Spam and phishing in Q3 2018
7.11.2018 Kaspersky Phishing Spam
Quarterly highlights
Personal data in spam
We have often said that personal data is candy on a stick to fraudsters and must be kept safe (that is, not given out on dubious websites). It can be used to gain access to accounts and in targeted attacks and ransomware campaigns.
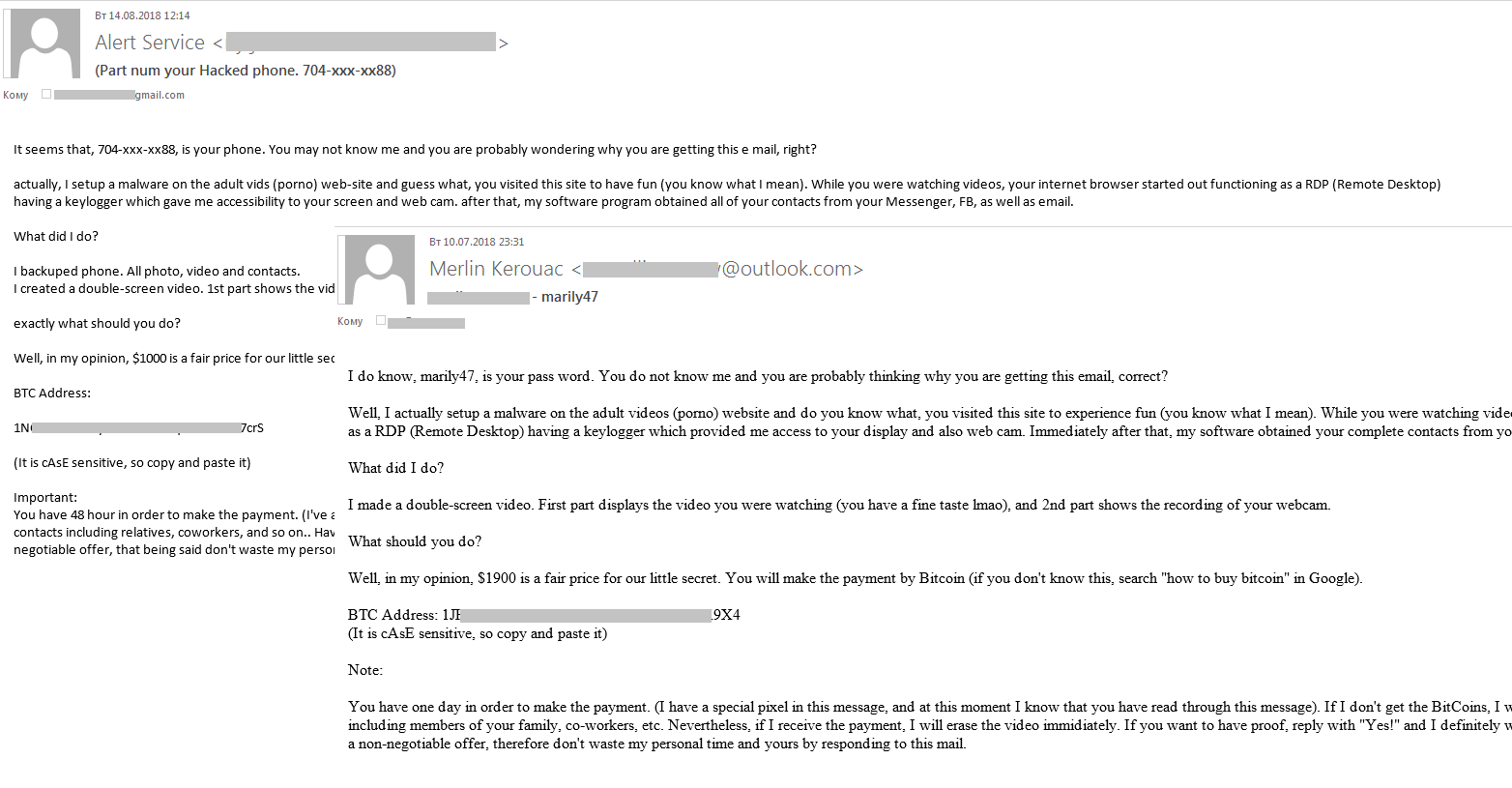
In Q3, we registered a surge of fraudulent emails in spam traffic. This type of scam we have already reported at the beginning of the year. A ransom (in bitcoins) is demanded in exchange for not disclosing the “damaging evidence” concerning the recipients. The new wave of emails contained users’ actual personal data (names, passwords, phone numbers), which the scammers used to try to convince victims that they really had the information specified in the message. The spam campaign was carried out in several stages, and it is likely that the fraudsters made use of a range of personal information databases, as evidenced, for example, by the telephone number formats that varied from stage to stage.
Whereas before, the target audience was primarily English-speaking, in September we logged a spate of mailings in other languages, including German, Italian, Arabic, and Japanese.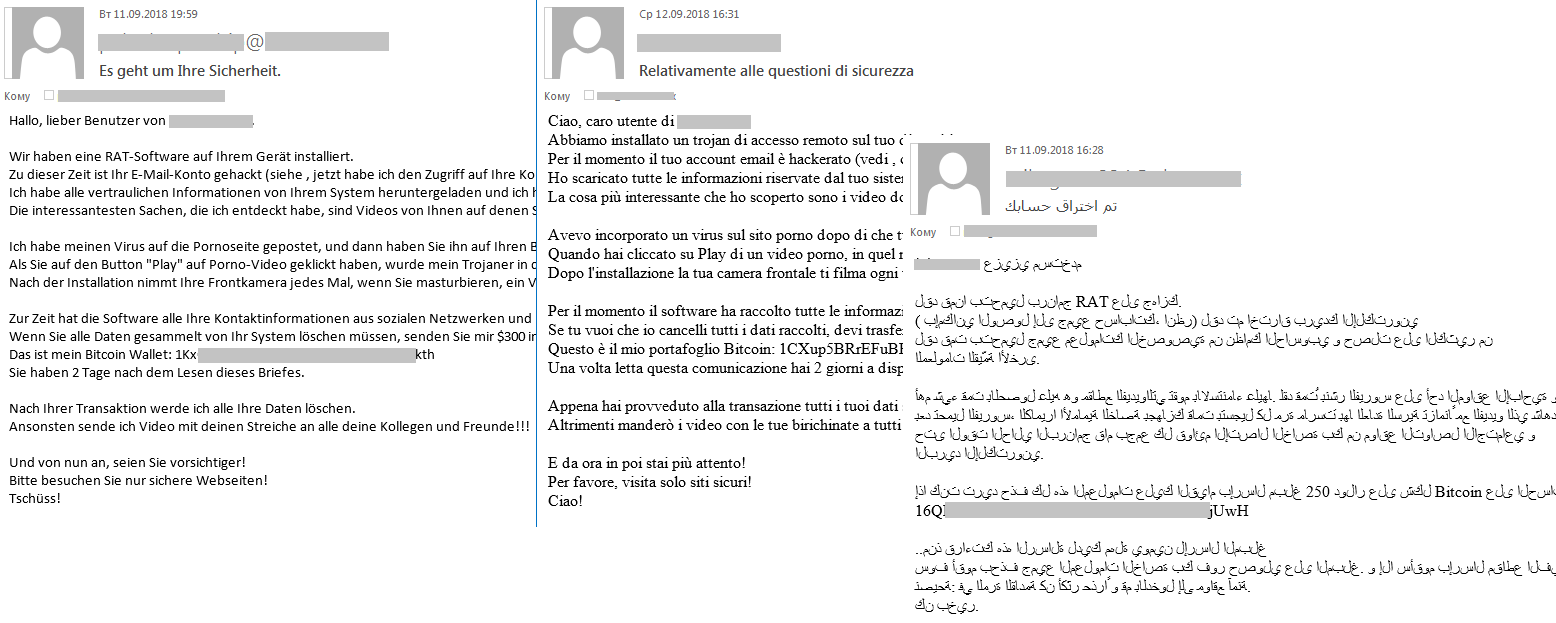
The amount demanded by the ransomers ranged from a few hundred to several thousand dollars. To collect the payments, different Bitcoin wallets were used, which changed from mailing to mailing. In July, 17 transactions worth more than 3 BTC ($18,000 at the then exchange rate) were made to one of such wallets.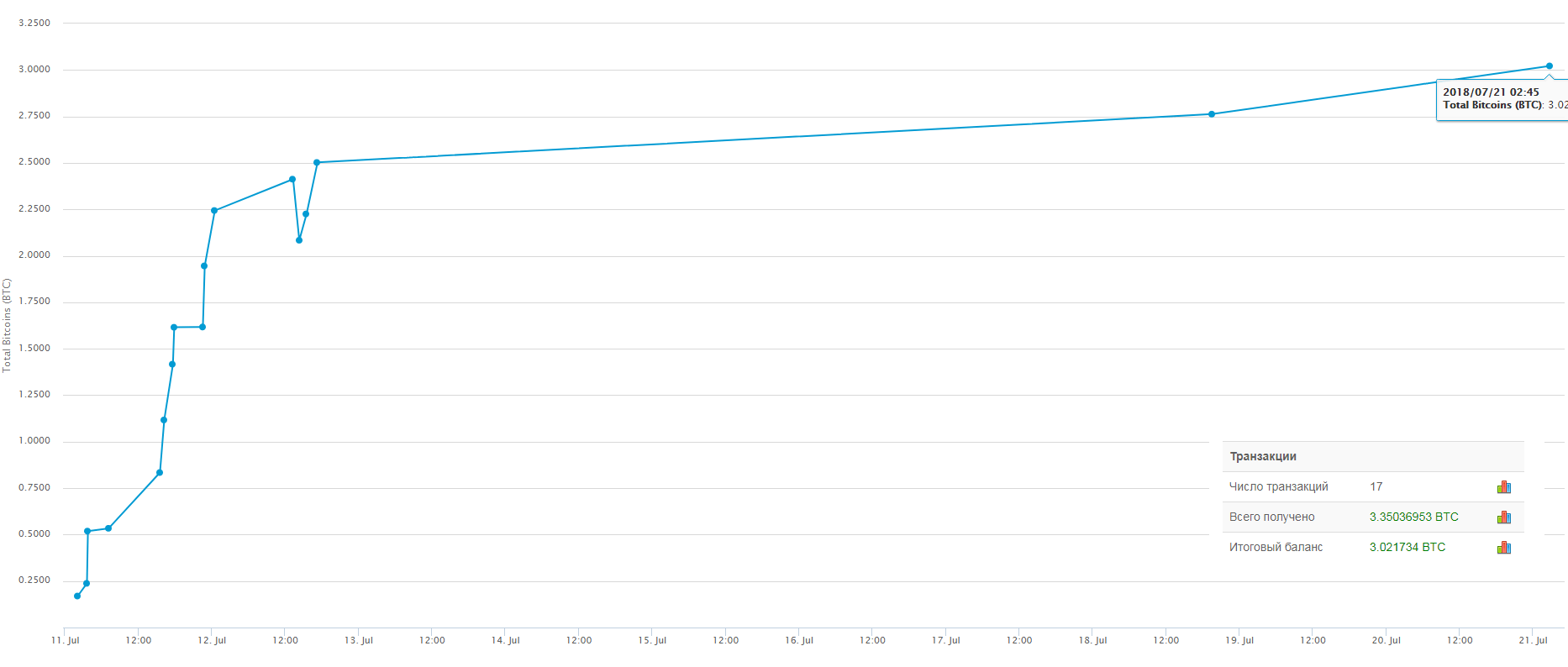
Transactions to scammers’ Bitcoin wallets
