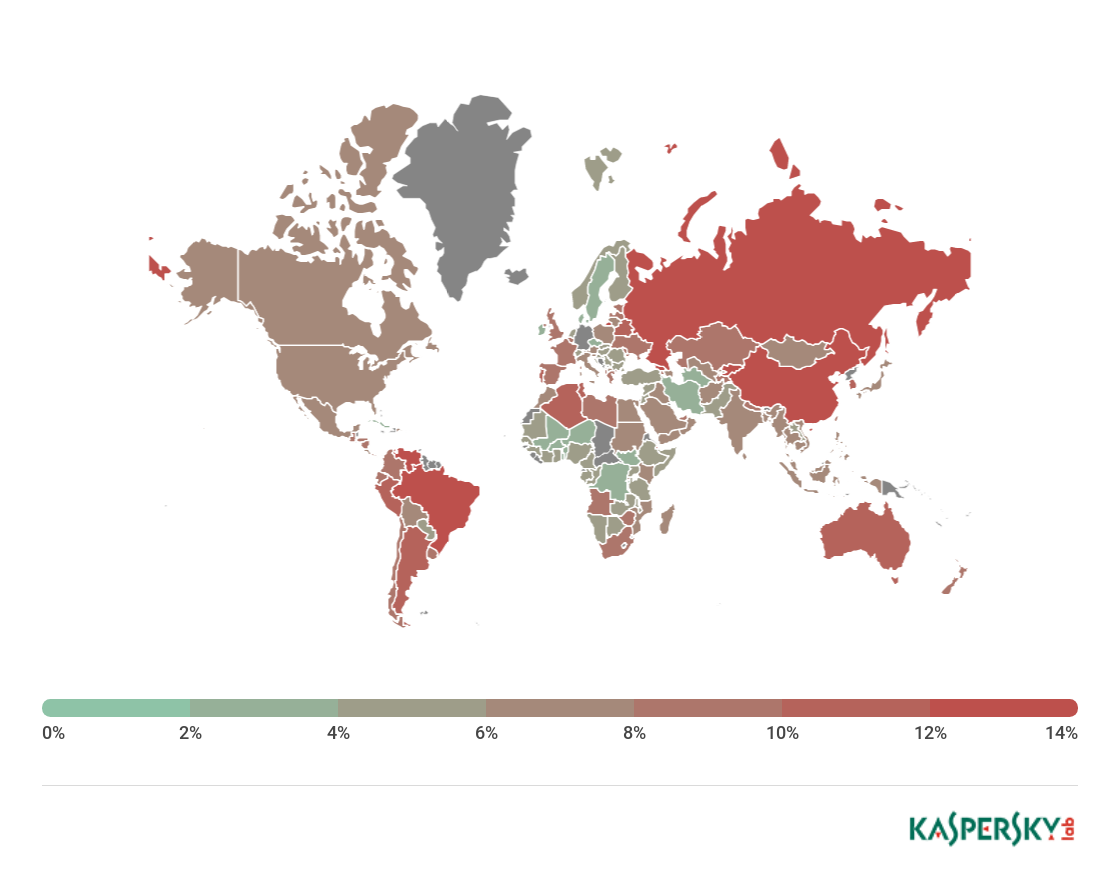
Geography of phishing attacks, Q2 2018 (download)
Country %*
Brazil 15.51
China 14.77
Georgia 14.44
Kyrgyzstan 13.60
Russia 13.27
Venezuela 13.26
Macao 12.84
Portugal 12.59
Belarus 12.29
South Korea 11.66
* Percentage of users whose Antiphishing system triggered against all Kaspersky Lab users in the respective country.