Also in Q3, we detected a malicious spam campaign aimed at corporate users. The main target was passwords (for browsers, instant messengers, email and FTP clients, cryptocurrency wallets, etc.). The cybercriminals attempted to infect victim computers with Loki Bot malware, concealing it in ISO files attached to messages. The latter were made to look like business correspondence or notifications from well-to-do companies.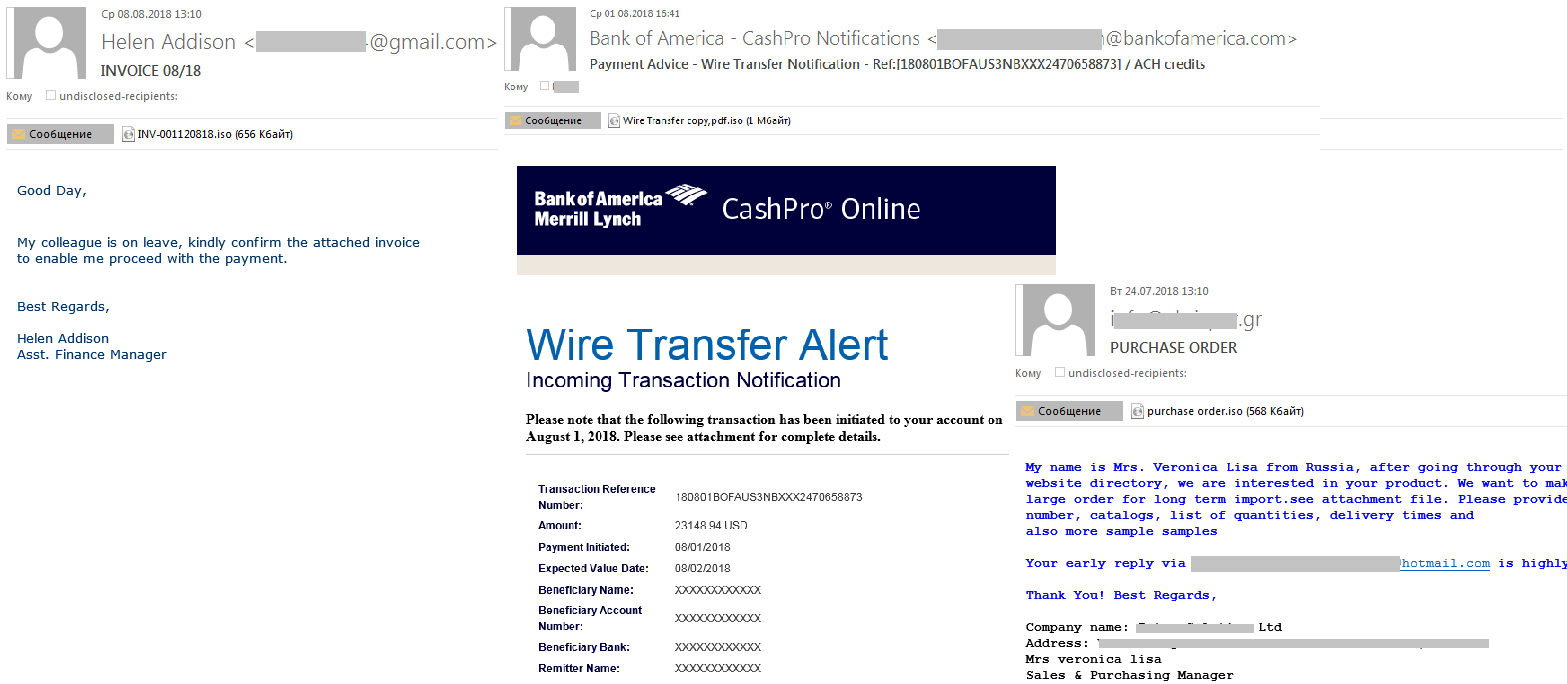
Malicious spam attacks against the banking sector
The owners of the Necurs botnet, which in Q2 was caught sending malicious emails with IQY (Microsoft Excel Web Query) attachments, turned their attention to the banking sector and, like in Q2, used a non-typical file format for spam, this time PUB (Microsoft Publisher). Messages were sent to the email addresses of credit institutions in different countries, and the PUB file attachments contained Trojan loaders for downloading executable files (detected as Backdoor.Win32.RA-based) onto victim computers.
We observed that the owners of Necurs are making increasing use of various techniques to bypass security solutions and send malicious spam containing attachments with non-typical extensions so as not to arouse users’ suspicion.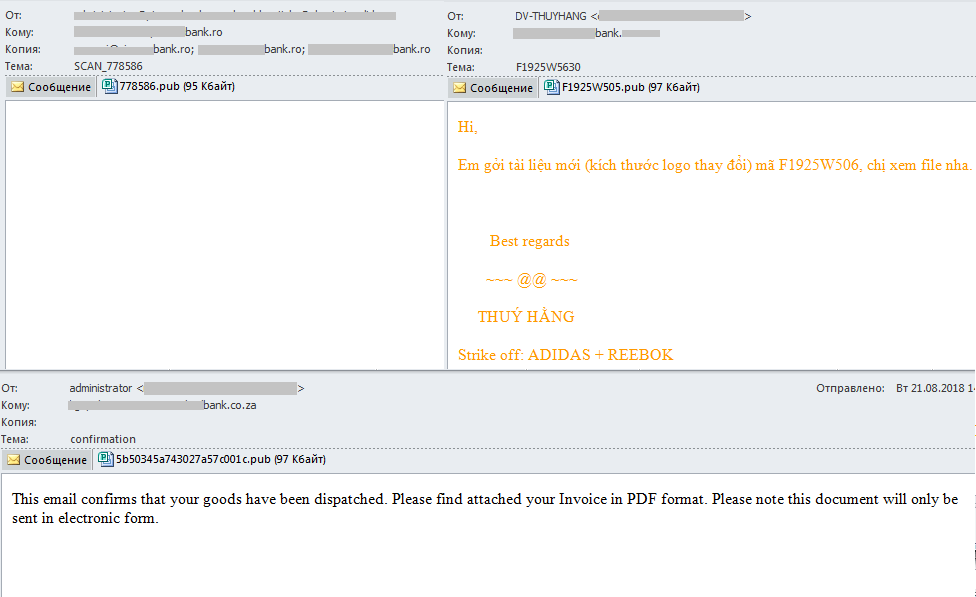
New iPhone launch
Late Q3 saw the release of Apple’s latest gizmo. Unsurprisingly, it coincided with a spike in email spam from Chinese “companies” offering Apple accessories and replica gadgets. Links in such messages typically point to a recently created, generic online store. Needless to say, having transferred funds to such one-day websites, you lose your money and your goods are not arriving.
The release also went hand in hand with a slight rise in both the number of phishing schemes exploiting Apple (and its services) and messages with malicious attachments: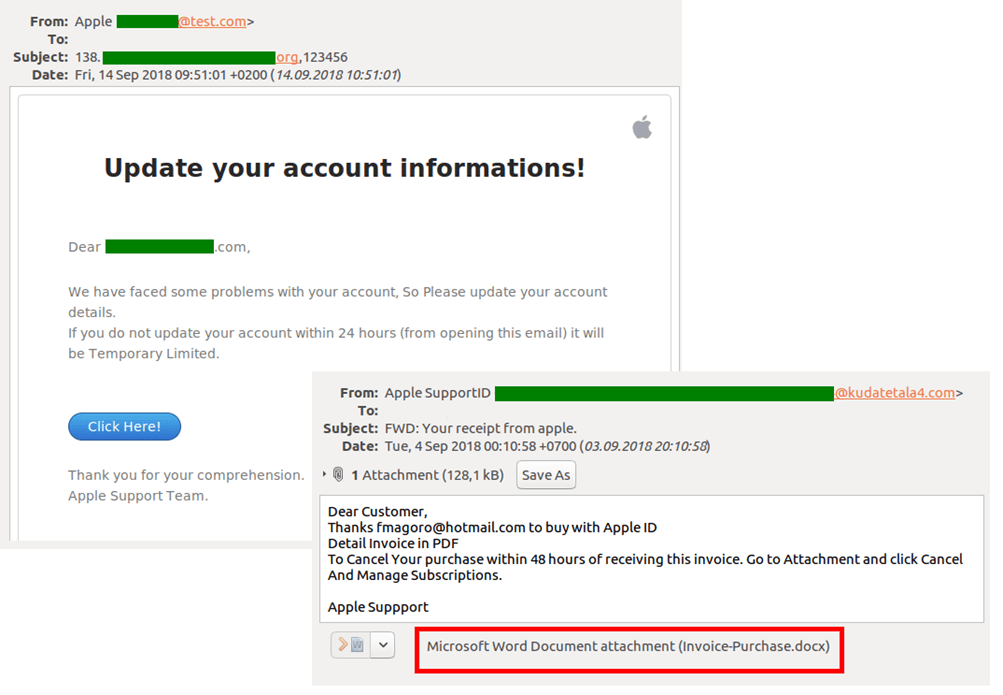
Classic pharma spam in a new guise
Spammers are constantly looking for ways to get round mail filters and increase the “deliverability” of their offers. To do so, they try to fabricate emails (both the contents and technical aspects) that look like messages from well-known companies and services. For example, they copy the layout of banking and other notifications and add bona fide headers in the fields that the user is sure to see.
Such techniques, typical of phishing and malicious campaigns, are being used more often in “classic spam” – for example, in messages offering prohibited medicines. For instance, this past quarter we detected messages disguised as notifications from major social networks, including LinkedIn. The messages contained a phoney link that we expected to point to a phishing form asking for personal data, but instead took us to a drug store.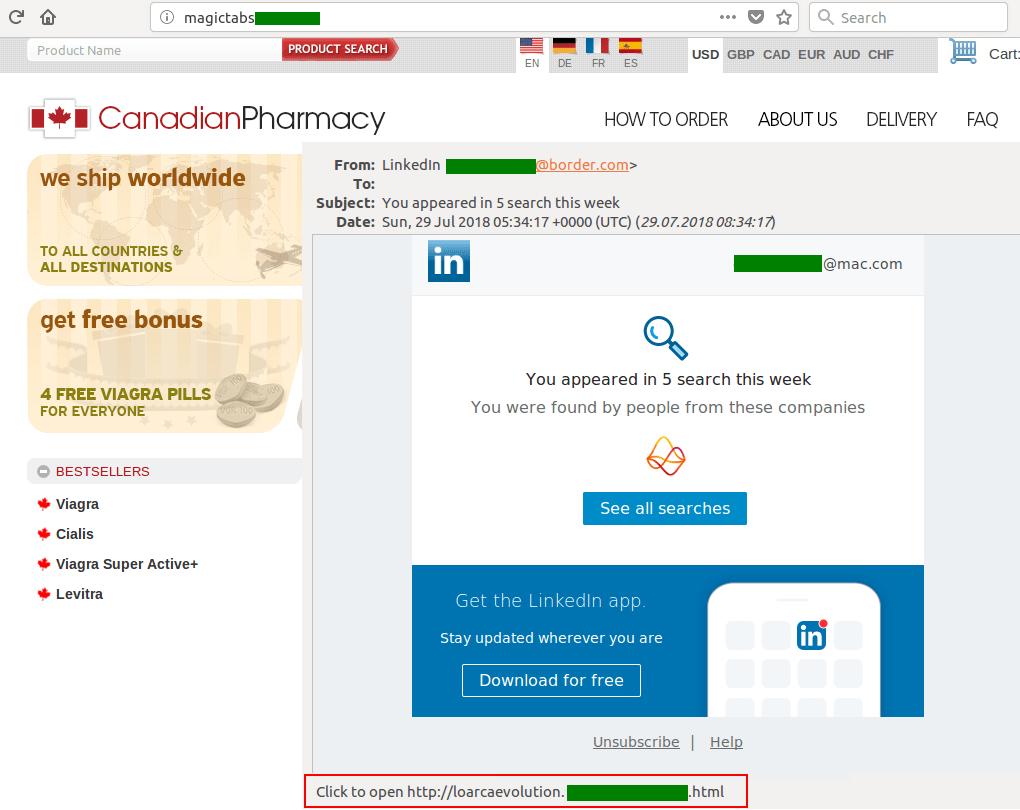
This new approach is taken due to the fact that this type of spam in its traditional form has long been detectable by anti-spam solutions, so spammers started using disguises. We expect this trend to pick up steam.
Universities
Since the start of the academic year, scammers’ interest in gaining access to accounts on university websites has risen. We registered attacks against 131 universities in 16 countries worldwide. Cybercriminals want to get their hands on both personal data and academic research.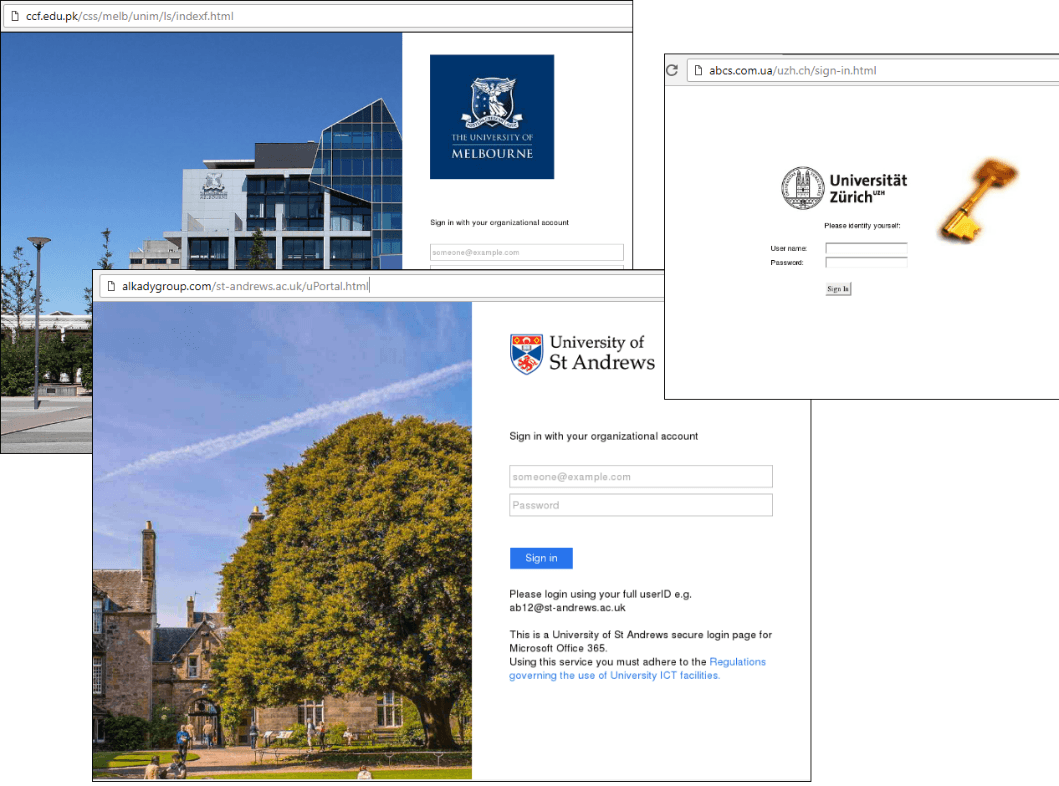
Fake login pages to personal accounts on university websites
Job search
To harvest personal data, attackers exploit the job-hunting efforts. Pages with application forms lure victims with tempting offers of careers in a big-name company, large salary, and the like.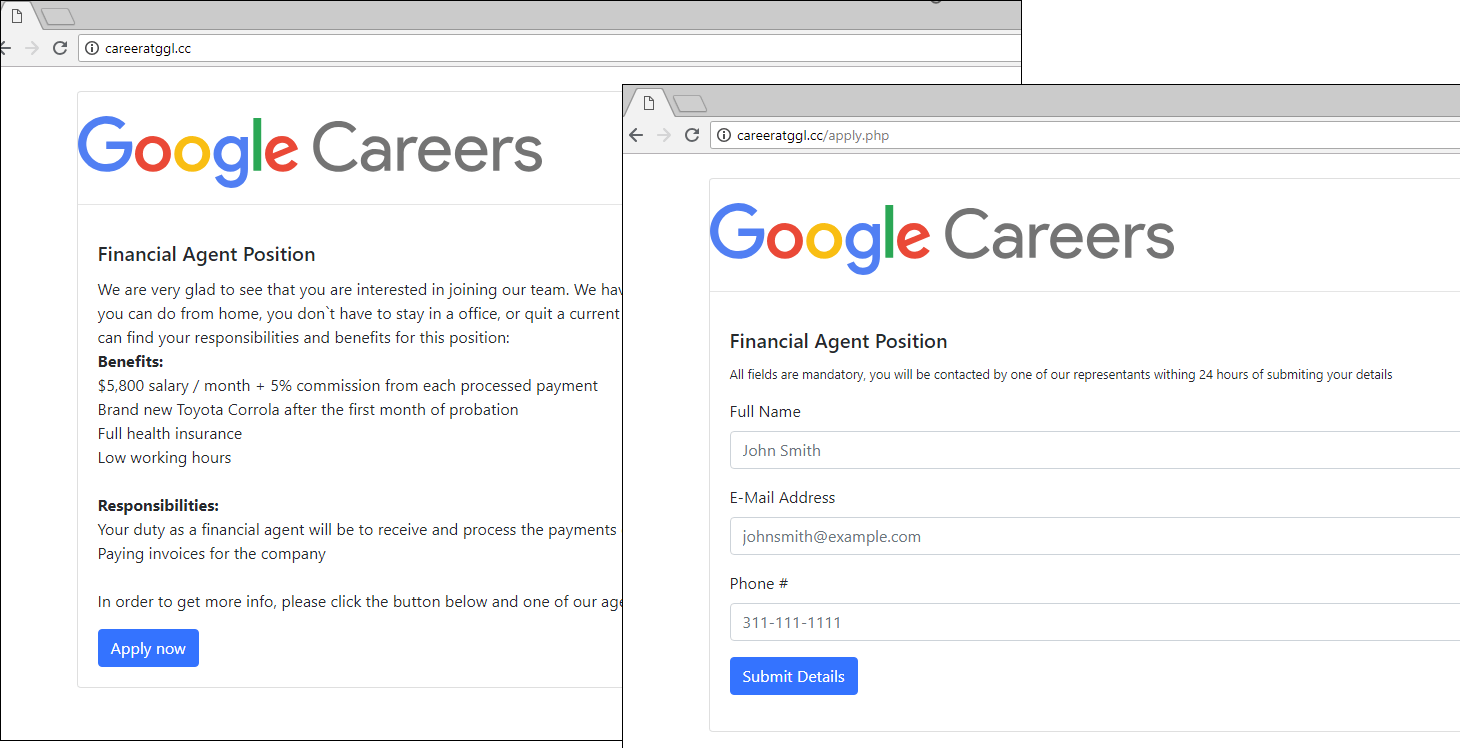
Propagation methods
This quarter we are again focused on ways in which phishing and other illegitimate content is distributed by cybercriminals. But this time we also want to draw attention to methods that are gaining popularity and being actively exploited by attackers.