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Lab’s heuristic Anti-Phishing component. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.[/caption]
In Q2 2018, the Global Internet Portals category again took first place with 25.00% (+1.3 p.p.).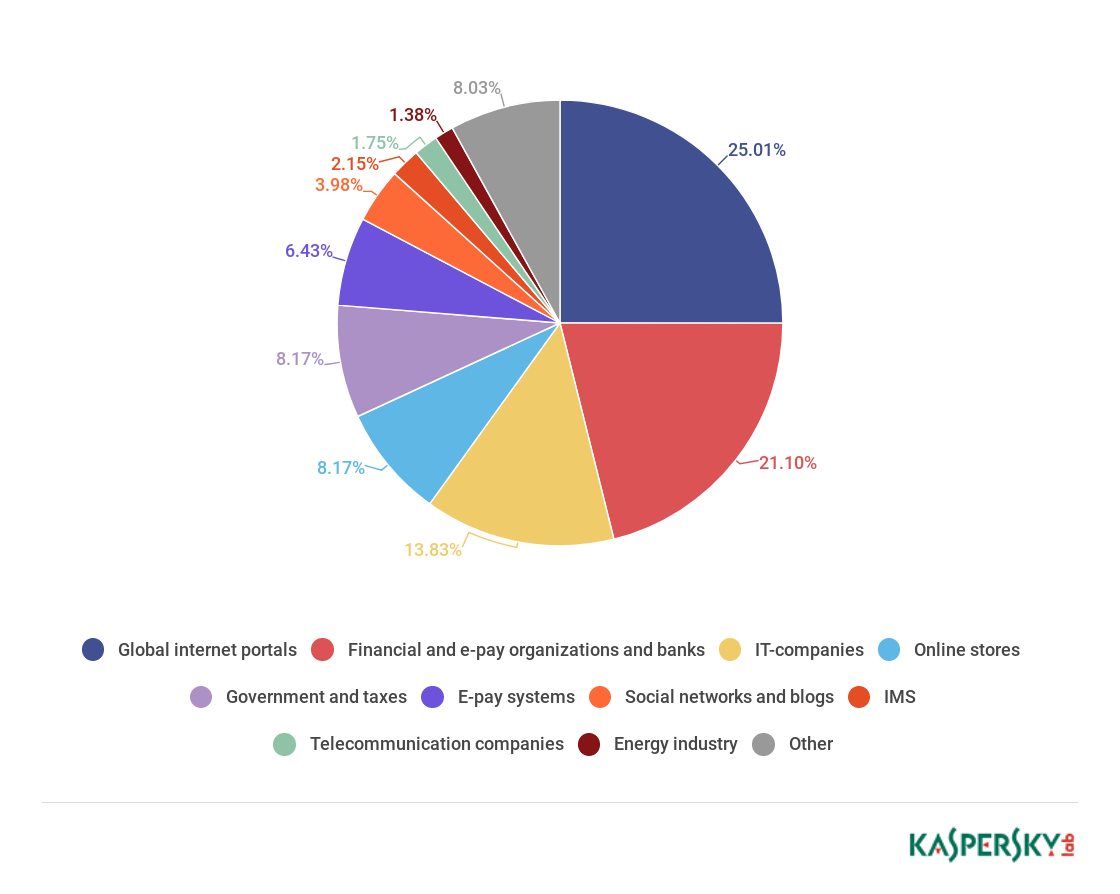
Distribution of organizations affected by phishing attacks by category, Q2 2018. (download)
The percentage of attacks on organizations that may be combined into a general Finance category (banks, at 21.10%, online stores, at 8.17%, and payment systems, at 6.43%) fell to 35.70% (-8.22 p.p.). IT companies in the second quarter were more often subject to threats then in the first quarter. This category saw an increase of 12.28 p.p. to 13.83%.
Conclusion
Average spam volume of 49.66% in world mail traffic in this quarter fell 2.16 p.p. in comparison with the previous reporting period, and the Antiphishing system prevented more than 107M attempts to connect users to phishing sites, which is 17M more than in the first quarter of 2018.
In this quarter, malefactors actively used GDPR, World Cup, and cryptocurrency themes, and links to malicious websites could be found on social networks and messengers (users were often distributing them themselves), as well as in marketing messages served by large search engines.
Exploit.Win32.CVE-2017-11882 was the most widely-distributed family of malware via mail, at 10.35%. Trojan-PSW.Win32.Fareit fell from the first place to the second place (5.90%), and the third and fourth places were taken by Backdoor.Win32.Androm (5.71%) and Backdoor.Java.QRat (3.80%).