Scam notifications
Some browsers make it possible for websites to send notifications to users (for example, Push API in Chrome), and this technology has not gone unnoticed by cybercriminals. It is mainly deployed by websites that collaborate with various partner networks. With the aid of pop-up notifications, users are lured onto “partner” sites, where they are prompted to enter, for example, personal data. The owners of the resource receive a reward for every user they process.
By default, Chrome requests permission to enable notifications for each individual site, and so as to nudge the user into making an affirmative decision, the attackers state that the page cannot continue loading without a little click on the Allow button.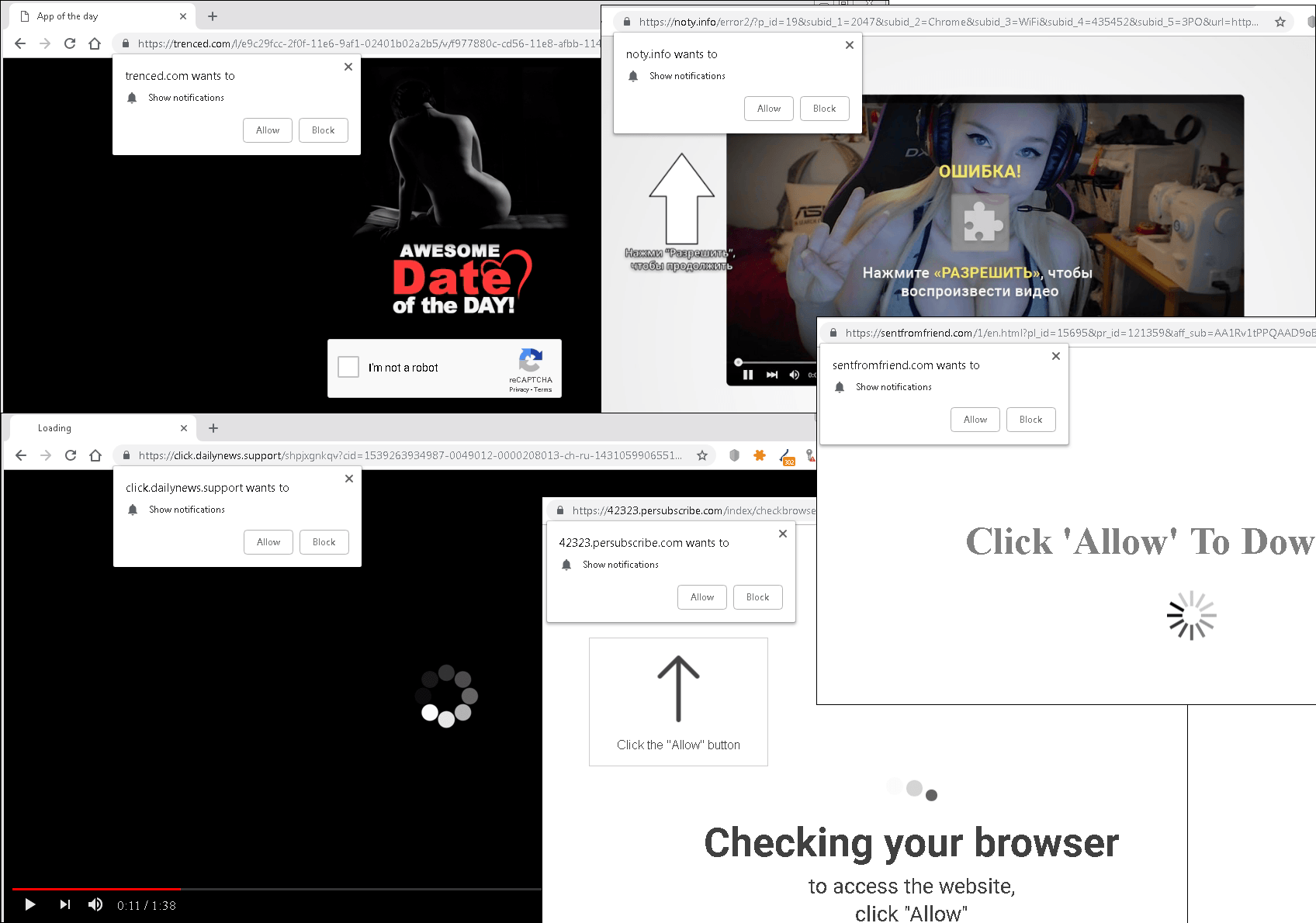
Having given the site permission to display notifications, many users simply forget about it, so when a pop-up message appears on the screen, they don’t always understand where it came from.
Notifications are tailored to the user’s location and displayed in the appropriate language
The danger is that notifications can appear when the user is visiting a trusted resource. This can mislead the victim as regards the source of the message: everything seems to suggest it came from the trusted site currently open. The user might see, for instance, a “notification” about a funds transfer, giveaway, or tasty offer. They all generally lead to phishing sites, online casinos, or sites with fake giveaways and paid subscriptions: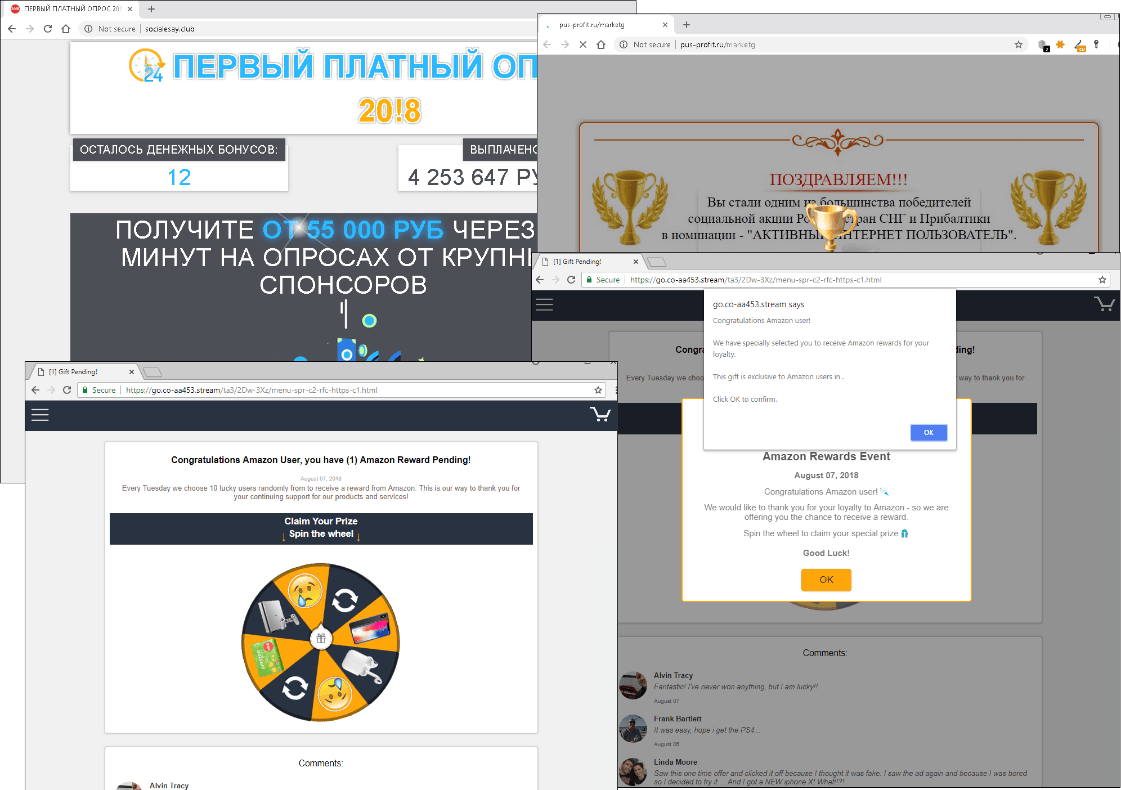
Examples of sites that open when users click on a notification
Clicking on a notification often leads to an online gift card generator, which we covered earlier in the quarter (it also works in the opposite direction: the resource may prompt to enable push notifications). Such generators offer visitors the chance to generate free gift card codes for popular online stores. The catch is that in order to get the generated codes, the visitor needs to prove their humanness by following a special link. Instead of receiving a code, the user is sent on a voyage through a long chain of partner sites with invitations to take part in giveaways, fill out forms, download stuff, sign up for paid SMS mailings, and much more.
Media
The use of media resources is a rather uncommon, yet effective way of distributing fraudulent content. This point is illustrated by the story of the quite popular WEX cryptocurrency exchange, which prior to 2017 went by the name of BTC-E. In August 2018, fake news was inserted into thematic “third tier” Russian media saying that, due to internal problems, the exchange was changing its domain name to wex.ac:
The wex.nz administration soon tweeted (its tweets are published on the exchange’s home page) that wex.ac was just another imitator and warned users about transferring funds.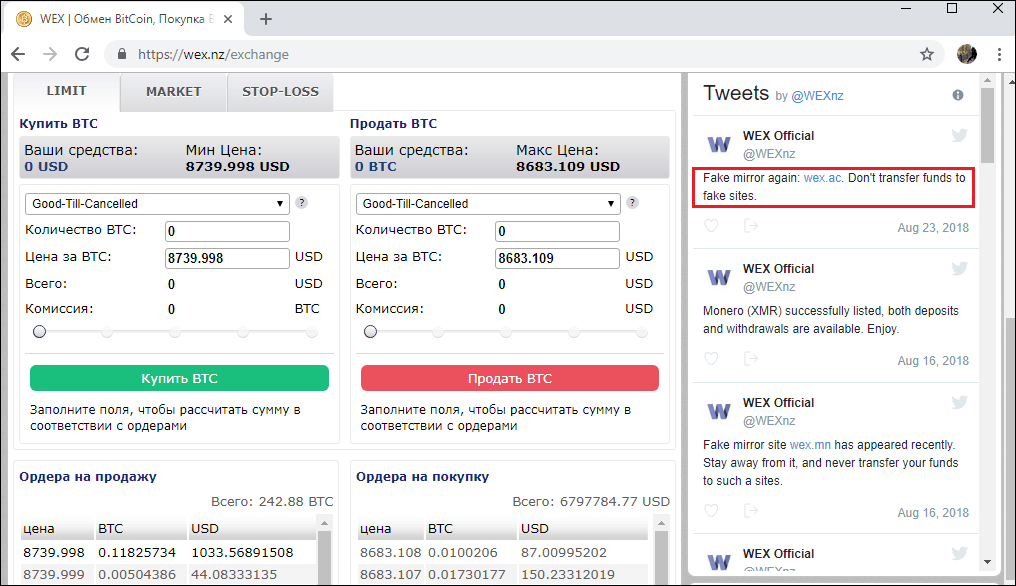
But that did not stop the scammers, who released more news about the exchange moving to a new domain. This time to the .sc zone: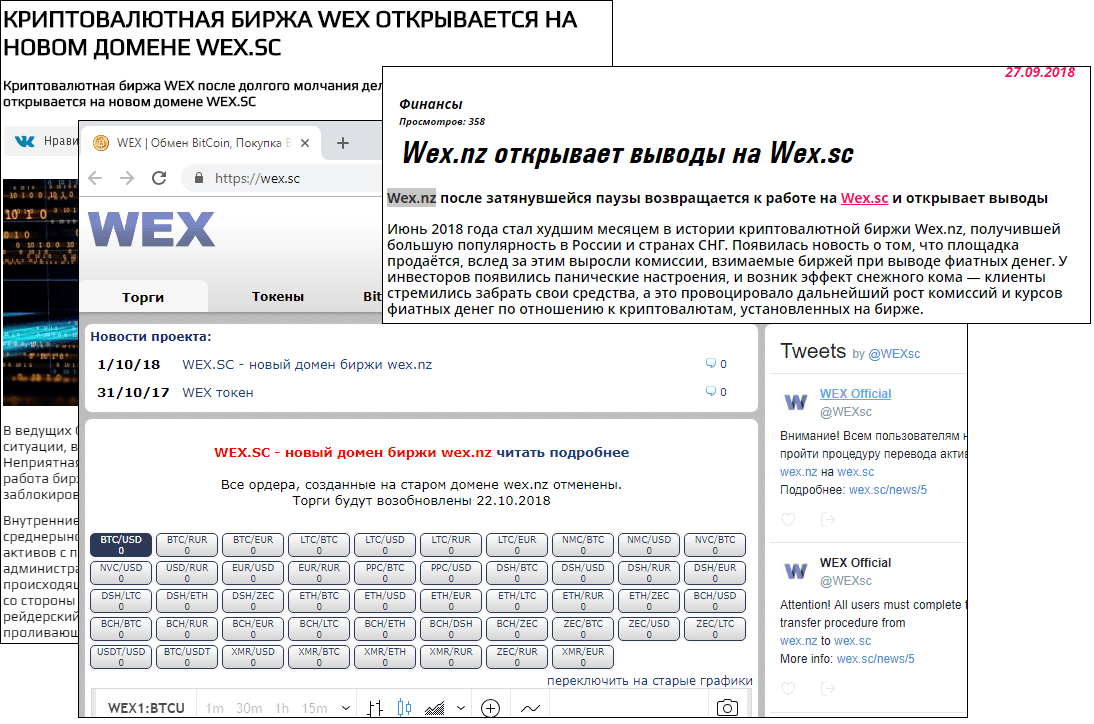
Instagram
Among the social media platforms used by scammers to distribute content, Instagram warrants a special mention. Only relatively recently have cybercriminals started paying attention to it. In Q3 2018, we came across many fake US Internal Revenue Service user accounts in this social network, as well as many others purporting to be an official account of one of the most widely-used Brazilian banks.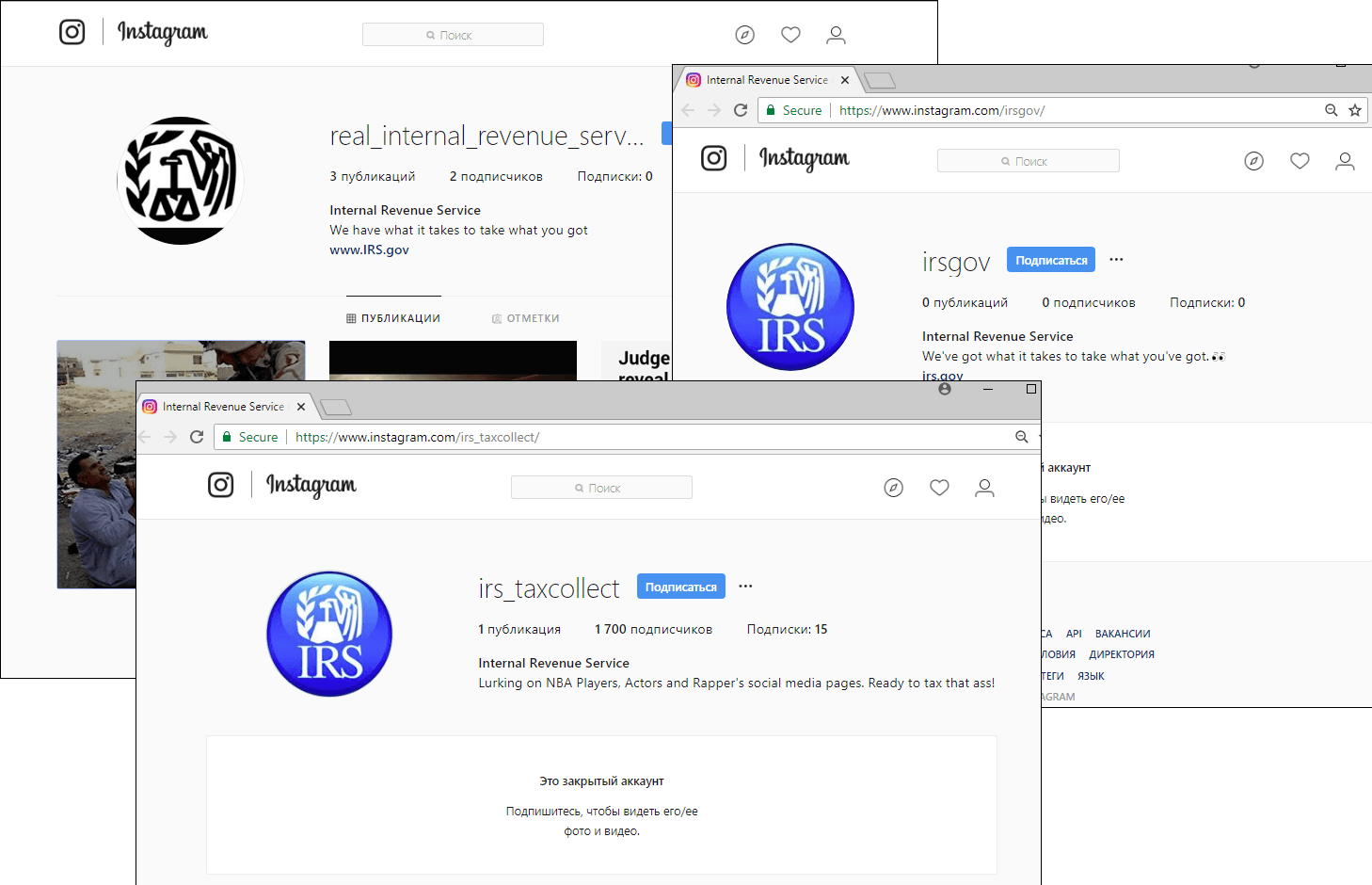
Fake IRS accounts on Instagram
Scammers not only create fakes, but seek access to popular accounts: August this year saw a wave of account hacking sweep through the social network. We observed accounts changing owners as a result of phishing attacks with “account verification” prompts – users themselves delivered their credentials on a plate in the hope of getting the cherished blue tick.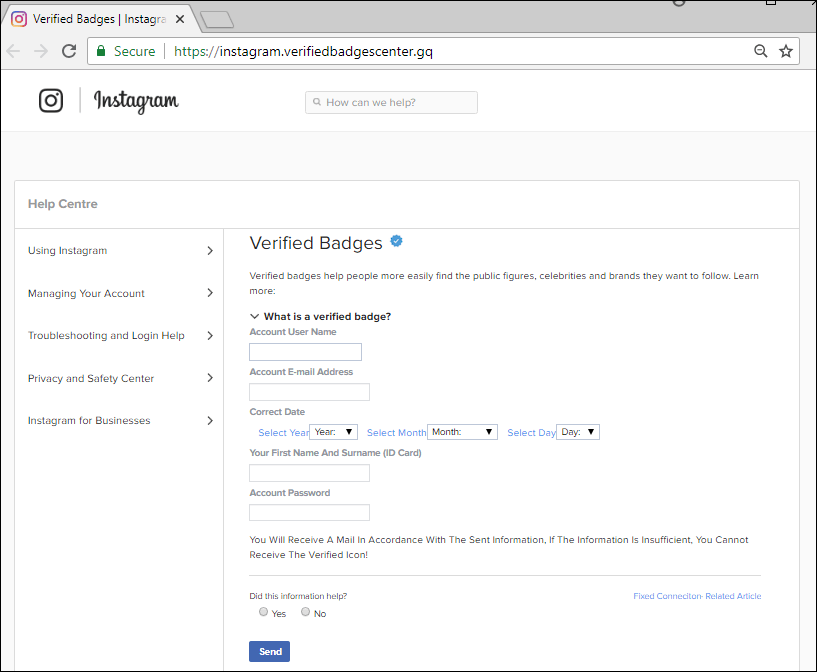
Back when scammers offered to “verify” accounts, there was no such function in the social network: the administration itself decided whom to award the sacred “badge.” Now it is possible to apply for one through the account settings.
Statistics: spam
Proportion of spam in email traffic
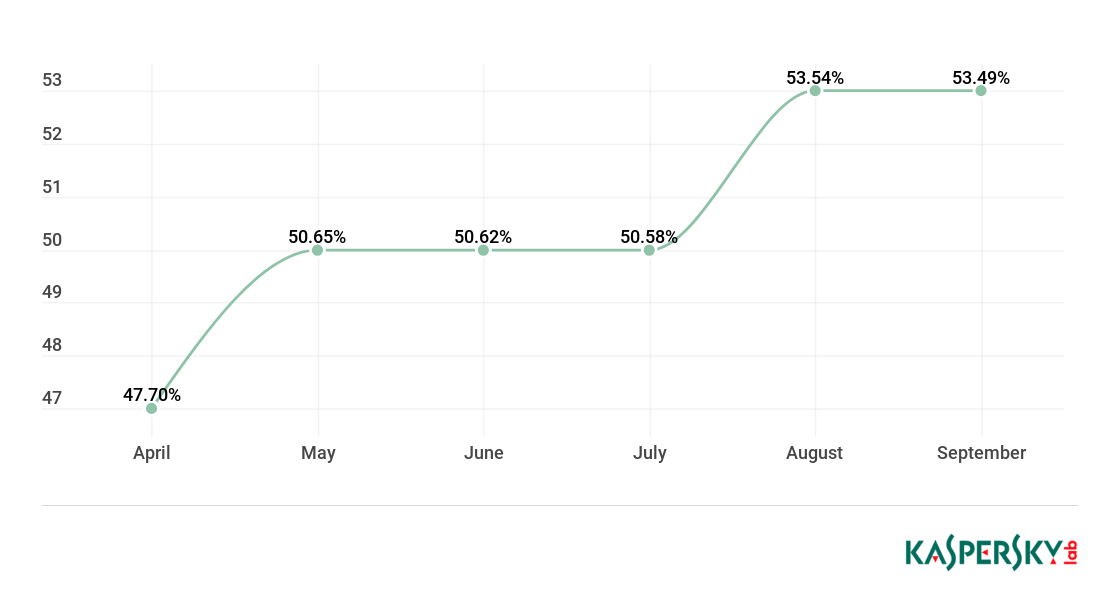
Proportion of spam in global email traffic, Q2 and Q3 2018 (download)
In Q3 2018, the largest share of spam was recorded in August (53.54%). The average percentage of spam in global mail traffic was 52.54%, up 2.88 p.p. against the previous reporting period.
Sources of spam by country
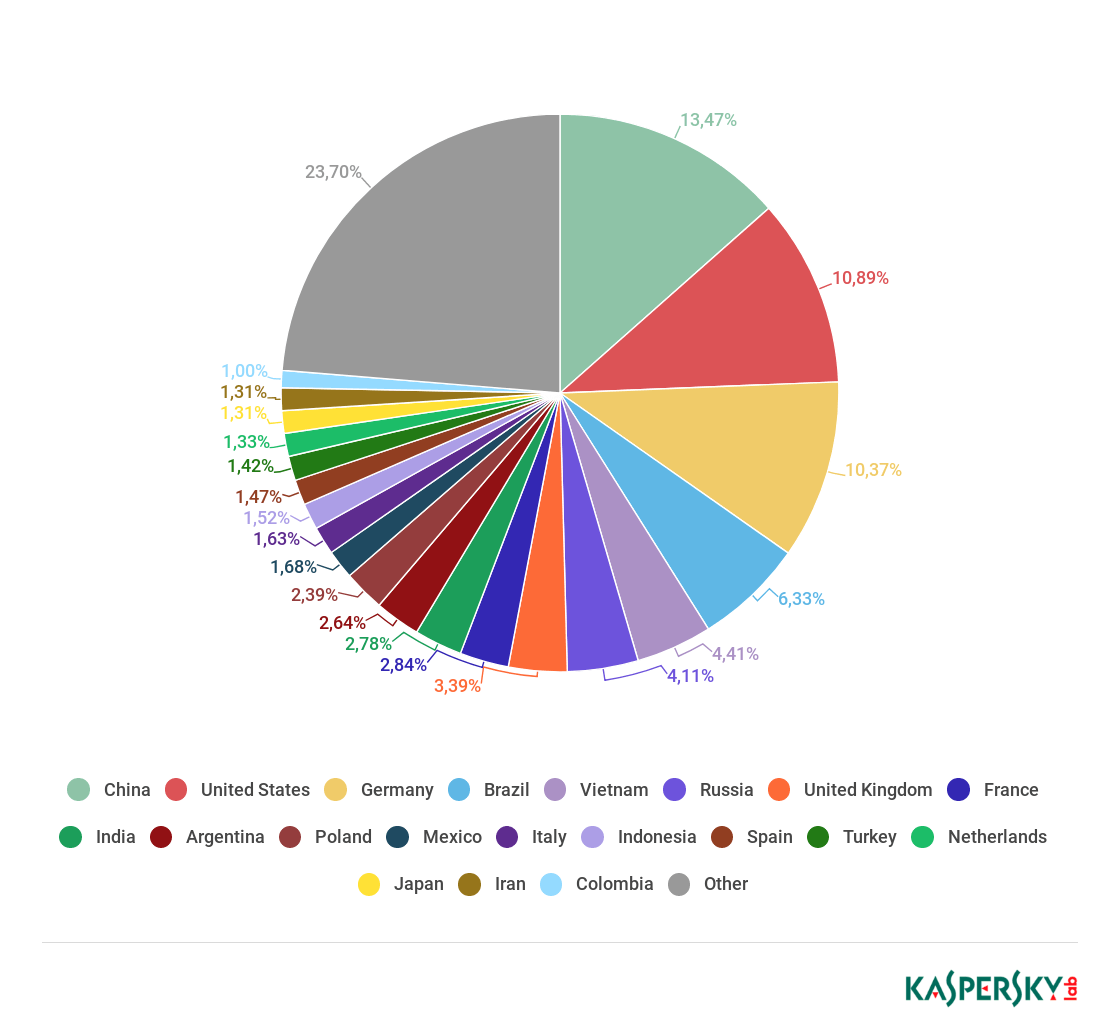
Sources of spam by country, Q3 2018 (download)
The three leading source countries for spam in Q3 were the same as in Q2 2018: China is in first place (13.47%), followed by the USA (10.89%) and Germany (10.37%). Fourth place goes to Brazil (6.33%), and fifth to Vietnam (4.41%). Argentina (2.64%) rounds off the Top 10.
Spam email size
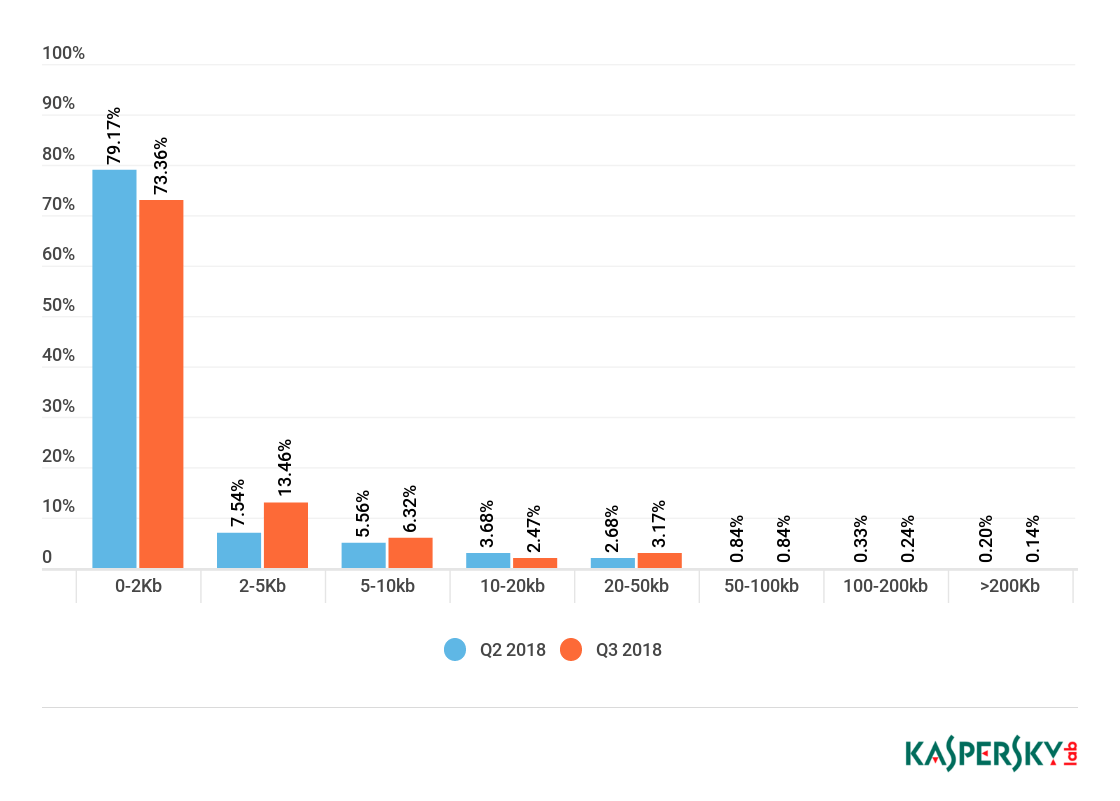
Spam email size, Q2 and Q3 2018 (download)
In Q3 2018, the share of very small emails (up to 2 KB) in spam fell by 5.81 p.p. to 73.36%. The percentage of emails sized 5-10 KB increased slightly compared to Q2 (+0.76 p.p.) and amounted to 6.32%. Meanwhile, the proportion of 10-20 KB emails dropped by 1.21 p.p. to 2.47%. The share of 20-50 KB spam messages remained virtually unchanged, climbing a mere 0.49 p.p. to 3.17%.
Malicious attachments: malware families
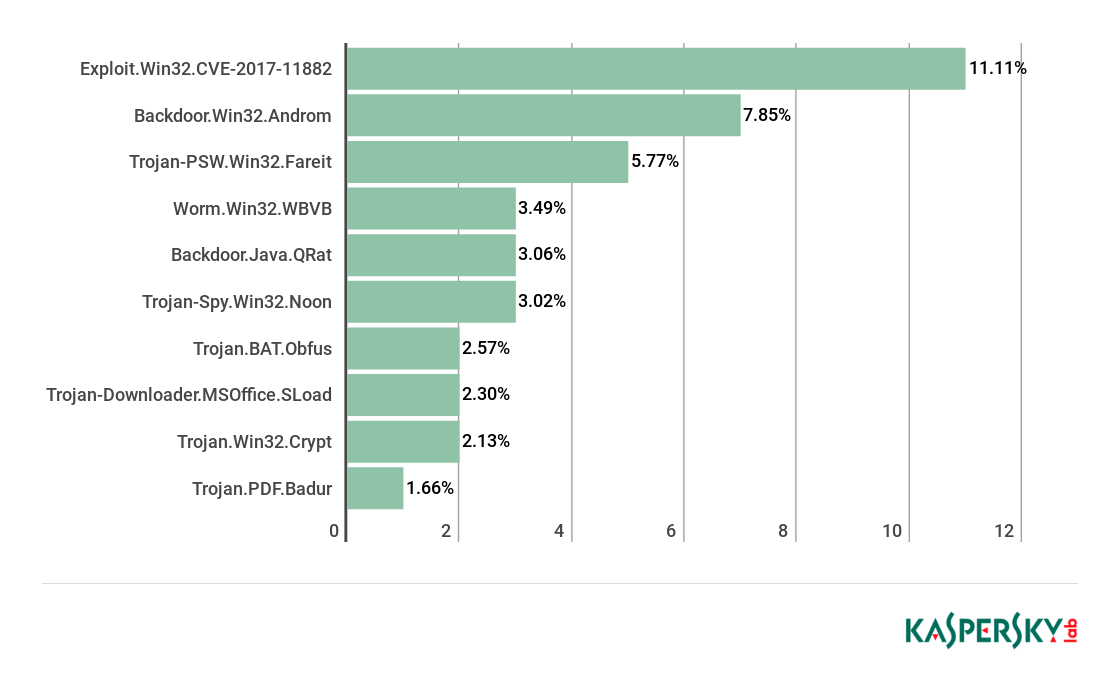
Top 10 malicious families in mail traffic, Q3 2018 (download)
According to the results of Q3 2018, still the most common malware in mail traffic were objects assigned the verdict Exploit.Win32.CVE-2017-11882, adding 0.76 p.p. since the last quarter (11.11%). The Backdoor.Win32.Androm bot was encountered more frequently than in the previous quarter and ranked second (7.85%), while Trojan-PSW.Win32.Farei dropped to third place (5.77%). Fourth and fifth places were taken by Worm.Win32.WBVB and Backdoor.Java.QRat, respectively.
Countries targeted by malicious mailshots
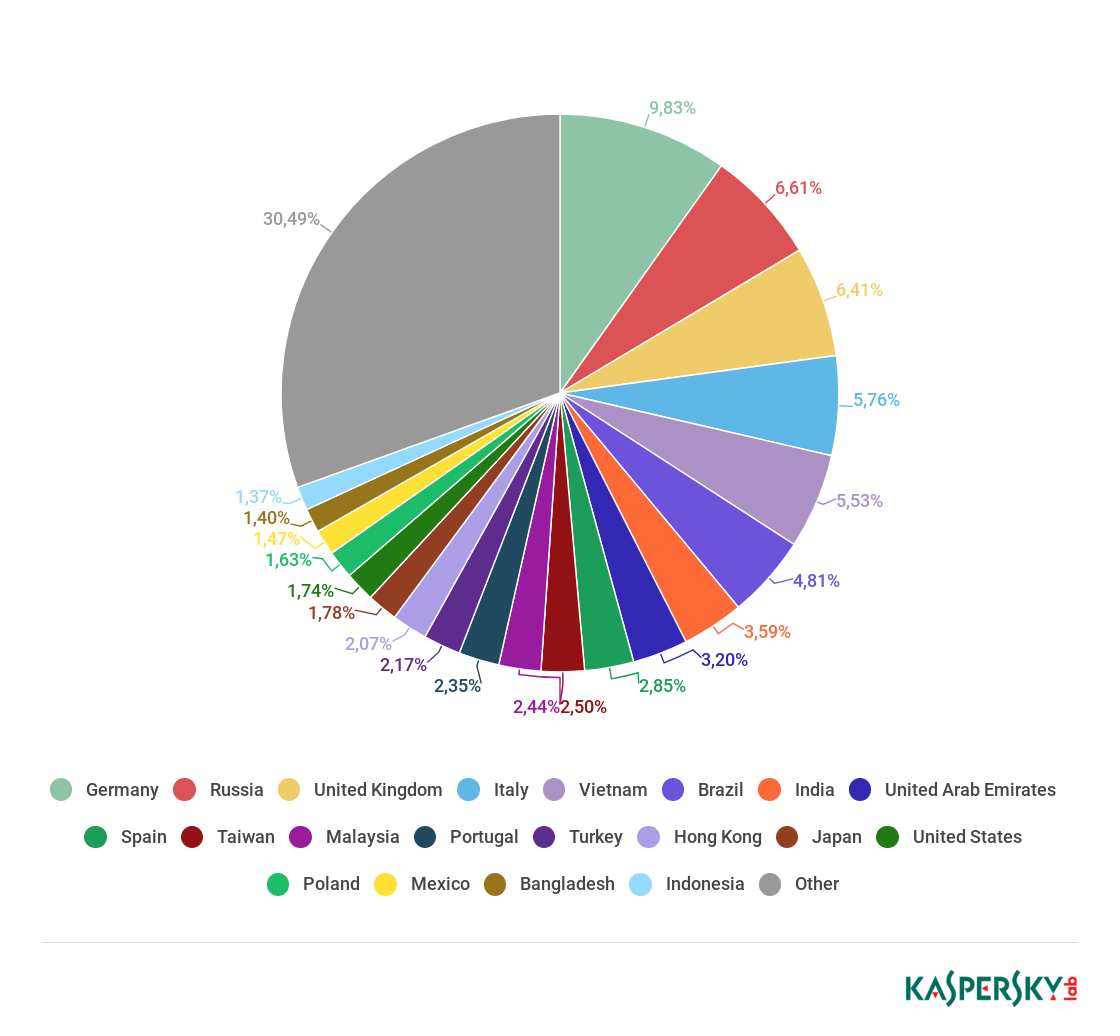
Countries targeted by malicious mailshots, Q3 2018 (download)
The Top 3 countries by number of Mail Anti-Virus triggers in Q3 remain unchanged since the start of the year: Germany took first place (9.83%), with Russia in second (6.61%) and the UK in third (6.41%). They were followed by Italy in fourth (5.76%) and Vietnam in fifth (5.53%).
Statistics: phishing
In Q3 2018, the Anti-Phishing system prevented 137,382,124 attempts to direct users to scam websites. 12.1% of all Kaspersky Lab users worldwide were subject to attack.
Geography of attacks
The country with the highest percentage of users attacked by phishing in Q3 2018 was Guatemala with 18.97% (+8.56 p.p.).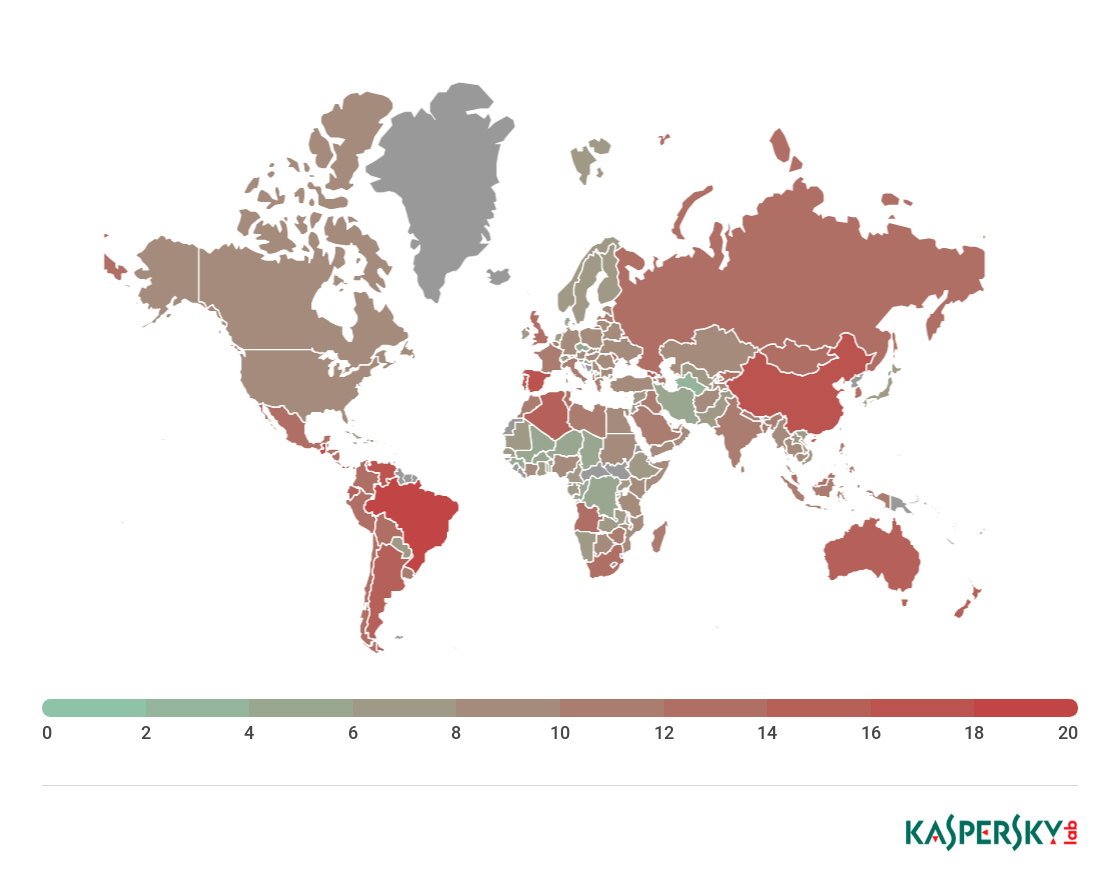
Geography of phishing attacks, Q3 2018 (download)
Q2’s leader Brazil dropped to second place, with 18.62% of users in this country attacked during the reporting period, up 3.11 p.p. compared to Q2. Third and fourth places went to Spain (17.51%) and Venezuela (16.75%), with Portugal rounding off the Top 5 (16.01%).
Country %*
Guatemala 18,97
Brazil 18,62
Spain 17,51
Venezuela 16,75
Portugal 16,01
China 15,99
Australia 15,65
Panama 15,33
Georgia 15,10
Ecuador 15,03
* Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky Lab users in the country
Organizations under attack
The rating of categories of organizations attacked by phishers is based on triggers of the Anti-Phishing component on user computers. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
As in the previous quarter, the Global Internet Portals category was in first place, bumping its share up to 32.27% (+7.27 p.p.).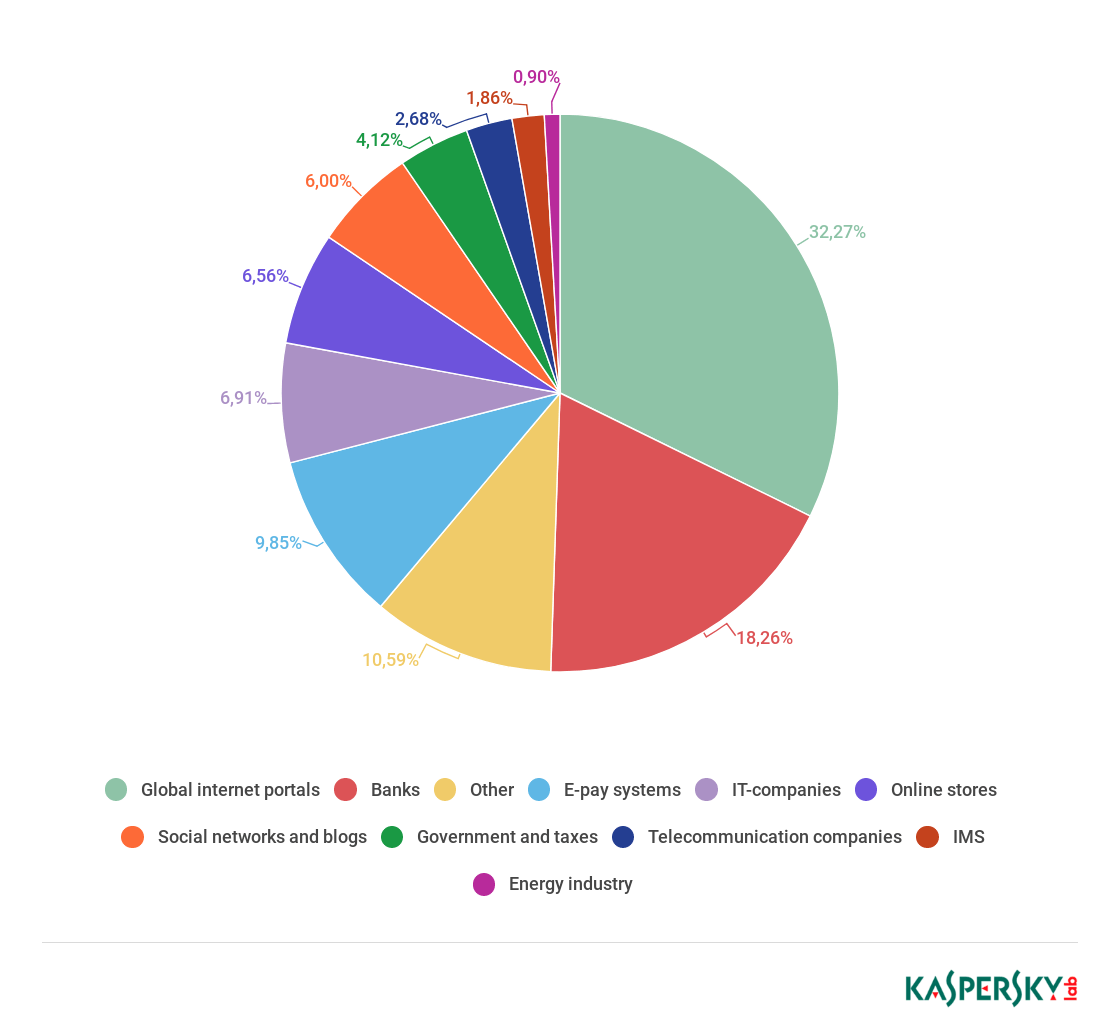
Distribution of organizations whose users were attacked by phishers, by category, Q3 2018 (download)
Only organizations that can be combined into a general Finance category were attacked more than global Internet portals. This provisional category accounted for 34.67% of all attacks (-1.03 p.p.): banks and payment systems had respective shares of 18.26% and 9.85%; only online stores (6.56%) had to concede fourth place to IT companies (6.91%).
Conclusion
In Q3 2018, the average share of spam in global mail traffic rose by 2.88 p.p. to 52.54%, and the Anti-Phishing system prevented more than 137 million redirects to phishing sites, up 30 million against the previous reporting period.
Spammers and phishers continue to exploit big news stories. This quarter, for instance, great play was made of the release of the new iPhone. The search for channels to distribute fraudulent content also continued. Alongside an uptick in Instagram activity, we spotted fake notifications from websites and the spreading of fake news through media resources.
A separate mention should go to the expanding geography of ransomware spam, featuring the use of victims’ real personal data.